08 陈天灏
Linux 配置 DNS服务
DNS 简介
域名系统(Domain Name System,缩写: DNS)是互联网的一项服务。域名解析是把域名指向网站空间IP,让人们通过注册的域名可以方便地访问到网站的一种服务。IP地址是网络上标识站点的数字地址,为了方便记忆,采用域名来代替IP地址标识站点地址。域名解析就是域名到IP地址的转换过程。域名的解析工作由DNS服务器完成。可以理解为DNS就是翻译官。
环境准备
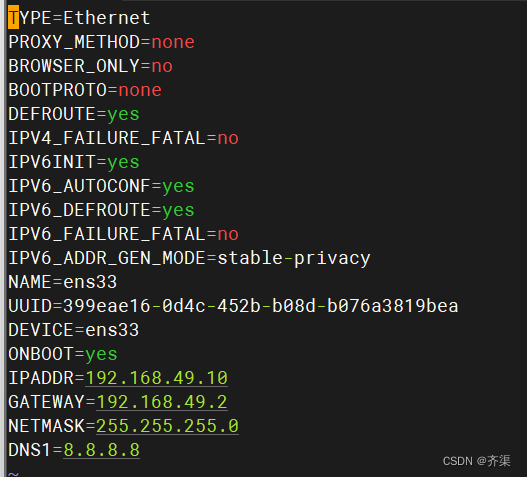
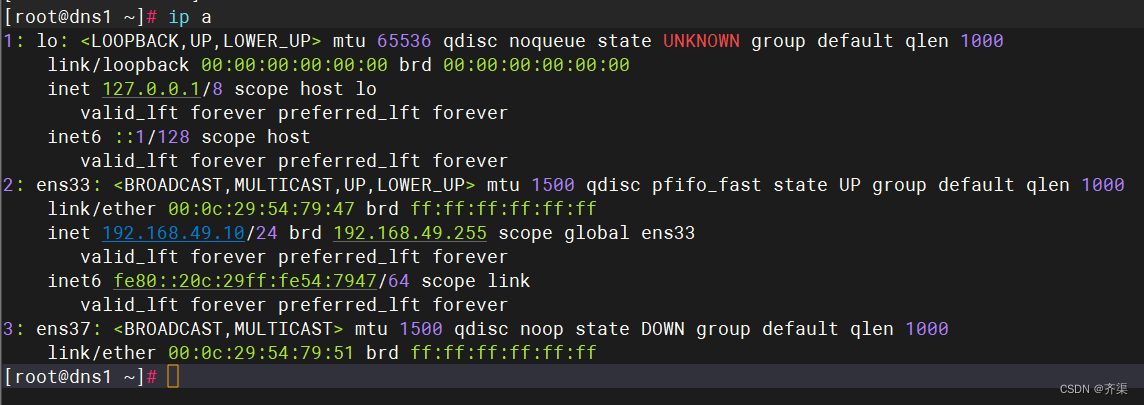
两台centos7虚拟机,绑定固定ip地址,关闭防火墙和selinux
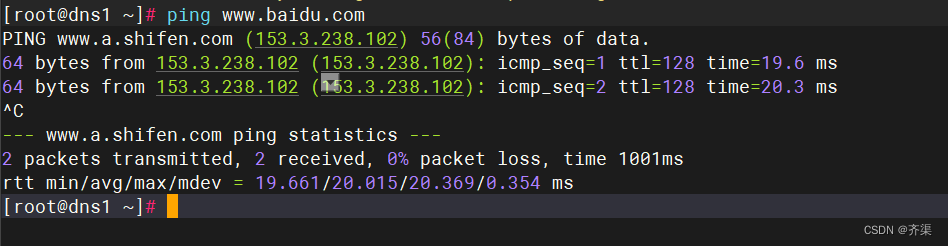
配置yum源
rm -rf /etc/yum.repos.d/*
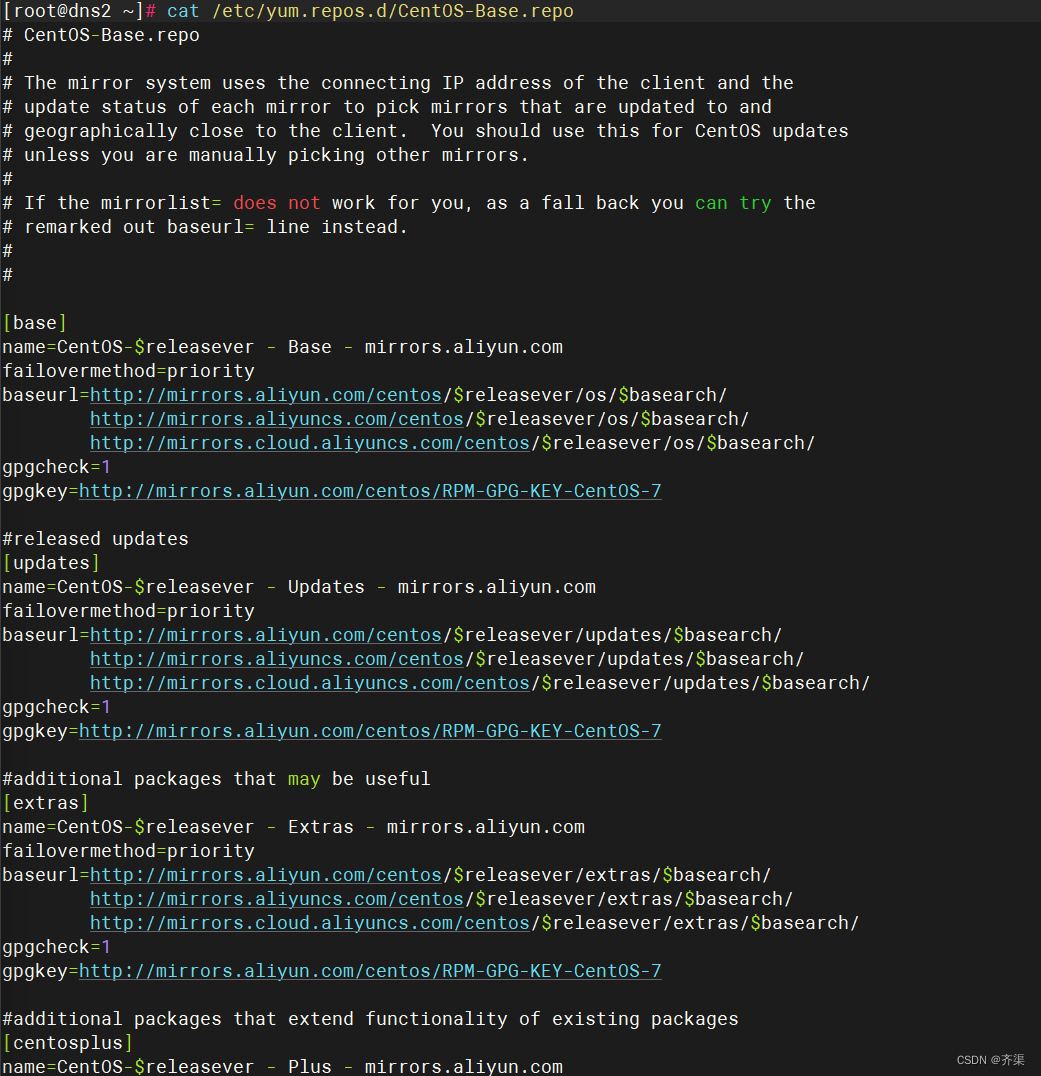
使用阿里源一键配置
curl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.aliyun.com/repo/Centos-7.repo
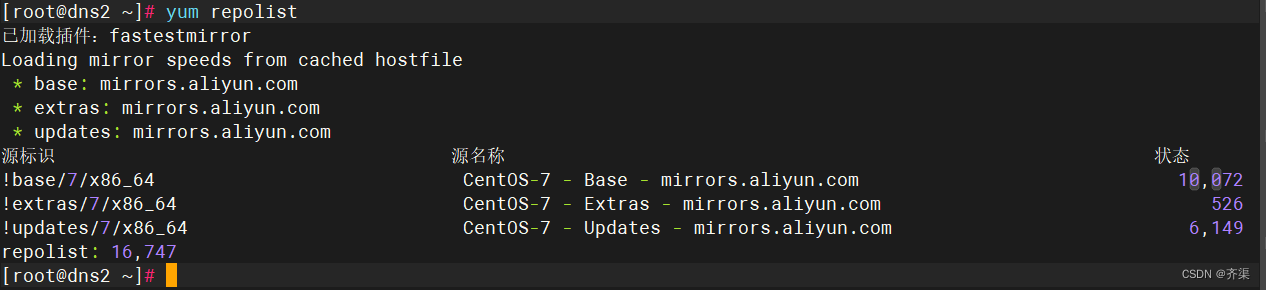
检查yum源
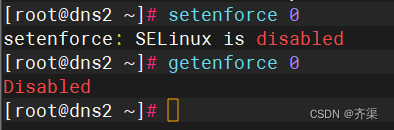
关闭防火墙和selinux
