10.15 iptables filter表小案例
规则:80端口,22端口,21端口放行。但是22端口指定ip段。
#!/bin/bash
ipt="/usr/sbin/iptables"
$ipt -F
$ipt -P INPUT DROP
$ipt -P OUTPUT ACCEPT
$ipt -P FORWARD ACCEPT
$ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT #IMPORTANT
$ipt -A INPUT -s 192.168.16.0/24 -p tcp --dport 22 -j ACCEPT
$ipt -A INPUT -p tcp --dport 80 -j ACCEPT
$ipt -A INPUT -p tcp --dport 21 -j ACCEPT
结果如下,
[root@localhost: ~]# vim /usr/local/sbin/iptables.sh
[root@localhost: ~]# . !$
. /usr/local/sbin/iptables.sh
[root@localhost: ~]# iptables -nvL
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
26 1716 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT tcp -- * * 192.168.16.0/24 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 14 packets, 1400 bytes)
pkts bytes target prot opt in out source destinationping外面的机器是可以通信的,但是ping本机是不通的。
[root@localhost: ~]# iptables -A INPUT -p icmp --icmp-type 8 -j DROP
[root@localhost: ~]# ping www.qq.com
PING www.qq.com (111.161.64.48) 56(84) bytes of data.
64 bytes from dns48.online.tj.cn (111.161.64.48): icmp_seq=1 ttl=128 time=33.4 ms
64 bytes from dns48.online.tj.cn (111.161.64.48): icmp_seq=2 ttl=128 time=31.3 ms
64 bytes from dns48.online.tj.cn (111.161.64.48): icmp_seq=3 ttl=128 time=33.7 ms
64 bytes from dns48.online.tj.cn (111.161.64.48): icmp_seq=4 ttl=128 time=31.1 ms
64 bytes from dns48.online.tj.cn (111.161.64.48): icmp_seq=5 ttl=128 time=33.4 ms
^C
--- www.qq.com ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4008ms
rtt min/avg/max/mdev = 31.154/32.632/33.712/1.144 msroot@DESKTOP-0M68VSD:~# ping 192.168.16.100
PING 192.168.16.100 (192.168.16.100) 56(84) bytes of data.
^C
--- 192.168.16.100 ping statistics ---
55 packets transmitted, 0 received, 100% packet loss, time 54024ms10.16/17/18 iptables nat表应用
背景:A机器两块网卡a1可以上外网,a2仅仅是内网,B机器只有b网卡和a2互联。.
需求1:B机器连接外网。
准备工作如下
先给A机器添加一块网卡,选定一个LAN segment
