Sunday , August 28 , 2016Dear Diary,
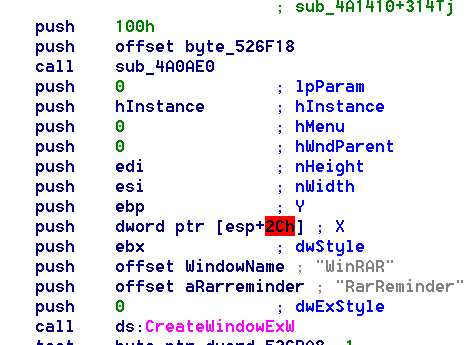
Since last month,I've been interested in ReverseEngineering(RE) and taught myself from the scratch.Now I have some progress and this is my first little challenge.I installed WinRar from a website this morning.It works good however,every time I open it ,an adds window will pop up and I have to close it.So I tried and succeeded to remove the pop-up window with what I learnt.Tools I used including IDA and Hiew.First,I noticed that the pop-up window has title of "WinRaR". So I loaded it with IDA and searched the string "WinRaR"(Serach->text).I find the "offset WindowName;' WinRaR ' ".Then I select the element "WindowName" and press X ,then I get a set of xfer to it.
So I loaded it with IDA and searched the string "WinRaR"(Serach->text).I find the "offset WindowName;' WinRaR ' ".Then I select the element "WindowName" and press X ,then I get a set of xfer to it. Inspected into these Address,I find two most suspicious code blocks.
Inspected into these Address,I find two most suspicious code blocks.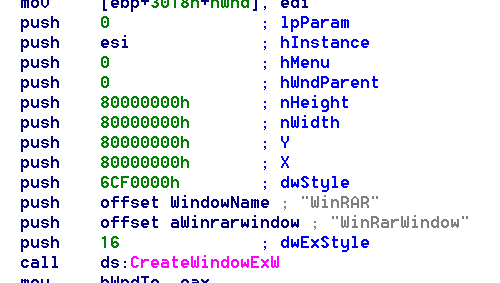 These two both call Windows API function"CreateWindowExW".Consulting the man pages I learnt that this function is used to create child windows like pop-up window.This is the very function I'm looking for.But,which of them pops adds?or both of them do the job?From the man pages we know that this function takes several parameters and the first one is dwExStyle which controls the extended style of the window.The two blocks differ on it.The former is 0 and the latter is 16.Due to the pop-up window is just a simple frame with a picture,I guess the zero one is what we wanted.Since I alreay got the target,the next thing need to do is to invalid this code block.Several approaches may make sense here.I can either replace the call instruction with NOP or simply make a jump to pass this function.Then I opened the file in Hiew and GoTo(F5) the target address 004A17DC.First I tried to replace the call instruction with several NOPs(I made backup just in case).
