文章仅限于学习使用
本文目的是为本人自己写个自动申购脚本
工具=>ida, frida(未去任何特征) lsposed ,so文件arm64-v8a
1.抓包
MT-K:1695709652297
MT-V:939dfa68ffca7b27a8d74ef90ak
MT-Token:
User-Agent:""
MT-Device-ID:clips_KxIgEiZFcRAnE3cRJEUnQXUWJkUjQnVDdhIkESBDdQ==
MT-APP-Version:1.4.7
MT-Request-ID:4464accc-5945-4d91-a385-fdc6ca1c6bb2
MT-Network-Type:4G
MT-R:clips_OlU6TmFRag5rCXwbNAQ/Tz1SKlN8THcecBp/HGhHdw==
MT-Bundle-ID:com.xx.mall
MT-USER-TAG:0
MT-SN:clips_ehwpSC0fLBggRnJAdxYgFiAYLxl9Si5PfEl/TC0afkw=
MT-DTIME:Thu Feb 09 11:49:42 GMT+08:00 2099
MT-RS:1080*2230
MT-Lng:11111
MT-Lat:22222
BS-DVID:8_lNVOMEiEaCgDe4LbQ1qxWx2J6gvlqGYn-THKQLsXq2TMQBTkITqdTZexieOYtWQeNpnklr4kwdcAq-MVLGBBQ
MT-DOUBLE:0
MT-SIM:0
MT-ACBE:1
MT-ACB:1
MT-ACBM:0
Content-Type:application/json; charset=UTF-8
Content-Length:65
Host:app.xxx.com.cn
Connection:Keep-Alive
Accept-Encoding:gzip可以看到很多参数都是clips_xxx的形式,那么应该是同一个函数生成的,
MT-V盲猜md5?
2.反检测
想掏出frida去hook时,发现还是闪退,这个应该和patch某哩frida检测差不多,先看下是哪个so在作怪
function hook_dlopen() {
Interceptor.attach(Module.findExportByName(null, "android_dlopen_ext"),
{
onEnter: function (args) {
var pathptr = args[0];
if (pathptr !== undefined && pathptr != null) {
var path = ptr(pathptr).readCString();
console.log(path)
}
}
}
);
}android_dlopen_ext=> libwalkstack.so
android_dlopen_ext=> libstats_jni.so
android_dlopen_ext=> /system/framework/oat/arm64/org.apache.http.legacy.odex
android_dlopen_ext=> /data/app/~~ihvoegmu2xy8soMC5G20dg==/com.xxx.mall-RW8qb9WZaGAbaHrJU9xaQQ==/oat/arm64/base.odex
