给大家的福利
零基础入门
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
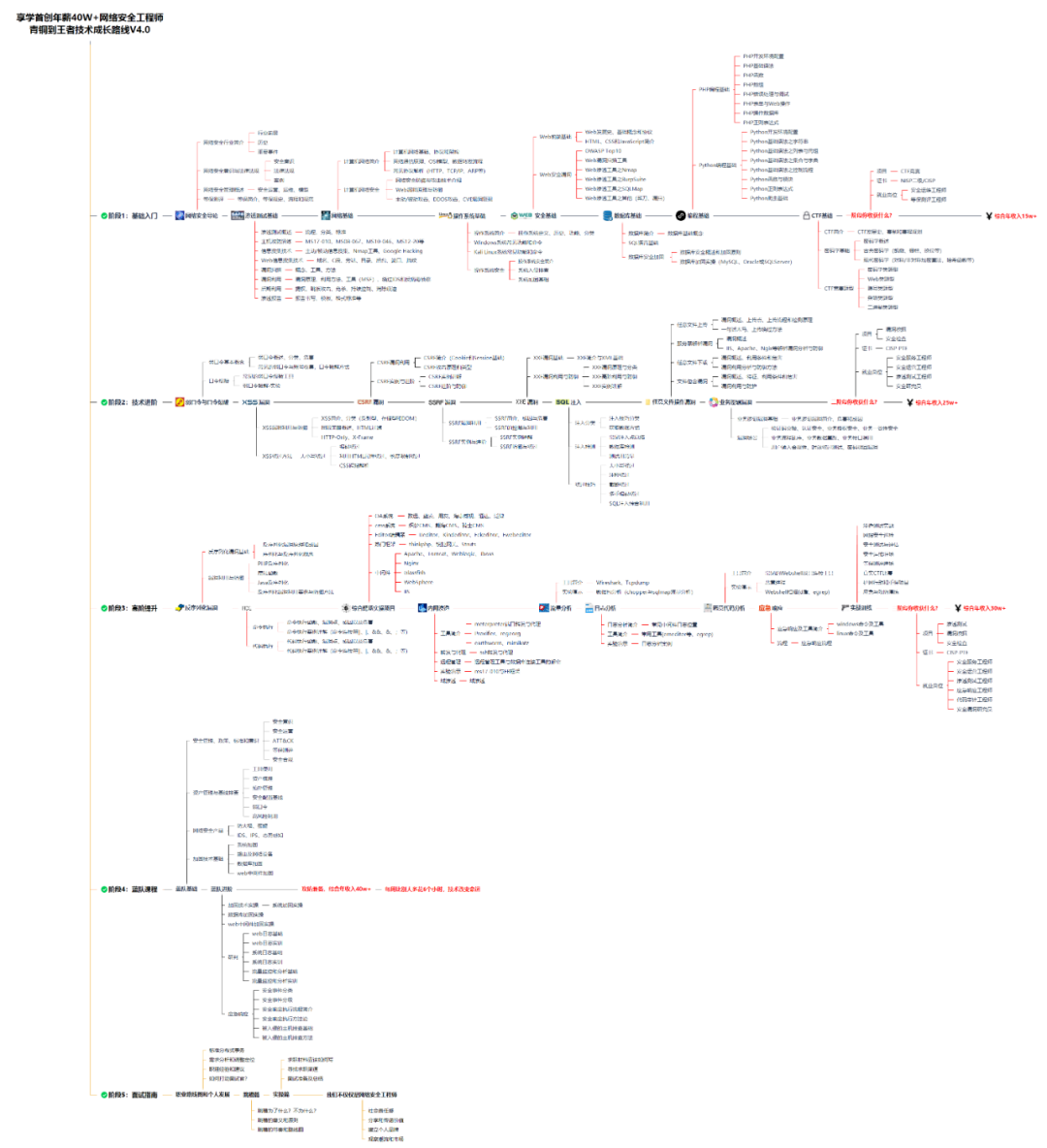
同时每个成长路线对应的板块都有配套的视频提供:
因篇幅有限,仅展示部分资料
网络安全面试题
绿盟护网行动
还有大家最喜欢的黑客技术
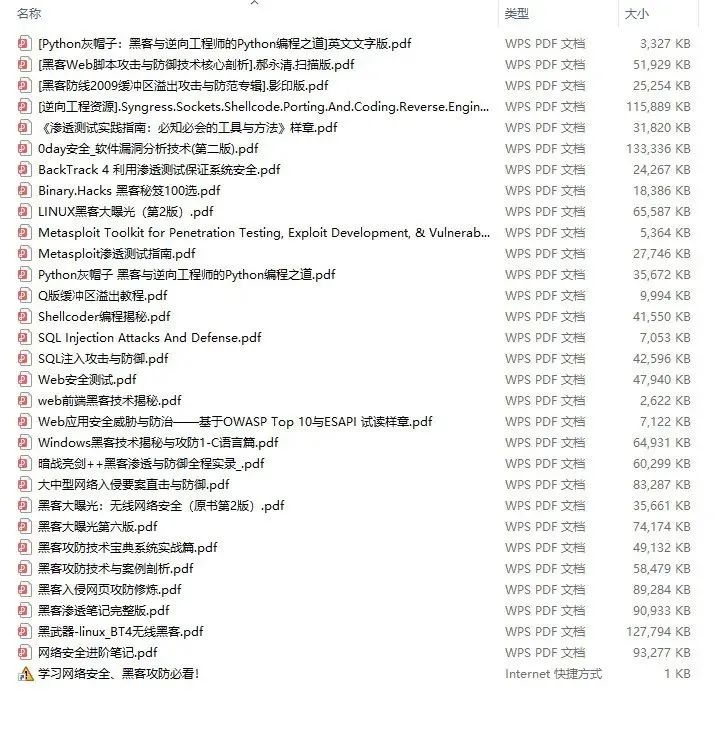
网络安全源码合集+工具包

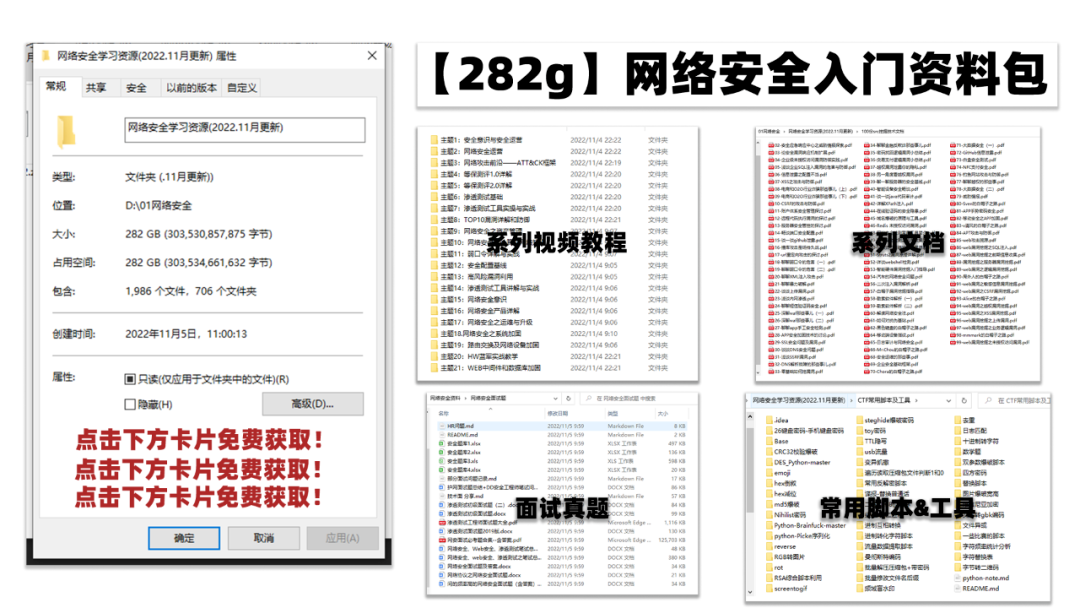
所有资料共282G,朋友们如果有需要全套《网络安全入门+黑客进阶学习资源包》,可以扫描下方二维码领取(如遇扫码问题,可以在评论区留言领取哦)~
需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
自动检测/配置脚本
#! /bin/bash
#检查系统版本
function CheckSystem() {
system\_version=''
if [[ -e /etc/os-release ]]; then
source /etc/os-release
system\_version=${system\_version}"PRETTY\_NAME: $PRETTY\_NAME, "
else
system\_version=${system\_version}"PRETTY\_NAME: `cat /etc/issue|head -n 1`, "
fi
var=${system\_version%??}
echo "......${var}......"
