前情回顾
K8S核心资源管理方法(CRUD) :
· 陈述式管理→基于众多kubectl命令
· 声明式管理→基于K8S资源配置清单
. GUl式管理→基于K8S仪表盘(dashboard)
.K8S的CNI网络插件
· 种类众多,以flannel为例
. 三种常用工作模式
· 优化SNAT规则
. K8S的服务发现
· 集群网络→Cluster IP
. Service资源→Service Name
. Coredns软件→实现了Service Name和Cluster IP的自动关联
. K8S的服务暴露
- Ingress资源→专用于暴露7层应用到K8S集群外的一种核心资源(http/https)
- Ingress控制器→一个简化版的nginx(调度流量) + go脚本(动态识别yaml)
- Traefik软件→实现了ingress控制器的一个软件
不管是json也好还是yaml也好都可以抽象成结构化数据
四个常用的k8s的核心附件有1.CNI网络插件 2.服务发现的插件 3.服务暴露的插件 4.GUI图像化辅助插件
在21上ping22的不通的需要
route add -net 172.7.22.0/24 gw 10.4.7.22 dev ens33
还需要在22上打开转发规则
iptables -t filter -I FORWARD -d 172.7.22.0/24 -j ACCEPT
然后去21上ping22就能通了
上面就是若是你的集群足够的小就不用什么网络插件了直接加路由转发规则就能实现相互的容器之间的相互通信了
k8s的服务发现回顾
服务发现
三个比较重要的概念
虚构出来的集群网络
一个仅仅在集群网络存在通过kube-proxy将集群网络和pod网络关联起来了
相对固定的帮你去找pod,是通过特色的功能就是标签选择器。。
使用coredns的软件将域名和容器的地址解析出来。就是自动的管理service name到cluster ip的功能
服务暴露
ingress资源----专门用于暴露7层应用到k8s集群外的一种核心资源(http/https)
ingress控制器—简化版的nginx(调度流量)+ go脚本(动态识别yaml)
traefik 软件-----实现ingress控制器的一个软件
看下面的图一个是前端,一个是后台,真正进入前端是通过下面的域名进来的,后端找到了真实提供的pod,每个运算节点起一份,因为起容器时通过deamonSet去启动的

