Rev
Rev视频解析:[Rev0:从零开始的逆向生活]BaseCTF2024 Week1 Rev 讲解_哔哩哔哩_bilibili
[Week1] You are good at IDA
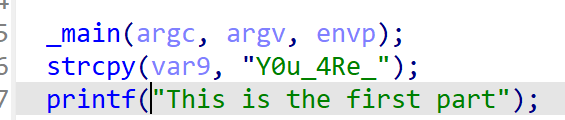
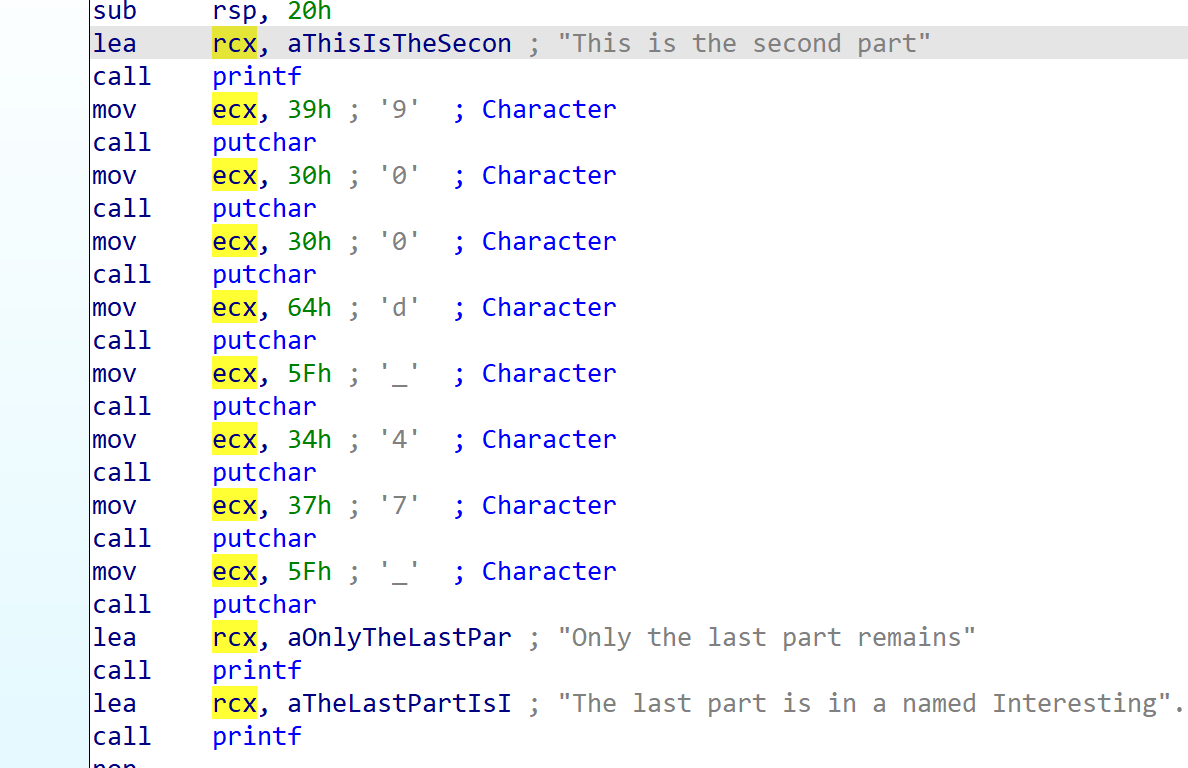
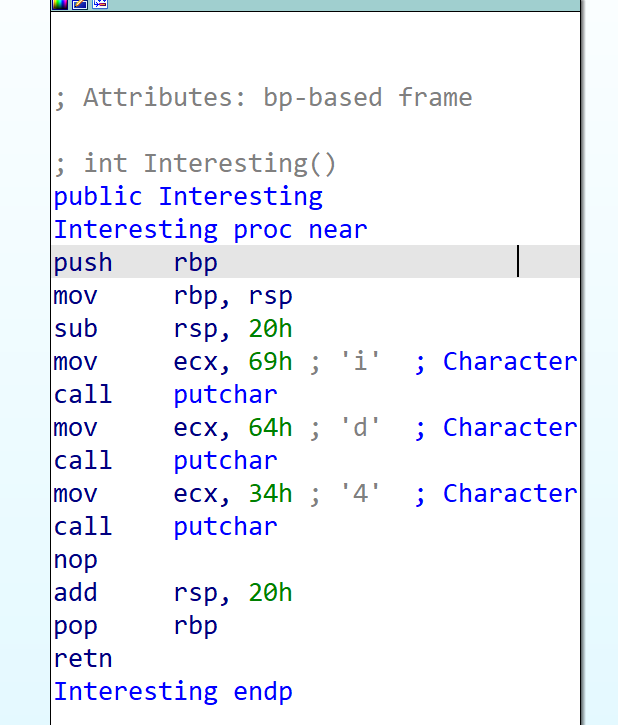
[Week1] UPX mini
脱UPX标准壳,解base64
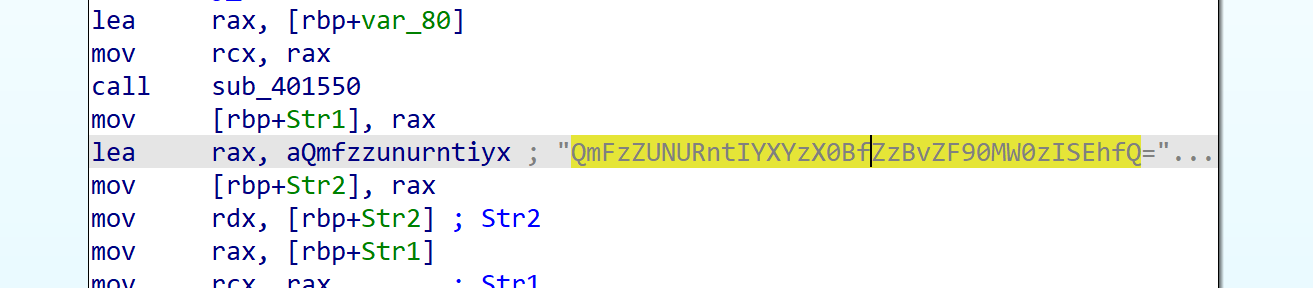
[Week1] Ez Xor
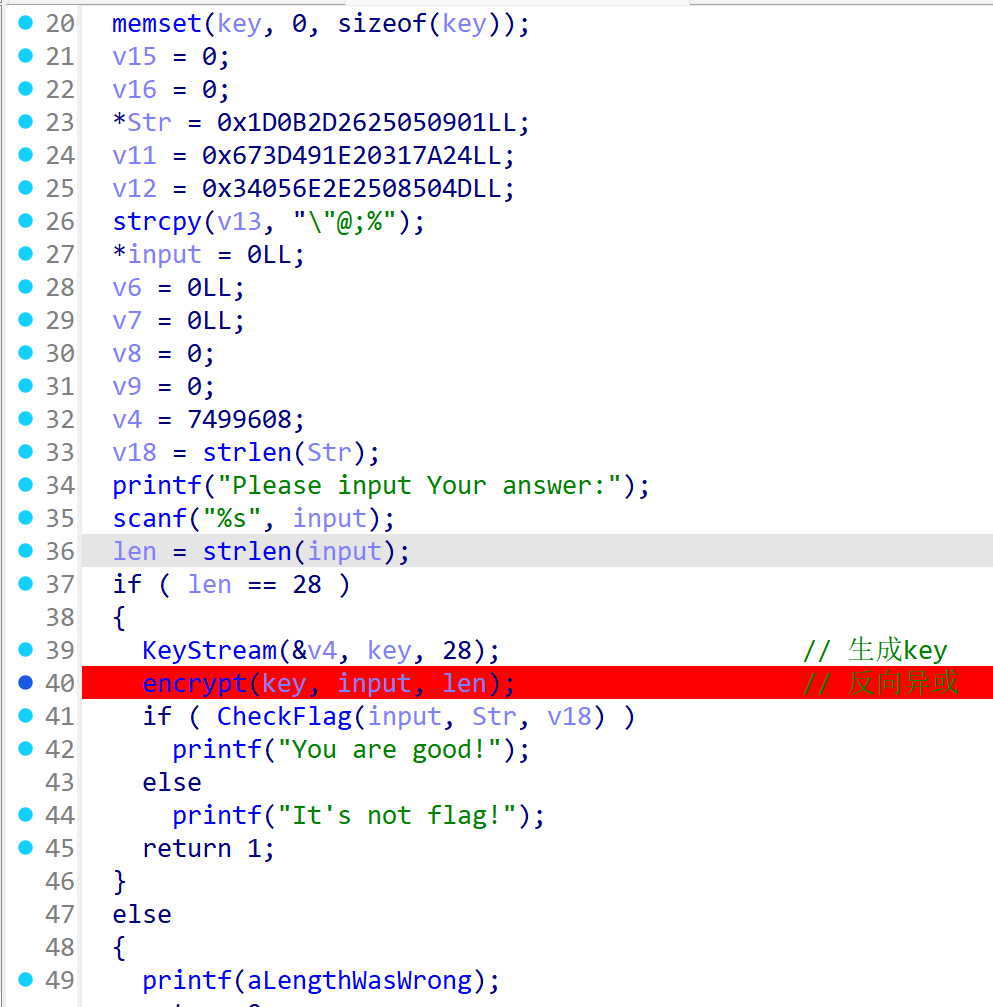
简单的反向异或,数据动调取一下
#base_xor
enc = [0x01, 0x09, 0x05, 0x25, 0x26, 0x2D, 0x0B, 0x1D, 0x24, 0x7A, 0x31, 0x20, 0x1E, 0x49, 0x3D, 0x67, 0x4D, 0x50, 0x08, 0x25, 0x2E, 0x6E, 0x05, 0x34, 0x22, 0x40, 0x3B, 0x25]
key = [0x58, 0x6E, 0x70, 0x5B, 0x6B, 0x77, 0x5E, 0x68, 0x7A, 0x51, 0x65, 0x79, 0x54, 0x62, 0x7C, 0x57, 0x7F, 0x63, 0x4A, 0x7C, 0x66, 0x4D, 0x79, 0x65, 0x40, 0x76, 0x68, 0x43]
for i in range(28):
enc[i] ^= key[28 - i - 1]
flag = ''
for i in enc:
flag += chr(i)
print(flag)[Week1] ez_maze