android_dlopen_ext=> libframework-connectivity-jni.so
android_dlopen_ext=> libforcedarkimpl.so
android_dlopen_ext=> /data/app/~~ihvoegmu2xy8soMC5G20dg==/com.xxx.mall-RW8qb9WZaGAbaHrJU9xaQQ==/lib/arm64/libbaiduprotect.so
Process terminated3.libbaiduprotect.so分析
hook下pthread_create
function hook_pthread_create() {
var libcModule = Process.findModuleByName('libc.so');
if (libcModule) {
var pthread_create = new NativeFunction(
libcModule.findExportByName('pthread_create'),
'int', ['pointer', 'pointer', 'pointer', 'pointer']
);
Interceptor.attach(pthread_create, {
onEnter: function (args) {
var libmsaoaidsecModule = Process.findModuleByName('libbaiduprotect.so');
if (libmsaoaidsecModule) {
// 在进入 pthread_create 之前
console.log("pthread_create called with arguments:");
console.log("attr:", args[0]);
console.log("attr:", (args[0] - libmsaoaidsecModule.base).toString(16));
console.log("start_routine:", args[1]);
console.log("arg:", args[2]);
console.log("function at=>0x"+(args[2] - libmsaoaidsecModule.base).toString(16));
console.log("pid:", args[3]);
console.log('----------------------------------------\n')
}
},
onLeave: function (retval) {
}
});
}
}
function hook_dlopen() {
var android_dlopen_ext = Module.findExportByName(null, "android_dlopen_ext");
Interceptor.attach(android_dlopen_ext, {
onEnter: function (args) {
this.call_hook = false;
var so_name = ptr(args[0]).readCString();
