先自我介绍一下,小编浙江大学毕业,去过华为、字节跳动等大厂,目前阿里P7
深知大多数程序员,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年最新网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。






既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较多,这里只是将部分目录截图出来,全套包含大厂面经、学习笔记、源码讲义、实战项目、大纲路线、讲解视频,并且后续会持续更新
如果你需要这些资料,可以添加V获取:vip204888 (备注网络安全)

正文
- 8 Amazon GuardDuty
- 9 AWS Systems Manager(SSM)
-
* 9.1 特性- 9.2 工作原理
- 9.3 Run Command
- 9.4 Systems Manager Parameter Store
- 10 AWS Security Hub
- 11 Amazon Detective
- 12 Amazon Macie
- 13 AWS组件内的安全
-
* 13.1 Web Server 集成SSL- 13.2 RDS security
- 13.3 S3 security
-
* 13.3.1 四种加密方式- 13.3.2 S3的Events
- 13.3.3 S3的安全
- 13.3.4 其它相关安全措施
- 13.4 Network Security, DDoS, Shield & WAF
-
* 13.4.1 Network Security- 13.4.2 DDoS&Shield
- 13.5 Network Firewall
-
* 13.5.1 基本特性- 13.5.2 典型架构
- 13.6 网络安全架构
1 AWS CloudTrail
AWS CloudTrail 是一项 AWS 服务,可帮助您对 AWS 账户进行操作和风险审核、监管和合规性检查。用户、角色或 AWS
服务执行的操作将记录为 CloudTrail 中的事件。事件包括在 AWS Management Console、AWS Command Line
Interface 和 AWS 开发工具包和 API
中执行的操作。简单来说,CloudTrail就是可以对用户在AWS上的行为进行采集、存储、操作和审查等,之所以将其放在安全部分,是因为对行为的监控是安全的第一步。
1.1 基本特性
- 包括: management events(管理事件)、data events(数据事件)、Insights events(见解事件)
- 可以将日志存入CloudWatch Logs中
- 可以和不同服务集成做更多事情:https://docs.aws.amazon.com/zh_cn/awscloudtrail/latest/userguide/cloudtrail-aws-service-specific-topics.html
- 控制台可以查看过去90天内容
- 默认包括创建、修改和删除事件,也可以自定义内容展示
1.2 典型架构
-
日志的处理架构

-
多账号多区域统一日志管理
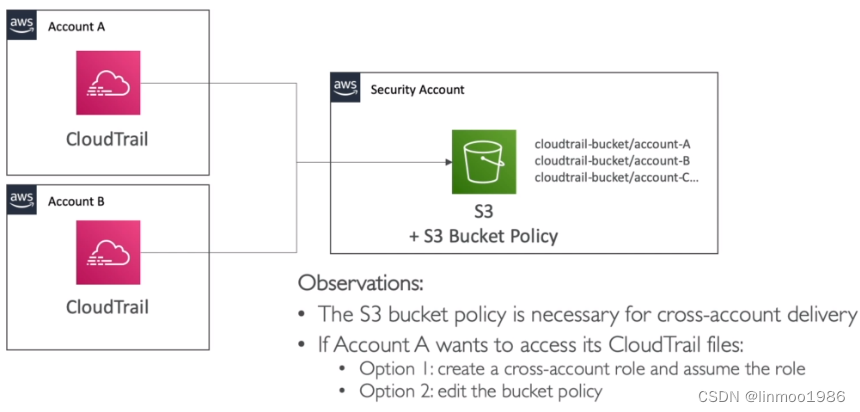
-
通过日志采集设置报警架构
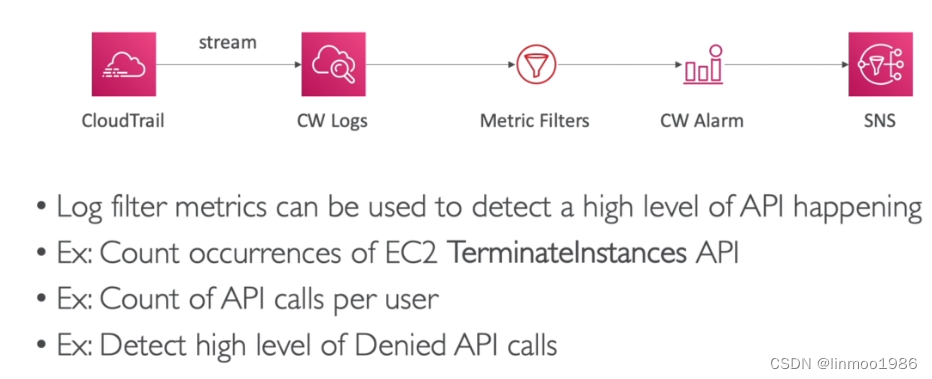
-
Organization下统一日志管理
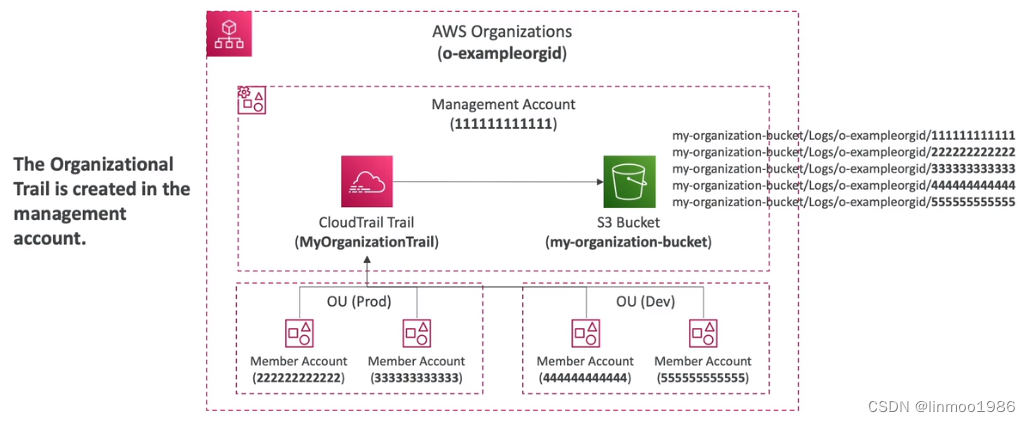
1.3 方案比较
日志采集后存储及处理,会有不同方案,不同的方案有不同的应用场景,下列给出不同方案,可供不同场景使用:
| 方案 | 解决问题 |
|---|---|
| CloudWatch Event | 能够在CloudTrail触发API调用,是目前延迟最小的监控 |
| CloudWatch Logs | 以流式将日志过滤并可以设置警告通知 |
| S3 | 将日志存储在S3,可以长期保持并且结合如Athena工具进行检索 |
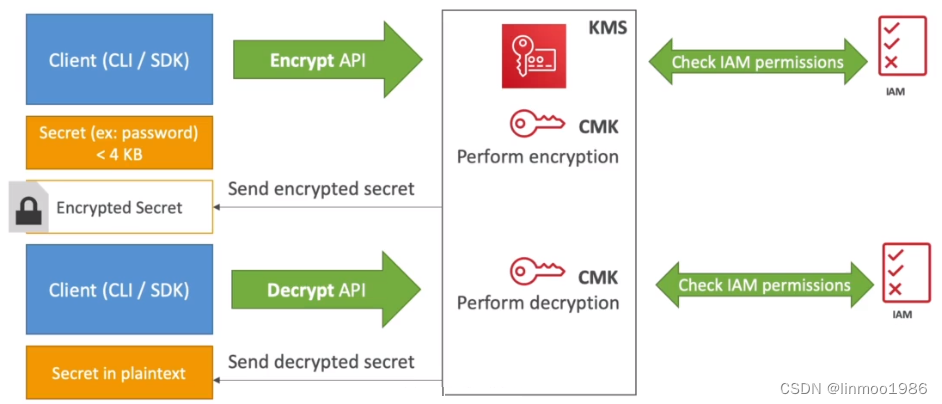
2 AWS KMS
AWS Key Management Service(AWS
KMS)是一项托管式服务,可让您轻松创建和控制用于保护您的数据的加密密钥。简单理解,就是一个加密平台,上面保存密钥,同时提供API供客户端进行加密和解密。
2.1 基本特性
- 基本功能是用来加密和解密(考试中但凡与加密解密有关的,那么一般跟KMS也有关系 )
- 有AWS管理密钥,因此安全度高
- AWS KMS 与大多数用于加密数据的其他 AWS 服务集成
例题:A company needs to move its write-intensive Amazon RDS for PostgreSQL
database from the eu-west-1 Region to the eu-north-1 Region. As part of the
migration, the company needs to change from Amazon RDS for PostgreSQL to
Amazon Aurora PostgreSQL.