经典迷宫,出题人不知道怎么想的让程序故意打不开,也没看见动调
找一下地图
排列一下

搓一个DFS(AI写的),上下左右wasd
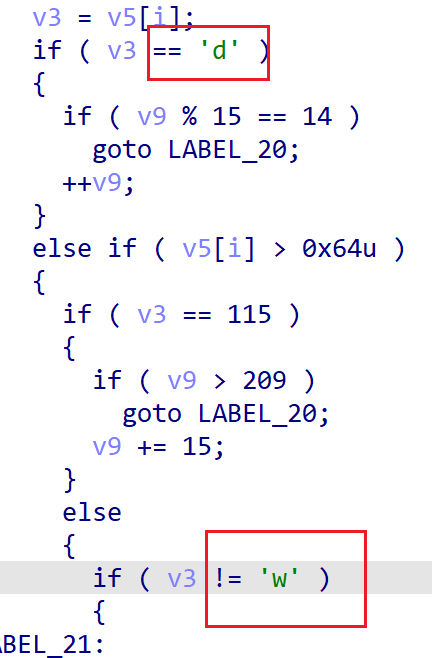
#base_maze
from collections import deque
# 定义迷宫
maze = [
"x11111111111111",
"000000111111111",
"010110110000011",
"010111001111011",
"011100011111011",
"011101001011111",
"011101011000111",
"000001000010111",
"111111000000111",
"111111011111111",
"111000011000111",
"111000000011111",
"111111111011011",
"111111111010111",
"11111100000000y"
]
# 将迷宫转换为二维数组
maze = [[c for c in row] for row in maze]
# 定义起点和终点
start = None
end = None
for i in range(len(maze)):
for j in range(len(maze[i])):
if maze[i][j] == 'x':
start = (i, j)
elif maze[i][j] == 'y':
end = (i, j)
# 定义移动方向
directions = [(-1, 0, 'w'), (1, 0, 's'), (0, -1, 'a'), (0, 1, 'd')]
# BFS 算法
def bfs(start, end):
queue = deque([(start, [])])
visited = set()
