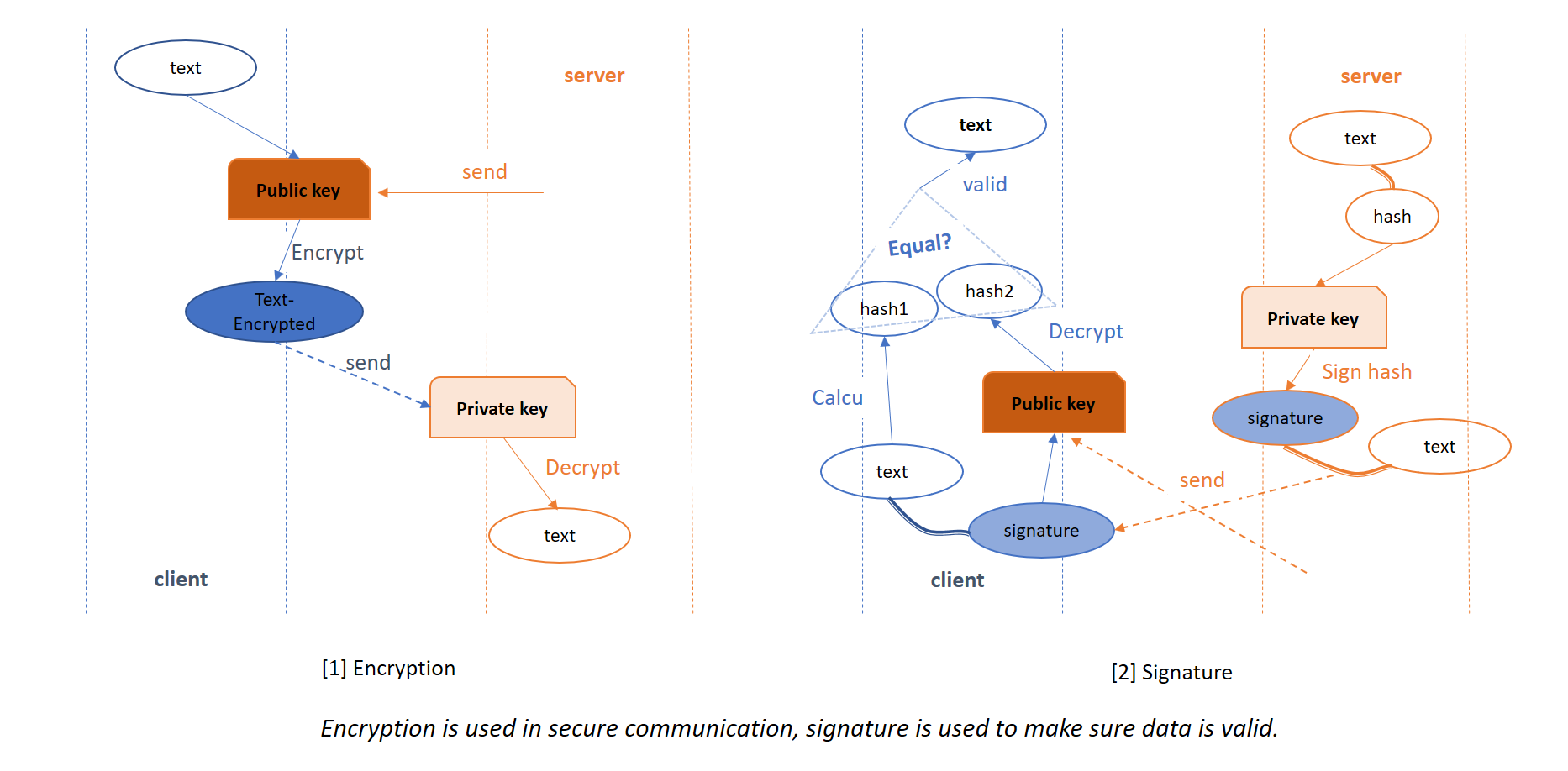
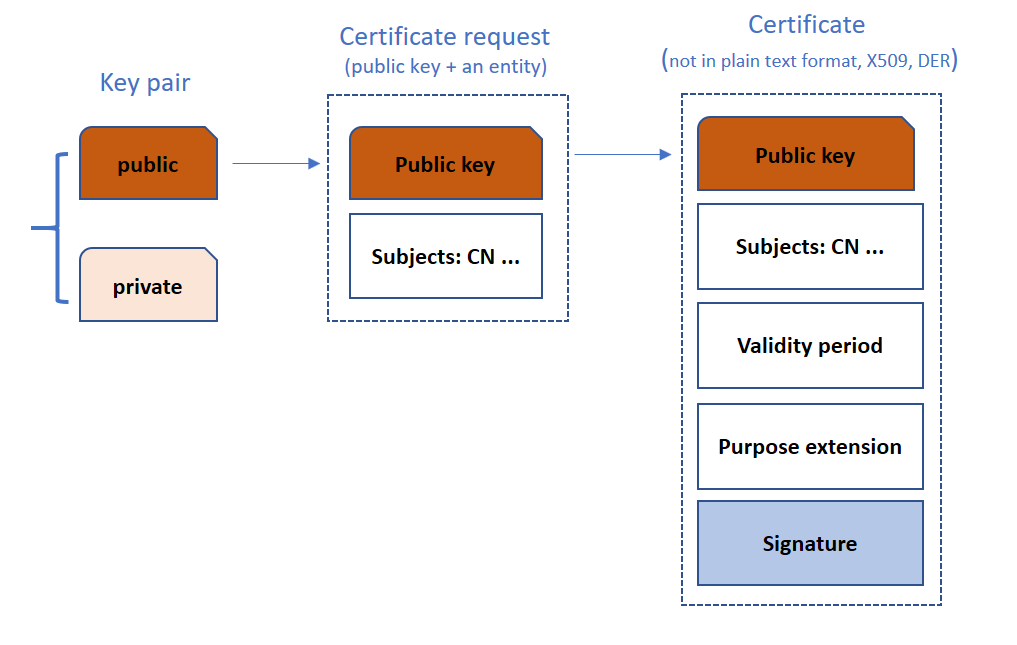
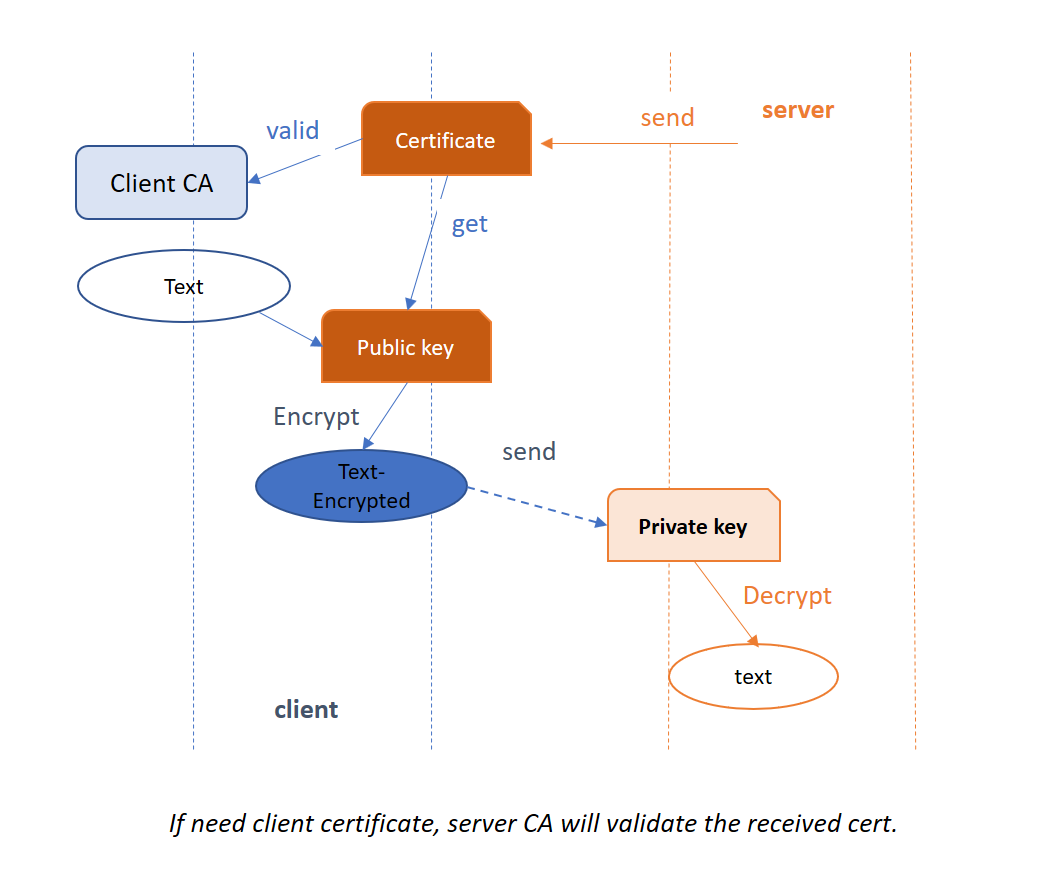
openssl commonly used commands before use Configure to generate Makefile, should notice follow options --prefix=DIR // install dir --libdir=DIR // install dir --openssldir=DIR // Directory for OpenSSL configuration files, and also the default certificate and key store use no-[option] or enable-[option] to turn off/on certion function. # openssl genrsa -des3 -out private.key 2048 # public key is also contained by private.key openssl genrsa -out private.key 2048 openssl req -new -key private.key -out cert.csr -subj "/C=CN/ST=sh/O=Internet Widgits Pty Ltd/CN=www.baidu.com" openssl x509 -days 360 -req -in cert.csr -signkey private.key -out cert.crt openssl x509 -in cert.crt -noout -text # openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout private.key -out cert.crt -subj "/C=CN/ST=sh/O=Internet Widgits Pty Ltd/CN=www.baidu.com" -extensions