这几天公司业务上需要使用到CAS单点登录,于是自己动手做了一个简易的小例子。
一、环境:
1.tomcat-7.0.70
2.jdk1.7.0_79
3.CAS Server版本 : 4.0.0(https://www.apereo.org/projects/cas/download-cas)4.CAS Client版本:3.3.3(http://developer.jasig.org/cas-clients/)
二、创建证书
这里使用的是本机上安装的JDK自带的keytool工具生成证书。
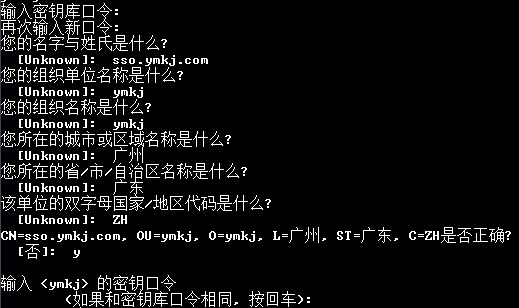
生成证书命令:keytool -genkey -alias ymkj -keyalg RSA -keystore d:/key/ymkjkey(先已手动创建了D盘下key文件夹)
三、导出证书
导出证书命令:D:\keys>keytool -export -file d:/key/ymkj.crt -alias ymkj -keystore d:/key/ymkjkey
四、为客户端JVM导入证书
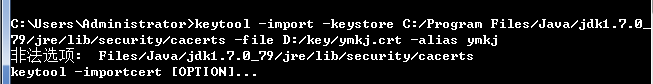
命令:keytool -import -keystore C:\Java\jdk1.7.0_79\jre\lib\security\cacerts -file d:/key/ymkj.crt -alias ymkj
注意,因为通常情况下JDK是安装在C:\Program Files目录下,所以会出现这样的问题:
因此,故将C:\Program Files目录下的JAVA文件夹拷贝到C盘目录下,再更新环境变量JAVA_HOME、JRE_HOME为当前的路径。最后执行导入证书命令并信任这个认证(输入y)。
如果提示:
keytool error: java.io.IOException: Keystore was tampered with, or password was incorrect,那么输入密码:changeit
这是因为JDK安装后会默认创建一个密钥库,密码为:changeit
五、应用证书到tomcat
打开tomcat目录的conf/server.xml文件,找到:
<!--
<Connector port="8443" protocol="org.apache.coyote.http11.Http11Protocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" />
-->修改为:
<Connector SSLEnabled="true" clientAuth="false"
keystoreFile="D:/key/ymkjkey"
keystorePass="123456" <!--创建证书时输入的密码-->
maxThreads="150" port="8443"
protocol="org.apache.coyote.http11.Http11Protocol"
scheme="https" secure="true" sslProtocol="TLS"/>
六、配置CAS Server
可在网上下载 cas-server-webapp-4.0.0.war文件,然后改名为cas.war,然后复制cas到tomcat/webapps目录下
七、配置域名
在C:\Windows\System32\drivers\etc\hosts内,添加:
127.0.0.1 sso.ymkj.com
127.0.0.1 sso.ymkj1.com
127.0.0.1 sso.ymkj2.com
第一个用于 CAS Server,第二个和第三个将用于CAS Client1和CAS Client2
八、运行
访问CAS应用了,要使用HTTPS加密协议访问,
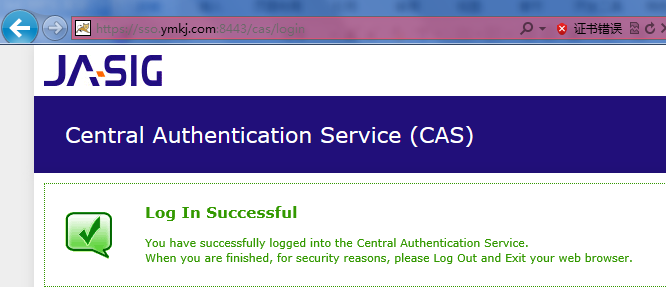
1.在地址栏输入:https://sso.ymkj.com:8443/cas/login
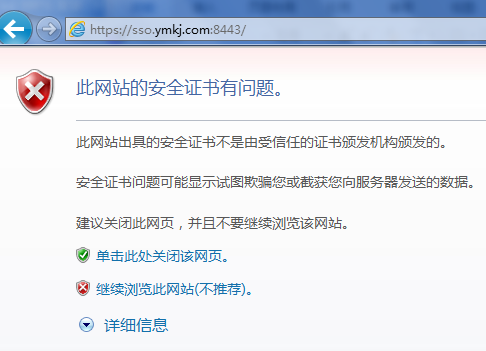
2.点击继续浏览,输入CAS Server 4.0.0默认的登录名和密码casuser /Mellon :
4.如果需要退出,地址栏输入: https://sso.ymkj.com:8443/cas/logout
至此,CAS Server 配置初步完成。
九、配置客户端
1.下载两个tomcat,改名为tomcat-ym1,tomcat-ym2
2.增加新环境变量CATALINA_HOME1,CATALINA_HOME1,以及CATALINA_BASE1, CATALINA_BASE2,值分别为两个新的tomcat的地址
3.修改tomcat-ym1,tomcat-ym2中的startup.bat,把其中所有的CATALINA_HOME改为 相应的CATALINA_HOME1,CATALINA_HOME2。