systemctl disable firewalld
systemctl stop firewalld
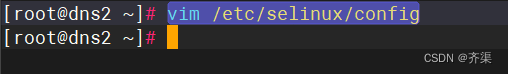
vim /etc/selinux/config
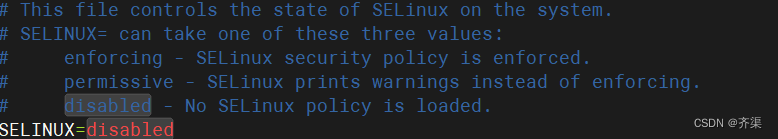
SELINUX=disabled

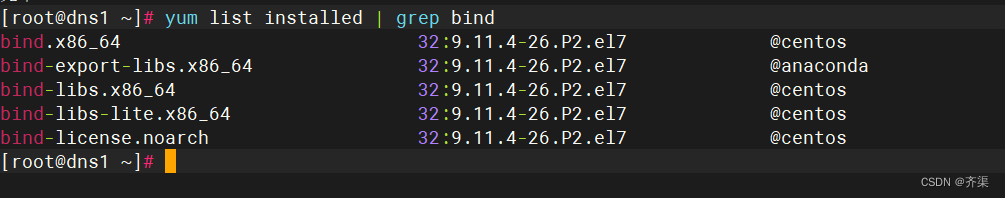
安装DNS软件包

检查是否安装成功
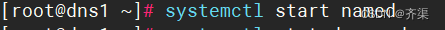
启动服务
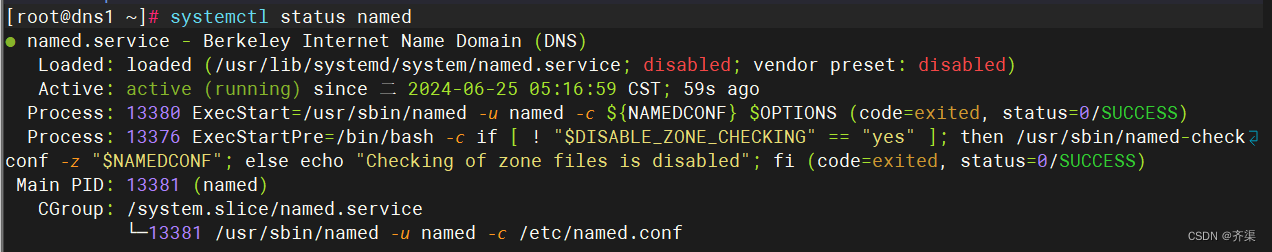
查看配置文件
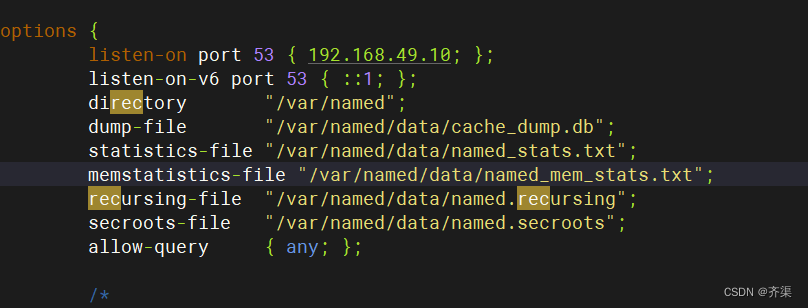
[root@dns1 ~]# cat /etc/named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { 192.168.49.10; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
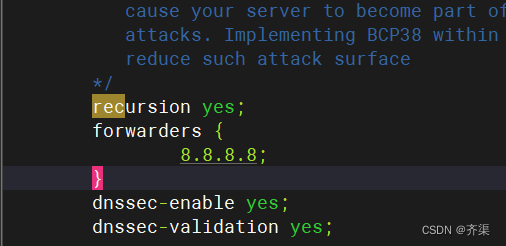
recursion yes;
forwarders {
8.8.8.8;
}
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
