2019领航杯write up
最近参加了领航杯,随便写点队伍做出来的题的write up
贴一下我队友的write up
他写的应该比我的详细
https://blog.csdn.net/qq_39683062/article/details/103234254
题目文件下载
https://download.csdn.net/download/LongSang01/11996313
编码解码
base64解码得到flag
DNS
打开数据包关键字搜索到原题
https://ctf-wiki.github.io/ctf-wiki/misc/traffic/protocols/DNS-zh/
stegano1
strings 直接得到flag
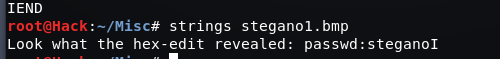
stegano
binwalk分离出zip,解压zip得到flag

lsb
三色素得到flag

凯撒Ⅰ
在线工具得到flag
https://www.ctftools.com/down/

凯撒Ⅱ
miwen="0B 33 33 28 20 2E 33 26 70 20 3D 33 39 20 37 33 30 3A 29 28 20 33 32 29 20 31 33 36 29 20 27 2C 25 30 30 29 32 2B 29 20 2D 32 20 3D 33 39 36 20 2E 33 39 36 32 29 3D 72 20 18 2C 2D 37 20 33 32 29 20 3B 25 37 20 2A 25 2D 36 30 3D 20 29 25 37 3D 20 38 33 20 27 36 25 27 2F 72 20 1B 25 37 32 6B 38 20 2D 38 03 20 75 76 7C 20 2F 29 3D 37 20 2D 37 20 25 20 35 39 2D 38 29 20 37 31 25 30 30 20 2F 29 3D 37 34 25 27 29 70 20 37 33 20 2D 38 20 37 2C 33 39 30 28 32 6B 38 20 2C 25 3A 29 20 38 25 2F 29 32 20 3D 33 39 20 38 33 33 20 30 33 32 2B 20 38 33 20 28 29 27 36 3D 34 38 20 38 2C 2D 37 20 31 29 37 37 25 2B 29 72 20 1B 29 30 30 20 28 33 32 29 70 20 3D 33 39 36 20 37 33 30 39 38 2D 33 32 20 2D 37 20 31 25 37 37 32 34 2A 33 25 37 26 37 72"
list1=miwen.split(' ')
mingwen=""
sign=True
for j in xrange(1,128):
for i in list1:
mingwen=mingwen+chr((int(i,16)+j)%128)
for i in mingwen:
if ord(i)>126 or ord(i)<33:
sign=False
break
if sign:
print mingwen
print j
mingwen=""
sign=True
ascii
s=[84,104,101,32,115,111,108,117,116,105,111,110,32,105,115,58,32,105,104,98,100,115,105,101,111,112,100,99,110]
for i in s:
print(chr(i),end="")
print("")
forensics
打开doc文件


USB
tshark -r u.pcapng -T fields -e usb.capdata > mouse_clicks.txt
#!/usr/bin/env python
from PIL import Image
import ctypes
width = 2048
height = 2048
img = Image.new("RGB", (width, height))
red = (0, 0, 0) # Skipping Right Mouse Btn, its not needed at all
green = (0, 255, 0)
blue = (0, 0, 255)
default = (0, 0, 0)
colormap = {
0: red,
1: green,
2: blue
}
x = width/2
y = height/2
with open('mouse_clicks.txt') as f:
for line in f:
bytes = map(lambda v: int('0x'+v, 16), line.split(":"))
b0, b1, b2, b3 = bytes
# byte0: 0==LBM, 1=RBM, 2=MBM
color = colormap.get(b0, default)
# byte1: X displacement
x_dis = ctypes.c_int8(b1).value
# byte2: Y displacement
y_dis = ctypes.c_int8(b2).value
x = x + x_dis
y = y + y_dis
#print "line = ", line, "bytes =", bytes, x, y
img.putpixel((x, y), color)
img.save("image.png")
OldCypher-Easy
维吉尼亚密码 , 直接在线跑出flag
MasterofZip-Middle
level1 根据提示设置爆破范围爆破出密码
level2 明文攻击
level3 伪加密 修改图片高度得到flag
数据包分析
发现flag.php直接追踪TCP流

easyrsa
import gmpy2
import libnum
e=65537
n=16969752165509132627630266968748854330340701692125427619559836488350298234735571480353078614975580378467355952333755313935516513773552163392952656321490268452556604858966899956242107008410558657924344295651939297328007932245741660910510032969527598266270511004857674534802203387399678231880894252328431133224653544948661283777645985028207609526654816645155558915197745062569124587412378716049814040670665079480055644873470756602993387261939566958806296599782943460141582045150971031211218617091283284118573714029266331227327398724265170352646794068702789645980810005549376399535110820052472419846801809110186557162127
dp=1781625775291028870269685257521108090329543012728705467782546913951537642623621769246441122189948671374990946405164459867410646825591310622618379116284293794090970292165263334749393009999335413089903796624326168039618287078192646490488534062803960418790874890435529393047389228718835244370645215187358081805
c=0x6c78dcee37830f3ec4ab4989d40fbb595060b3fbc395d52ad26defc13372c1a3948c5388f4e450e46e016c7803133d6881e5efc3b90a4789448097c94124590b1e7949f2524d7edccd61a27691c18d090ac1f54643b563141306045417581e3b263f4ad2816136a48b106f3058b08e2a810f4ae8ef25916cc110b41ac8158ce69ecbe20fc60c1ddb20154c6646bc5142aefe47abf053a8ac949d5bc057bb18b191ad08070fe9ec5d76b1fceae685514532448c1b388b2d38e7241ac19c296e95e4e021a3a4015d909a1d53a2eb7fa86f6329f4e6c937f958be576c58fab4d9c9126999c99bb28718efc41a6f5db52b47942a2ddf21639f020b5489699cf22b46L
for i in range(1,65538):
if (dp*e-1)%i == 0:
if n%(((dp*e-1)//i)+1)==0:
p=((dp*e-1)//i)+1
q=n//(((dp*e-1)//i)+1)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)%phi
print libnum.n2s(pow(c,d,n))
easyelf
key=[0x00000010,0x0000001A,0x00000017,0x00000011,0x0000000D,0x0000004F,0x00000073,0x0000005D,0x0000007A,0x00000070,0x00000029,0x0000004E,0x00000012,0x00000043,0x00000047,0x0000000E,
0x00000029,0x0000001A,0x00000042,0x00000013,0x00000012,0x00000029,0x00000013,0x00000045,0x00000007,0x00000019,0x00000001,0x00000028,0x00000023,0x00000018,0x0000000F,0x0000000B]
flag=""
v1 = 17;
i=30
while(v1<i):
result = v1;
if ( v1 >= i ):
break;
key[v1]=key[v1]^key[i]
key[i]=key[v1]^key[i]
key[v1]=(key[i]+1)^key[v1]
i=i-1
v1=v1+1
i=11
for i in range(11,16):
key[i] = ((key[i]& 0xCC) >> 2) | 4 *key[i] & 0xCC;
key[i] ^= 0xE;
i=5
for i in range(5,10):
key[i]=(key[i]&0xaa)>>1|2*key[i]&0xaa
key[i]=key[i]^0xAD
i=0
for i in range(0,32):
key[i]=key[i]^0x76
flag=flag+chr(key[i])
print flag
easyre

得到flag{Let_Us_st4rt_R3v3rSe}
card
谷歌搜索到原题直接修改exp得到flag
https://github.com/Ex-Origin/ctf-writeups/tree/master/pwnthebytesctf2019/pwn/ace_of_spades





















 3442
3442











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