4.修改tomcat-ym1,tomcat-ym2中的catalina.bat,把其中所有的CATALINA_HOME改为相应的CATALINA_HOME1,CATALINA_HOME2。CATALINA_BASE改为相应的CATALINA_BASE1,CATALINA_BASE2。
5.修改tomcat的端口(5处)
在tomcat-ym1,tomcat-ym2中的conf/server.xml文件中找到如下3处内容:
<Server port="8005" shutdown="SHUTDOWN">、
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="8443" />、
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443" />,
分别改为:
<Serverport="18005" shutdown="SHUTDOWN">
<Connectorport="18080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="18443" />
<Connectorport="18009" protocol="AJP/1.3"redirectPort="18443" /><Serverport="28005" shutdown="SHUTDOWN">
<Connectorport="28080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="28443" />
<Connectorport="28009" protocol="AJP/1.3"redirectPort="28443" />6.配置拦截器
在tomcat-ym1,tomcat-ym2中的webapps\root\WEB-INF\web.xml 中,分别添加:
<!-- ======================== start ======================== -->
<context-param>
<param-name>casServerLogoutUrl</param-name>
<param-value>https://sso.ymkj.com:8443/cas/login</param-value>
</context-param>
<listener>
<listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class>
</listener>
<filter>
<filter-name>CAS Single Sign Out Filter</filter-name>
<filter-class>org.jasig.cas.client.session.SingleSignOutFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Single Sign Out Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Filter</filter-name>
<filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class>
<init-param>
<param-name>casServerLoginUrl</param-name>
<param-value>https://sso.ymkj.com:8443/cas/login</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://sso.ymkj1.com:18080</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CAS Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Validation Filter</filter-name>
<filter-class>
org.jasig.cas.client.validation.Cas20ProxyReceivingTicketValidationFilter
</filter-class>
<init-param>
<param-name>casServerUrlPrefix</param-name>
<param-value>https://sso.ymkj.com:8443/cas</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://sso.ymkj1.com:18080</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CAS Validation Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<filter-class>