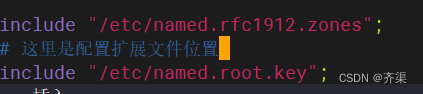
include "/etc/named.rfc1912.zones";
# 这里是配置扩展文件位置
include "/etc/named.root.key";查看扩展文件
正向代理模版
反向代理模版
正确配置
[root@dns1 ~]# cat /etc/named.rfc1912.zones
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
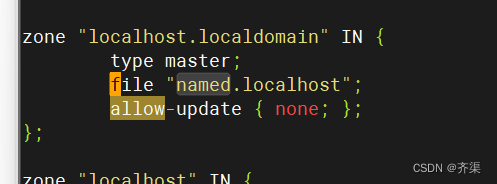
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
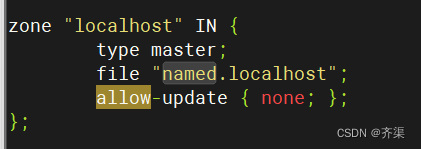
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
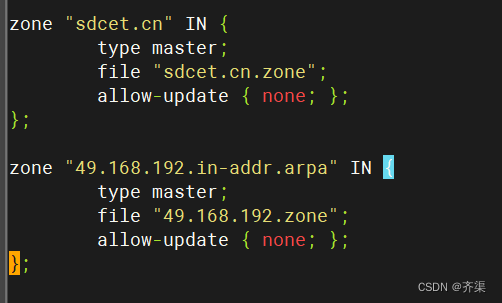
zone "sdcet.cn" IN {
type master;
file "sdcet.cn.zone";
allow-update { none; };
};
zone "49.168.192.in-addr.arpa" IN {
type master;
file "49.168.192.zone";