The company is using a new AWS account to host a new Aurora PostgreSQL DB
cluster. The RDS database is encrypted with an AWS managed AWS Key
Management Service (AWS KMS) key. There must be no interruption to
applications that use the RDS for PostgreSQL DB instance.
Which solution will meet these requirements?
A. Create VPC peering between the VPCs in both accounts. Take a snapshot of
the RDS DB instance. Export the snapshot to Amazon S3. Create an S3 gateway
endpoint. Use the S3 sync command for ongoing synchronization of data.
Restore the snapshot from Amazon S3 in the Aurora account. Migrate the
snapshot to the Aurora DB cluster.
B. Create VPC peering between the VPCs in both accounts. Import the AWS
managed KMS key to the Aurora account. Take a snapshot of the RDS DB
instance. Share the snapshot with the Aurora account. Copy the shared
snapshot to eu-north-1 in the Aurora account. Migrate the shared snapshot to
the Aurora DB cluster. Use AWS Database Migration Service (AWS DMS) with
ongoing replication to complete the migration.
C. Create VPC peering between the VPCs in both accounts. Copy the AWS
managed KMS key to the Aurora account. Create an Aurora cross-Region read
replica of the RDS DB instance in the Aurora account. Promote the read
replica from standby DB instance to primary DB instance.
D. Create VPC peering between the VPCs in both accounts. Create a multi-
Region customer managed KMS key in the RDS account, and share the key with
the Aurora account. Modify the cluster to use the customer managed KMS key.
Take a snapshot of the RDS DB instance. Share the snapshot with the Aurora
account. Copy the shared snapshot to eu-north-1 in the Aurora account.
Migrate the shared snapshot to the Aurora DB cluster. Use AWS Database
Migration Service (AWS DMS) with ongoing replication to complete the
migration.
答案:D
答案解析:题目要求需要跨区域迁移PostgreSQL数据库。并且使用KMS做密钥管理。因此D选项最合适。
例题:A company is implementing a serverless architecture by using AWS Lambda
functions that need to access a Microsoft SQL Server DB instance on Amazon
RDS. The company has separate environments for development and production,
including a clone of the database system. The company’s developers are
allowed to access the credentials for the development database. However, the
credentials for the production database must be encrypted with a key that
only members of the IT security team’s IAM user group can access. This key
must be rotated on a regular basis.
What should a solutions architect do in the production environment to meet
these requirements?
A. Store the database credentials in AWS Systems Manager Parameter Store by
using a SecureString parameter that is encrypted by an AWS Key Management
Service (AWS KMS) customer managed key. Attach a role to each Lambda
function to provide access to the SecureString parameter. Restrict access to
the SecureString parameter and the customer managed key so that only the IT
security team can access the parameter and the key.
B. Encrypt the database credentials by using the AWS Key Management Service
(AWS KMS) default Lambda key. Store the credentials in the environment
variables of each Lambda function. Load the credentials from the environment
variables in the Lambda code. Restrict access to the KMS key so that only
the IT security team can access the key.
C. Store the database credentials in the environment variables of each
Lambda function. Encrypt the environment variables by using an AWS Key
Management Service (AWS KMS) customer managed key. Restrict access to the
customer managed key so that only the IT security team can access the key.
D. Store the database credentials in AWS Secrets Manager as a secret that
is associated with an AWS Key Management Service (AWS KMS) customer managed
key. Attach a role to each Lambda function to provide access to the secret.
Restrict access to the secret and the customer managed key so that only the
IT security team can access the secret and the key.
答案:D
答案解析:题目要求IT团队的IAM用户才能访问密钥,且密钥定期轮转。密钥管理最好使用KMS,而存储可以是Parameter
Store或者是Secrets Manager ,题目要求定期轮转,那么应该是Secrets Manager 。所以选择D选项
- 提供CLI或者SDK进行加密和解密
- 只能对小于4KB的内容加密
- 集成CloudTrail进行API调用审计
- 密钥可以轮转
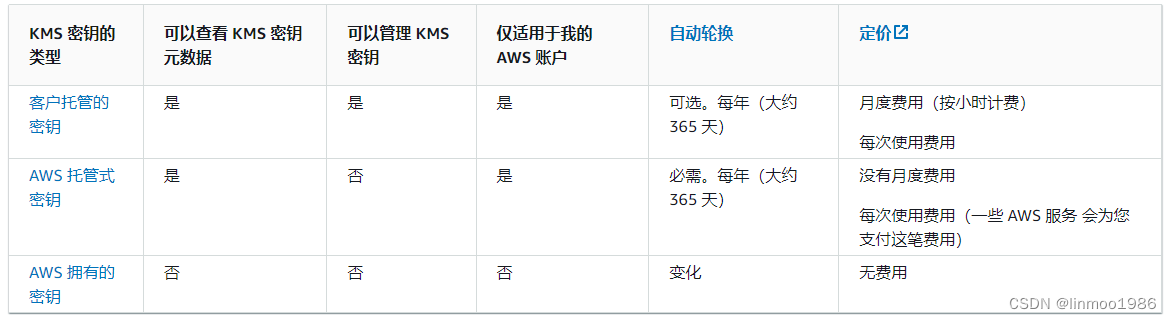
2.2 密钥类型
KMS的密钥有3种不同类型,区别如下:(考试中出现客户托管和AWS托管的区别判别 )
例题:A company has multiple business units. Each business unit has its own AWS
account and runs a single website within that account. The company also has
a single logging account. Logs from each business unit website are
aggregated into a single Amazon S3 bucket in the logging account. The S3
bucket policy provides each business unit with access to write data into the
bucket and requires data to be encrypted.