}
#检查密码有效期
function CheckPassMaxDays() {
PASS\_MAX\_DAYS=`cat /etc/login.defs | grep PASS\_MAX\_DAYS | grep -v ^# | awk '{print $2}'`
if [ -z $PASS\_MAX\_DAYS ];then
sed -i 's/#PASS\_MAX\_DAYS/PASS\_MAX\_DAYS/' /etc/login.defs
PASS\_MAX\_DAYS=`cat /etc/login.defs | grep PASS\_MAX\_DAYS | grep -v ^# | awk '{print $2}'`
fi
if [ -z $PASS\_MAX\_DAYS ];then
echo "............[N] Password Validity Period: Reset failed"
elif [ $PASS\_MAX\_DAYS -le 90 -a $PASS\_MAX\_DAYS -ge 30 ];then
echo "......[Y] Password Validity Period: $PASS\_MAX\_DAYS days"
else
sed -i '/PASS\_MAX\_DAYS/s/'"${PASS\_MAX\_DAYS}"'/90/g' /etc/login.defs
PASS\_MAX\_DAYS=`cat /etc/login.defs | grep PASS\_MAX\_DAYS | grep -v ^# | awk '{print $2}'`
if [ $PASS\_MAX\_DAYS -le 90 -a $PASS\_MAX\_DAYS -ge 30 ];then
echo "......[Y] Password Validity Period: $PASS\_MAX\_DAYS days"
else
echo "............[N] Password Validity Period: Reset failed"
fi
fi
}
#检查日志保留时间
function CheckLogBackupTime() {
Log\_Backup\_Time=`cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'`
if [ -z $Log\_Backup\_Time ];then
sed -i 's/#rotate/rotate/' /etc/logrotate.conf
Log\_Backup\_Time=`cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'`
fi
if [ -z $Log\_Backup\_Time ];then
echo "............[N] Log backup Time,Configuration does not exist"
elif [ $Log\_Backup\_Time -ge 26 ];then
echo "......[Y] Log backup Time: $Log\_Backup\_Time weeks"
else
sed -i '/rotate/s/'"${Log\_Backup\_Time}"'/26/g' /etc/logrotate.conf
Log\_Backup\_Time=`cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'`
if [ $Log\_Backup\_Time -ge 26 ];then
echo "......[Y] Log backup Time: $Log\_Backup\_Time weeks"
else
echo "............[N] Log backup Time,Reset failed"
fi
fi
}
#检查会话超时时间
function CheckConnectionTimeout() {
Connection\_Timeout=`cat /etc/profile | grep 'export TMOUT' | grep -v ^# | cut -d= -f2`
if [ -z $Connection\_Timeout ];then
sed -i '$a export TMOUT=1800' /etc/profile
elif [ $Connection\_Timeout -gt 1800 -o $Connection\_Timeout -lt 600 ];then
sed -i '/TMOUT/s/'"${Connection\_Timeout}"'/1800/g' /etc/profile
fi
source /etc/profile
Connection\_Timeout=`cat /etc/profile | grep 'export TMOUT' | grep -v ^# | cut -d= -f2`
if [ $Connection\_Timeout -le 1800 -a $Connection\_Timeout -ge 600 ];then
echo "......[Y] Connection timeout: $Connection\_Timeout seconds"
else
echo "............[N] Connection timeout: Reset failed"
fi
}
#检查共享账户
function CheckSharedUser() {
usermod -L shutdown 2>/dev/null
usermod -L halt 2>/dev/null
echo "......[Y] Shared user: Locked"
}
#检查审计策略
function CheckAuditLogs() {
Audit\_Logs=`auditctl -s | grep enabled | awk '{print $2}'`
if [ $Audit\_Logs -ne 1 ];then