allow-update { none; };
};配置反向解析文
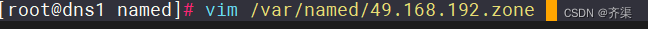
[root@dns1 ~]# vim /var/named/49.168.192.zone
$TTL 1D
@ IN SOA dns.sdcet.cn. admin.sdcet.cn. (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS dns.sdcet.cn.
10 IN PTR dns.sdcet.cn.
10 IN PTR www.sdcet.cn.
100 IN PTR mail.sdcet.cn.
101 IN PTR ftp.sdcet.cn.
200 IN PTR oa.sdcet.cn.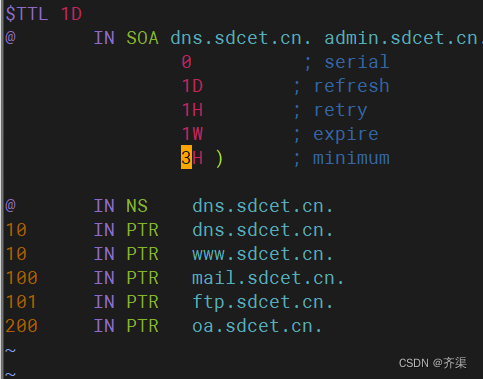
配置正向代理
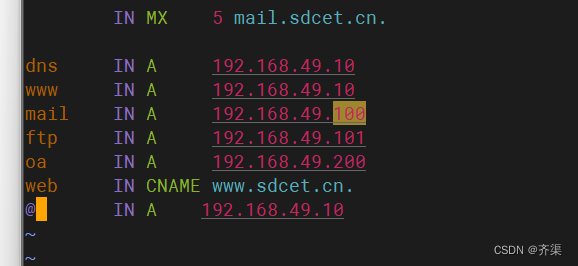
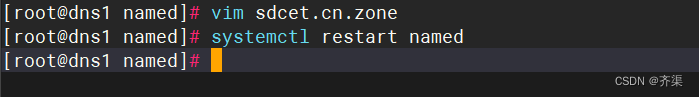
[root@dns1 ~]# vim /var/named/sdcet.cn.zone
$TTL 1D
@ IN SOA dns.sdcet.cn. admin.sdcet.cn. (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS dns.sdcet.cn.