The company needs to encrypt logs uploaded into the bucket using a single
AWS Key Management Service (AWS KMS) CMK. The CMK that protects the data
must be rotated once every 365 days.
Which strategy is the MOST operationally efficient for the company to use
to meet these requirements?
A. Create a customer managed CMK in the logging account. Update the CMK key
policy to provide access to the logging account only. Manually rotate the
CMK every 365 days.
B. Create a customer managed CMK in the logging account. Update the CMK key
policy to provide access to the logging account and business unit accounts.
Enable automatic rotation of the CMK.
C. Use an AWS managed CMK in the logging account. Update the CMK key policy
to provide access to the logging account and business unit accounts.
Manually rotate the CMK every 365 days.
D. Use an AWS managed CMK in the logging account. Update the CMK key policy
to provide access to the logging account only. Enable automatic rotation of
the CMK.
答案:B
答案解析:题目要求使用KMS管理密钥,并且密钥能够轮转。因此A选项手动轮转比自动轮转要差;C选项同样手动轮转比自动轮转要差;D选项AWS
managed CMK默认就是开启rotation,所以无需在手动开启。因此选择B选项
2.3 加密和解密过程
3.4 典型架构
- 通过KMS与S3加密配置架构(需要使用:kms:GenerateDataKey)
例题:A solutions architect needs to implement a client-side encryption
mechanism for objects that will be stored in a new Amazon S3 bucket. The
solutions architect created a CMK that is stored in AWS Key Management
Service (AWS KMS) for this purpose.
The solutions architect created the following IAM policy and attached it to
an IAM role:
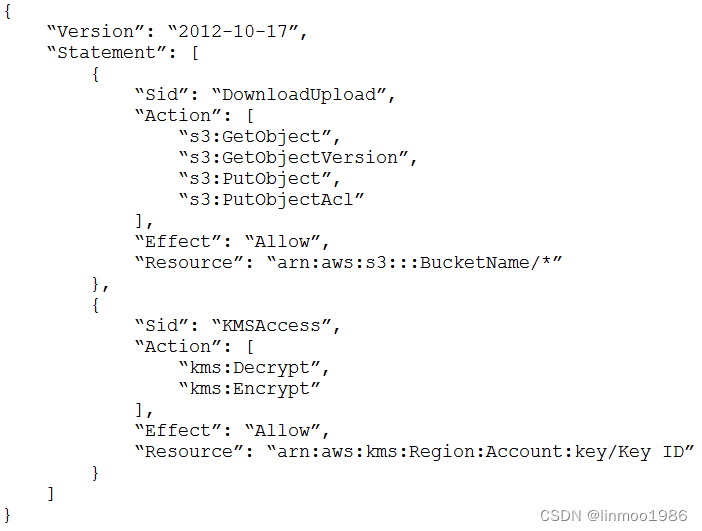
During tests, the solutions architect was able to successfully get existing
test objects in the S3 bucket. However, attempts to upload a new object
resulted in an error message. The error message stated that the action was
forbidden.
Which action must the solutions architect add to the IAM policy to meet all
the requirements?
A. kms:GenerateDataKey
B. kms:GetKeyPolicy
C. kms:GetPublicKey
D. kms:Sign
答案:A
答案解析:SSE-KMS要上传对象,需要使用AWS kms密钥的kms:GenerateDataKey权限。
例题:A health insurance company stores personally identifiable information
(PII) in an Amazon S3 bucket. The company uses server-side encryption with
S3 managed encryption keys (SSE-S3) to encrypt the objects. According to a
new requirement, all current and future objects in the S3 bucket must be
encrypted by keys that the company’s security team manages. The S3 bucket
does not have versioning enabled.
Which solution will meet these requirements?
A. In the S3 bucket properties, change the default encryption to SSE-S3
with a customer managed key. Use the AWS CLI to re-upload all objects in the
S3 bucket. Set an S3 bucket policy to deny unencrypted PutObject requests.
B. In the S3 bucket properties, change the default encryption to server-
side encryption with AWS KMS managed encryption keys (SSE-KMS). Set an S3
bucket policy to deny unencrypted PutObject requests. Use the AWS CLI to re-
upload all objects in the S3 bucket.
C. In the S3 bucket properties, change the default encryption to server-
side encryption with AWS KMS managed encryption keys (SSE-KMS). Set an S3
bucket policy to automatically encrypt objects on GetObject and PutObject
requests.
D. In the S3 bucket properties, change the default encryption to AES-256
with a customer managed key. Attach a policy to deny unencrypted PutObject
requests to any entities that access the S3 bucket. Use the AWS CLI to re-
upload all objects in the S3 bucket.
答案:B
答案解析:在S3桶属性中,使用AWS KMS管理的加密密钥(SSE-
KMS)将默认加密更改为服务器端加密。设置S3桶策略,拒绝未加密的PutObject请求。通过AWS
CLI重新上传S3桶中的所有对象。参考:https://docs.aws.amazon.com/AmazonS3/latest/userguide/UsingKMSEncryption.html
3 Parameter store
Parameter Store(AWS Systems Manager(SSM)
的一项功能)可提供安全的分层存储,用于配置数据管理和密钥管理。您可以将密码、数据库字符串、Amazon Machine Image (AMI) ID
和许可证代码等数据存储为参数值。可以将值存储为纯文本或加密数据。在考试中出现概率较高,重点关注其与Secrets manager的区别。
3.1 基本特性
- severless的服务,使用SDK调用API
- 可以自动结合KMS进行加密
- 有版本和追踪功能
- 能够触发CloudWatch Event
- 能够被CloudFormation中引用
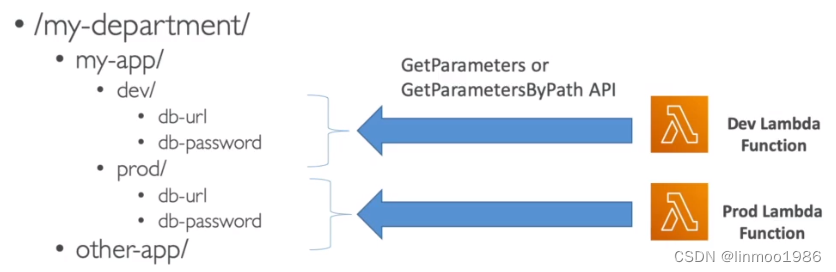
3.2 典型架构
- 开发环境和生产环境配置
4 AWS Secrets manager
AWS Secrets Manager,您可以在数据库凭证、应用程序凭证、OAuth 令牌、API
密钥和其他密钥的整个生命周期内对其进行管理、检索和轮换。许多 AWS 服务将密钥存储在 Secrets Manager
中。其加密也是可以与KMS自动结合。在考试中出现概率较高,重点关注其与Parameter store的区别。
4.1 基本特性
注意点(考试中与Parameter store区别,但出现下面2个应用需求时,基本上就选择Secrets manager ):
- 其能使用Lambda自动生成密钥,且能每隔一段时间将密钥轮转(出现密钥轮转,基本上就要选择Secrets manager,虽然Parameter store也能设计轮转但比较麻烦)
例题:A security engineer determined that an existing application retrieves
credentials to an Amazon RDS for MySQL database from an encrypted file in
Amazon S3. For the next version of the application, the security engineer
wants to implement the following application design changes to improve
security:
– The database must use strong, randomly generated passwords stored in a
secure AWS managed service.
