个人仓库地址
Security: 参考若依 而实现的 权限认证框架 (gitee.com)
Securit使用
简单的使用
第一步:导入依赖
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>第二步:设置用户名和密码
在application.yml文件设置,不然启动后密码会在控制台打印,且每次都不一样,账号user
spring:
security:
user:
name: root
password: root或者使用Bean配置实现
package cn.djx.springsecurity.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.password.NoOpPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.provisioning.InMemoryUserDetailsManager;
@Configuration
public class SecurityConfig {
/**
* 定义认证逻辑
* @return
*/
@Bean
public UserDetailsService userDetailsService() {
// 1. 创建UserDetails对象
InMemoryUserDetailsManager manager = new InMemoryUserDetailsManager();
// 2. 创建User对象并添加到UserDetailsManager中
UserDetails user1 = User
.withUsername("XiaoMing"). //设置账号
password("123456"). // 设置密码
authorities("admin"). //设置角色
build();
UserDetails user2 = User.withUsername("XiaoWang").password("123456").authorities("admin").build();
manager.createUser(user1);
manager.createUser(user2);
return manager;
}
/**
* 设置编译器 不解析密码
* @return
*/
@Bean
public PasswordEncoder passwordEncoder(){
return NoOpPasswordEncoder.getInstance();
}
}
两个同时存在时 编程式 的方式生效
连接数据库使用
讲解一些实际场景
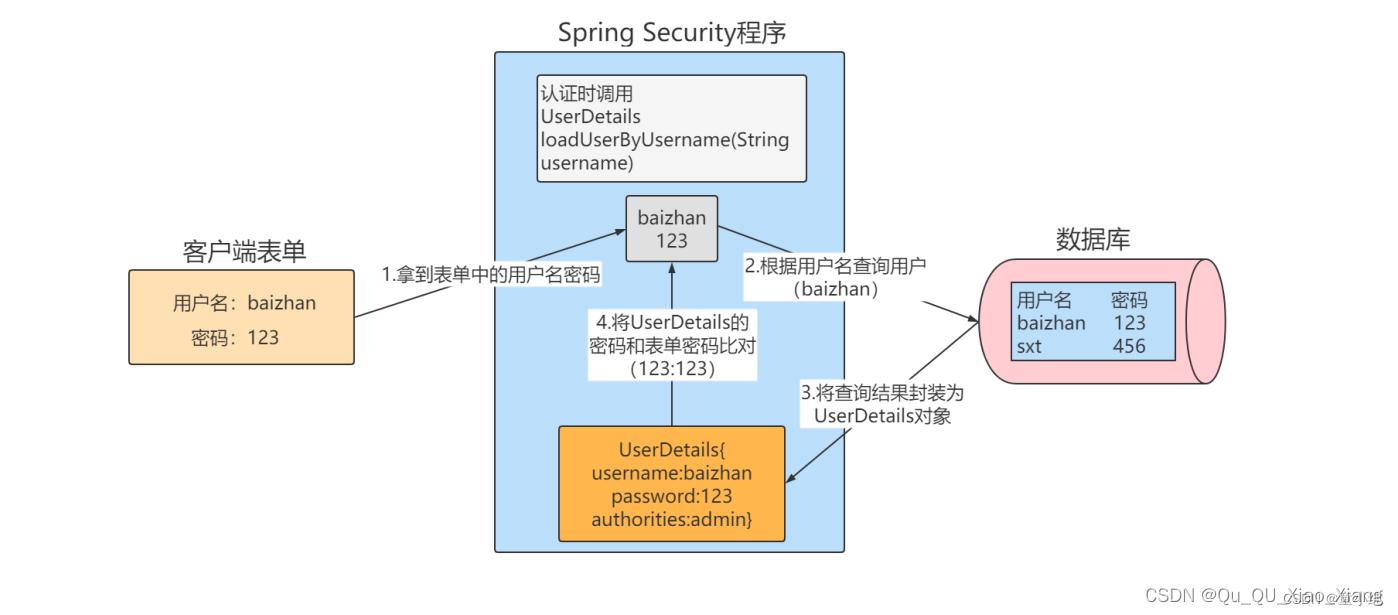
在实际项目过程中,认证逻辑需要自定义,将UserDetailsService接口的实现类放在Spring容器中即可自定义认证逻辑。
InMemoryUserDetailsManager就是UserDetailsService接口的一个实现类,他讲登录页传来的用户名密码和内存种的用户名和密码做匹配认证,我们可以自定义UserDetailsService接口的实现
package org.springframework.security.core.userdetails;
public interface UserDetailsService {
UserDetails loadUserByUsername(String username) throws UsernameNotFoundException;
}UserDetailsService的实现类必须重新loadUserByUsername方法,该方法定义了具体的认证逻辑,参数username是前端传过来的用户名,我们需要更具用户名查询到该用户(一般是从数据库中查询),并将查询到的用户封装成一个UserDetails对象,该对象是SpringSecurity提供的用户对象,包含用户名、密码、权限。SpringSecurity会更具UserDetails对象种的密码和客户端提供的密码比较。相同则认证通过,不同则认证失败
添加依赖
连接数据库的依赖 和 mybatis 的依赖,我这里使用的SpringBoot3.0以上版本
<!--MySQL-->
<dependency>
<groupId>com.mysql</groupId>
<artifactId>mysql-connector-j</artifactId>
<version>8.4.0</version>
</dependency>
<!--Lombok-->
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<optional>true</optional>
</dependency>
<!--Mybatis-->
<dependency>
<groupId>com.baomidou</groupId>
<artifactId>mybatis-plus-spring-boot3-starter</artifactId>
<version>3.5.6</version>
</dependency>编写配置文件application.yml
spring:
datasource:
url: jdbc:mysql://192.168.74.188:3306/security
username: root
password: 123456
data:
redis:
username: root
password: 123456
host: 192.168.74.188
port: 6379
database: 0
mybatis-plus:
mapper-locations: classpath*:mapper/*.xml
configuration:
log-impl: org.apache.ibatis.logging.stdout.StdOutImpl创建数据库并添加表
CREATE TABLE `sys_user` (
`id` BIGINT(20) NOT NULL AUTO_INCREMENT COMMENT '主键',
`user_name` VARCHAR(64) NOT NULL DEFAULT 'NULL' COMMENT '用户名',
`nick_name` VARCHAR(64) NOT NULL DEFAULT 'NULL' COMMENT '昵称',
`password` VARCHAR(64) NOT NULL DEFAULT 'NULL' COMMENT '密码',
`status` CHAR(1) DEFAULT '0' COMMENT '账号状态(0正常 1停用)',
`email` VARCHAR(64) DEFAULT NULL COMMENT '邮箱',
`phonenumber` VARCHAR(32) DEFAULT NULL COMMENT '手机号',
`sex` CHAR(1) DEFAULT NULL COMMENT '用户性别(0男,1女,2未知)',
`avatar` VARCHAR(128) DEFAULT NULL COMMENT '头像',
`user_type` CHAR(1) NOT NULL DEFAULT '1' COMMENT '用户类型(0管理员,1普通用户)',
`create_by` BIGINT(20) DEFAULT NULL COMMENT '创建人的用户id',
`create_time` DATETIME DEFAULT NULL COMMENT '创建时间',
`update_by` BIGINT(20) DEFAULT NULL COMMENT '更新人',
`update_time` DATETIME DEFAULT NULL COMMENT '更新时间',
`del_flag` INT(11) DEFAULT '0' COMMENT '删除标志(0代表未删除,1代表已删除)',
PRIMARY KEY (`id`)
) ENGINE=INNODB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4 COMMENT='用户表'
创建Dao层
package cn.djx.springsecurity.mapper;
import cn.djx.springsecurity.entity.Users;
import com.baomidou.mybatisplus.core.mapper.BaseMapper;
public interface UsersMapper extends BaseMapper<Users> {
}创建用户实体类
package cn.djx.springsecurity.entity;
import com.baomidou.mybatisplus.annotation.TableName;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
import java.io.Serializable;
import java.util.Date;
/**
* 用户表(User)实体类
*/
@Data
@TableName(value="sys_user")
@AllArgsConstructor
@NoArgsConstructor
public class Users implements Serializable {
private static final long serialVersionUID = -40356785423868312L;
/**
* 主键
*/
private Long id;
/**
* 用户名
*/
private String userName;
/**
* 昵称
*/
private String nickName;
/**
* 密码
*/
private String password;
/**
* 账号状态(0正常 1停用)
*/
private String status;
/**
* 邮箱
*/
private String email;
/**
* 手机号
*/
private String phonenumber;
/**
* 用户性别(0男,1女,2未知)
*/
private String sex;
/**
* 头像
*/
private String avatar;
/**
* 用户类型(0管理员,1普通用户)
*/
private String userType;
/**
* 创建人的用户id
*/
private Long createBy;
/**
* 创建时间
*/
private Date createTime;
/**
* 更新人
*/
private Long updateBy;
/**
* 更新时间