// console.log("android_dlopen_ext=>", so_name)
if(so_name!=null){
hook_pthread_create()
}
}, onLeave: function (retval) {
}
});
}
setImmediate(hook_dlopen);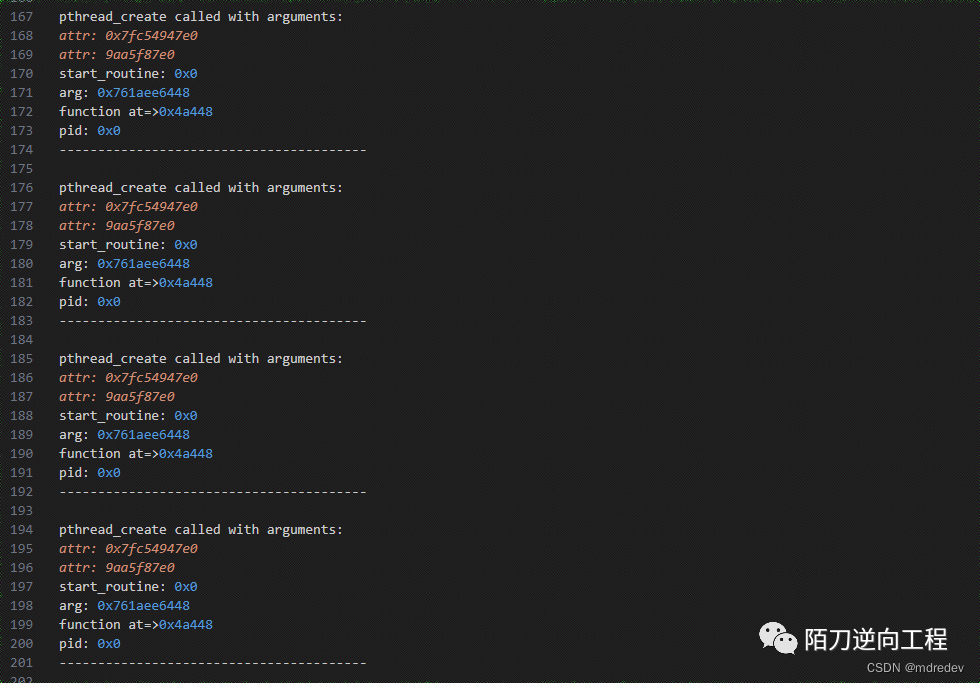
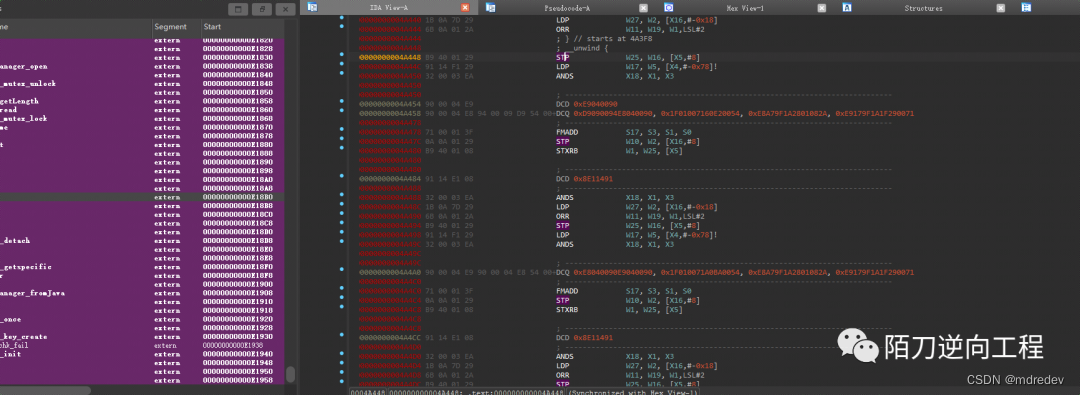
掏出ida看一下0x4a448,满屏幕的垃圾指令,按F5无法查看伪代码,难道本文就要到此结束了吗
掏出这个,lsp注入后修复一下
https://github.com/F8LEFT/SoFixer
修复后就直接shift+f12搜索gmain
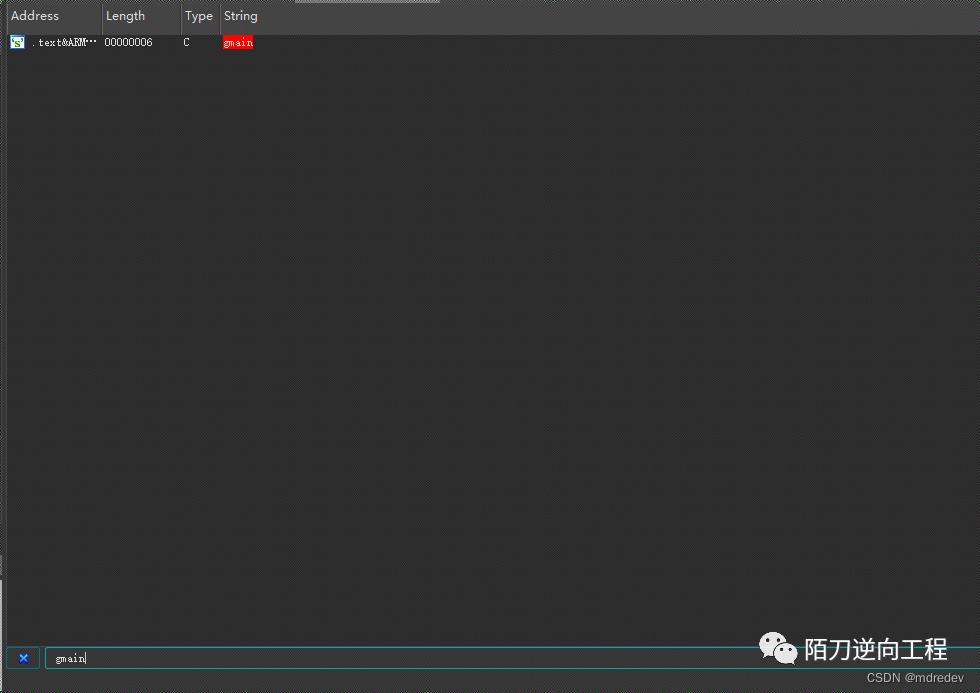
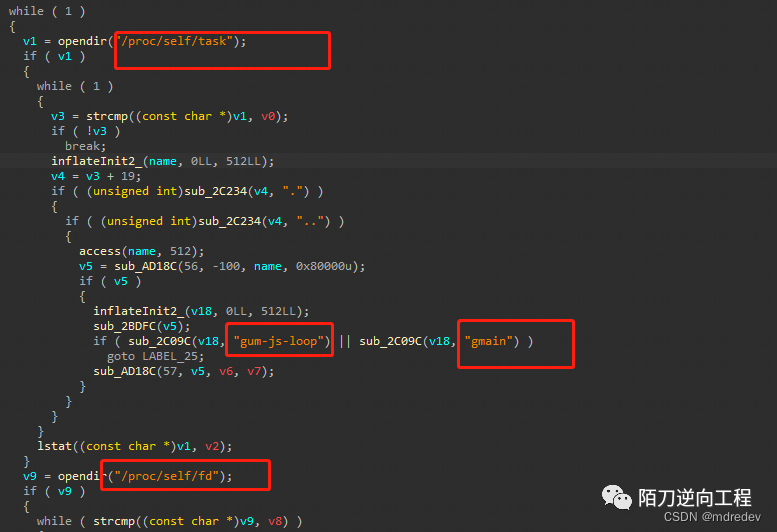
然后就非常清楚了,直接patch掉2BA40就行,直接上代码
function patch_pthread_create() {
var pthread_create_addr = Module.findExportByName(null, "pthread_create");
var pthread_create = new NativeFunction(pthread_create_addr, "int", ["pointer", "pointer", "pointer", "pointer"]);
Interceptor.replace(pthread_create_addr, new NativeCallback((Thread, attr, start_routine, pid) => {
var module = Process.findModuleByAddress(start_routine);
var ret = 0;
if (module) {
var so_name = module.name
var so_base = Module.getBaseAddress(so_name);
var offset = start_routine - so_base;
if (so_name.indexOf("libbaiduprotect.so") !=-1) {
if (offset.toString(16) == "2ba40") {
console.log("patch at=> 0x"+offset.toString(16));
}
else {
ret = pthread_create(Thread, attr, start_routine, pid);
}
} else {
ret = pthread_create(Thread, attr, start_routine, pid);
}
}
return ret;
}, "int", ["pointer", "pointer", "pointer", "pointer"]));
}
function hook_pthread_create() {
var libcModule = Process.findModuleByName('libc.so');
