前言:
前面我有提到过Kubernetes如何部署Dashboard,怎样获取token进行登录,那么其实还存在很多问题。每次都要去抓token比较繁琐,那么是不是有更好的校验方式呢?比如我们常用的用户名密码形式,答案是:有!!!,好了废话不多说,直接上干货。
1.在装过dashboard环境下。我们去master节点新增一个文件,如果是ha会有多个master,那么每个master同下操作。里面内容结构是:用户名,密码(用户名和密码要保持一致),唯一ID。
[root@master ~]# echo "admin,admin,1" > /etc/kubernetes/pki/basic_auth_file
2.修改配置kube-apiserver.yaml文件。
[root@master ~]# cat /etc/kubernetes/manifests/kube-apiserver.yaml
apiVersion: v1
kind: Pod
metadata:
annotations:
kubeadm.kubernetes.io/kube-apiserver.advertise-address.endpoint: 192.168.168.100:6443
creationTimestamp: null
labels:
component: kube-apiserver
tier: control-plane
name: kube-apiserver
namespace: kube-system
spec:
containers:
- command:
- kube-apiserver
- --advertise-address=192.168.168.100
- --allow-privileged=true
- --authorization-mode=Node,RBAC
- --client-ca-file=/etc/kubernetes/pki/ca.crt
- --enable-admission-plugins=NodeRestriction
- --enable-bootstrap-token-auth=true
- --etcd-cafile=/etc/kubernetes/pki/etcd/ca.crt
- --etcd-certfile=/etc/kubernetes/pki/apiserver-etcd-client.crt
- --etcd-keyfile=/etc/kubernetes/pki/apiserver-etcd-client.key
- --etcd-servers=https://127.0.0.1:2379
- --insecure-port=0
- --kubelet-client-certificate=/etc/kubernetes/pki/apiserver-kubelet-client.crt
- --kubelet-client-key=/etc/kubernetes/pki/apiserver-kubelet-client.key
- --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname
- --proxy-client-cert-file=/etc/kubernetes/pki/front-proxy-client.crt
- --proxy-client-key-file=/etc/kubernetes/pki/front-proxy-client.key
- --requestheader-allowed-names=front-proxy-client
- --requestheader-client-ca-file=/etc/kubernetes/pki/front-proxy-ca.crt
- --requestheader-extra-headers-prefix=X-Remote-Extra-
- --requestheader-group-headers=X-Remote-Group
- --requestheader-username-headers=X-Remote-User
- --secure-port=6443
- --service-account-key-file=/etc/kubernetes/pki/sa.pub
- --service-cluster-ip-range=10.1.0.0/16
- --tls-cert-file=/etc/kubernetes/pki/apiserver.crt
- --tls-private-key-file=/etc/kubernetes/pki/apiserver.key
- --basic-auth-file=/etc/kubernetes/pki/basic_auth_file # 就这一行是我新增的。大家不要搞错。