它时和宿主机共享的网络命名成空间hostname
相应时间呀都要的

k8s的GUI资源管理插件–仪表盘
部署kubernetes-dashboard
下载地址::在github可以去找
准备dashboard镜像
运维主机200上进行操作
[root@hdss7-200 k8s-yaml]# docker pull k8scn/kubernetes-dashboard-amd64:v1.8.3
v1.8.3: Pulling from k8scn/kubernetes-dashboard-amd64
a4026007c47e: Pull complete
Digest: sha256:ebc993303f8a42c301592639770bd1944d80c88be8036e2d4d0aa116148264ff
Status: Downloaded newer image for k8scn/kubernetes-dashboard-amd64:v1.8.3
docker.io/k8scn/kubernetes-dashboard-amd64:v1.8.3
[root@hdss7-200 k8s-yaml]# docker images |grep dashb
k8scn/kubernetes-dashboard-amd64 v1.8.3 fcac9aa03fd6 3 years ago 102MB
[root@hdss7-200 k8s-yaml]# docker tag fcac9aa03fd6 harbor.od.com/public/dashboard:v1.8.3
[root@hdss7-200 k8s-yaml]# docker push harbor.od.com/public/dashboard:v1.8.3
The push refers to repository [harbor.od.com/public/dashboard]
23ddb8cbb75a: Pushed
v1.8.3: digest: sha256:ebc993303f8a42c301592639770bd1944d80c88be8036e2d4d0aa116148264ff size: 529
[root@hdss7-200 k8s-yaml]# mkdir dashboard
[root@hdss7-200 k8s-yaml]# cd dashboard/
[root@hdss7-200 dashboard]# ll
total 0
[root@hdss7-200 dashboard]# vi rbac.yaml
[root@hdss7-200 dashboard]# vim dp.yaml
[root@hdss7-200 dashboard]# vi dp.yaml
[root@hdss7-200 dashboard]# vi svc.yaml
[root@hdss7-200 dashboard]# vi ingress.yaml
[root@hdss7-200 dashboard]# cat rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
[root@hdss7-200 dashboard]# ll
total 16
-rw-r--r-- 1 root root 1382 Aug 29 21:26 dp.yaml
-rw-r--r-- 1 root root 318 Aug 29 21:27 ingress.yaml
-rw-r--r-- 1 root root 610 Aug 29 21:25 rbac.yaml
-rw-r--r-- 1 root root 322 Aug 29 21:26 svc.yaml
[root@hdss7-200 dashboard]# cat ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
[root@hdss7-200 dashboard]# cat rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
[root@hdss7-200 dashboard]# cat svc.yaml
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
[root@hdss7-200 dashboard]# cat dp.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.8.3
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
[root@hdss7-200 dashboard]#
然后去21上创建pod
[root@hdss7-21 ~]# kubectl create -f http://k8s-yaml.od.com/dashboard/rbac.yaml
serviceaccount/kubernetes-dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-admin created
[root@hdss7-21 ~]# kubectl create -f http://k8s-yaml.od.com/dashboard/dp.yaml
deployment.apps/kubernetes-dashboard created
[root@hdss7-21 ~]# kubectl create -f http://k8s-yaml.od.com/dashboard/svc.yaml
service/kubernetes-dashboard created
[root@hdss7-21 ~]# kubectl create -f http://k8s-yaml.od.com/dashboard/ingress.yaml
ingress.extensions/kubernetes-dashboard created
[root@hdss7-21 ~]# kubectl get po -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-6b6c4f9648-ckjh7 1/1 Running 0 5h13m
kubernetes-dashboard-76dcdb4677-855kz 1/1 Running 0 44s
traefik-ingress-2jb8z 1/1 Running 0 157m
traefik-ingress-zh4k6 1/1 Running 0 157m
[root@hdss7-21 ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
coredns ClusterIP 192.168.0.2 <none> 53/UDP,53/TCP,9153/TCP 5h39m
kubernetes-dashboard ClusterIP 192.168.37.169 <none> 443/TCP 3m54s
traefik-ingress-service ClusterIP 192.168.225.63 <none> 80/TCP,8080/TCP 168m
[root@hdss7-21 ~]# kubectl get ingress -n kube-system
NAME HOSTS ADDRESS PORTS AGE
kubernetes-dashboard dashboard.od.com 80 3m50s
traefik-web-ui traefik.od.com 80 168m
在11上添加域名解析
[root@hdss7-11 ~]# vi /var/named/od.com.zone
[root@hdss7-11 ~]# systemctl restart named
[root@hdss7-11 ~]# cat /var/named/od.com.zone
$ORIGIN od.com.
$TTL 600 ; 10 minutes
@ IN SOA dns.od.com. dnsadmin.od.com. (
2021052305 ; serial
10800 ; refresh (3 hours)
900 ; retry (15 minutes)
604800 ; expire (1 week)
86400 ; minimum (1 day)
)
NS dns.od.com.
$TTL 60 ; 1 minute
dns A 10.4.7.11
harbor A 10.4.7.200
k8s-yaml A 10.4.7.200
traefik A 10.4.7.10
dashboard A 10.4.7.10
[root@hdss7-11 ~]#
在21上看解析是否正常
[root@hdss7-21 ~]# dig -t A dashboard.od.com @192.168.0.2 +short
10.4.7.10
[root@hdss7-21 ~]#
然后就去浏览器查看是否安装好了
http://dashboard.od.com/#!/overview?namespace=default


k8s的RBAC原理详解
基于角色的访问控制就是rbac

用户账户如kubelet.kubeconfig,而它就是k8s的用户账户的配置文件
无法直接给账户赋予权限。必须要绑定角色,然后基于角色去给用户账户或服务账户赋予相应的权限
role 角色-----仅仅最指定名称空间有效
clusterrole 普通角色-----对集群名称空间有效
绑定角色的操作也是一种资源
所有的pod都要有一个服务用户,如果你没有指定服务账户是谁,它就给你选定默认的服务账户default。如下图