*/
private Date updateTime;
/**
* 删除标志(0代表未删除,1代表已删除)
*/
private Integer delFlag;
}对UserDetails进行实现
最下面的一些重写的方法 返回值 设置成true,因为暂时用不到
package cn.djx.springsecurity.entity;
import lombok.*;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.Collection;
@Data
@AllArgsConstructor
@RequiredArgsConstructor
@NoArgsConstructor
public class LoginUsers implements UserDetails {
@NonNull
private Users users;
private String token;
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
return null;
}
@Override
public String getPassword() {
return users.getPassword();
}
@Override
public String getUsername() {
return users.getUserName();
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return true;
}
}
重写UserDetailsService实现逻辑
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
import jakarta.annotation.Resource;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
@Service
public class UserDetailsServiceImpl implements UserDetailsService {
@Resource
private UsersMapper usersMapper;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
// 1.构建条件
LambdaQueryWrapper<Users> queryWrapper = new LambdaQueryWrapper<>();
queryWrapper.eq(Users::getUserName,username);
// 2.查询用户
Users users=usersMapper.selectOne(queryWrapper);
// 3.判断用户是否存在
if(users==null){
throw new RuntimeException("用户名密码错误");
}
// 4.返回用户信息
return new LoginUsers(users);
}
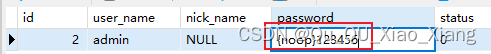
}注意:使用明文密码
当密码是明文是,需要在数据库字段数据前面添加{noop}
此时重启项目 随便访问一个 项目地址,输入这个账号密码
加密方式
SpringSecurity提供了很多加密方法,我们暂时使用默认的一种
向SpringIOC容器中注册
package cn.djx.springsecurity.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
@Configuration
public class SecurityConfig {
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
}记得注释或者删除这个
此时数据库
此时再次登录会提示 登录失败
获取加密后的密文
package cn.djx.springsecurity;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import jakarta.annotation.Resource;
import org.junit.jupiter.api.Test;
import org.springframework.boot.test.context.SpringBootTest;
import org.springframework.security.crypto.password.PasswordEncoder;
import java.util.List;
@SpringBootTest
class SpringSecurityApplicationTests {
@Resource
private UsersMapper usersMapper;
@Resource
private PasswordEncoder passwordEncoder;
@Test
public void passwordTest() {
String password = "123456";
String password1 = passwordEncoder.encode(password);
String password2 = passwordEncoder.encode(password);
System.out.println(password1);
System.out.println(password2);
}
}执行后:每次加密出现的密文都不一样,但他们都是 123456 加密后的 密文,具体是更具一个 盐值 计算的
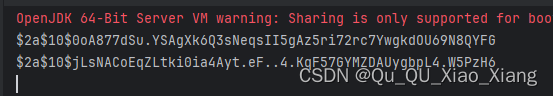
修改数据库密码
![]()
通过默认是的登录器测试,可以登录成功
自定义登录接口
编写Controller
package cn.djx.springsecurity.controller;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.ResponseResult;
import jakarta.annotation.Resource;
import org.springframework.web.bind.annotation.*;
@RestController
public class LoginController {
@Resource
private LoginService loginService;
@PostMapping("/login")
public ResponseResult login(@RequestBody Users users) {
return loginService.login(users);
}
}编写Service
package cn.djx.springsecurity.service;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.utils.ResponseResult;
public interface LoginService {
// 登录
ResponseResult login(Users users);
}
实现类
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.IdWorker;
import cn.djx.springsecurity.utils.RedisUtil;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.stereotype.Service;
import java.util.HashMap;
import java.util.Map;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Resource
private AuthenticationManager authenticationManager;
@Resource
private RedisUtil redisUtil;
@Resource
private UsersMapper usersMapper;
@Resource
private PasswordEncoder passwordEncoder;
@Resource
private ObjectMapper objectMapper;
@Override
public ResponseResult login(Users users) throws JsonProcessingException {
// 进行登录验证
// 创建包含用户名和密码的身份验证令牌
UsernamePasswordAuthenticationToken authenticationToken =
new UsernamePasswordAuthenticationToken(users.getUserName(), users.getPassword());
// 进行身份验证
Authentication auth = authenticationManager.authenticate(authenticationToken);
if (Objects.isNull(auth)){
throw new RuntimeException("登录失败");
}
// 验证通过
// 将身份验证后的用户信息转换为LoginUsers对象
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
// 生成token并将登录用户信息存储到redis中
String token = IdWorker.getId();
redisUtil.set(Constants.redis_token+token, objectMapper.writeValueAsString(loginUsers));
// 构建包含token的map作为登录成功的返回结果
Map<String, Object> map = new HashMap<>();
map.put("token", token);
return new ResponseResult(200,"登录成功",map);
}
}
修改SecurityConfig
因为我们自定义的登录接口 需要 放开
package cn.djx.springsecurity.config;
import jakarta.annotation.Resource;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.ProviderManager;