systemctl start auditd
systemctl enable auditd
fi
Audit\_Logs=`auditctl -s | grep enabled | awk '{print $2}'`
if [ $Audit\_Logs -eq 1 ];then
echo "......[Y] Audit Policy: $Audit\_Logs Enable"
else
echo "............[N] Audit Policy: $Audit\_Logs Disabled"
fi
}
#检查分权账户
function CheckAuthorizedUser() {
shenji=`cat /etc/passwd |grep shenji | grep -v ^# | cut -d: -f 1`
anquan=`cat /etc/passwd |grep anquan | grep -v ^# | cut -d: -f 1`
sysadmin=`cat /etc/passwd |grep sysadmin | grep -v ^# | cut -d: -f 1`
if [ -z $shenji ];then
useradd shenji
echo shenji:In123!@#123|chpasswd
sed -i '$a shenji ALL = (root) NOPASSWD: /usr/bin/cat , /usr/bin/less , /usr/bin/more , /usr/bin/tail , /usr/bin/head' /etc/sudoers
fi
if [ -z $anquan ];then
useradd anquan
echo anquan:In123!@#123|chpasswd
fi
if [ -z $sysadmin ];then
useradd sysadmin
echo sysadmin:In123!@#123|chpasswd
fi
shenji=`cat /etc/passwd |grep shenji | grep -v ^# | cut -d: -f 1`
anquan=`cat /etc/passwd |grep anquan | grep -v ^# | cut -d: -f 1`
sysadmin=`cat /etc/passwd |grep sysadmin | grep -v ^# | cut -d: -f 1`
if [ -z $shenji -o -z $anquan -o -z $sysadmin ];then
echo "............[N] Authorized user: $shenji, $anquan, $sysadmin"
else
echo "......[Y] Authorized user: $shenji, $anquan, $sysadmin"
fi
}
#检查登录失败锁定配置CentOS
function CheckLoginFailureLock\_CentOS() {
Login\_Failure\_Lock=`grep "pam\_tally2.so" /etc/pam.d/system-auth| grep -v ^#|head -n 1|awk '{print $7}'`
if [ -z $Login\_Failure\_Lock ];then
sed -i '/pam_tally2.so/s/#auth/auth/g' /etc/pam.d/system-auth
Login\_Failure\_Lock=`grep "pam\_tally2.so" /etc/pam.d/system-auth| grep -v ^#|head -n 1|awk '{print $7}'`
fi
if [ -z $Login\_Failure\_Lock ];then
sed -i '$a auth required pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600 even\_deny\_root root\_unlock\_time=600' /etc/pam.d/system-auth
else
Login\_Failure\_Lock=`grep "pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600" /etc/pam.d/system-auth| grep -v ^#|awk '{print $7}'`
if [ -z $Login\_Failure\_Lock ];then
sed -i '/pam\_tally2.so/s/auth/#auth/g' /etc/pam.d/system-auth
sed -i '$a auth required pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600 even\_deny\_root root\_unlock\_time=600' /etc/pam.d/system-auth
fi
fi
Login\_Failure\_Lock=`grep "pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600" /etc/pam.d/system-auth| grep -v ^#|awk '{print $7","$8","$10}'`
if [ -z $Login\_Failure\_Lock ];then
echo "............[N] Login Failure Lock: Reset failed"
else
echo "......[Y] Login Failure Lock: $Login\_Failure\_Lock"
fi
}
#检查登录失败锁定配置SUSE
function CheckLoginFailureLock\_SUSE() {
Login\_Failure\_Number=`cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'`
