未经作者同意,任何人不得以“原创”形式发布,也不得已用于商业用途,本人不负责任何法律责任。
前一篇:http://blog.csdn.net/dba_huangzj/article/details/38063823
前言:
SQL Server 的通信基于TCP和UDP端口,如果你需要从非本机的机器上访问SQL Server,需要打开防火墙的端口。而Windows Server 2008 默认防火墙是开启的。简单来说,就是全部端口都被阻止。
实现:
可以按照下面步骤配置Windows 防火墙:
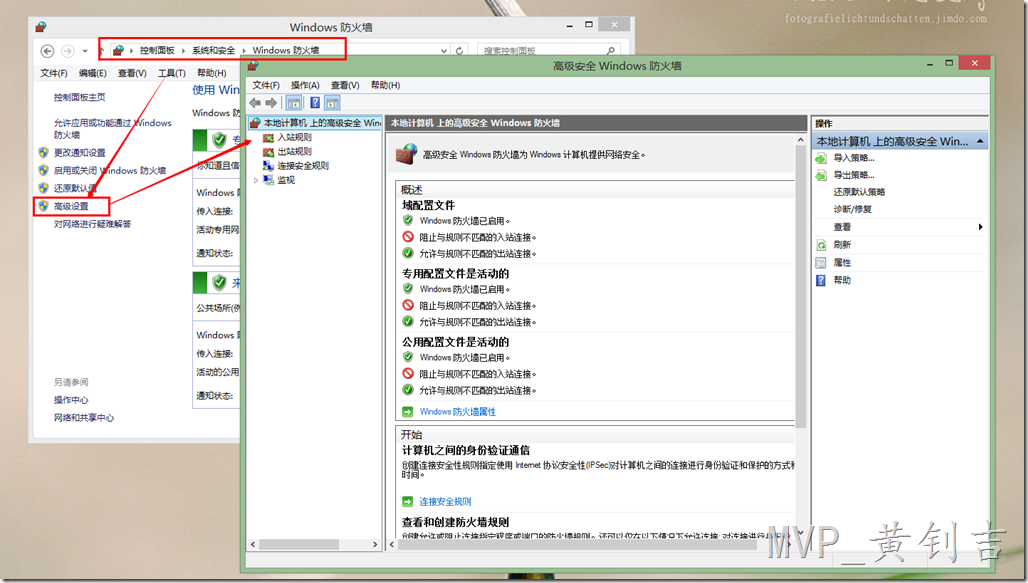
1. 在【开始】菜单中打开【控制面板】,也可以直接点击网络图标打开,然后选择【系统和安全】,点击【Windows 防火墙】,最后点击【高级设置】,如图:
原文出处:http://blog.csdn.net/dba_huangzj/article/details/38082123,专题目录:http://blog.csdn.net/dba_huangzj/article/details/37906349
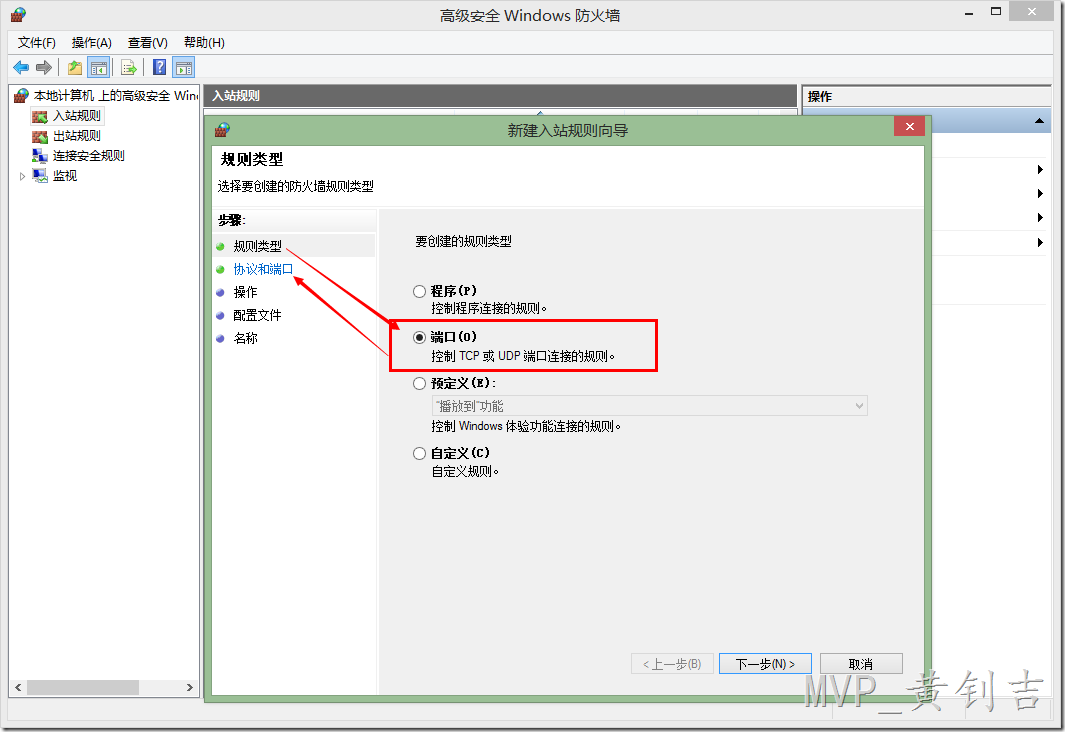
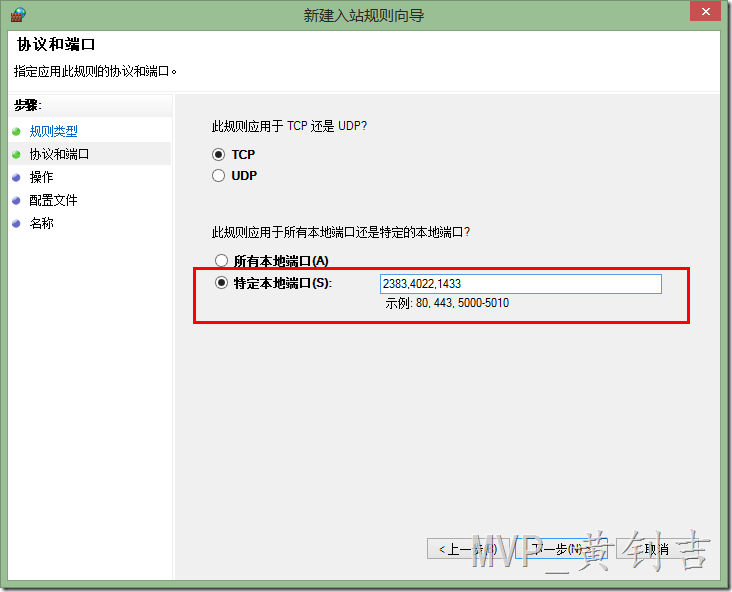
2.右键【入站规则】,选择【新建规则】,然后在【规则类型】中选择【端口】,然后在【协议和端口】中输入下面的端口:
- 如果仅用SQL Server 引擎的默认实例,输入1433
- 如果需要使用Analysis Services 引起的默认实例,输入2383
- 如果使用Service Broker ,输入4022
点击【下一步】。完整的端口列表可以访问:http://msdn.microsoft.com/zh-cn/library/cc646023%28v=SQL.110%29.aspx
原文出处:http://blog.csdn.net/dba_huangzj/article/details/38082123,专题目录:http://blog.csdn.net/dba_huangzj/article/details/37906349