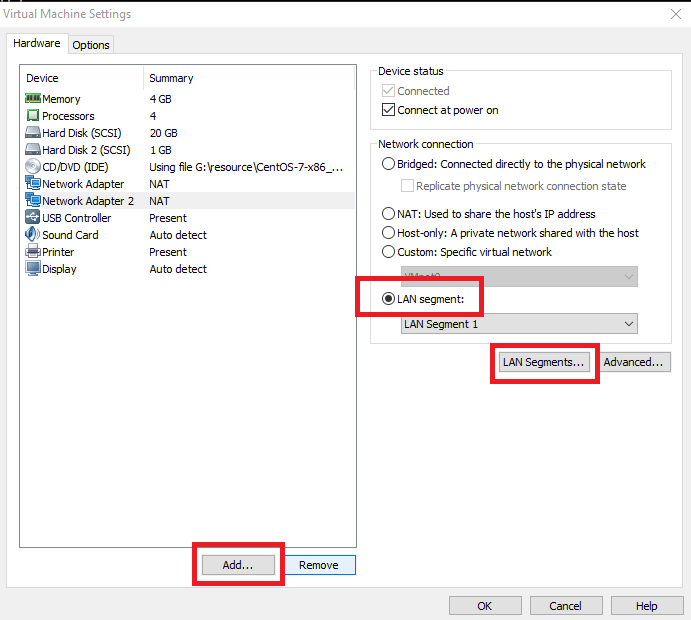
在克隆机上禁掉我们克隆的网卡,同样添加一块新网卡
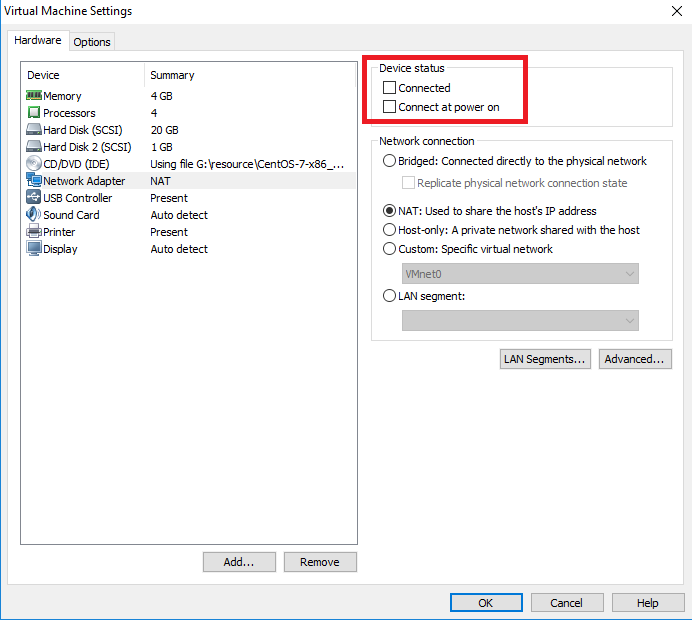
下一步,给新出现的网卡ens37(a2)设定一个ip地址。
[root@localhost: ~]# ifconfig ens37 192.168.17.100/24
[root@localhost: ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.16.100 netmask 255.255.255.0 broadcast 192.168.16.255
inet6 fe80::4f75:15d9:faa2:c641 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:1c:de:be txqueuelen 1000 (Ethernet)
RX packets 972 bytes 85423 (83.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 854 bytes 88981 (86.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.17.100 netmask 255.255.255.0 broadcast 192.168.17.255
inet6 fe80::20c:29ff:fe1c:dec8 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:1c:de:c8 txqueuelen 1000 (Ethernet)
RX packets 454 bytes 154422 (150.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1186 bytes 209240 (204.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 56 bytes 4680 (4.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 56 bytes 4680 (4.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0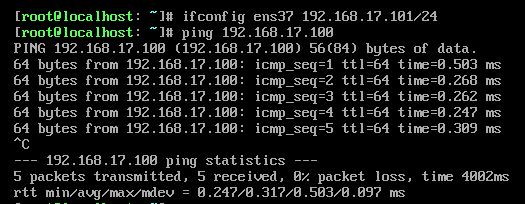
此时准备工作结束。
A机器:192.168.16.100(外网)、192.168.17.100(LAN segment1)
B机器:192.168.17.101(LAN segment1)
root@DESKTOP-0M68VSD:~# ping 192.168.16.100 Windows下
PING 192.168.16.100 (192.168.16.100) 56(84) bytes of data.
64 bytes from 192.168.16.100: icmp_seq=1 ttl=64 time=0.893 ms
64 bytes from 192.168.16.100: icmp_seq=2 ttl=64 time=1.41 ms
64 bytes from 192.168.16.100: icmp_seq=3 ttl=64 time=1.00 ms
^C
--- 192.168.16.100 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 0.893/1.106/1.418/0.226 ms
root@DESKTOP-0M68VSD:~# ping 192.168.17.100
PING 192.168.17.100 (192.168.17.100) 56(84) bytes of data.
^C
--- 192.168.17.100 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 3001ms
root@DESKTOP-0M68VSD:~# ping 192.168.17.101
PING 192.168.17.101 (192.168.17.101) 56(84) bytes of data.
