题目:
http://overthewire.org/wargames/natas/
Write-up:
http://perso.heavyberry.com/articles/2014-01/natas
https://infamoussyn.com/2014/02/05/overthewire-natas-level-0-16-writeup-updated/
https://just4funand2learn.wordpress.com/2013/04/22/overthewire-natas-16/
禁用上下文按钮(右键)
<body oncontextmenu="javascript:alert('right clicking has been blocked!');return false;">
<h1>natas1</h1>
<div id="content">
You can find the password for the
next level on this page, but rightclicking has been blocked!
<!--The password for natas2 is ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi -->
</div>
</body>前几关都是跟 view-source, cookie, Referrer, robots,txt, 网站目录有关的,而第六关只有一个这个,
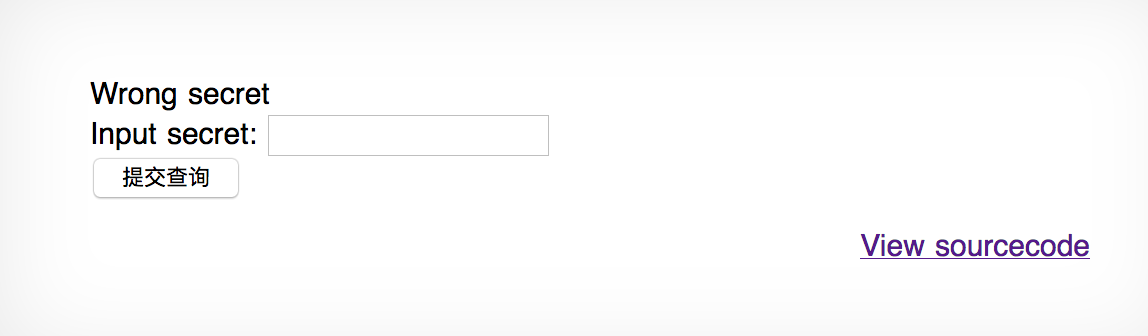
而且尝试在输入框里输入
<script>alert(0)</script>并没有什么反应。于是看一下write-up。
结果write-up说要用那个 View sourcecode的按钮,即访问当前域名的index-source.html页面。开始几关看了一下感觉跟浏览器里地址栏里直接view-source:一样的,结果发现这次不一样。
多了一个这个,是部分php代码。
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>于是去includes/secret.inc目录下查看,发现该文件内容为
<?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>即只定义了一个secret变量。到时候从$_post['secret']即我们提交的表单里面的’secret’字段的值,如果与$secret变量的值一样,则会Access granted. The password for natas7 is <censored>
第7题,发现它的url有点特点,用?来传递参数。
其中有两个?page=home和?page=about。再根据之前的提示,说,密码在/etc/natas_webpass/natas8目录下。
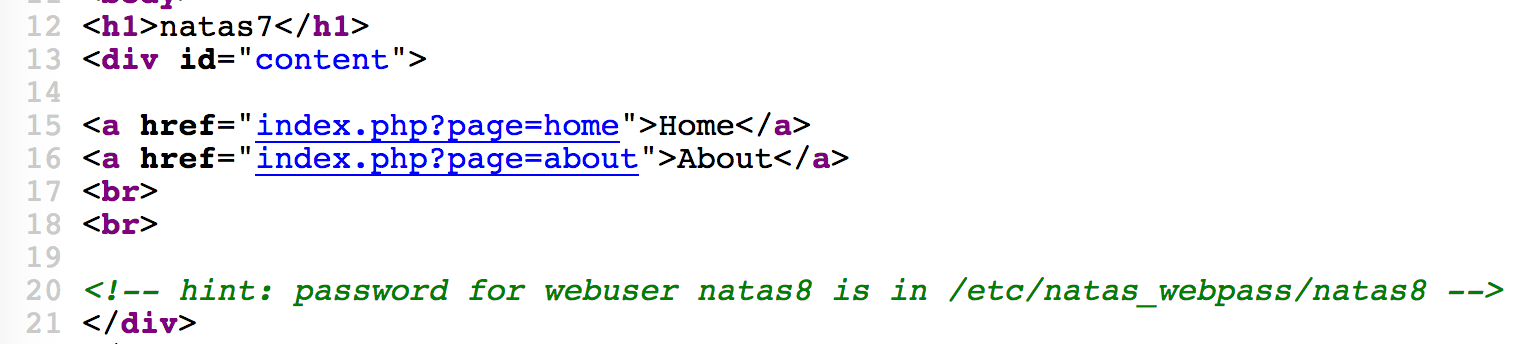
于是试着
?page=/etc/natas_webpass/natas8
完整url为http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8
得到响应中包含了密码
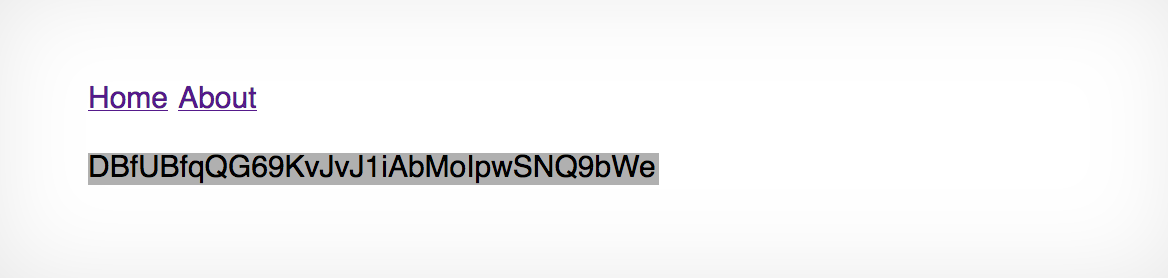
至于为什么home, about这种参数可以和系统的目录这样的参数作为同等地位的参数
























 911
911

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