– The application resources must be deployed through AWS CloudFormation.
– The application must rotate credentials for the database every 90 days.
A solutions architect will generate a CloudFormation template to deploy the
application.
Which resources specified in the CloudFormation template will meet the
security engineer’s requirements with the LEAST amount of operational
overhead?
A. Generate the database password as a secret resource using AWS Secrets
Manager. Create an AWS Lambda function resource to rotate the database
password. Specify a Secrets Manager RotationSchedule resource to rotate the
database password every 90 days.
B. Generate the database password as a SecureString parameter type using
AWS Systems Manager Parameter Store. Create an AWS Lambda function resource
to rotate the database password. Specify a Parameter Store RotationSchedule
resource to rotate the database password every 90 days.
C. Generate the database password as a secret resource using AWS Secrets
Manager. Create an AWS Lambda function resource to rotate the database
password. Create an Amazon EventBridge scheduled rule resource to trigger
the Lambda function password rotation every 90 days.
D. Generate the database password as a SecureString parameter type using
AWS Systems Manager Parameter Store. Specify an AWS AppSync DataSource
resource to automatically rotate the database password every 90 days.
答案:A
答案解析:题目关键词:randomly generated passwords, rotate
credentials。B选项和D选项对于轮换密钥过复杂,因此只能选择A选项或者C选项;而设置RotationSchedule做自动轮转不需要EventBridge,因此答案为A
A company has Linux-based Amazon EC2 instances. Users must access the
instances by using SSH with EC2 SSH key pairs. Each machine requires a
unique EC2 key pair.
The company wants to implement a key rotation policy that will, upon
request, automatically rotate all the EC2 key pairs and keep the keys in a
securely encrypted place. The company will accept less than 1 minute of
downtime during key rotation.
Which solution will meet these requirements?
A. Store all the keys in AWS Secrets Manager. Define a Secrets Manager
rotation schedule to invoke an AWS Lambda function to generate new key
pairs. Replace public keys on EC2 instances. Update the private keys in
Secrets Manager.
B. Store all the keys in Parameter Store, a capability of AWS Systems
Manager, as a string. Define a Systems Manager maintenance window to invoke
an AWS Lambda function to generate new key pairs. Replace public keys on EC2
instances. Update the private keys in Parameter Store.
C. Import the EC2 key pairs into AWS Key Management Service (AWS KMS).
Configure automatic key rotation for these key pairs. Create an Amazon
EventBridge scheduled rule to invoke an AWS Lambda function to initiate the
key rotation in AWS KMS.
D. Add all the EC2 instances to Fleet Manager, a capability of AWS Systems
Manager. Define a Systems Manager maintenance window to issue a Systems
Manager Run Command document to generate new key pairs and to rotate public
keys to all the instances in Fleet Manager.
答案:A答案解析:题目要求维护一批EC2的不同密钥,且自动轮转密钥,轮转期间少于1分钟。参考:https://aws.amazon.com/blogs/security/how-
to-use-aws-secrets-manager-securely-store-rotate-ssh-key-
pairs/。A选项整个过程不需要手动生成密钥。
- 与RDS深度结合
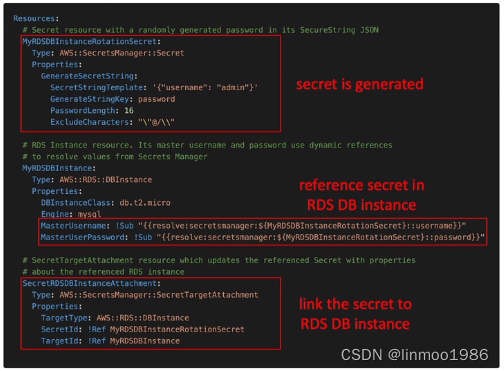
4.2 典型架构
-
与CloudFormation集成
-
跨账号共享Secrets
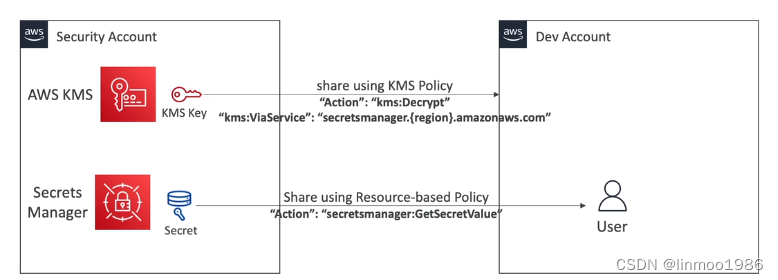