import org.springframework.security.authentication.dao.DaoAuthenticationProvider;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.SecurityFilterChain;
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Resource
private UserDetailsService userDetailsService;
@Bean
// 返回一个 BCryptPasswordEncoder 实例作为 PasswordEncode
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
// CSRF禁用,因为不使用session
http.csrf().disable();
// 禁用HTTP响应标头
http.headers().cacheControl().disable();
// 基于token,所以不需要session
http.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
http.authorizeHttpRequests(auth -> auth
.requestMatchers("/login", "/register")
// 除上面外的所有请求全部需要鉴权认证
.permitAll().anyRequest().authenticated());
return http.build();
}
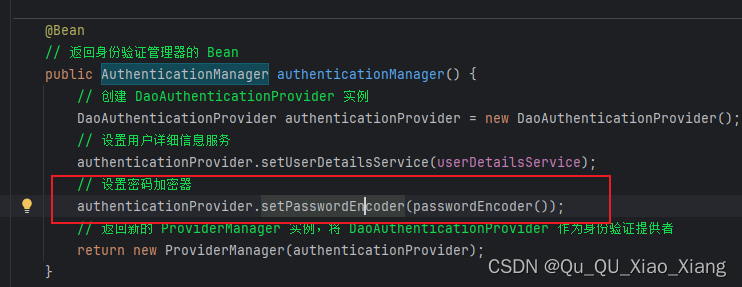
@Bean
// 返回身份验证管理器的 Bean
public AuthenticationManager authenticationManager() {
// 创建 DaoAuthenticationProvider 实例
DaoAuthenticationProvider authenticationProvider = new DaoAuthenticationProvider();
// 设置用户详细信息服务
authenticationProvider.setUserDetailsService(userDetailsService);
// 设置密码加密器
authenticationProvider.setPasswordEncoder(passwordEncoder());
// 返回新的 ProviderManager 实例,将 DaoAuthenticationProvider 作为身份验证提供者
return new ProviderManager(authenticationProvider);
}
}
此时自定义登录接口
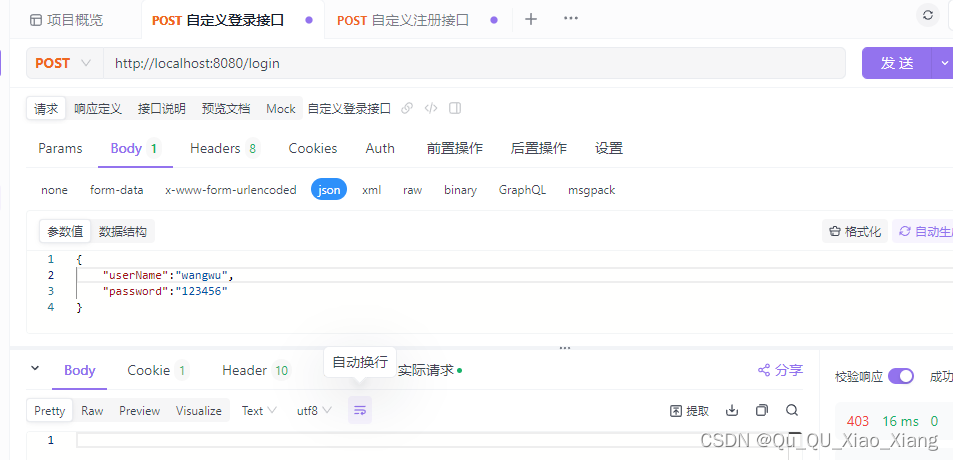
出现问题
上面已经添加过了,这是 自己 练习是出现的 错误 出现 给大家提个醒
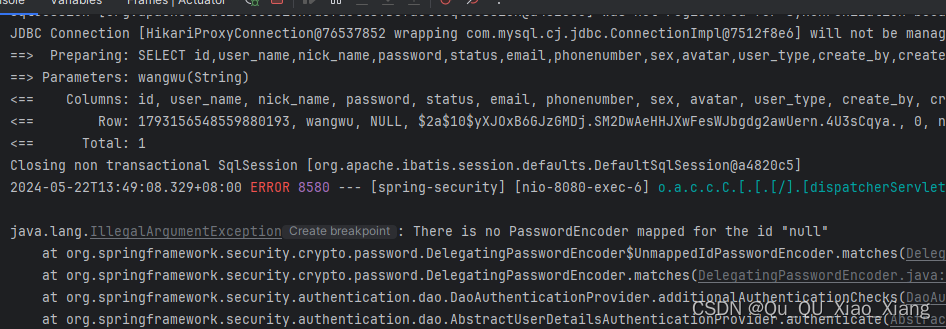
没有设置密码加密器
自定义注册
和登录差不多
编写Controller注册接口
package cn.djx.springsecurity.controller;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import jakarta.annotation.Resource;
import org.springframework.web.bind.annotation.*;
@RestController
public class LoginController {
@Resource
private LoginService loginService;
@PostMapping("/login")
public ResponseResult login(@RequestBody Users users) throws JsonProcessingException {
return loginService.login(users);
}
@PostMapping("/register")
public ResponseResult register(@RequestBody Users users) {
return loginService.register(users);
}
}
编写新增用service
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.IdWorker;
import cn.djx.springsecurity.utils.RedisUtil;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.stereotype.Service;
import java.util.HashMap;
import java.util.Map;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Resource
private AuthenticationManager authenticationManager;
@Resource
private RedisUtil redisUtil;
@Resource
private UsersMapper usersMapper;
@Resource
private PasswordEncoder passwordEncoder;
@Resource
private ObjectMapper objectMapper;
@Override
public ResponseResult login(Users users) throws JsonProcessingException {
// 进行登录验证
// 创建包含用户名和密码的身份验证令牌
UsernamePasswordAuthenticationToken authenticationToken =
new UsernamePasswordAuthenticationToken(users.getUserName(), users.getPassword());
// 进行身份验证
Authentication auth = authenticationManager.authenticate(authenticationToken);
if (Objects.isNull(auth)){
throw new RuntimeException("登录失败");
}
// 验证通过
// 将身份验证后的用户信息转换为LoginUsers对象
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
// 生成token并将登录用户信息存储到redis中
String token = IdWorker.getId();
redisUtil.set(Constants.redis_token+token, objectMapper.writeValueAsString(loginUsers));
// 构建包含token的map作为登录成功的返回结果
Map<String, Object> map = new HashMap<>();
map.put("token", token);
return new ResponseResult(200,"登录成功",map);
}
@Override
public ResponseResult register(Users users) {
// 密码加密
users.setPassword(passwordEncoder.encode(users.getPassword()));
// 保存用户信息到数据库
int row = usersMapper.insert(users);
if (row > 0){
return new ResponseResult(200,"注册成功",null);
}
return new ResponseResult(500,"注册失败",null);
}
}
注意:记得放行注册接口
上面我已经写好了
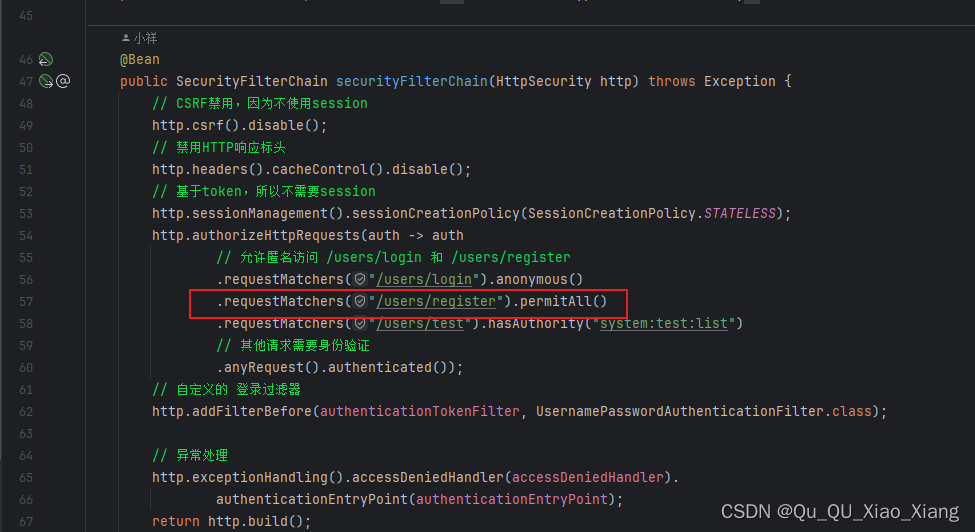
自定义token过滤器
登录时我们一般会将 Token 存到数据库里面,这里我们需要自定义下 过滤器
package cn.djx.springsecurity.filter;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.utils.RedisUtil;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.util.StringUtils;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@Configuration
public class AuthenticationTokenFilter extends OncePerRequestFilter {
@Resource
private RedisUtil redisUtil;
@Resource
private ObjectMapper objectMapper;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {
// 从请求头中获取token
String token = request.getHeader(Constants.header_token);
if (!StringUtils.hasText(token)){
// 如果请求头中没有token,则直接放行
filterChain.doFilter(request, response);
return;
}
String jsonLgoinUsers = (String) redisUtil.get(Constants.redis_token+token);
LoginUsers loginUsers = objectMapper.readValue(jsonLgoinUsers, LoginUsers.class);
if (loginUsers == null){
// 如果token不存在
throw new ServletException("登录超时,请重新登录");
}
// 将token放入loginUsers中
loginUsers.setToken(token);
// 如果token存在,则将用户信息放入request中
UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(loginUsers,null,null);