These two both call Windows API function"CreateWindowExW".Consulting the man pages I learnt that this function is used to create child windows like pop-up window.This is the very function I'm looking for.But,which of them pops adds?or both of them do the job?From the man pages we know that this function takes several parameters and the first one is dwExStyle which controls the extended style of the window.The two blocks differ on it.The former is 0 and the latter is 16.Due to the pop-up window is just a simple frame with a picture,I guess the zero one is what we wanted.Since I alreay got the target,the next thing need to do is to invalid this code block.Several approaches may make sense here.I can either replace the call instruction with NOP or simply make a jump to pass this function.Then I opened the file in Hiew and GoTo(F5) the target address 004A17DC.First I tried to replace the call instruction with several NOPs(I made backup just in case).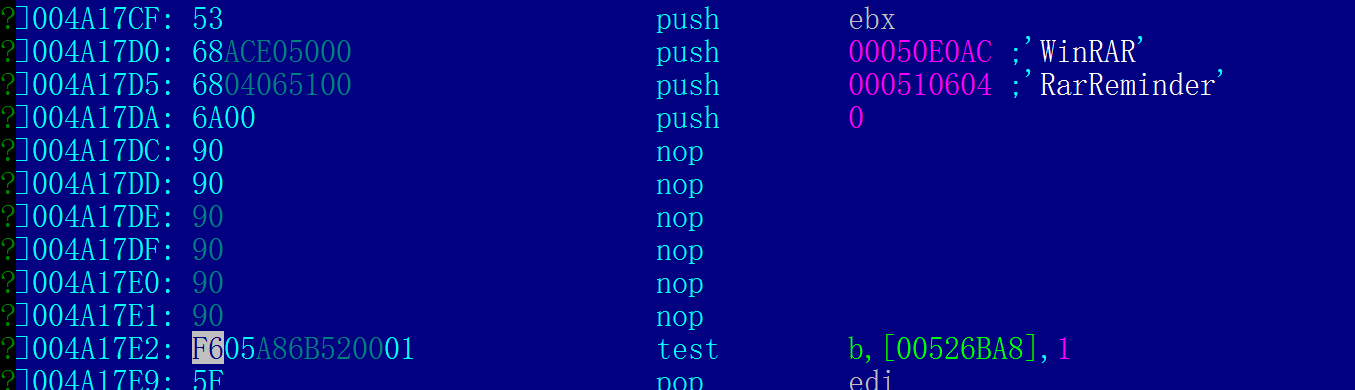 Save with F9 and we can see what happen.I opened the edited winrar.exe.Oh no,The file stops working and raised exception.But good news is that this time there was no adds window poped up."Keep going,you almost succeeded",I told myself.Then I looked into the assembly code in IDA again and found something new.After the "CreateWindowExW" API it called some other APIs like "SetWindowPos".
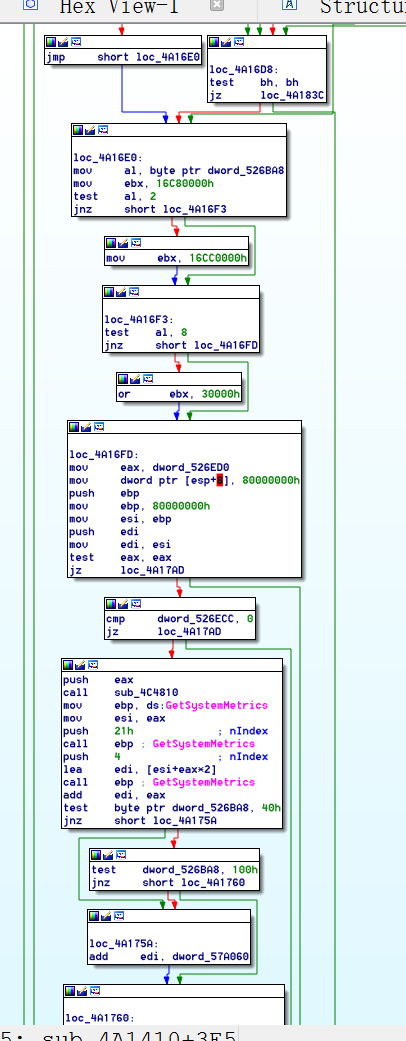
Save with F9 and we can see what happen.I opened the edited winrar.exe.Oh no,The file stops working and raised exception.But good news is that this time there was no adds window poped up."Keep going,you almost succeeded",I told myself.Then I looked into the assembly code in IDA again and found something new.After the "CreateWindowExW" API it called some other APIs like "SetWindowPos".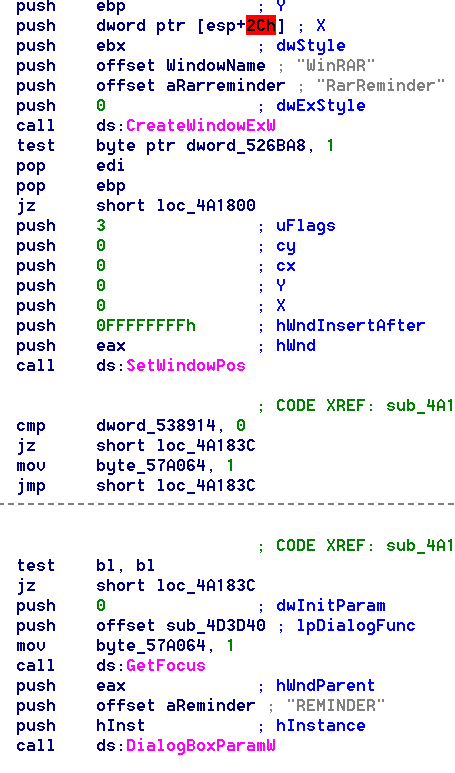 After consulting the man pages I realized that these API also affected the pop-up window created by "CreateWindowExW".When I invalid the "Create" function,these functions cited a non-existent object and then,exception occurred.Figured out the question,I am supposed to make the solution.Thanks to the Graph view provided by IDA,I found that all the APIs related to the pop-up window started from loc_4A16E0 and terminated in loc_4A183C.