IN MX 5 mail.sdcet.cn.
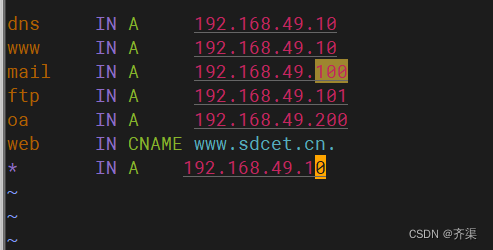
dns IN A 192.168.49.10
www IN A 192.168.49.10
mail IN A 192.168.49.100
ftp IN A 192.168.49.101
oa IN A 192.168.49.200
web IN CNAME www.sdcet.cn.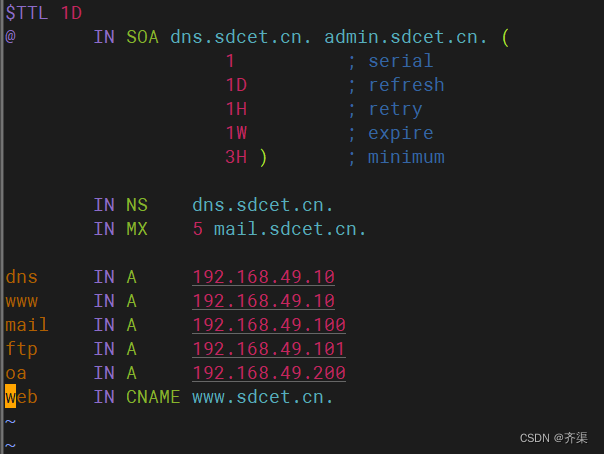
重启

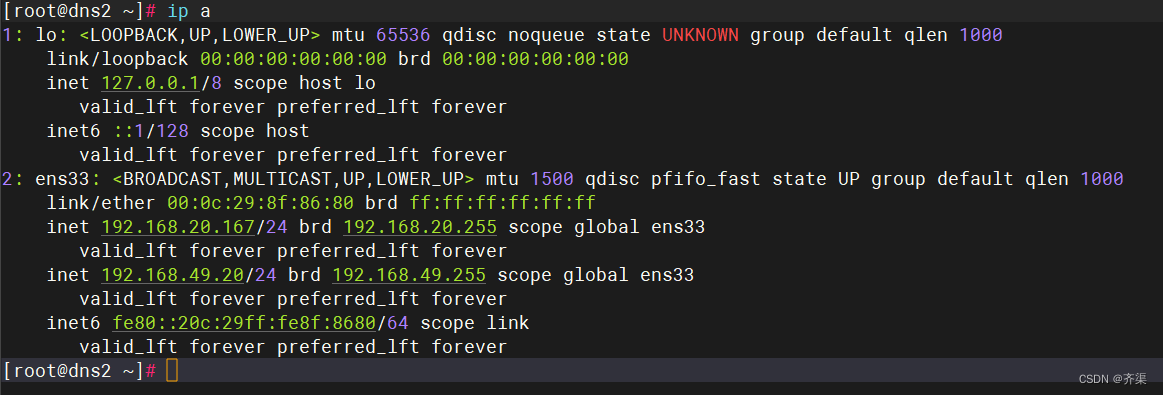
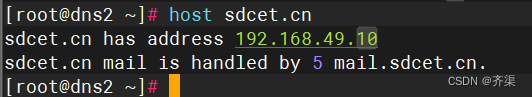
客户机测试,将DNS设置为本地DNS服务器
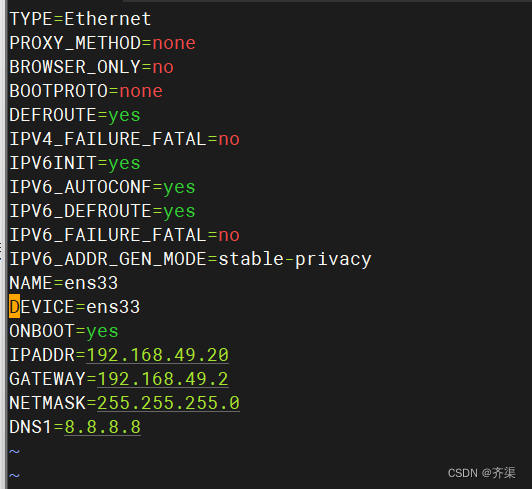
[root@dns2 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.49.20
GATEWAY=192.168.49.2