5 AWS Certificate manager(ACM)
AWS Certificate Manager (ACM) 处理创建、存储和续订公有及私有 SSL/TLS X.509
证书和密钥的复杂操作,这些证书和密钥可保护您的AWS网站和应用程序。您可以直接通过 ACM 签发证书,或者通过将第三方证书导入 ACM
管理系统中,为集成AWS服务提供证书。很明显,它是一个SSL/TLS X.509
证书和密钥的管理平台,要真正弄清楚ACM,我们先要弄清楚几个内容:SSL/TLS、SNI、DNSSEC。
5.1 SSL/TLS、SNI、DNSSEC
5.1.1 SSL/TLS
网络传输中,如果我们使用HTTP传输,其实是不安全的,因此需要加密。而SSL/TLS(安全套接层/传输套接层)是Netscape公司率先采用的网络安全协议。它是在传输通信协议(TCP/IP)上实现的一种安全协议,采用公开密钥技术。也就是说通过SSL/TLS可实现加密,HTTPS就是通过SSL/TLS技术实现安全加密。加密原理如下:
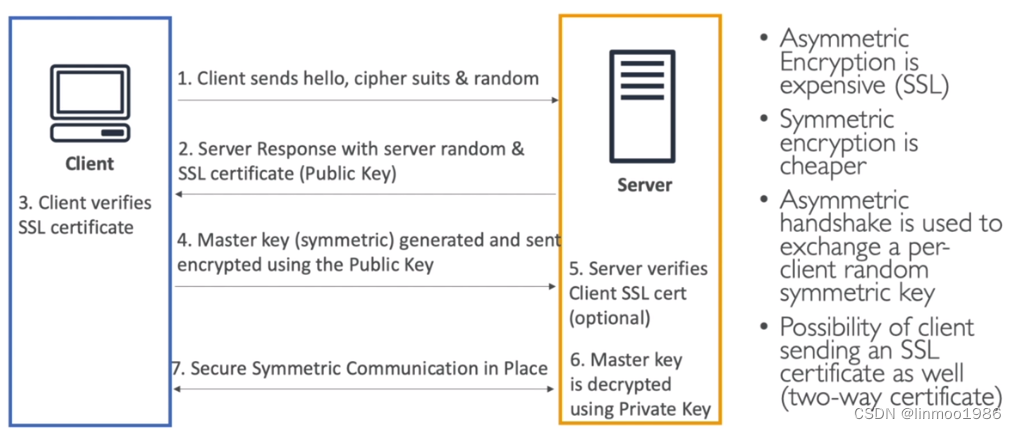
5.1.2 SNI
从4.1.1图中知道加密需要一个叫SSL Certificate,也就是所谓的安全证书。SNI的作用就是可以在同一个web服务器中实现多个SSL
Certificate,AWS的负载均衡服务ALB和NLB都有此功能,但CLB不具备。
5.1.3 DNSSEC
下图是一个“Man-in-the-MiddleAttack(中间人攻击)”,以及通过SSL加密后防止的原理:
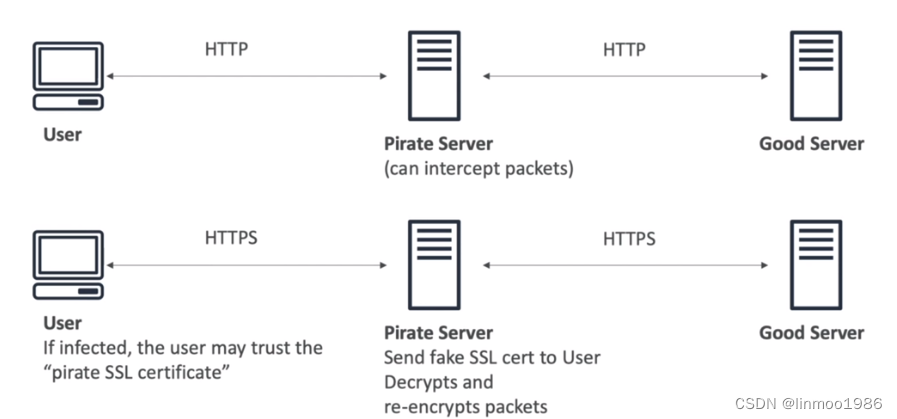
除了使用SSL外,还有一种可以放在这种中间人攻击,那就是DNSSEC,但是AWS Route53不支持DNSSEC,除非你使用第三方的DNS 。
5.2 基本特性
- 管理和颁发Certificate的AWS服务
- 可以与多个组件集成(ELB、CloudFormation、API gateway等)
- 公有证书:必须使用符合 DNS 的主题名称
- 私有证书:CA 可能位于您的账户中,也可能由其他账户与您共享
- 证书更新可以托给ACM管理
- 只是一个单区域的,不能跨区域
6 AWS CloudHSM
AWS CloudHSM将AWS云的优势与硬件安全模块 (HSM) 的安全性相结合。硬件安全模块 (HSM)
是一种计算设备,可处理加密操作并提供加密密钥的安全存储。借助AWS CloudHSM,您可以完全控制 AWS 云中的高可用性
HSM,这些密码具有低延迟访问权限,并拥有可自动执行 HSM
管理(包括备份、配置、配置和维护)的安全信任根。简单来说就是一个硬件版本的KMS。主要记住以下几点特性和与KMS的比较即可
6.1 基本特性
- 是一个基于硬件的加密工具
- 支持对称和非对称加密
- 密钥需要自己管理,不能托管AWS
- 可以部署多可用区集群
- 必须使用CloudHSM Client Software
- 不是免费的(注意:考试中出现过S3存储加密,有SSE-S3和CloudHSM的选择,CloudHSM是收费的,并非开销最小的选择 )
6.2 与KMS比较

7 AWS Inspector
Amazon Inspector 是一项漏洞管理服务,持续扫描您的AWS工作负载中是否存在软件漏洞和意外网络暴露。Amazon Inspector
会自动发现和扫描正在运行的 Amazon EC2 实例、亚马逊Elastic Container Registry (Amazon ECR)
中的容器映像,以及针对已知软件漏洞和意外网络泄露的AWS Lambda函数。这里只需要记住以下几点:
- 它只用于EC2、ECR和Lambda的漏洞扫描即可
- 漏洞规则是AWS管理的
- 最后生成报告
8 Amazon GuardDuty
Amazon GuardDuty 是一项安全监控服务,用于分析和处理AWS CloudTrail管理事件基础数据源、AWS
CloudTrail事件日志、VPC 流日志(来自 Amazon EC2 实例)和 DNS 日志。它还处理 Kubernetes 审计日志、RDS
登录活动、S3 日志、EBS 卷、运行时监控和 Lambda
网络活动日志等功能。简单理解就是一个安全监测工具,将通过一些日志作为输入,然后通过机器学习等算法分析出存在异常的内容,再通过CloudWatch发出警告。
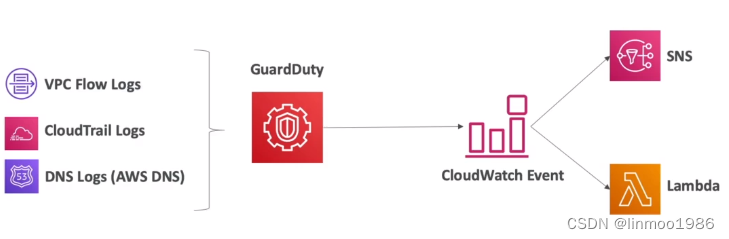
9 AWS Systems Manager(SSM)
AWS Systems Manager 是您 AWS
应用程序和资源的操作中心,也是混合和多云环境的安全端到端管理解决方案,可以实现大规模的安全操作。简单理解就是一个可以对你的EC2、本地数据中心的服务器的操作系统做管理的平台。
9.1 特性
- 管理你的EC2或者本地数据中心的服务器
- 发现你基础设施存在的安全问题
- 可以更新你服务器的补丁(注意:考试中遇到patching,基本上就是与SSM相关 )
A Solutions Architect must establish a patching plan for a large mixed fleet
of Windows and Linux servers.The patching plan must be implemented securely,
be audit ready, and comply with the company’s business requirements. Which
option will meet these requirements with MINIMAL effort?
A. Install and use an OS-native patching service to manage the update
frequency and release approval for all instances.Use AWS Config to verify
the OS state on each instance and report on any patch compliance issues
B. Use AWS Systems Manager on all instances to manage patching. Test
patches outside of production and then deployduring a maintenance window
with the appropriate approval.
C. Use AWS OpsWorks for Chef Automate to run a set of scripts that will
iterate through all instances of a given typessue the appropriate OS command
to get and install updates on each instance, including any required restarts
during themaintenance window.
D. Migrate all applications to AWS Ops Works and use Ops Works automatic
patching support to keep the OS up-to-datefollowing the initial
installation. Use AWS Config to provide audit and compliance reporting.