// 将用户信息放入SecurityContextHolder中
SecurityContextHolder.getContext().setAuthentication(authenticationToken);
filterChain.doFilter(request, response);
}
}
将自定义过滤器添加到Security过滤链中
package cn.djx.springsecurity.config;
import cn.djx.springsecurity.filter.AuthenticationTokenFilter;
import jakarta.annotation.Resource;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.ProviderManager;
import org.springframework.security.authentication.dao.DaoAuthenticationProvider;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Resource
private UserDetailsService userDetailsService;
@Resource
private AuthenticationTokenFilter authenticationTokenFilter;
@Bean
// 返回一个 BCryptPasswordEncoder 实例作为 PasswordEncode
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
// CSRF禁用,因为不使用session
http.csrf().disable();
// 禁用HTTP响应标头
http.headers().cacheControl().disable();
// 基于token,所以不需要session
http.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
http.authorizeHttpRequests(auth -> auth
.requestMatchers("/login", "/register")
// 除上面外的所有请求全部需要鉴权认证
.permitAll().anyRequest().authenticated());
// 自定义的 登录过滤器
http.addFilterBefore(authenticationTokenFilter, UsernamePasswordAuthenticationFilter.class);
return http.build();
}
@Bean
// 返回身份验证管理器的 Bean
public AuthenticationManager authenticationManager() {
// 创建 DaoAuthenticationProvider 实例
DaoAuthenticationProvider authenticationProvider = new DaoAuthenticationProvider();
// 设置用户详细信息服务
authenticationProvider.setUserDetailsService(userDetailsService);
// 设置密码加密器
authenticationProvider.setPasswordEncoder(passwordEncoder());
// 返回新的 ProviderManager 实例,将 DaoAuthenticationProvider 作为身份验证提供者
return new ProviderManager(authenticationProvider);
}
}
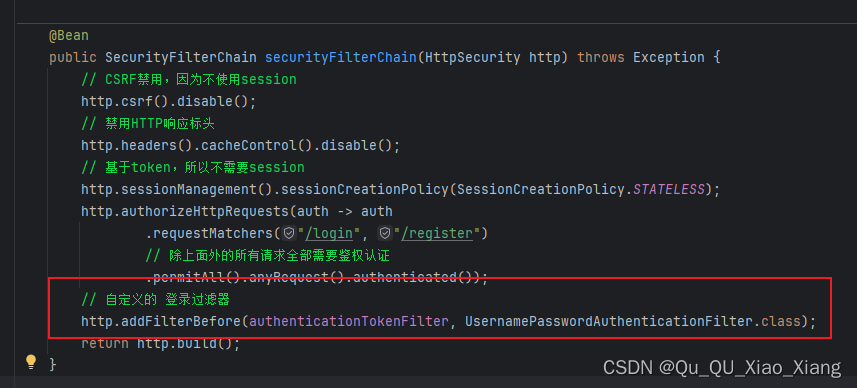
自定义注销
编写Controller
package cn.djx.springsecurity.controller;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import jakarta.annotation.Resource;
import org.springframework.web.bind.annotation.*;
@RestController
@RequestMapping("/users")
public class LoginController {
@Resource
private LoginService loginService;
@PostMapping("/login")
public ResponseResult login(@RequestBody Users users) throws JsonProcessingException {
return loginService.login(users);
}
@PostMapping("/register")
public ResponseResult register(@RequestBody Users users) {
return loginService.register(users);
}
@PostMapping("/logout")
public ResponseResult logout() {
return loginService.logout();
}
@GetMapping("/hello")
public String hello() {
return "hello";
}
}
退出的Service
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.IdWorker;
import cn.djx.springsecurity.utils.RedisUtil;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.stereotype.Service;
import java.util.HashMap;
import java.util.Map;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Resource
private AuthenticationManager authenticationManager;
@Resource
private RedisUtil redisUtil;
@Resource
private UsersMapper usersMapper;
@Resource
private PasswordEncoder passwordEncoder;
@Resource
private ObjectMapper objectMapper;
@Override
public ResponseResult login(Users users) throws JsonProcessingException {
// 进行登录验证
// 创建包含用户名和密码的身份验证令牌
UsernamePasswordAuthenticationToken authenticationToken =
new UsernamePasswordAuthenticationToken(users.getUserName(), users.getPassword());
// 进行身份验证
Authentication auth = authenticationManager.authenticate(authenticationToken);
if (Objects.isNull(auth)){
throw new RuntimeException("登录失败");
}
// 验证通过
// 将身份验证后的用户信息转换为LoginUsers对象
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
// 生成token并将登录用户信息存储到redis中
String token = IdWorker.getId();
redisUtil.set(Constants.redis_token+token, objectMapper.writeValueAsString(loginUsers));
// 构建包含token的map作为登录成功的返回结果
Map<String, Object> map = new HashMap<>();
map.put("token", token);
return new ResponseResult(200,"登录成功",map);
}
@Override
public ResponseResult register(Users users) {
// 密码加密
users.setPassword(passwordEncoder.encode(users.getPassword()));
// 保存用户信息到数据库
int row = usersMapper.insert(users);
if (row > 0){
return new ResponseResult(200,"注册成功",null);
}
return new ResponseResult(500,"注册失败",null);
}
@Override
public ResponseResult logout() {
// 获取当前认证信息
Authentication auth = SecurityContextHolder.getContext().getAuthentication();
// 获取登录用户信息
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
// 从redis中移除用户的token
redisUtil.remove(Constants.redis_token+loginUsers.getToken());
// 清空当前认证信息
SecurityContextHolder.getContext().setAuthentication(null);
// 返回注销成功的响应结果
return new ResponseResult(200,"注销成功",null);
}
}
注意:记得放行
设置用户访问权限认证
第一步:添加注解
@EnableGlobalMethodSecurity(prePostEnabled = true)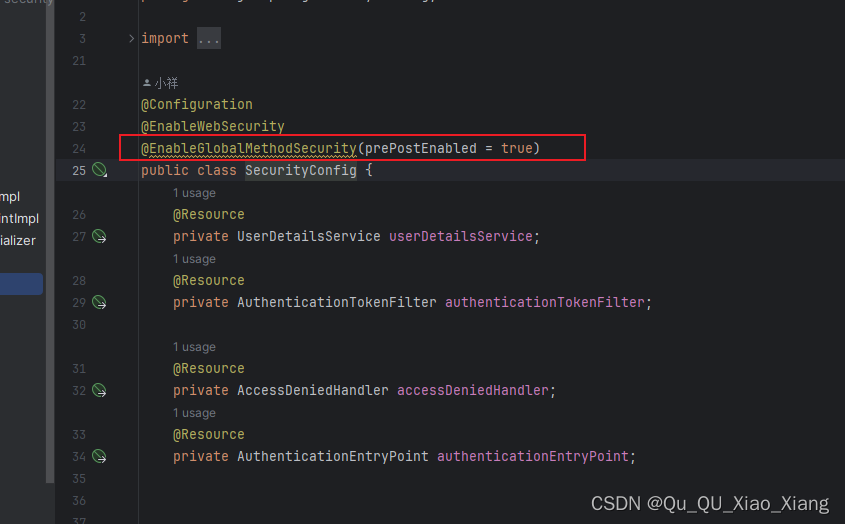
第二步:在UserDetails添加权限
package cn.djx.springsecurity.entity;