v3_ca # CA # if we want to sign a self-signed certificate we can use command: # openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout private.key -out cert.crt "/C=CN/ST=sh/O=Internet Widgits Pty Ltd/CN=www.baidu.com" # -extensions v3_ca # if not, we use step 2), for which we must build an CA first. echo "create CA" mkdir demoCA cd demoCA mkdir certs crl private newcerts touch index.txt index.txt.attr echo "01" > serial cd .. openssl genrsa -out demoCA/private/cakey.pem 2048 openssl req -new -key demoCA/private/cakey.pem -out cert.csr -subj "/C=CN/ST=sh/O=Internet Widgits Pty Ltd/CN=www.baidu.com" yes|openssl ca -selfsign -in cert.csr -extensions v3_ca cp demoCA/newcerts/01.pem demoCA/cacert.pem echo "Done" echo " using CA sign a certificate, same countryName, provinceName, OrganizationName" openssl genrsa -out private.key 2048 openssl req -new -key private.key -out cert.csr -subj "/C=CN/ST=sh/O=Internet Widgits Pty Ltd/CN=www.bing.com" yes|openssl ca -in cert.csr # install CA or certificates to openssl's default stroe # if dont do so, when test, we should use -CAfile or -CApath to specify CA sudo cp demoCA/newcerts/01.pem /usr/local/ssl/certs cd /usr/local/ssl/certs sudo ln -s 01.pem `openssl x509 -noout -hash -in 01.pem`.0 openssl verify -CApath ./ 01.pem # test openssl s_server -key key.pem -cert cert.pem -CAfile demoCA/cacert.pem -accept 44330 -www -Verify 2 # or through browser # here we can generate another certificate for client openssl s_client -key key.pem -cert cert.pem -CAfile demoCA/cacert.pem -connect localhost:44330 # add extention to certificate # or we can create a extion file https://comm.support.ca.com/kb/adding-custom-x509-extensions-to-certificate-signing-requests/kb000042912 # is common name mandatory? https://security.stackexchange.com/questions/55414/is-the-common-name-mandatory-for-digital-certificates




















 4370
4370











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