然后可以去看yaml文件进行解析
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller 服务用户
namespace: kube-system 名称空间
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole 声明集群角色
metadata:
name: traefik-ingress-controller
rules: 定义角色的规则(权限)
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding 集群角色绑定,就是将上面用户和规则关联起来
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef: 让你参考的集群角色
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects: 角色让那个用户使用呢
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
rbac就是三步,一创建用户,二定义角色,三将角色和用户绑定起来
然后可以看下dashborad的rbac
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin 声明服务账户
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef: 直接做了角色绑定
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole 指定的是默认集群角色可以用名kubectl get clusterrole查看默认的集群角色
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
可以看下默认的定义的角色
[root@hdss7-21 ~]# kubectl get clusterrole cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: "2021-08-29T04:36:12Z"
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: cluster-admin
resourceVersion: "40"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/cluster-admin
uid: 5b982688-f5b2-47b2-9725-c9124845ad28
rules: #对所有的组所有的资源有所有权限,就是admin
- apiGroups:
- '*'
resources:
- '*'
verbs:
- '*'
- nonResourceURLs:
- '*'
verbs:
- '*'
[root@hdss7-21 ~]#

也可以看下默认的集群角色是是什么样的
[root@hdss7-21 ~]# kubectl get clusterrole system:node -oyaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: "2021-08-29T04:36:13Z"
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: system:node
resourceVersion: "51"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/system%3Anode
uid: e16e15e2-0686-4edc-ad70-5cdc6b7c6e71
rules:
- apiGroups:
- authentication.k8s.io
resources:
- tokenreviews
省略
下面你可以去官方去看rbac是什么一个工作原理


k8s仪表盘鉴权方式了解
在200上进行操作
这个作用不大,不详细写,想做的话可以看下面的图自己做
首先创建浏览器上网站上用到的私钥,在200上
[root@hdss7-200 certs]# (umask 077; openssl genrsa -out dashboard.od.com.key 2048)
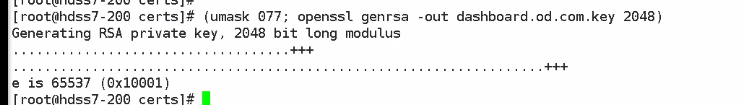
然后做证书签发的请求文件
[root@hdss7-200 certs]# openssl req -new -key dashboard.od.com.key -out dashboar.od.com.csr -subj "/CN=dashboard.od.com/C=CN/ST=BJ/L=Beijing/O=OldboyEdu/OU=ops"

可以看到已经创建了证书签发的请求文件

然后去签发证书
[root@hdss7-200 certs]# openssl x509 -req -in dashboar.od.com.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out dashboard.od.com.crt -days 3650
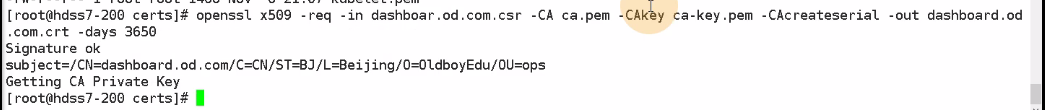
$$下面是可以检查下,可以不做