import cn.djx.springsecurity.config.CustomAuthorityDeserializer;
import com.alibaba.fastjson2.annotation.JSONField;
import com.fasterxml.jackson.databind.annotation.JsonDeserialize;
import lombok.*;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.Collection;
import java.util.List;
import java.util.stream.Collectors;
@Data
@AllArgsConstructor
@RequiredArgsConstructor
@NoArgsConstructor
public class LoginUsers implements UserDetails {
@NonNull
private Users users;
private String token;
@NonNull
private List<String> permission;
// GrantedAuthority 序列化 问题
@JSONField(serialize = false)
private List<GrantedAuthority> authorities;
@Override
// GrantedAuthority 序列化 问题
@JsonDeserialize(using = CustomAuthorityDeserializer.class)
public Collection<? extends GrantedAuthority> getAuthorities() {
if (authorities!= null) {
return authorities;
}
authorities = permission.stream().map(SimpleGrantedAuthority::new).collect(Collectors.toList());
return authorities;
}
@Override
public String getPassword() {
return users.getPassword();
}
@Override
public String getUsername() {
return users.getUserName();
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return true;
}
}
添加一个类CustomAuthorityDeserializer
package cn.djx.springsecurity.config;
import com.fasterxml.jackson.core.JsonParser;
import com.fasterxml.jackson.core.JsonProcessingException;
import com.fasterxml.jackson.databind.DeserializationContext;
import com.fasterxml.jackson.databind.JsonDeserializer;
import com.fasterxml.jackson.databind.JsonNode;
import com.fasterxml.jackson.databind.ObjectMapper;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import java.io.IOException;
import java.util.Iterator;
import java.util.LinkedList;
public class CustomAuthorityDeserializer extends JsonDeserializer {
@Override
public Object deserialize(JsonParser p, DeserializationContext ctxt) throws IOException, JsonProcessingException {
ObjectMapper mapper = (ObjectMapper) p.getCodec();
JsonNode jsonNode = mapper.readTree(p);
LinkedList<GrantedAuthority> grantedAuthorities = new LinkedList<>();
Iterator<JsonNode> elements = jsonNode.elements();
while (elements.hasNext()) {
JsonNode next = elements.next();
JsonNode authority = next.get("authority");
//将得到的值放入链表 最终返回该链表
grantedAuthorities.add(new SimpleGrantedAuthority(authority.asText()));
}
return grantedAuthorities;
}
}
第三步:配置权限 目前写死
UserDetailsServiceImpl实现类中获取权限
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
import jakarta.annotation.Resource;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
@Service
public class UserDetailsServiceImpl implements UserDetailsService {
@Resource
private UsersMapper usersMapper;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
// 1.构建条件
LambdaQueryWrapper<Users> queryWrapper = new LambdaQueryWrapper<>();
queryWrapper.eq(Users::getUserName,username);
// 2.查询用户
Users users=usersMapper.selectOne(queryWrapper);
// 3.判断用户是否存在
if(users==null){
throw new RuntimeException("用户名密码错误");
}
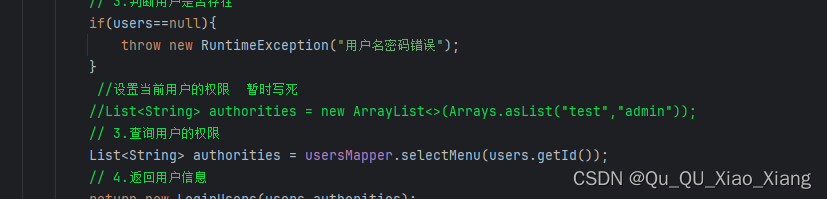
//设置当前用户的权限 暂时写死
List<String> authorities = new ArrayList<>(Arrays.asList("test","admin"));
// 4.返回用户信息
return new LoginUsers(users,authorities);
}
}
第四步:过滤器添加权限
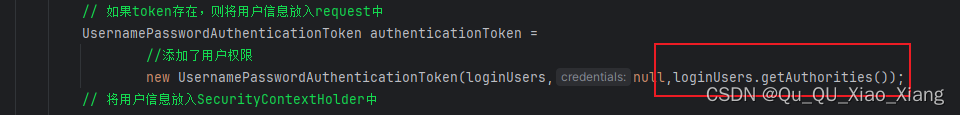
package cn.djx.springsecurity.filter;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.utils.RedisUtil;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.util.StringUtils;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@Configuration
public class AuthenticationTokenFilter extends OncePerRequestFilter {
@Resource
private RedisUtil redisUtil;
@Resource
private ObjectMapper objectMapper;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {
// 从请求头中获取token
String token = request.getHeader(Constants.header_token);
if (!StringUtils.hasText(token)){
// 如果请求头中没有token,则直接放行
filterChain.doFilter(request, response);
return;
}
String jsonLgoinUsers = (String) redisUtil.get(Constants.redis_token+token);
if (!StringUtils.hasText(jsonLgoinUsers)){
// 如果token不存在
throw new ServletException("登录超时,请重新登录");
}
LoginUsers loginUsers = objectMapper.readValue(jsonLgoinUsers, LoginUsers.class);
// 将token放入loginUsers中
loginUsers.setToken(token);
// 如果token存在,则将用户信息放入request中
UsernamePasswordAuthenticationToken authenticationToken =
//添加了用户权限
new UsernamePasswordAuthenticationToken(loginUsers,null,loginUsers.getAuthorities());
// 将用户信息放入SecurityContextHolder中
SecurityContextHolder.getContext().setAuthentication(authenticationToken);
filterChain.doFilter(request, response);
}
}
第五步:Controller添加权限注解
package cn.djx.springsecurity.controller;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.ResponseResult;
import com.fasterxml.jackson.core.JsonProcessingException;