visited.add(start)
while queue:
(x, y), path = queue.popleft()
if (x, y) == end:
return path
for dx, dy, direction in directions:
nx, ny = x + dx, y + dy
if 0 <= nx < len(maze) and 0 <= ny < len(maze[0]) and maze[nx][ny] != '1' and (nx, ny) not in visited:
queue.append(((nx, ny), path + [direction]))
visited.add((nx, ny))
return None
# 寻找最短路径
path = bfs(start, end)
if path:
print("最短路径:", ''.join(path))
else:
print("没有找到路径")然后算个md5
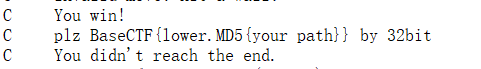
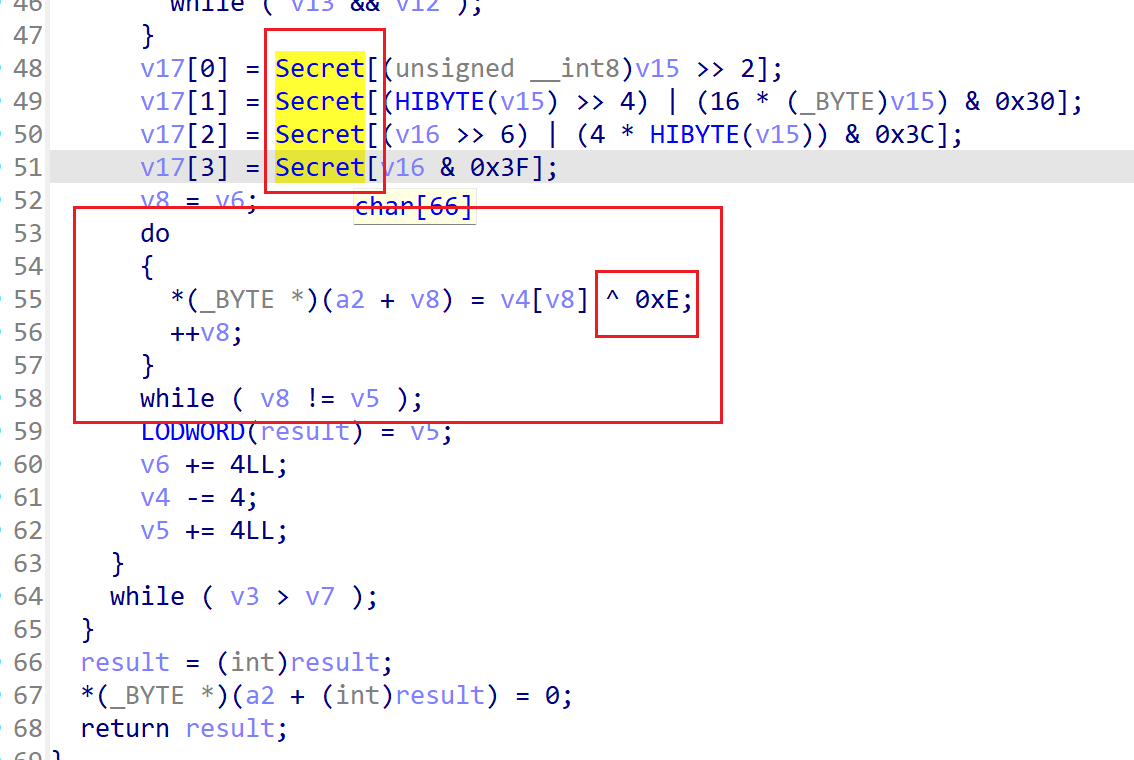
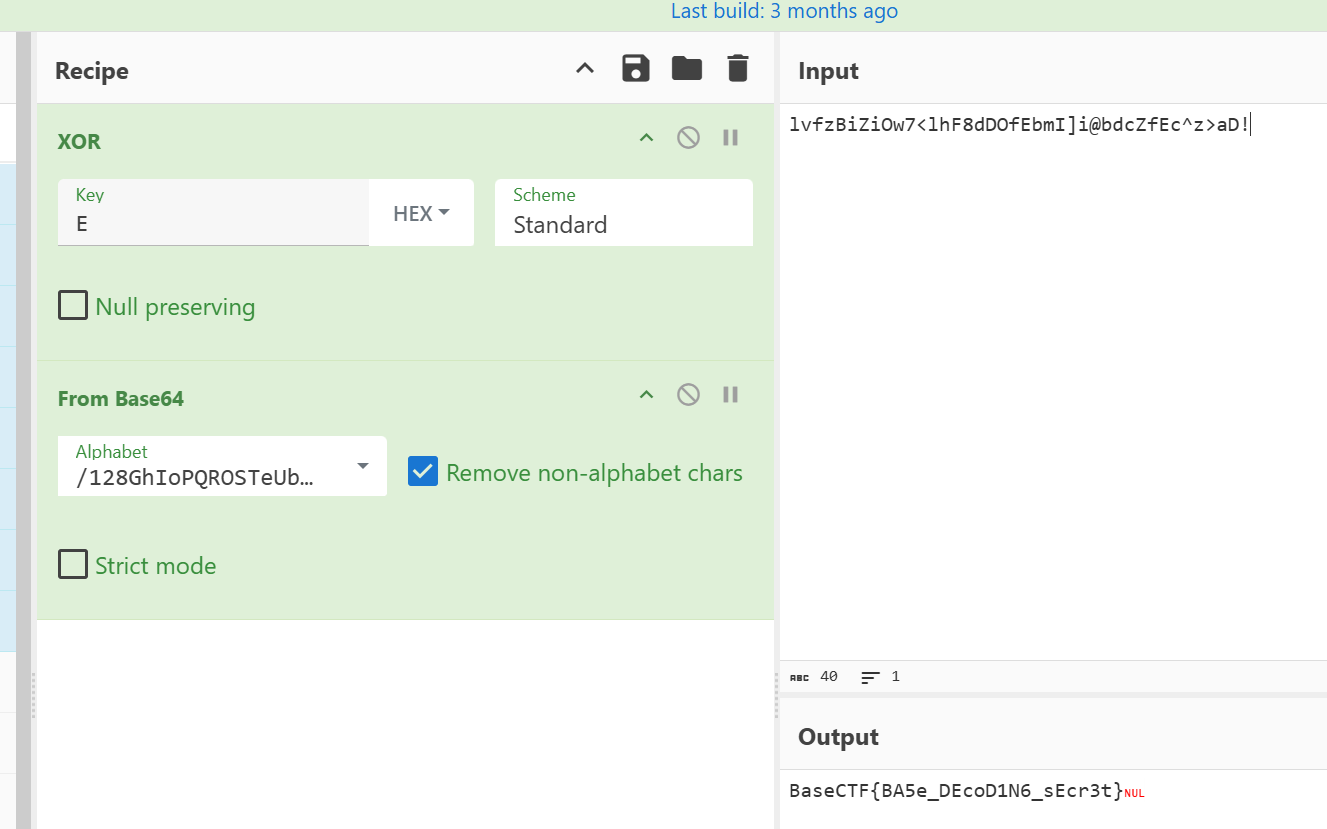
[Week1] BasePlus
换表base64+异或
Crypto
[Week1] helloCrypto
AI秒了,实际上就是个AES
#base_crypt
from Crypto.Util.number import long_to_bytes
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
# 给定的 key 和密文
key1 = 208797759953288399620324890930572736628