if [ -z $Login\_Failure\_Number ];then
sed -i 's/#LOGIN\_RETRIES/LOGIN\_RETRIES/' /etc/login.defs
Login\_Failure\_Number=`cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'`
fi
if [ -z $Login\_Failure\_Number ];then
echo "............[N] Number of login failures: No configuration"
elif [ $Login\_Failure\_Number -le 8 -a $Login\_Failure\_Number -ge 3 ];then
echo "......[Y] Number of login failures: $Login\_Failure\_Number"
else
sed -i '/LOGIN\_RETRIES/s/'"${Login\_Failure\_Number}"'/5/g' /etc/login.defs
Login\_Failure\_Number=`cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'`
if [ $Login\_Failure\_Number -le 8 -a $Login\_Failure\_Number -ge 3 ];then
echo "......[Y] Number of login failures: $Login\_Failure\_Number"
else
echo "............[N] Number of login failures: No configuration"
fi
fi
Login\_Failure\_Time=`cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'`
if [ -z $Login\_Failure\_Time ];then
sed -i 's/#LOGIN\_TIMEOUT/LOGIN\_TIMEOUT/' /etc/login.defs
Login\_Failure\_Time=`cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'`
fi
if [ -z $Login\_Failure\_Time ];then
echo "............[N] Login failure lock time: Reset failed"
elif [ $Login\_Failure\_Time -le 1800 -a $Login\_Failure\_Time -ge 300 ];then
echo "......[Y] Login failure lock time: $Login\_Failure\_Time seconds"
else
sed -i '/LOGIN\_TIMEOUT/s/'"${Login\_Failure\_Time}"'/300/g' /etc/login.defs
Login\_Failure\_Time=`cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'`
if [ $Login\_Failure\_Time -le 1800 -a $Login\_Failure\_Time -ge 300 ];then
echo "......[Y] Login failure lock time: $Login\_Failure\_Time seconds"
else
echo "............[N] Login failure lock time: Reset failed"
fi
fi
}
#检查密码策略CentOS
function CheckPasswordPolicy\_CentOS() {
Password\_Policy=`grep "pam\_cracklib.so" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'`
if [ -z $Password\_Policy ];then
sed -i '/pam_cracklib.so/s/#password/password/g' /etc/pam.d/system-auth
Password\_Policy=`grep "pam\_cracklib.so" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'`
fi
if [ -z $Password\_Policy ];then
sed -i '$a password requisite pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1' /etc/pam.d/system-auth
else
Password\_Policy=`grep "pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'`
if [ -z $Password\_Policy ];then
sed -i '/pam\_cracklib.so/s/password/#password/g' /etc/pam.d/system-auth
sed -i '$a password requisite pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1' /etc/pam.d/system-auth
fi
fi
Password\_Policy=`grep "pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4","$5","$6","$7","$8}'`