在11上进行操作
[root@hdss7-11 ~]# cd /etc/nginx/
[root@hdss7-11 nginx]# mkdir certs
[root@hdss7-11 nginx]# cd certs/
[root@hdss7-11 certs]# scp hdss7-200:/opt/certs/dashboard.od.com.crt .
The authenticity of host 'hdss7-200 (10.4.7.200)' can't be established.
ECDSA key fingerprint is SHA256:S8lqSXkRnqiGTHxKRSz2BsEbZ45BZTzgVUg611F56/0.
ECDSA key fingerprint is MD5:bb:9d:b7:1f:be:e3:0a:cc:2a:58:5b:13:56:df:c9:82.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'hdss7-200' (ECDSA) to the list of known hosts.
dashboard.od.com.crt 100% 1196 1.4MB/s 00:00
[root@hdss7-11 certs]# ll
总用量 4
-rw-r--r-- 1 root root 1196 6月 22 23:09 dashboard.od.com.crt
[root@hdss7-11 certs]# scp hdss7-200:/opt/certs/dashboard.od.com.key .
dashboard.od.com.key 100% 1679 1.9MB/s 00:00
[root@hdss7-11 certs]# ll
总用量 8
-rw-r--r-- 1 root root 1196 6月 22 23:09 dashboard.od.com.crt
-rw------- 1 root root 1679 6月 22 23:10 dashboard.od.com.key
[root@hdss7-11 certs]# cd ..
[root@hdss7-11 nginx]# cd conf.d/

在这里做了一个特殊的操作
[root@hdss7-11 conf.d]# vi dashboard.od.com.conf
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.od.com.crt";
ssl_certificate_key "certs/dashboard.od.com.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MDS;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
[root@hdss7-11 conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@hdss7-11 conf.d]# nginx -s reload

然后在刷新的时候就需要证书了
这时候填写-高级–继续连接–

再去看证书的时候就显示是证书无效
如果你给浏览器交钱就会有效了

这个时候就是需要用token登录了
登录方式
[root@hdss7-21 ~]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
coredns-token-2j5fs kubernetes.io/service-account-token 3 6d
default-token-7vfng kubernetes.io/service-account-token 3 18d
kubernetes-dashboard-admin-token-zpdqq kubernetes.io/service-account-token 3 2d1h
kubernetes-dashboard-key-holder Opaque 2 2d1h
traefik-ingress-controller-token-k7z4c kubernetes.io/service-account-token 3 2d6h
[root@hdss7-21 ~]# kubectl describe secret kubernetes-dashboard-admin-token-zpdqq -n kube-system
Name: kubernetes-dashboard-admin-token-zpdqq
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard-admin
kubernetes.io/service-account.uid: ee381186-ee4a-485a-8861-d6791aab0c93
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1346 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbi10b2tlbi16cGRxcSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImVlMzgxMTg2LWVlNGEtNDg1YS04ODYxLWQ2NzkxYWFiMGM5MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiJ9.YFnb4kcn4Ykkdmq4lDrkyy2mLzCo2RwwWDS8S8cPaaWgEdYXdXHfHZr0zbsiaEkN1Rlmby6aZwpQwqK8MpeYjTxmn13HX-2uAMdPy5w6deLr_cdDBtKU94gQWQVTcLPrjg01RJ6QZLRv0tv2CDcKJUd9u3C7CUO3xmzjJJTY0XJBtUvHrlCLYooGAVwYbyTWhoD0G6cWDh_ncK8iDTUeVHjJw1u-cwgA3N2E6R8TcAwxlrQUWqEM07U9odKp-YX8YnLWoRFupH4mVSkNzoO0-7Djix2Q8x59_xqtpoxzi_aE39uMjSCy_lbv0xqNNaJQ5JuPsgli73Co9RpWnkkTLw
这个时候可能没有报错但是登录还是一直卡着
需要去配置认证下
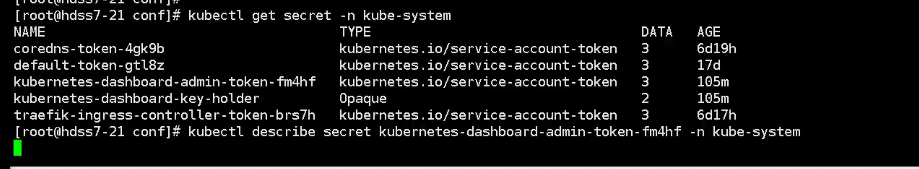
令牌就能登录上了