image: registry.cn-shanghai.aliyuncs.com/k8sgcrio_containers/kube-apiserver:v1.18.5
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 8
httpGet:
host: 192.168.168.100
path: /healthz
port: 6443
scheme: HTTPS
initialDelaySeconds: 15
timeoutSeconds: 15
name: kube-apiserver
resources:
requests:
cpu: 250m
volumeMounts:
- mountPath: /etc/ssl/certs
name: ca-certs
readOnly: true
- mountPath: /etc/pki
name: etc-pki
readOnly: true
- mountPath: /etc/kubernetes/pki
name: k8s-certs
readOnly: true
hostNetwork: true
priorityClassName: system-cluster-critical
volumes:
- hostPath:
path: /etc/ssl/certs
type: DirectoryOrCreate
name: ca-certs
- hostPath:
path: /etc/pki
type: DirectoryOrCreate
name: etc-pki
- hostPath:
path: /etc/kubernetes/pki
type: DirectoryOrCreate
name: k8s-certs
status: {}
3.改完重新部署。
[root@master ~]# kubectl apply -f /etc/kubernetes/manifests/kube-apiserver.yaml
4.创建集群角色权限绑定。
[root@master ~]# kubectl create clusterrolebinding login-on-dashboard-with-cluster-admin --clusterrole=cluster-admin --user=admin
5.检查集群角色权限绑定。
[root@master ~]# kubectl get clusterrolebinding login-on-dashboard-with-cluster-admin
NAME ROLE AGE
login-on-dashboard-with-cluster-admin ClusterRole/cluster-admin 6m
6.最后修改我前面提到过的 recommended.yaml 就是dashboard相关部署文件。我就截取了中间重要部分,以供大家参考。
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
- --token-ttl=21600 #新增行 单位秒
- --authentication-mode=basic #新增行
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: registry.cn-shanghai.aliyuncs.com/dockerio_containers/kubernetesui-dashboard:v2.0.3
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
- --token-ttl=21600 #新增行 单位秒
- --authentication-mode=basic #新增行
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
7.部署recommended.yaml
[root@master ~]# kubectl apply -f recommended.yaml
8.去浏览器看看效果吧。
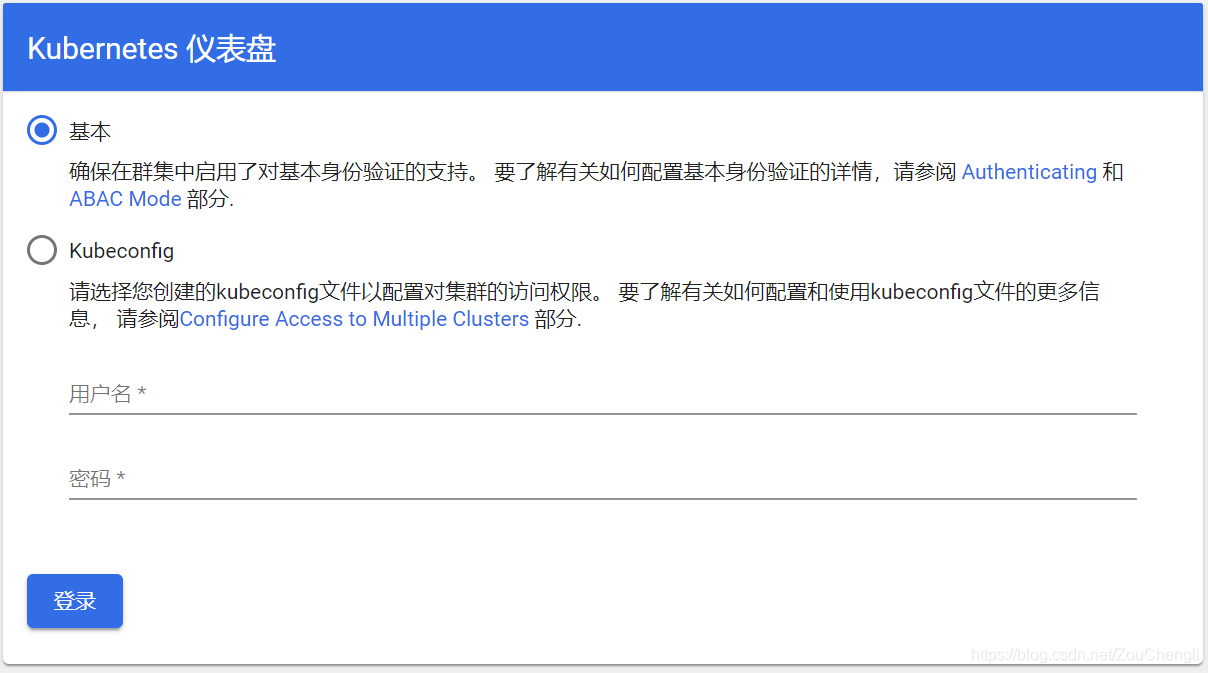










 本文介绍如何在Kubernetes中使用用户名密码而非token登录Dashboard,通过修改kube-apiserver配置,创建集群角色绑定,调整Dashboard部署文件实现更便捷的安全验证。
本文介绍如何在Kubernetes中使用用户名密码而非token登录Dashboard,通过修改kube-apiserver配置,创建集群角色绑定,调整Dashboard部署文件实现更便捷的安全验证。
















 3580
3580

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