答案:B
答案解析:这道题关键词:Windows and Linux servers,patching plan,MINIMAL effort。主要考察AWS
Config、Systems Manager、OpsWorks的使用场景。AWS
Config主要是配置管理,OpsWorks也有更新补丁功能,是Puppet 或 Chef迁移到AWS云上使用,但是AWS如果不强调Puppet 或
Chef迁移,补丁修复建议都是使用Systems
Manager(https://docs.aws.amazon.com/zh_cn/opsworks/latest/userguide/workingsecurity-
updates.html)。而Systems Manager其中一个重要功能就是更新服务器补丁。因此选B。
例题:A company needs to implement a patching process for its servers. The on-
premises servers and Amazon EC2 instances use a variety of tools to perform
patching.
Management requires a single report showing the patch status of all the
servers and instances.
Which set of actions should a solutions architect take to meet these
requirements?
A. Use AWS Systems Manager to manage patches on the on-premises servers and
EC2 instances. Use Systems Manager to generate patch compliance reports
B. Use AWS OpsWorks to manage patches on the on-premises servers and EC2
instances. Use Amazon QuickSight integration with OpsWorks to generate patch
compliance reports.
C. Use an Amazon EventBridge (Amazon CloudWatch Events) rule to apply
patches by scheduling an AWS Systems Manager patch remediation job. Use
Amazon Inspector to generate patch compliance reports.
D. Use AWS OpsWorks to manage patches on the on-premises servers and EC2
instances. Use AWS X-Ray to post the patch status to AWS Systems Manager
OpsCenter to generate patch compliance reports.
答案:A答案解析:题目要求给本地和EC2更新补丁。OpsWorks是主要是做配置管理;EventBridge更多是应用程序组件连接在一起的bus。而Systems
Manager本身就有patching功能
- 适用于Windows和Linux OS
- 集成了CloudWatch metrics/dashboards/AWS Config
- Session Manager :可以管理 Amazon Elastic Compute Cloud(Amazon EC2)实例、边缘设备、本地服务器和虚拟机(VM)。您可使用基于浏览器的一键式交互 Shell 或 AWS Command Line Interface (AWS CLI)。Session Manager 提供安全且可审计的节点管理,而无需打开入站端口、维护堡垒主机或管理 SSH 密钥。
例题:A startup company hosts a fleet of Amazon EC2 instances in private
subnets using the latest Amazon Linux 2 AMI. The company’s engineers rely
heavily on SSH access to the instances for troubleshooting.
The company’s existing architecture includes the following:
– A VPC with private and public subnets, and a NAT gateway
– Site-to-Site VPN for connectivity with the on-premises environment
– EC2 security groups with direct SSH access from the on-premises
environment
The company needs to increase security controls around SSH access and
provide auditing of commands run by the engineers.
Which strategy should a solutions architect use?
A. Install and configure EC2 Instance Connect on the fleet of EC2
instances. Remove all security group rules attached to EC2 instances that
allow inbound TCP on port 22. Advise the engineers to remotely access the
instances by using the EC2 Instance Connect CLI.
B. Update the EC2 security groups to only allow inbound TCP on port 22 to
the IP addresses of the engineer’s devices. Install the Amazon CloudWatch
agent on all EC2 instances and send operating system audit logs to
CloudWatch Logs.
C. Update the EC2 security groups to only allow inbound TCP on port 22 to
the IP addresses of the engineer’s devices. Enable AWS Config for EC2
security group resource changes. Enable AWS Firewall Manager and apply a
security group policy that automatically remediates changes to rules.
D. Create an IAM role with the AmazonSSMManagedInstanceCore managed policy
attached. Attach the IAM role to all the EC2 instances. Remove all security
group rules attached to the EC2 instances that allow inbound TCP on port 22.
Have the engineers install the AWS Systems Manager Session Manager plugin
for their devices and remotely access the instances by using the start-
session API call from Systems Manager
答案:D
答案解析:题目要求管理SSH登录,最好的就是使用Systems Manager的Session
Manager方案,参考:https://docs.aws.amazon.com//systems-
manager/latest/userguide/session-manager.html
例题:A research company is running daily simulations in the AWS Cloud to meet
high demand. The simulations run on several hundred Amazon EC2 instances
that are based on Amazon Linux 2. Occasionally, a simulation gets stuck and
requires a cloud operations engineer to solve the problem by connecting to
an EC2 instance through SSH.
Company policy states that no EC2 instance can use the same SSH key and
that all connections must be logged in AWS CloudTrail.
How can a solutions architect meet these requirements?
A. Launch new EC2 instances, and generate an individual SSH key for each
instance. Store the SSH key in AWS Secrets Manager. Create a new IAM policy,
and attach it to the engineers’ IAM role with an Allow statement for the
GetSecretValue action. Instruct the engineers to fetch the SSH key from
Secrets Manager when they connect through any SSH client.
B. Create an AWS Systems Manager document to run commands on EC2 instances
to set a new unique SSH key. Create a new IAM policy, and attach it to the
engineers’ IAM role with an Allow statement to run Systems Manager
documents. Instruct the engineers to run the document to set an SSH key and
to connect through any SSH client.
C. Launch new EC2 instances without setting up any SSH key for the
instances. Set up EC2 Instance Connect on each instance. Create a new IAM
policy, and attach it to the engineers’ IAM role with an Allow statement for
the SendSSHPublicKey action. Instruct the engineers to connect to the
instance by using a browser-based SSH client from the EC2 console.
D. Set up AWS Secrets Manager to store the EC2 SSH key. Create a new AWS
Lambda function to create a new SSH key and to call AWS Systems Manager
Session Manager to set the SSH key on the EC2 instance. Configure Secrets
Manager to use the Lambda function for automatic rotation once daily.
Instruct the engineers to fetch the SSH key from Secrets Manager when they
connect through any SSH client.
答案:D
答案解析:要求不需要使用SSH直接登录,那么使用Systems Manager的Session
Manager方案是最好的方案,参考:https://docs.aws.amazon.com//systems-
manager/latest/userguide/session-manager.html
例题:A company’s AWS architecture currently uses access keys and secret access
keys stored on each instance to access AWS services. Database credentials
are hard-coded on each instance. SSH keys for command-line remote access are
stored in a secured Amazon S3 bucket. The company has asked its solutions
architect to improve the security posture of the architecture without adding
operational complexity.
Which combination of steps should the solutions architect take to
accomplish this? (Choose three.)