org.jasig.cas.client.util.HttpServletRequestWrapperFilter
</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<filter-class>org.jasig.cas.client.util.AssertionThreadLocalFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>和:
<!-- ======================== start ======================== -->
<context-param>
<param-name>casServerLogoutUrl</param-name>
<param-value>https://sso.ymkj.com:8443/cas/login</param-value>
</context-param>
<listener>
<listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class>
</listener>
<filter>
<filter-name>CAS Single Sign Out Filter</filter-name>
<filter-class>org.jasig.cas.client.session.SingleSignOutFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Single Sign Out Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Filter</filter-name>
<filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class>
<init-param>
<param-name>casServerLoginUrl</param-name>
<param-value>https://sso.ymkj.com:8443/cas/login</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://sso.ymkj2.com:28080</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CAS Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Validation Filter</filter-name>
<filter-class>
org.jasig.cas.client.validation.Cas20ProxyReceivingTicketValidationFilter
</filter-class>
<init-param>
<param-name>casServerUrlPrefix</param-name>
<param-value>https://sso.ymkj.com:8443/cas</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://sso.ymkj2.com:28080</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CAS Validation Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<filter-class>
org.jasig.cas.client.util.HttpServletRequestWrapperFilter
</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<filter>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<filter-class>org.jasig.cas.client.util.AssertionThreadLocalFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>7.添加jar包
下载cas-client-3.3.3,解压之后将modules目录下的jar包根据自身情况拷入到tomcat-ym1\webapps\ROOT\WEB-INF\lib里(我是选择全部拷入)和tomcat-ym2\webapps\ROOT\WEB-INF\lib里。
十、通过数据库验证登录
我使用的是MySQL数据库:
1、需要的jar包有cas-server-support-jdbc.jar,mysql-connector-java-5.1.24, c3p0-0.9.1.2.jar,拷入到webapps\cas\WEB-INF\lib 中
2、在cas\WEB-INF下找到deployerConfigContext.xml进行修改:
注释掉:
<bean id="primaryAuthenticationHandler"
class="org.jasig.cas.authentication.AcceptUsersAuthenticationHandler">
<property name="users">
<map>
<entry key="casuser" value="Mellon"/>
</map>
</property>
</bean>添加:
<bean id="dataSource" class="com.mchange.v2.c3p0.ComboPooledDataSource"
p:driverClass="com.mysql.jdbc.Driver"
p:jdbcUrl="jdbc:mysql://localhost:3306/链接名?useUnicode=true&
characterEncoding=UTF-8&zeroDateTimeBehavior=convertToNull"
p:user=”数据库用户名”
p:password=”数据库密码”/>
<bean id="dbAuthHandler"
class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler">
<property name="sql" value="select password from user where username=?" />
<property name="dataSource" ref="dataSource" />
</bean> 再找到id=authenticationManager的bean,
<bean id="authenticationManager"
class="org.jasig.cas.authentication.PolicyBasedAuthenticationManager">
<constructor-arg>
<map>
<entry key-ref="proxyAuthenticationHandler"
value-ref="proxyPrincipalResolver" />
<!-- <entry key-ref="primaryAuthenticationHandler"
value-ref="primaryPrincipalResolver" />-->
<entry key-ref="dbAuthHandler"
value-ref="primaryPrincipalResolver"/>
</map>
</constructor-arg>
<property name="authenticationPolicy">
<bean class="org.jasig.cas.authentication.AnyAuthenticationPolicy" />
</property>
</bean> 是为了注释掉key-ref="primaryAuthenticationHandler"的部分,然后引入id=dbAuthHandler的bean。
3、重启tomcat 进行验证:打开tomcat-ym1,然后输入数据库user表中存储的用户名和密码:
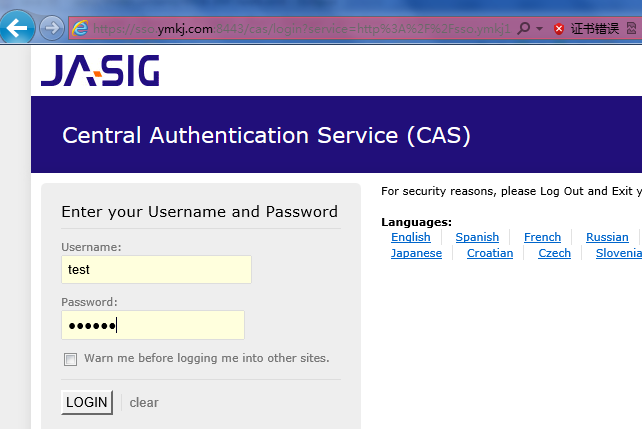
点击login,验证成功。
4.设置 tomcat-ym1 , tomcat-ym2的进入首页,代码为(另有css和其他的代码未贴出):
<h1>page 1 welcome you</h1>
<a href="http://sso.ymkj2.com:28080">to page 2----</a>
<a href="https://sso.ymkj.com:8443/cas/logout">-------logout</a>
和
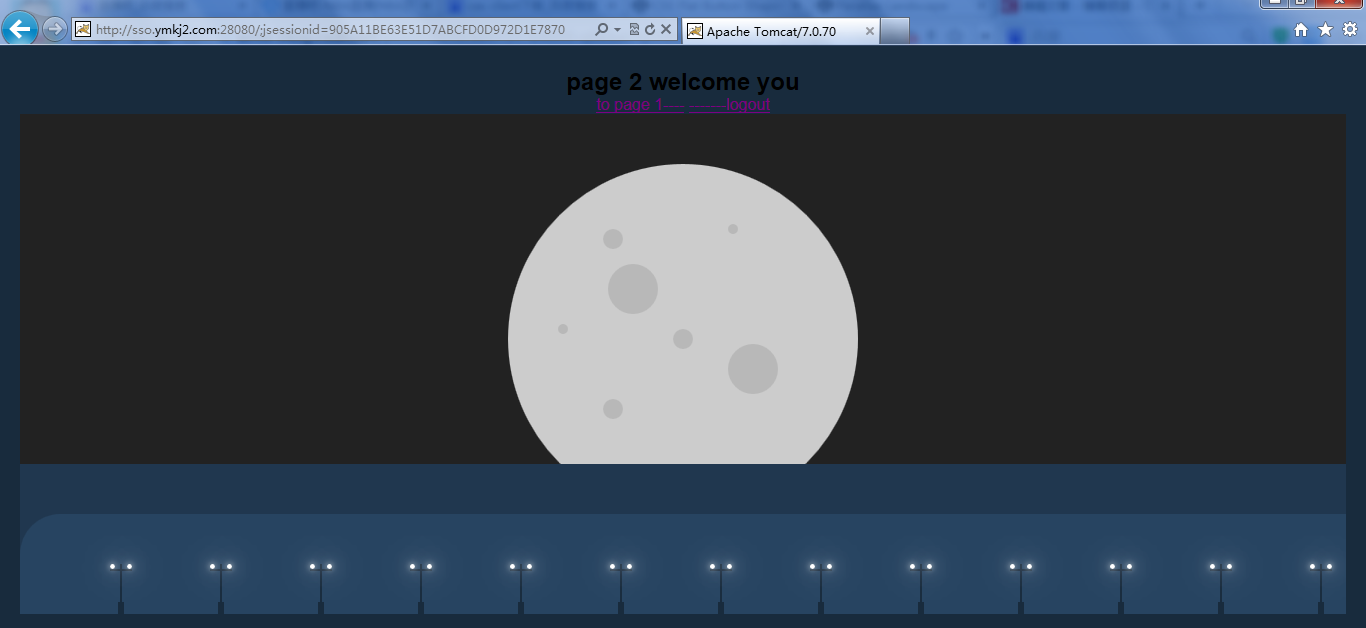
<h1>page 2 welcome you</h1>
<a href="http://sso.ymkj1.com:18080">to page 1----</a>
<a href="https://sso.ymkj.com:8443/cas/logout">-------logout</a> tomcat-ym1页面:
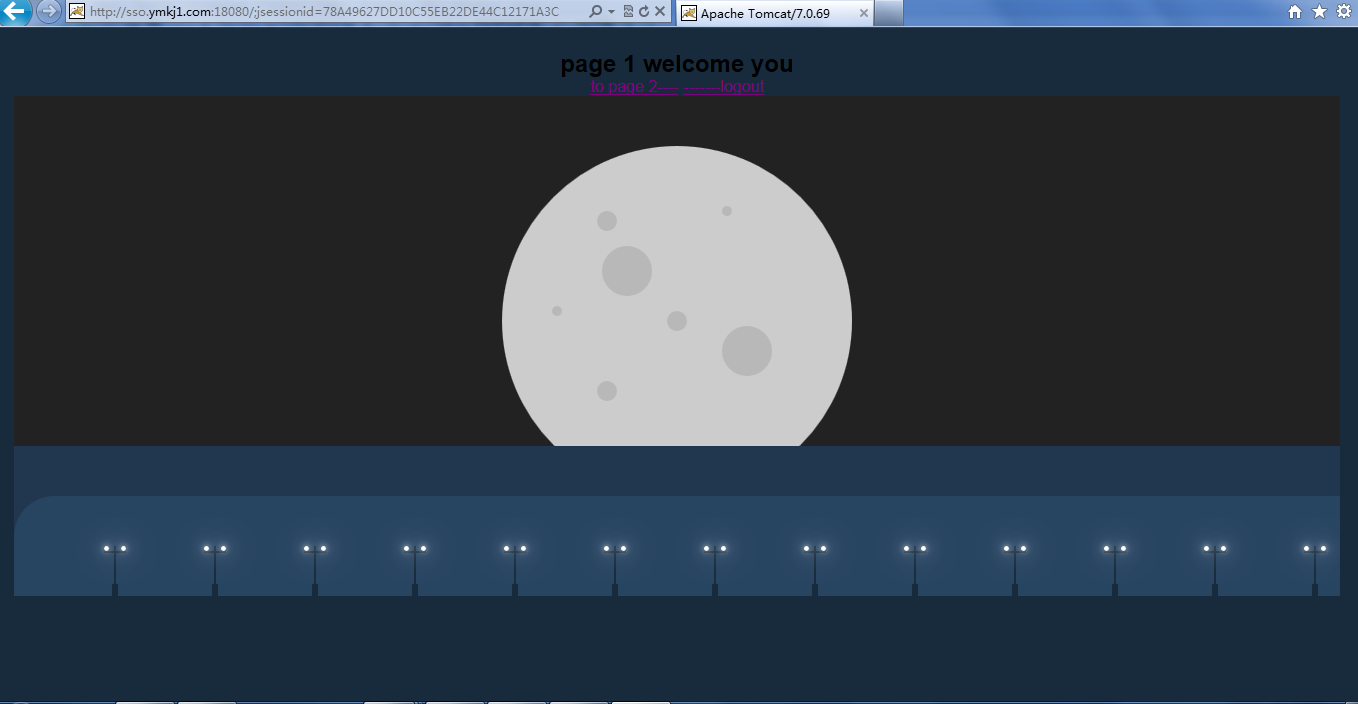
点击超链接跳转到tomcat-ym2:
至此,这个小例子就完成了~





















 3087
3087











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