if [ -z $Password\_Policy ];then
echo "............[N] Password Policy: Reset failed"
else
echo "......[Y] Password Policy: $Password\_Policy"
fi
}
#检查密码策略SUSE
function CheckPasswordPolicy\_SUSE() {
Password\_Policy=`grep "pam\_cracklib.so" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'`
if [ -z $Password\_Policy ];then
sed -i '/pam\_cracklib.so/s/#password/password/g' /etc/pam.d/common-password
Password\_Policy=`grep "pam\_cracklib.so" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'`
fi
if [ -z $Password\_Policy ];then
sed -i '$a password requisite pam\_cracklib.so retry=3 difok=3 minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1' /etc/pam.d/common-password
else
Password\_Policy=`grep "minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'`
if [ -z $Password\_Policy ];then
sed -i '/pam\_cracklib.so/s/password/#password/g' /etc/pam.d/common-password
sed -i '$a password requisite pam\_cracklib.so retry=3 difok=3 minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1' /etc/pam.d/common-password
fi
fi
Password\_Policy=`grep "minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/common-password| grep -v ^#|awk '{print $4","$5","$6","$7","$8}'`
if [ -z $Password\_Policy ];then
echo "............[N] Password Policy: Reset failed"
else
echo "......[Y] Password Policy: $Password\_Policy"
fi
}
#检查日志服务CentOS
function CheckLogService\_CentOS() {
Log\_Service=`systemctl status rsyslog | grep active | awk '{print $3}'`
if [ $Log\_Service != "(running)" ];then
systemctl start rsyslog
systemctl enable rsyslog
fi
Log\_Service=`systemctl status rsyslog | grep active | awk '{print $3}'`
if [ $Log\_Service = "(running)" ];then
echo "......[Y] Log Service: $Log\_Service"
else
echo "............[N] Log Service: $Log\_Service"
fi
}
#检查日志服务SUSE
function CheckLogService\_SUSE() {
Log\_Service=`systemctl status syslog-ng | grep active | awk '{print $3}'`
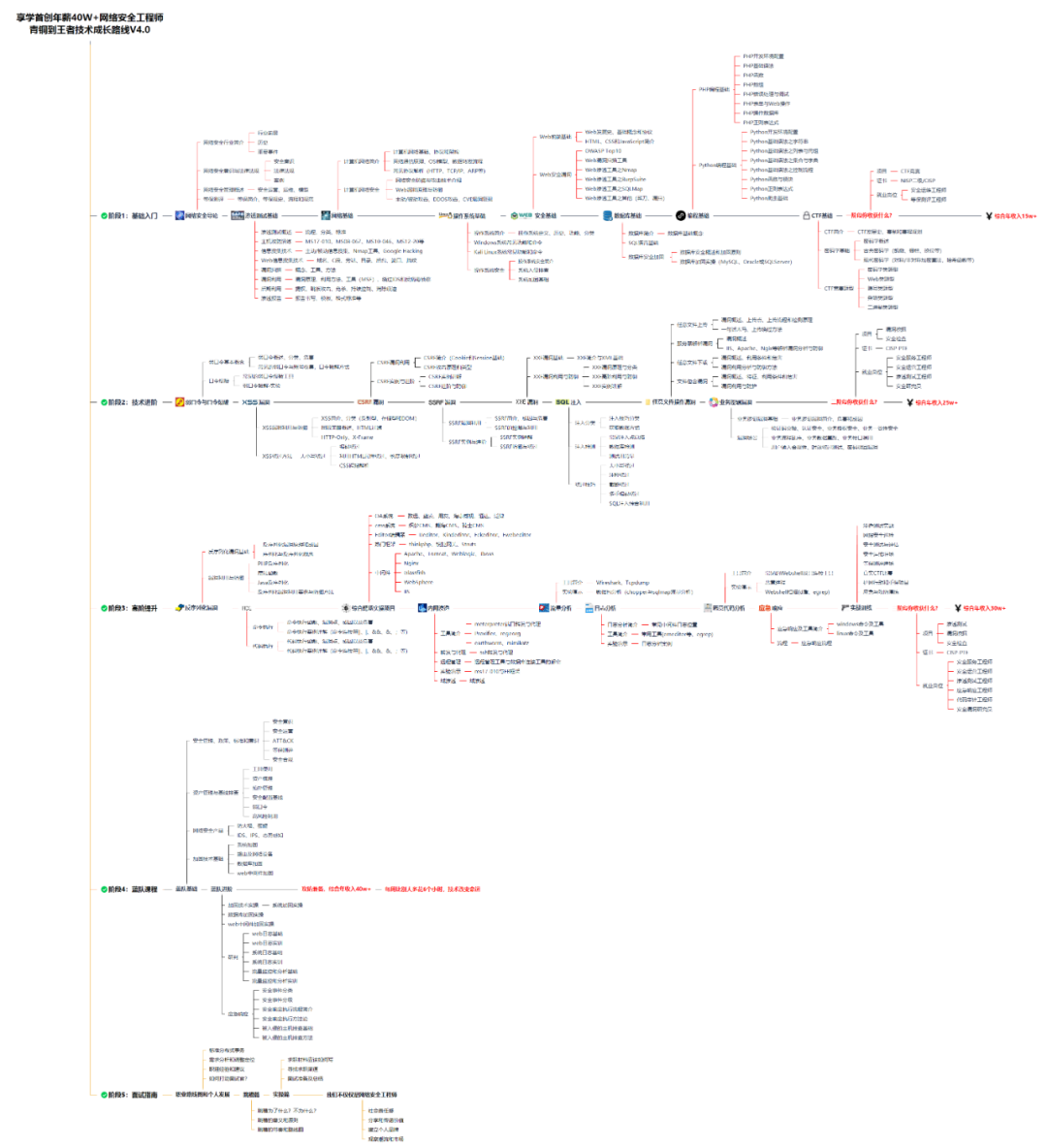
### 一、网安学习成长路线图
网安所有方向的技术点做的整理,形成各个领域的知识点汇总,它的用处就在于,你可以按照上面的知识点去找对应的学习资源,保证自己学得较为全面。
### 二、网安视频合集
观看零基础学习视频,看视频学习是最快捷也是最有效果的方式,跟着视频中老师的思路,从基础到深入,还是很容易入门的。
### 三、精品网安学习书籍
当我学到一定基础,有自己的理解能力的时候,会去阅读一些前辈整理的书籍或者手写的笔记资料,这些笔记详细记载了他们对一些技术点的理解,这些理解是比较独到,可以学到不一样的思路。
### 四、网络安全源码合集+工具包
光学理论是没用的,要学会跟着一起敲,要动手实操,才能将自己的所学运用到实际当中去,这时候可以搞点实战案例来学习。
**需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)**

### 五、网络安全面试题
最后就是大家最关心的网络安全面试题板块
**网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。**
**[需要这份系统化资料的朋友,可以点击这里获取](https://bbs.csdn.net/topics/618540462)**
**一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**






















 1651
1651

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