A. Use Amazon EC2 instance profiles with an IAM role
B. Use AWS Secrets Manager to store access keys and secret access keys
C. Use AWS Systems Manager Parameter Store to store database credentials
D. Use a secure fleet of Amazon EC2 bastion hosts for remote access
E. Use AWS KMS to store database credentials
F. Use AWS Systems Manager Session Manager for remote access
答案:ACF
答案解析:题目要改进安全访问EC2方式。因此使用Systems Manager Session Manager是最合适,因此步骤是ACF。
学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:
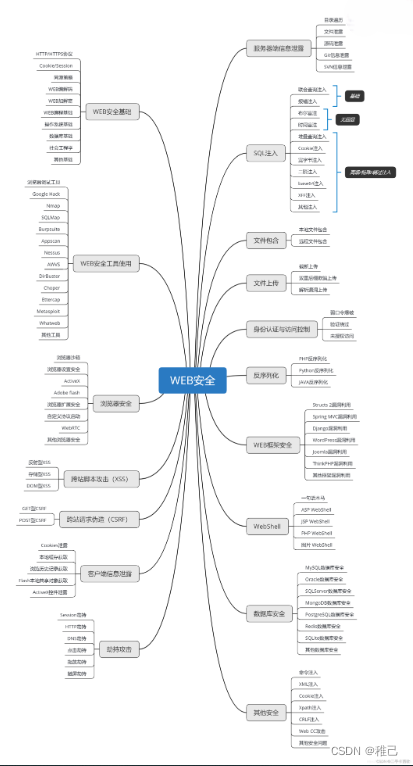
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)

一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
最合适,因此步骤是ACF。
学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:

网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)
[外链图片转存中…(img-5Xo6kGLk-1713116924487)]
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
学习网络安全技术的方法无非三种:
第一种是报网络安全专业,现在叫网络空间安全专业,主要专业课程:程序设计、计算机组成原理原理、数据结构、操作系统原理、数据库系统、 计算机网络、人工智能、自然语言处理、社会计算、网络安全法律法规、网络安全、内容安全、数字取证、机器学习,多媒体技术,信息检索、舆情分析等。
第二种是自学,就是在网上找资源、找教程,或者是想办法认识一-些大佬,抱紧大腿,不过这种方法很耗时间,而且学习没有规划,可能很长一段时间感觉自己没有进步,容易劝退。
如果你对网络安全入门感兴趣,那么你需要的话可以点击这里👉网络安全重磅福利:入门&进阶全套282G学习资源包免费分享!
第三种就是去找培训。
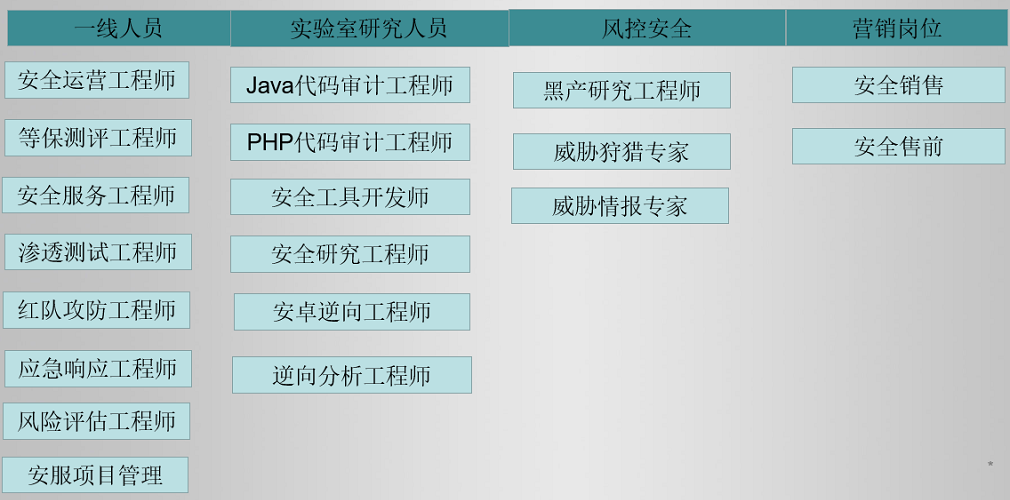
接下来,我会教你零基础入门快速入门上手网络安全。