^C
--- 192.168.17.101 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 3001msA机器要打开内核转发。
[root@localhost: ~]# cat /proc/sys/net/ipv4/ip_forward
0
[root@localhost: ~]# echo "1" > !$
echo "1" > /proc/sys/net/ipv4/ip_forward
[root@localhost: ~]# cat /proc/sys/net/ipv4/ip_forward
1
添加iptables规则。
[root@localhost: ~]# iptables -t nat -A POSTROUTING -s 192.168.17.0/24 -o ens33 -j MASQUERADE
[root@localhost: ~]# iptables -nvL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * ens33 192.168.17.0/24 0.0.0.0/0 这样可以让192.168.17.0网段上网。
B上要设置网关为192.168.17.100
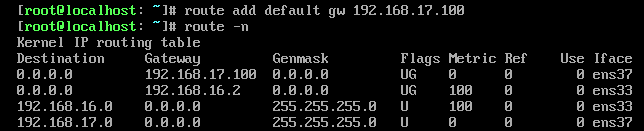
A上要删除掉拒绝icmp的规则,这时候就可以ping通了。
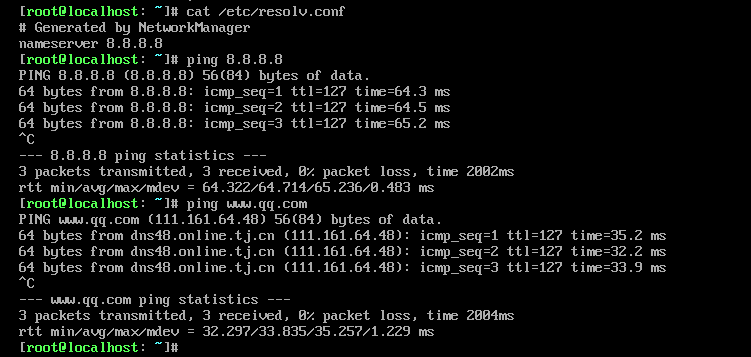
编辑一下配置文件,添加DNS 就可以ping外网了。
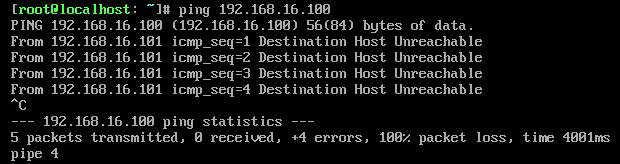
但是此时外网依然ping不通内网。
root@DESKTOP-0M68VSD:~# ping 192.168.17.100
PING 192.168.17.100 (192.168.17.100) 56(84) bytes of data.
^C
--- 192.168.17.100 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2001ms
root@DESKTOP-0M68VSD:~# ping 192.168.17.101
PING 192.168.17.101 (192.168.17.101) 56(84) bytes of data.
^C
--- 192.168.17.101 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2001ms
root@DESKTOP-0M68VSD:~# ping 192.168.16.100
PING 192.168.16.100 (192.168.16.100) 56(84) bytes of data.
64 bytes from 192.168.16.100: icmp_seq=1 ttl=64 time=0.857 ms
64 bytes from 192.168.16.100: icmp_seq=2 ttl=64 time=0.653 ms
^C
--- 192.168.16.100 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.653/0.755/0.857/0.102 ms需求2:C机器只能和A机器通讯,让C机器可以直接连通B机器的22端口(端口映射)
打开端口转发
[root@localhost: ~]# !cat
cat /proc/sys/net/ipv4/ip_forward
1
清空NAT规则
[root@localhost: ~]# iptables -t nat -F
[root@localhost: ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination 设置nat转发,两条规则,去和回。
[root@localhost: ~]# iptables -t nat -A PREROUTING -d 192.168.16.100 -p tcp --dport 1122 -j DNAT --to 192.168.17.101:22
[root@localhost: ~]# iptables -t nat -A POSTROUTING -s 192.168.17.101 -j SNAT --to 192.168.16.100给B机器添加网关,同上。
Connecting to 192.168.16.100:1122...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
Last login: Fri Jul 13 19:26:38 2018
[root@localhost: ~]# ls
anaconda-ks.cfg awk ifcfg-ens33 ifcfg-ens33:0 xxx zsh-5.0.2-28.el7.x86_64.rpm
[root@localhost: ~]# ifconfig
ens33: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 00:0c:29:18:28:6e txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.17.101 netmask 255.255.255.0 broadcast 192.168.17.255
inet6 fe80::20c:29ff:fe18:2878 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:18:28:78 txqueuelen 1000 (Ethernet)
RX packets 540 bytes 160773 (157.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1327 bytes 226504 (221.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 656 bytes 64516 (63.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 656 bytes 64516 (63.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@localhost: ~]# ping www.qq.com
PING www.qq.com (111.161.64.40) 56(84) bytes of data.
64 bytes from dns40.online.tj.cn (111.161.64.40): icmp_seq=1 ttl=127 time=33.1 ms
64 bytes from dns40.online.tj.cn (111.161.64.40): icmp_seq=2 ttl=127 time=31.6 ms
64 bytes from dns40.online.tj.cn (111.161.64.40): icmp_seq=3 ttl=127 time=30.1 ms
^C
--- www.qq.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 30.182/31.686/33.188/1.244 m此时已经可以连接外网了。并且可以使用xshell登录了。
xshell登录的端口要设置成1122.





















 978
978

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