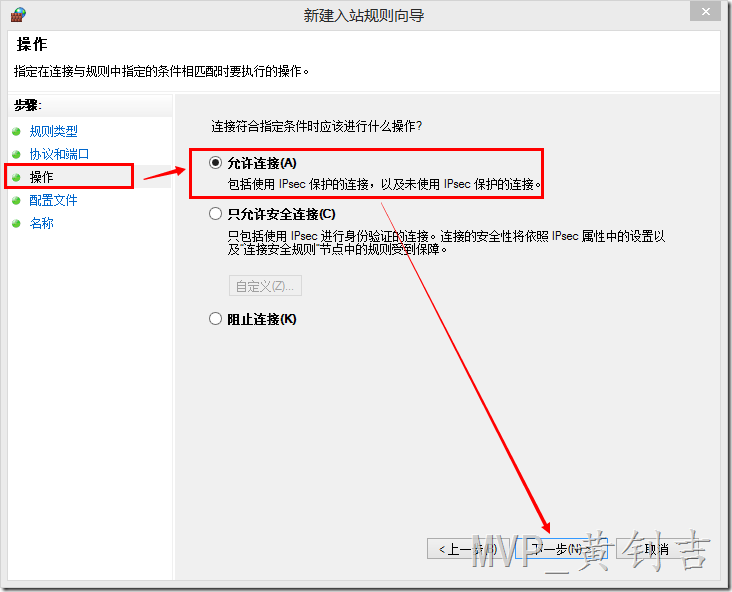
3. 在【操作】项中选择【允许连接】,点击【下一步】:
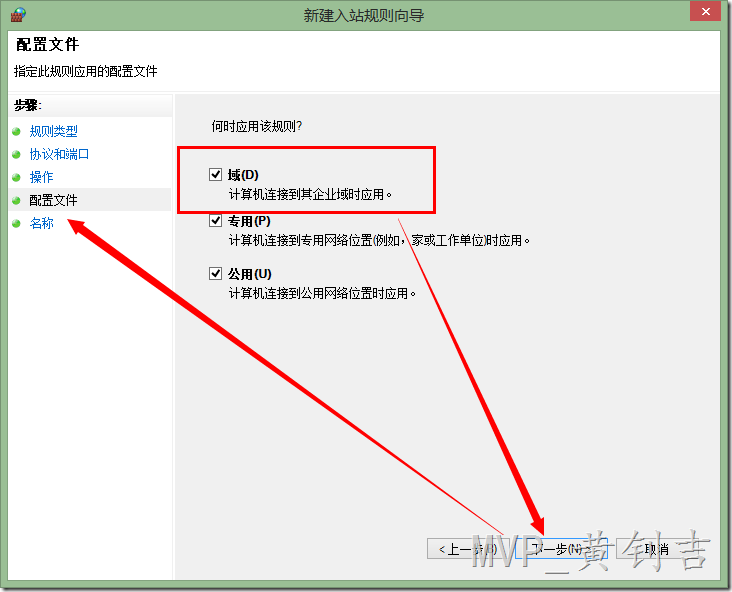
4. 在【配置文件】项中,如果你在域中,仅保留【域】选项的勾选,另外两个,主要用于工作站或笔记本。如果服务器是通过标识为【公共】的网络连接的,比如从互联网直接访问,并且你想SQL Server能被外部发现,可以选择【公共】,当然,这比较危险。最后选择【下一步】并输入规则名。
原理:
原文出处:http://blog.csdn.net/dba_huangzj/article/details/38082123,专题目录:http://blog.csdn.net/dba_huangzj/article/details/37906349
上面描述了如何打开SQL Server默认实例的端口,比如TCP 1433。而命名实例使用的是动态端口,每次SQL Server 服务重启后端口可能改变。这个端口是通过SQLServer Browser 服务监听UDP 1434端口来实现客户端的通信。动态端口不适用于防火墙配置,因为使用动态端口会强制你打开一个“范围”的端口。
最好的方式是指定一个已经在防火墙中配置了的固定TCP端口给命名实例,并禁用SQL Server Browser,然后关闭防火墙中的UDP 1434端口。这部分会在接下来的一篇文章中介绍。
注意:从Windows Server 2008/Vista开始,默认动态端口范围已经改变,详细信息可从这里查看:http://support.microsoft.com/kb/929851
更多信息:
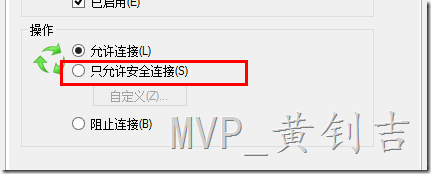
为了限制特定的用户或者机器访问SQL Server,可以通过防火墙的【入站规则】实现,可以在【入站规则】中找到对应的服务,如【SQL Server】,右键然后点击【属性】,在【常规页】勾选【只允许安全连接】,如图:
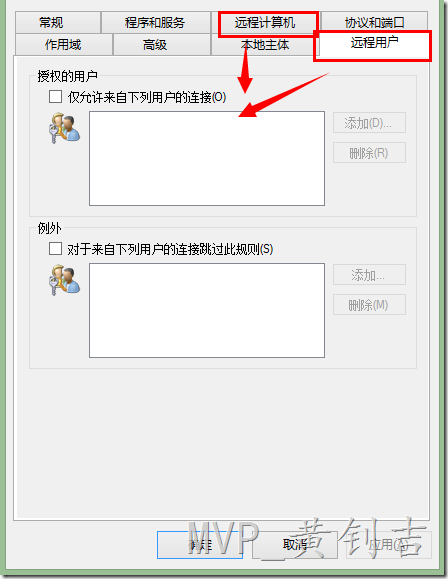
然后分别在【远程用户】和【远程计算机】标签中授予特定用户或计算机访问:
另外,可以在SQL Server中用命令查询特定端口,可以使用下面语句查看Service Broker、镜像中的端口,如果需要使用这些功能,需要开放对应的端口:
SELECT name ,
protocol_desc ,
port ,
state_desc
FROM sys.tcp_endpoints
WHERE type_desc IN ( 'SERVICE_BROKER', 'DATABASE_MIRRORING' );除了图形化操作,还可以使用netsh.exe命令实现防火墙配置,以管理员身份运行这个命令,并用下面语句开放TCP 1433端口:
netsh advfirewall firewall add rule name = "SQL Server" dir = in protocol = tcp action = allow localport = 1433,2383 profile = DOMAIN原文出处: http://blog.csdn.net/dba_huangzj/article/details/38082123 ,专题目录: http://blog.csdn.net/dba_huangzj/article/details/37906349
更多相关信息可以访问:(如何使用"netsh 由防火墙"上下文,而不是控制 Windows Vista 和 Windows Server 2008 中的 Windows 防火墙行为"netsh 防火墙"上下文)
http://support.microsoft.com/kb/947709
下一篇:http://blog.csdn.net/dba_huangzj/article/details/38227187
























 1314
1314

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