网络安全入门到底是先学编程还是先学计算机基础?这是一个争议比较大的问题,有的人会建议先学编程,而有的人会建议先学计算机基础,其实这都是要学的。而且这些对学习网络安全来说非常重要。但是对于完全零基础的人来说又或者急于转行的人来说,学习编程或者计算机基础对他们来说都有一定的难度,并且花费时间太长。
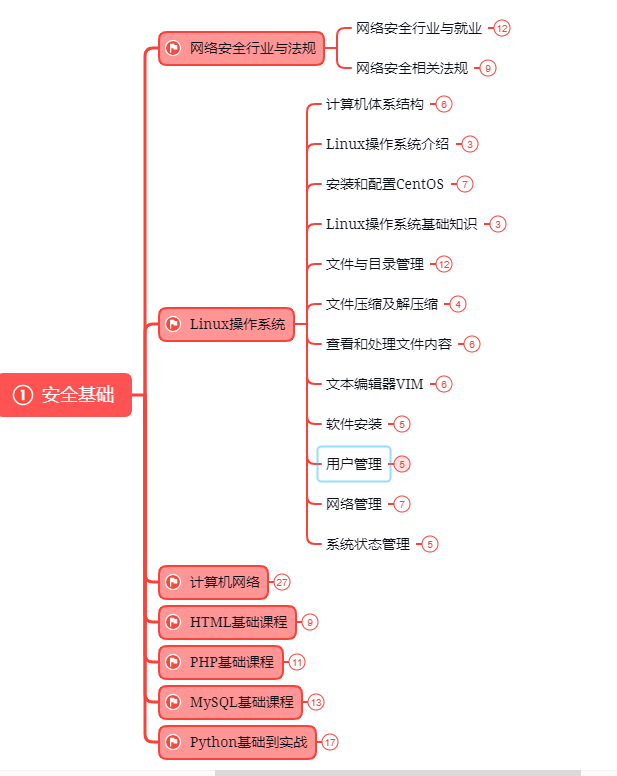
第一阶段:基础准备 4周~6周
这个阶段是所有准备进入安全行业必学的部分,俗话说:基础不劳,地动山摇
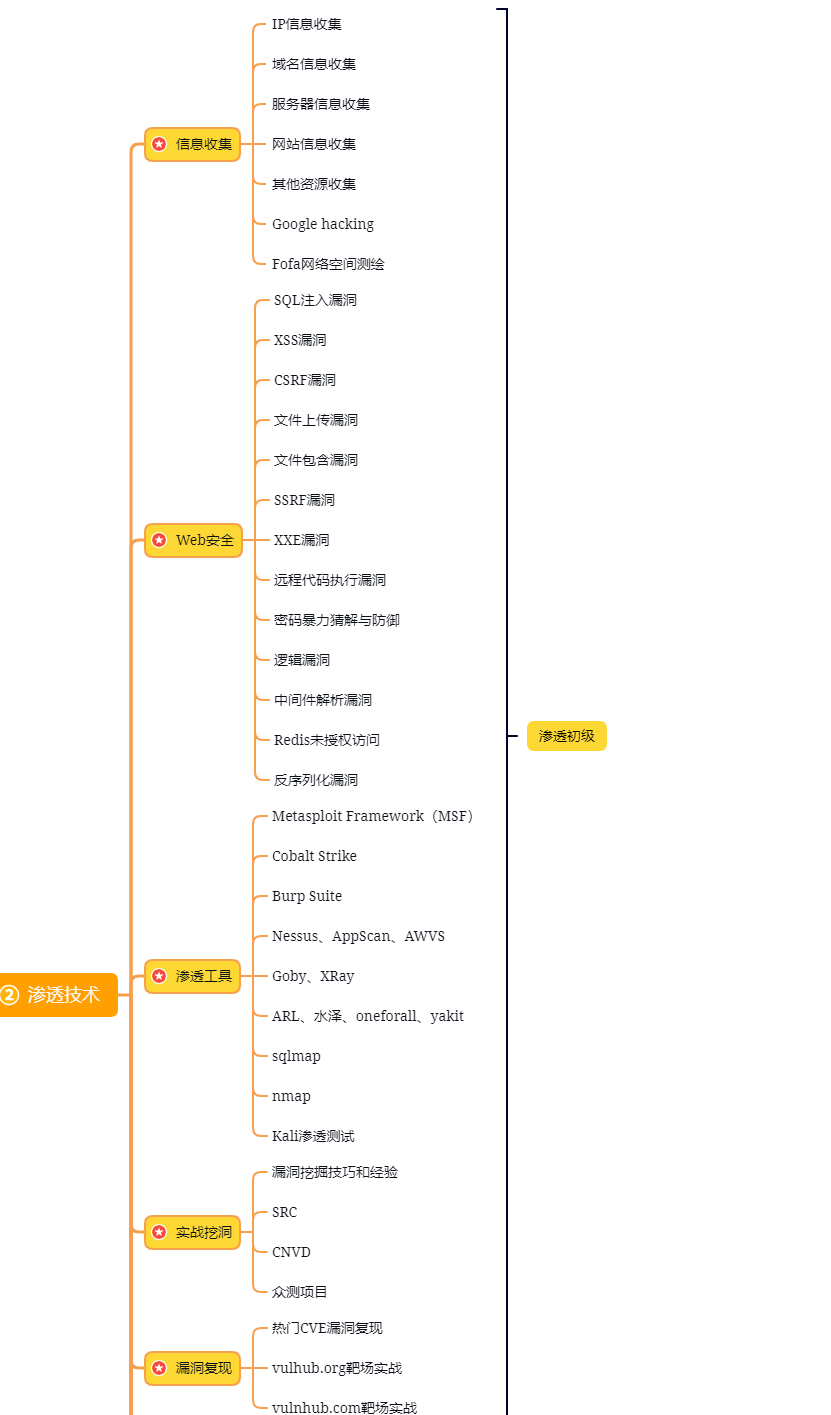
第二阶段:web渗透
学习基础 时间:1周 ~ 2周:
① 了解基本概念:(SQL注入、XSS、上传、CSRF、一句话木马、等)为之后的WEB渗透测试打下基础。
② 查看一些论坛的一些Web渗透,学一学案例的思路,每一个站点都不一样,所以思路是主要的。
③ 学会提问的艺术,如果遇到不懂得要善于提问。
配置渗透环境 时间:3周 ~ 4周:
① 了解渗透测试常用的工具,例如(AWVS、SQLMAP、NMAP、BURP、中国菜刀等)。
② 下载这些工具无后门版本并且安装到计算机上。
③ 了解这些工具的使用场景,懂得基本的使用,推荐在Google上查找。
渗透实战操作 时间:约6周:
① 在网上搜索渗透实战案例,深入了解SQL注入、文件上传、解析漏洞等在实战中的使用。
② 自己搭建漏洞环境测试,推荐DWVA,SQLi-labs,Upload-labs,bWAPP。
③ 懂得渗透测试的阶段,每一个阶段需要做那些动作:例如PTES渗透测试执行标准。
④ 深入研究手工SQL注入,寻找绕过waf的方法,制作自己的脚本。
⑤ 研究文件上传的原理,如何进行截断、双重后缀欺骗(IIS、PHP)、解析漏洞利用(IIS、Nignix、Apache)等,参照:上传攻击框架。
⑥ 了解XSS形成原理和种类,在DWVA中进行实践,使用一个含有XSS漏洞的cms,安装安全狗等进行测试。
⑦ 了解一句话木马,并尝试编写过狗一句话。
⑧ 研究在Windows和Linux下的提升权限,Google关键词:提权
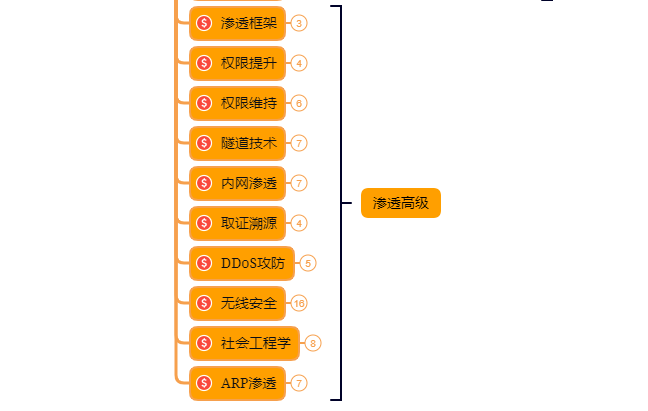
以上就是入门阶段
第三阶段:进阶
已经入门并且找到工作之后又该怎么进阶?详情看下图
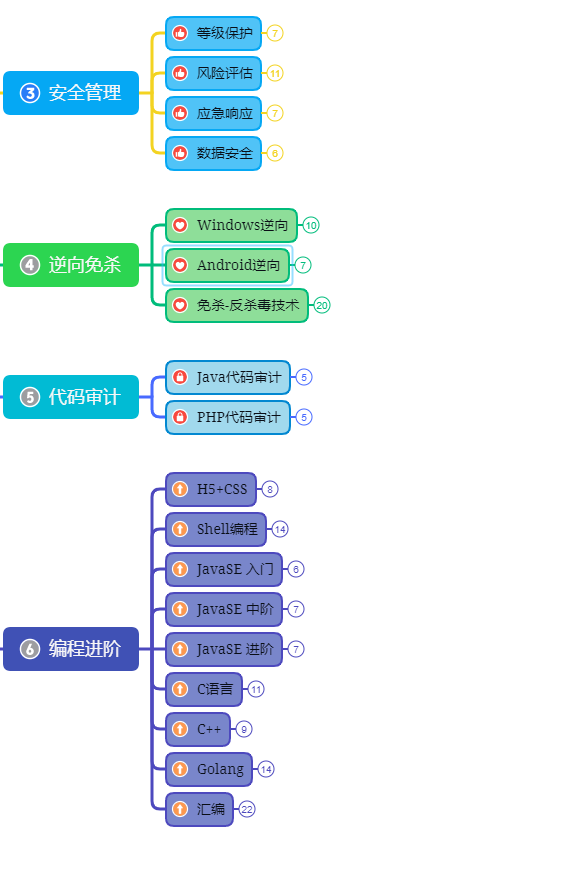
给新手小白的入门建议:
新手入门学习最好还是从视频入手进行学习,视频的浅显易懂相比起晦涩的文字而言更容易吸收,这里我给大家准备了一套网络安全从入门到精通的视频学习资料包免费领取哦!
如果你对网络安全入门感兴趣,那么你需要的话可以点击这里👉网络安全重磅福利:入门&进阶全套282G学习资源包免费分享!






















 1296
1296

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