这个时候可能很不好刷出来,因为需要换成v1.10.1
升级v1.10.1版本
[root@hdss7-200 certs]# docker pull hexun/kubernetes-dashboard-amd64:v1.10.1
v1.10.1: Pulling from hexun/kubernetes-dashboard-amd64
9518d8afb433: Pull complete
Digest: sha256:0ae6b69432e78069c5ce2bcde0fe409c5c4d6f0f4d9cd50a17974fea38898747
Status: Downloaded newer image for hexun/kubernetes-dashboard-amd64:v1.10.1
docker.io/hexun/kubernetes-dashboard-amd64:v1.10.1
[root@hdss7-200 certs]# docker images |grep dash
hexun/kubernetes-dashboard-amd64 v1.10.1 f9aed6605b81 2 years ago 122MB
k8scn/kubernetes-dashboard-amd64 v1.8.3 fcac9aa03fd6 3 years ago 102MB
harbor.od.com/public/dashboard v1.8.3 fcac9aa03fd6 3 years ago 102MB
[root@hdss7-200 certs]# docker tag f9aed6605b81 harbor.od.com/public/dashboard:v1.10.1
[root@hdss7-200 certs]# docker push harbor.od.com/public/dashboard:v1.10.1
The push refers to repository [harbor.od.com/public/dashboard]
fbdfe08b001c: Pushed
v1.10.1: digest: sha256:0ae6b69432e78069c5ce2bcde0fe409c5c4d6f0f4d9cd50a17974fea38898747 size: 529
[root@hdss7-200 certs]# cd /data/k8s-yaml/dashboard/
[root@hdss7-200 dashboard]# vi dp.yaml
24 image: harbor.od.com/public/dashboard:v1.10.1 ##将1.8.3改成1.10.1

注意把dp.yaml的v1.8.3改为v1.10.1
然后去浏览器去更改下就能直接更新了

这个时候可能就会出现错误的了,过一会就好了,
同样的道理可以去查看密钥登录了

会强制你登录

dashboard分权举例
这个这不在做了,
在200上创建rbac-minimal.yaml文件
[root@hdss7-200 dashboard]# pwd
/data/k8s-yaml/dashboard
[root@hdss7-200 dashboard]# cat rbac-minimal.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard
namespace: kube-system
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update ' kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroups: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
然后更改下dp的那个目录
[root@hdss7-200 dashboard]# cat dp.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.8.3
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard ##这里更改
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
[root@hdss7-200 dashboard]#
然后在22上进行创建minimal的pod了
然后再去hdss7-22上创建
[root@hdss7-22 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/rbac-minimal.yaml
serviceaccount/kubernetes-dashboard unchanged
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal unchanged
error: error validating "http://k8s-yaml.od.com/dashboard/rbac-minimal.yaml": error validating data: [ValidationError(RoleBinding.roleRef): unknown field "apiGroups" in io.k8s.api.rbac.v1.RoleRef, ValidationError(RoleBinding.roleRef): missing required field "apiGroup" in io.k8s.api.rbac.v1.RoleRef]; if you choose to ignore these errors, turn validation off with --validate=false
[root@hdss7-22 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/rbac-minimal.yaml --validate=false
serviceaccount/kubernetes-dashboard unchanged
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal unchanged
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
[root@hdss7-22 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/dp.yaml
deployment.apps/kubernetes-dashboard configured
[root@hdss7-22 ~]# kubectl get po -n kube-system ----这里查看的快乐会看到一个更新的过程
NAME READY STATUS RESTARTS AGE
coredns-6b6c4f9648-qb9fw 1/1 Running 3 14d
kubernetes-dashboard-6d58ccc9fc-9j2jg 1/1 Running 0 12s
traefik-ingress-8t8zl 1/1 Running 1 10d
traefik-ingress-xhwk7 1/1 Running 0 10d


这个时候去登录的时候就有两个令牌了,登录的时候先去查看令牌


l两个令牌都能登陆的,当然了在minimal的是很小的权限的
下面主要就是说明的是最小权限的可以改别设置,这样能够用有效的利用这个软件,免的给你经常能坏

上面的实验最后都是需要还原为1.8.3的注意哦























 3763
3763











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