import jakarta.annotation.Resource;
import org.springframework.security.access.prepost.PreAuthorize;
import org.springframework.web.bind.annotation.*;
@RestController
@RequestMapping("/users")
public class LoginController {
@Resource
private LoginService loginService;
@PostMapping("/login")
public ResponseResult login(@RequestBody Users users) throws JsonProcessingException {
return loginService.login(users);
}
@PostMapping("/register")
public ResponseResult register(@RequestBody Users users) {
return loginService.register(users);
}
@PostMapping("/logout")
public ResponseResult logout() {
return loginService.logout();
}
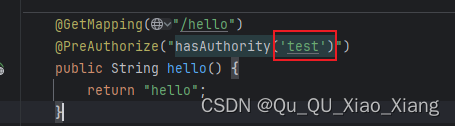
@GetMapping("/hello")
@PreAuthorize("hasAuthority('test')")
public String hello() {
return "hello";
}
}
此时请求 只有有 该权限的用户可以 房屋这个接口
从数据库查询用户权限
添加数据表
CREATE DATABASE /*!32312 IF NOT EXISTS*/`sg_security` /*!40100 DEFAULT CHARACTER SET utf8mb4 */;
USE `sg_security`;
/*Table structure for table `sys_menu` */
DROP TABLE IF EXISTS `sys_menu`;
CREATE TABLE `sys_menu` (
`id` bigint(20) NOT NULL AUTO_INCREMENT,
`menu_name` varchar(64) NOT NULL DEFAULT 'NULL' COMMENT '菜单名',
`path` varchar(200) DEFAULT NULL COMMENT '路由地址',
`component` varchar(255) DEFAULT NULL COMMENT '组件路径',
`visible` char(1) DEFAULT '0' COMMENT '菜单状态(0显示 1隐藏)',
`status` char(1) DEFAULT '0' COMMENT '菜单状态(0正常 1停用)',
`perms` varchar(100) DEFAULT NULL COMMENT '权限标识',
`icon` varchar(100) DEFAULT '#' COMMENT '菜单图标',
`create_by` bigint(20) DEFAULT NULL,
`create_time` datetime DEFAULT NULL,
`update_by` bigint(20) DEFAULT NULL,
`update_time` datetime DEFAULT NULL,
`del_flag` int(11) DEFAULT '0' COMMENT '是否删除(0未删除 1已删除)',
`remark` varchar(500) DEFAULT NULL COMMENT '备注',
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4 COMMENT='菜单表';
/*Table structure for table `sys_role` */
DROP TABLE IF EXISTS `sys_role`;
CREATE TABLE `sys_role` (
`id` bigint(20) NOT NULL AUTO_INCREMENT,
`name` varchar(128) DEFAULT NULL,
`role_key` varchar(100) DEFAULT NULL COMMENT '角色权限字符串',
`status` char(1) DEFAULT '0' COMMENT '角色状态(0正常 1停用)',
`del_flag` int(1) DEFAULT '0' COMMENT 'del_flag',
`create_by` bigint(200) DEFAULT NULL,
`create_time` datetime DEFAULT NULL,
`update_by` bigint(200) DEFAULT NULL,
`update_time` datetime DEFAULT NULL,
`remark` varchar(500) DEFAULT NULL COMMENT '备注',
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=3 DEFAULT CHARSET=utf8mb4 COMMENT='角色表';
/*Table structure for table `sys_role_menu` */
DROP TABLE IF EXISTS `sys_role_menu`;
CREATE TABLE `sys_role_menu` (
`role_id` bigint(200) NOT NULL AUTO_INCREMENT COMMENT '角色ID',
`menu_id` bigint(200) NOT NULL DEFAULT '0' COMMENT '菜单id',
PRIMARY KEY (`role_id`,`menu_id`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4;
/*Table structure for table `sys_user` */
DROP TABLE IF EXISTS `sys_user`;
CREATE TABLE `sys_user` (
`id` bigint(20) NOT NULL AUTO_INCREMENT COMMENT '主键',
`user_name` varchar(64) NOT NULL DEFAULT 'NULL' COMMENT '用户名',
`nick_name` varchar(64) NOT NULL DEFAULT 'NULL' COMMENT '昵称',
`password` varchar(64) NOT NULL DEFAULT 'NULL' COMMENT '密码',
`status` char(1) DEFAULT '0' COMMENT '账号状态(0正常 1停用)',
`email` varchar(64) DEFAULT NULL COMMENT '邮箱',
`phonenumber` varchar(32) DEFAULT NULL COMMENT '手机号',
`sex` char(1) DEFAULT NULL COMMENT '用户性别(0男,1女,2未知)',
`avatar` varchar(128) DEFAULT NULL COMMENT '头像',
`user_type` char(1) NOT NULL DEFAULT '1' COMMENT '用户类型(0管理员,1普通用户)',
`create_by` bigint(20) DEFAULT NULL COMMENT '创建人的用户id',
`create_time` datetime DEFAULT NULL COMMENT '创建时间',
`update_by` bigint(20) DEFAULT NULL COMMENT '更新人',
`update_time` datetime DEFAULT NULL COMMENT '更新时间',
`del_flag` int(11) DEFAULT '0' COMMENT '删除标志(0代表未删除,1代表已删除)',
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=3 DEFAULT CHARSET=utf8mb4 COMMENT='用户表';
/*Table structure for table `sys_user_role` */
DROP TABLE IF EXISTS `sys_user_role`;
CREATE TABLE `sys_user_role` (
`user_id` bigint(200) NOT NULL AUTO_INCREMENT COMMENT '用户id',
`role_id` bigint(200) NOT NULL DEFAULT '0' COMMENT '角色id',
PRIMARY KEY (`user_id`,`role_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
编写Mapper
package cn.djx.springsecurity.mapper;
import cn.djx.springsecurity.entity.Users;
import com.baomidou.mybatisplus.core.mapper.BaseMapper;
import org.apache.ibatis.annotations.Param;
import java.util.List;
public interface UsersMapper extends BaseMapper<Users> {
public List<String> selectMenu(@Param("userId") Long userId);
}
只查询当前用户 的 权限
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN" "http://mybatis.org/dtd/mybatis-3-mapper.dtd" >
<mapper namespace="cn.djx.springsecurity.mapper.UsersMapper">
<select id="selectMenu" resultType="java.lang.String">
select DISTINCT m.perms
from sys_user_role ur