c = b'U\xcd\xf3\xb1 r\xa1\x8e\x88\x92Sf\x8a`Sk],\xa3(i\xcd\x11\xd0D\x1edd\x16[&\x92@^\xfc\xa9(\xee\xfd\xfb\x07\x7f:\x9b\x88\xfe{\xae'
# 将 key1 转换为字节形式
key = long_to_bytes(key1)
# 创建 AES 解密对象
my_aes = AES.new(key=key, mode=AES.MODE_ECB)
# 解密密文
padded_flag = my_aes.decrypt(c)
# 去除填充以获得原始的明文
flag = unpad(padded_flag, AES.block_size)
print(flag)
# b'BaseCTF{b80bf679-1869-4fde-b3f9-d51b872d31fb}'[Week1] 你会算md5吗
GPT秒了,爆一下hash
import hashlib
# 给定的 MD5 哈希值列表
output = ['9d5ed678fe57bcca610140957afab571', '0cc175b9c0f1b6a831c399e269772661', '03c7c0ace395d80182db07ae2c30f034', 'e1671797c52e15f763380b45e841ec32', '0d61f8370cad1d412f80b84d143e1257', 'b9ece18c950afbfa6b0fdbfa4ff731d3', '800618943025315f869e4e1f09471012', 'f95b70fdc3088560732a5ac135644506', '0cc175b9c0f1b6a831c399e269772661', 'a87ff679a2f3e71d9181a67b7542122c', '92eb5ffee6ae2fec3ad71c777531578f', '8fa14cdd754f91cc6554c9e71929cce7', 