NETMASK=255.255.255.0
DNS1=192.168.49.10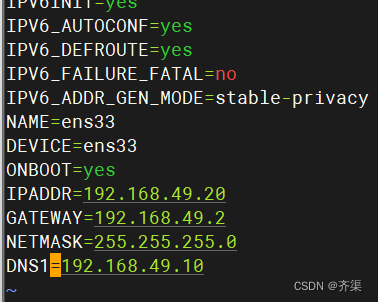
重启网卡


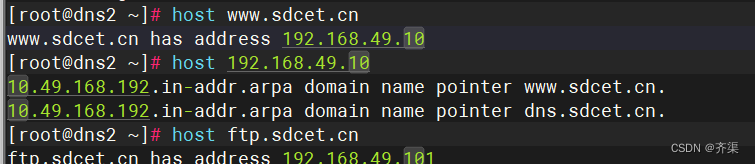
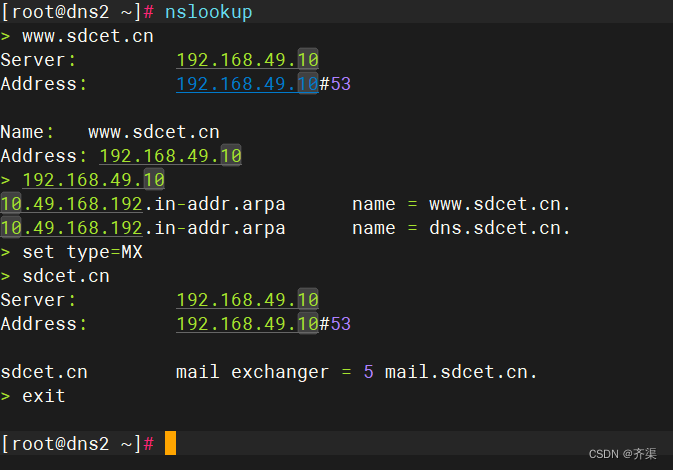
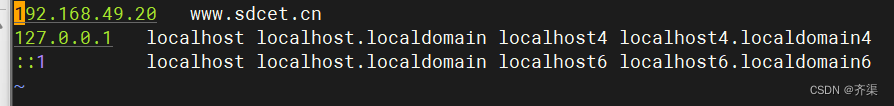
关于hosts
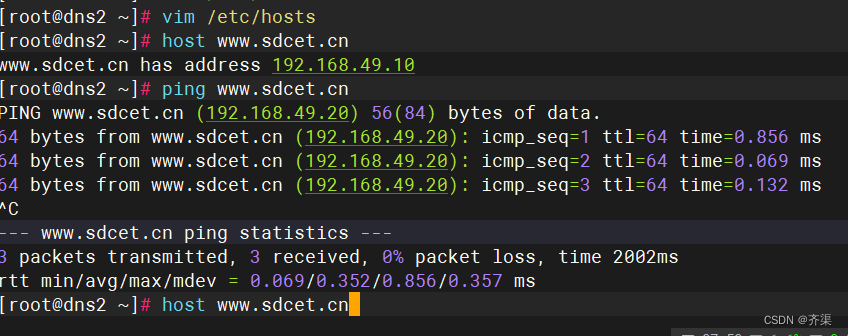
泛域名解析
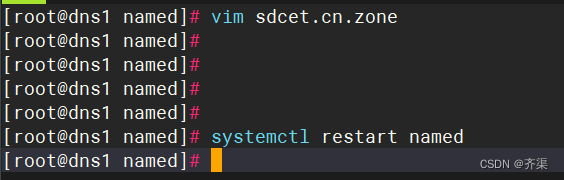
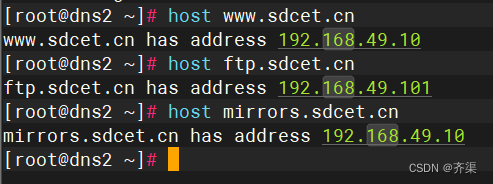
直接实现域名解析
Dns转发器
出现下图就是大功搞成啦!





















 2645
2645

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