LEFT JOIN sys_role r on r.id = ur.role_id
left join sys_role_menu rm on rm.role_id = r.id
left join sys_menu m on rm.menu_id = m.id
WHERE ur.user_id=#{userId}
</select>
</mapper>
修改UserDetailsServiceImpl
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import com.baomidou.mybatisplus.core.conditions.query.LambdaQueryWrapper;
import jakarta.annotation.Resource;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import java.util.List;
@Service
public class UserDetailsServiceImpl implements UserDetailsService {
@Resource
private UsersMapper usersMapper;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
// 1.构建条件
LambdaQueryWrapper<Users> queryWrapper = new LambdaQueryWrapper<>();
queryWrapper.eq(Users::getUserName,username);
// 2.查询用户
Users users=usersMapper.selectOne(queryWrapper);
// 3.判断用户是否存在
if(users==null){
throw new RuntimeException("用户名密码错误");
}
//设置当前用户的权限 暂时写死
//List<String> authorities = new ArrayList<>(Arrays.asList("test","admin"));
// 3.查询用户的权限
List<String> authorities = usersMapper.selectMenu(users.getId());
// 4.返回用户信息
return new LoginUsers(users,authorities);
}
}
自定义失败处理器
Web工具列
package cn.djx.springsecurity.utils;
import jakarta.servlet.http.HttpServletResponse;
import java.io.IOException;
public class WebUtils
{
/**
* 将字符串渲染到客户端
*
* @param response 渲染对象
* @param string 待渲染的字符串
* @return null
*/
public static String renderString(HttpServletResponse response, String string) {
try
{
response.setStatus(200);
response.setContentType("application/json");
response.setCharacterEncoding("utf-8");
response.getWriter().print(string);
}
catch (IOException e)
{
e.printStackTrace();
}
return null;
}
}认证失败处理器
package cn.djx.springsecurity.config;
import cn.djx.springsecurity.utils.ResponseResult;
import cn.djx.springsecurity.utils.WebUtils;
import com.alibaba.fastjson2.JSON;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.http.HttpStatus;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.stereotype.Component;
import java.io.IOException;
@Component
public class AuthenticationEntryPointImpl implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException authException) throws IOException, ServletException {
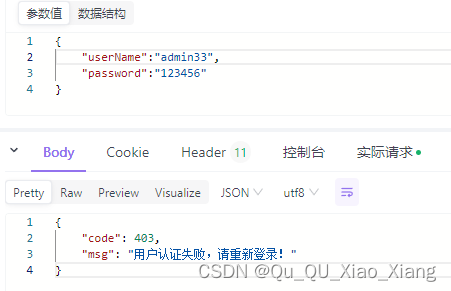
ResponseResult result = new ResponseResult(HttpStatus.FORBIDDEN.value(), "用户认证失败,请重新登录!");
String json = JSON.toJSONString(result);
WebUtils.renderString(response, json);
}
}
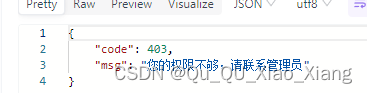
权限不足处理器
package cn.djx.springsecurity.config;
import cn.djx.springsecurity.utils.ResponseResult;
import cn.djx.springsecurity.utils.WebUtils;
import com.alibaba.fastjson2.JSON;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.http.HttpStatus;
import org.springframework.security.access.AccessDeniedException;
import org.springframework.security.web.access.AccessDeniedHandler;
import org.springframework.stereotype.Component;
import java.io.IOException;
@Component
public class AccessDeniedHandlerImpl implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest request, HttpServletResponse response, AccessDeniedException accessDeniedException) throws IOException, ServletException {
ResponseResult result = new ResponseResult(HttpStatus.FORBIDDEN.value(), "您的权限不够,请联系管理员");
String json = JSON.toJSONString(result);
WebUtils.renderString(response, json);
}
}
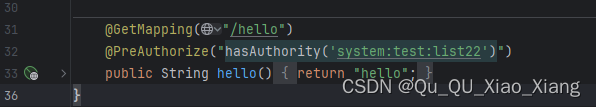
效果
当权限不匹配时
登录失败时
其他权限效验方式
多个权限
hasAnyAuthority方法可以传入多个权限,只有用户有其中任意一个权限都可以访问对应资源。
@PreAuthorize("hasAnyAuthority('admin','test','system:dept:list')")
public String hello(){
return "hello";
}
角色权限
hasRole要求有对应的角色才可以访问,但是它内部会把我们传入的参数拼接上 ROLE_ 后再去比较。所以这种情况下要用用户对应的权限也要有 ROLE_ 这个前缀才可以。
@PreAuthorize("hasRole('system:dept:list')")
public String hello(){
return "hello";
}
角色多个权限
hasAnyRole 要求有对应的角色才可以访问,但是它内部会把我们传入的参数拼接上 ROLE_ 后再去比较。所以这种情况下要用用户对应的权限也要有 ROLE_ 这个前缀才可以。
@PreAuthorize("hasAnyRole('admin','system:dept:list')")
public String hello(){
return "hello";
}
自定义权限校验方法
定义校验方法
package cn.djx.springsecurity.expression;
import cn.djx.springsecurity.entity.LoginUsers;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.stereotype.Component;
import java.util.List;
@Component("ex")
public class SGExpressionRoot {
public boolean hasPermission(String authority) {
// 获取当前登录用户的权限
Authentication authentication = SecurityContextHolder.getContext().getAuthentication();
LoginUsers loginUser = (LoginUsers) authentication.getPrincipal();
List<String> permissions = loginUser.getPermission();
// 判断当前用户是否有权限
return permissions.contains(authority);
}
}
使用自定义校验方法
@GetMapping("/hello")
@PreAuthorize("@ex.hasPermission('system:test:list')")
public String hello() {
return "hello";
}基于配置的权限配置

使用JWT改进
使用了国人的工具库
Hutool🍬一个功能丰富且易用的Java工具库,涵盖了字符串、数字、集合、编码、日期、文件、IO、加密、数据库JDBC、JSON、HTTP客户端等功能。