'a87ff679a2f3e71d9181a67b7542122c', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '0cc175b9c0f1b6a831c399e269772661', 'e4da3b7fbbce2345d7772b0674a318d5', '336d5ebc5436534e61d16e63ddfca327', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '8fa14cdd754f91cc6554c9e71929cce7', '8fa14cdd754f91cc6554c9e71929cce7', '45c48cce2e2d7fbdea1afc51c7c6ad26', '336d5ebc5436534e61d16e63ddfca327', 'a87ff679a2f3e71d9181a67b7542122c', '8f14e45fceea167a5a36dedd4bea2543', '1679091c5a880faf6fb5e6087eb1b2dc', 'a87ff679a2f3e71d9181a67b7542122c', '336d5ebc5436534e61d16e63ddfca327', '92eb5ffee6ae2fec3ad71c777531578f', '8277e0910d750195b448797616e091ad', '0cc175b9c0f1b6a831c399e269772661', 'c81e728d9d4c2f636f067f89cc14862c', '336d5ebc5436534e61d16e63ddfca327', '0cc175b9c0f1b6a831c399e269772661', '8fa14cdd754f91cc6554c9e71929cce7', 'c9f0f895fb98ab9159f51fd0297e236d', 'e1671797c52e15f763380b45e841ec32', 'e1671797c52e15f763380b45e841ec32', 'a87ff679a2f3e71d9181a67b7542122c', '8277e0910d750195b448797616e091ad', '92eb5ffee6ae2fec3ad71c777531578f', '45c48cce2e2d7fbdea1afc51c7c6ad26', '0cc175b9c0f1b6a831c399e269772661', 'c9f0f895fb98ab9159f51fd0297e236d', '0cc175b9c0f1b6a831c399e269772661', 'cbb184dd8e05c9709e5dcaedaa0495cf']
# 常见字符及其 MD5 哈希值的字典
common_chars = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}-"
md5_dict = {hashlib.md5(char.encode()).hexdigest(): char for char in common_chars}
# 还原原始字符串
flag = ''.join(md5_dict.get(md5_hash, '?') for md5_hash in output)
print("Flag:", flag)Pwn
[Week1] 签个到吧
nc一下即可,注意nc之后要ls





















 4776
4776

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








