Lab 1 : Butter Overflow
Lab Environment Setup
Ubuntu 12.04 ( 64 bits )
Brief introduction
This is a experiment of Information Security, about 10 exercises and challenges in this blog. May be a lot mistakes here, if you find it, please contact me.
Part A:Butter Overflow Principal
Stack layout and Buffers
+------------------+ high address | ... | | stack frame of | | main | | ... | +------------------+ | str(a pointer) | (4 bytes) | return address | (4 bytes) %ebp----> | saved %ebp | (4 bytes) +------------------+ | buf[11] | | ... | (12 bytes) buf----> | buf[0] | | variable_a | (4 bytes) | ... | +------------------+ low address
We use BF ( address of the Small Buffer ) to change the RET. So it will execute from BF after completed the function calling.
Our goal is very simple, change the return address of a function, and execute the shell code to do something what we want.
Exercise 1 :
Now, you can write some code. Your job is to print the address of the variable buffer, in the C program stack1.c, and compile the C program as above.
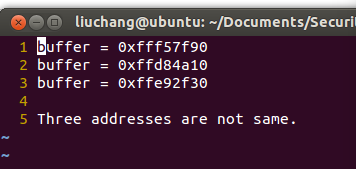
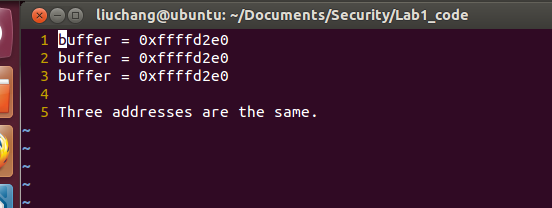
Run it three times, observe and write down the output addresses in address.txt, are these 3 addresses the same or not?
These 3 addresses are not same ! We can use
printf("buffer = %p\n", buffer)to get this address. We can see the addresses in the picture.
Challenge !
Read the file /proc/pid/maps on your machine (pid is the process id), observe the value of [stack].
$ sudo vim /proc/2100/maps
Exercise 2 :
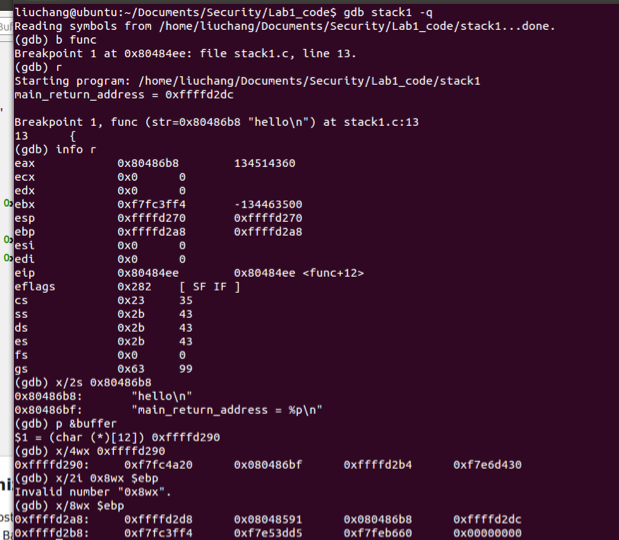
Use gdb to debug the program, as the following. You may find the online gdb documentation useful.
Address Space Layout Randomization
In order to protect against buffer overflows, most recent operating systems introduce many protection mechanisms, among which the most important one is address space layout randomization (ASLR).For the purpose of this lab, you should simply turn off ASLR (in lab 2, you’ll perform attacks when ASLR is effective), which will make your attack easier to achieve. To turn off ASLR, you can run these commands:
$ su root
Password : ( enter root password )
# sysctl -w kernel.randomize_va_space=0
Exercise 3 :
Turn off the address space layout randomization, and then do exercise 1 again, write down the three addresses in args.txt, are tho se three addresses same or not?
These 3 addresses are same ! We can see these addresses in the picture.
Buffer Overflow and Shellcode
A buffer overflow occurs when data written to a buffer exceeds the length of the buffer, so that corrupting data values in memory addresses adjacent the end of the buffer. This often occurs when copying data into a buffer without sufficient bounds checking.
Exercise 4 :
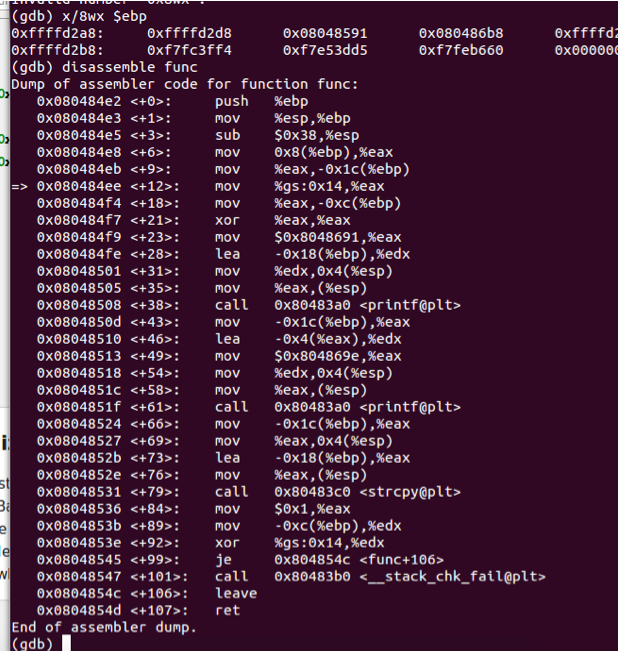
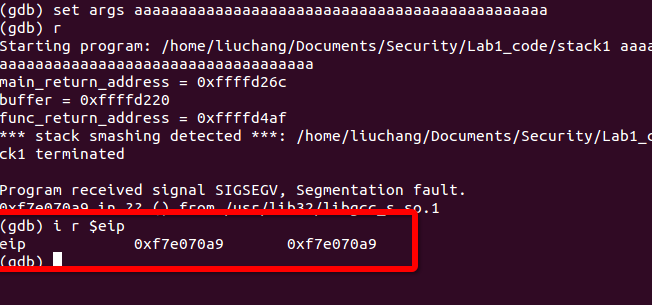
Use gdb, to print the value of the register %eip when the program crashes. How does the program run to this address?
When this program crashes, we can use
i r $eipto get the value of%eip, and it’s0xf7e070a9in my laptop.As follows:
eip 0xf7e070a9 0xf7e070a9
- Why the program run to this address? I cut some codes from the result of
disassemb








![The value of [stack] is marked red](https://img-blog.csdn.net/20151022221030693)
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章


















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