<dependency>
<groupId>cn.hutool</groupId>
<artifactId>hutool-all</artifactId>
<version>5.8.26</version>
</dependency>改进了AuthenticationTokenFilter认证过滤器
package cn.djx.springsecurity.filter;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.utils.RedisUtil;
import cn.hutool.jwt.JWT;
import cn.hutool.jwt.JWTUtil;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.util.StringUtils;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@Configuration
public class AuthenticationTokenFilter extends OncePerRequestFilter {
@Resource
private RedisUtil redisUtil;
@Resource
private ObjectMapper objectMapper;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {
// 从请求头中获取token
String token = request.getHeader(Constants.header_token);
if (!StringUtils.hasText(token)){
// 如果请求头中没有token,则直接放行
filterChain.doFilter(request, response);
return;
}
// 解密 jwt token
final JWT jwt = JWTUtil.parseToken(token);
// 获取userid
String key = jwt.getPayload("uid").toString();
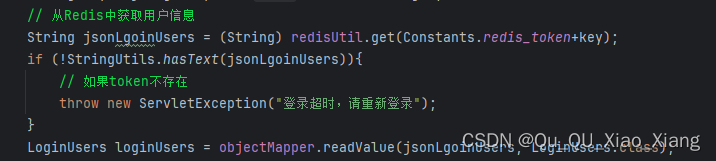
// 从Redis中获取用户信息
String jsonLgoinUsers = (String) redisUtil.get(Constants.redis_token+key);
if (!StringUtils.hasText(jsonLgoinUsers)){
// 如果token不存在
throw new ServletException("登录超时,请重新登录");
}
LoginUsers loginUsers = objectMapper.readValue(jsonLgoinUsers, LoginUsers.class);
// 将token放入loginUsers中
loginUsers.setToken(token);
// 如果token存在,则将用户信息放入request中
UsernamePasswordAuthenticationToken authenticationToken =
//添加了用户权限
new UsernamePasswordAuthenticationToken(loginUsers,null,loginUsers.getAuthorities());
// 将用户信息放入SecurityContextHolder中
SecurityContextHolder.getContext().setAuthentication(authenticationToken);
filterChain.doFilter(request, response);
}
}
改进了自定义登录LoginServiceImpl
package cn.djx.springsecurity.service.impl;
import cn.djx.springsecurity.constants.Constants;
import cn.djx.springsecurity.entity.LoginUsers;
import cn.djx.springsecurity.entity.Users;
import cn.djx.springsecurity.mapper.UsersMapper;
import cn.djx.springsecurity.service.LoginService;
import cn.djx.springsecurity.utils.RedisUtil;
import cn.djx.springsecurity.utils.ResponseResult;
import cn.hutool.jwt.JWTUtil;
import com.fasterxml.jackson.core.JsonProcessingException;
import com.fasterxml.jackson.databind.ObjectMapper;
import jakarta.annotation.Resource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.stereotype.Service;
import java.util.HashMap;
import java.util.Map;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Resource
private AuthenticationManager authenticationManager;
@Resource
private RedisUtil redisUtil;
@Resource
private UsersMapper usersMapper;
@Resource
private PasswordEncoder passwordEncoder;
@Resource
private ObjectMapper objectMapper;
@Override
public ResponseResult login(Users users) throws JsonProcessingException {
// 进行登录验证
// 创建包含用户名和密码的身份验证令牌
UsernamePasswordAuthenticationToken authenticationToken =
new UsernamePasswordAuthenticationToken(users.getUserName(), users.getPassword());
// 进行身份验证
Authentication auth = authenticationManager.authenticate(authenticationToken);
if (Objects.isNull(auth)){
throw new RuntimeException("登录失败");
}
// 验证通过
// 将身份验证后的用户信息转换为LoginUsers对象
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
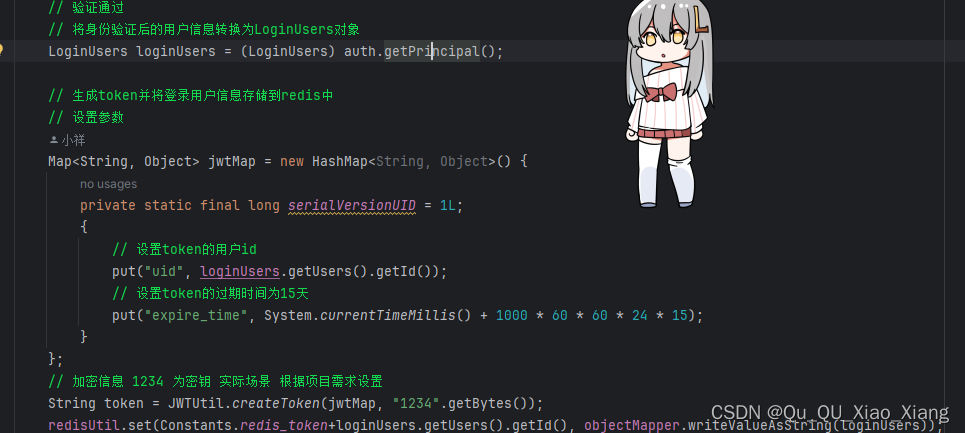
// 生成token并将登录用户信息存储到redis中
// 设置参数
Map<String, Object> jwtMap = new HashMap<String, Object>() {
private static final long serialVersionUID = 1L;
{
// 设置token的用户id
put("uid", loginUsers.getUsers().getId());
// 设置token的过期时间为15天
put("expire_time", System.currentTimeMillis() + 1000 * 60 * 60 * 24 * 15);
}
};
// 加密信息 1234 为密钥 实际场景 根据项目需求设置
String token = JWTUtil.createToken(jwtMap, "1234".getBytes());
redisUtil.set(Constants.redis_token+loginUsers.getUsers().getId(), objectMapper.writeValueAsString(loginUsers));
// 构建包含token的map作为登录成功的返回结果
Map<String, Object> result = new HashMap<>();
result.put("token", token);
return new ResponseResult(200,"登录成功",result);
}
@Override
public ResponseResult register(Users users) {
// 密码加密
users.setPassword(passwordEncoder.encode(users.getPassword()));
// 保存用户信息到数据库
int row = usersMapper.insert(users);
if (row > 0){
return new ResponseResult(200,"注册成功",null);
}
return new ResponseResult(500,"注册失败",null);
}
@Override
public ResponseResult logout() {
// 获取当前认证信息
Authentication auth = SecurityContextHolder.getContext().getAuthentication();
// 获取登录用户信息
LoginUsers loginUsers = (LoginUsers) auth.getPrincipal();
// 从redis中移除用户的token
redisUtil.remove(Constants.redis_token+loginUsers.getToken());
// 清空当前认证信息
SecurityContextHolder.getContext().setAuthentication(null);
// 返回注销成功的响应结果
return new ResponseResult(200,"注销成功",null);
}
}





















 1572
1572

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