if (libcModule) {
var pthread_create = new NativeFunction(
libcModule.findExportByName('pthread_create'),
'int', ['pointer', 'pointer', 'pointer', 'pointer']
);
Interceptor.attach(pthread_create, {
onEnter: function (args) {
var libmsaoaidsecModule = Process.findModuleByName('libbaiduprotect.so');
if (libmsaoaidsecModule) {
// 在进入 pthread_create 之前
console.log("pthread_create called with arguments:");
console.log("attr:", args[0]);
console.log("attr:", (args[0] - libmsaoaidsecModule.base).toString(16));
console.log("start_routine:", args[1]);
console.log("arg:", args[2]);
console.log("function at=>0x"+(args[2] - libmsaoaidsecModule.base).toString(16));
console.log("pid:", args[3]);
console.log('----------------------------------------\n')
}
},
onLeave: function (retval) {
}
});
}
}
function hook_dlopen() {
var android_dlopen_ext = Module.findExportByName(null, "android_dlopen_ext");
Interceptor.attach(android_dlopen_ext, {
onEnter: function (args) {
this.call_hook = false;
var so_name = ptr(args[0]).readCString();
// console.log("android_dlopen_ext=>", so_name)
if(so_name!=null){
hook_pthread_create()
}
}, onLeave: function (retval) {
}
});
}
// setImmediate(hook_dlopen);
setImmediate(patch_pthread_create)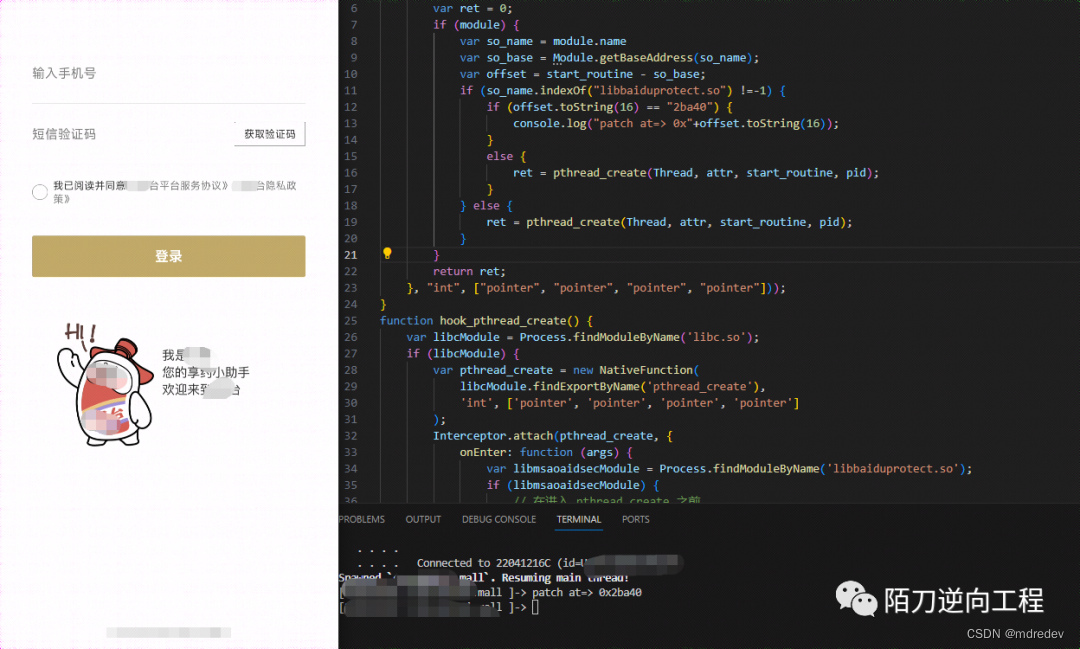
part-2部分看了一下,感觉挺繁琐的有时间再写




















 3333
3333











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