After consulting the man pages I realized that these API also affected the pop-up window created by "CreateWindowExW".When I invalid the "Create" function,these functions cited a non-existent object and then,exception occurred.Figured out the question,I am supposed to make the solution.Thanks to the Graph view provided by IDA,I found that all the APIs related to the pop-up window started from loc_4A16E0 and terminated in loc_4A183C.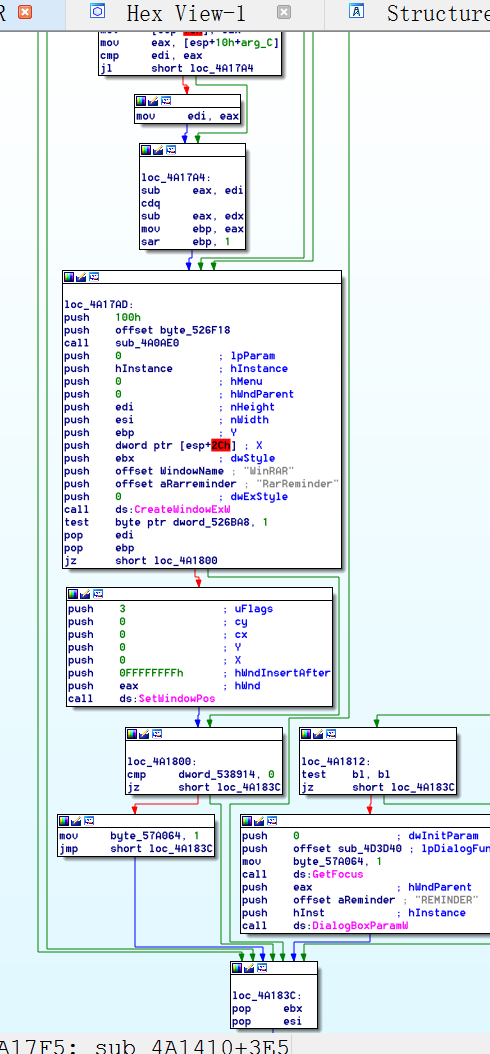 As is shown in the graph,there many conditional jumps like jz and jl.After some time of analysis,I find a route to avoid block loc_4A16E0.All I need to do is to change the jz loc_4A183C on address 004A16DA to jmp loc_4A183C and the jnz short loc_4A16D8 on 004A16C0 to jmp short loc_4A16D8 and the jz short loc_4A16E0 on 004A16D6 to jmp short loc_4A16D8.
As is shown in the graph,there many conditional jumps like jz and jl.After some time of analysis,I find a route to avoid block loc_4A16E0.All I need to do is to change the jz loc_4A183C on address 004A16DA to jmp loc_4A183C and the jnz short loc_4A16D8 on 004A16C0 to jmp short loc_4A16D8 and the jz short loc_4A16E0 on 004A16D6 to jmp short loc_4A16D8.
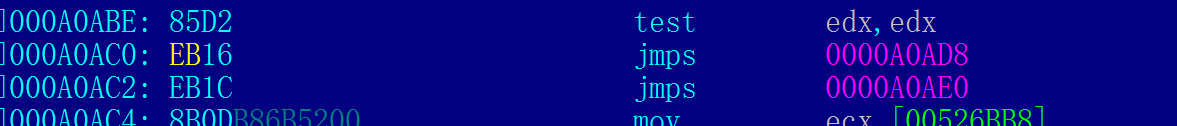 When this done,let's check our product.HAHA,the WinRaR started as expected without the pop-up adds window,I succeeded :DThis may be a piece of cake for you professional guys,but for me,it's the first and an important step,LOL.
When this done,let's check our product.HAHA,the WinRaR started as expected without the pop-up adds window,I succeeded :DThis may be a piece of cake for you professional guys,but for me,it's the first and an important step,LOL.
Thx for Reading!:)
评论


 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?
查看更多评论

添加红包