系统环境: rhel6 x86_64 iptables and selinux disabled
主机: 192.168.122.119:haproxy,keepalived server19.example.com
192.168.122.25:haproxy,keepalived server25.example.com
192.168.122.163:apache server63.example.com
192.168.122.193:apache server93.example.com
所需的包:haproxy-1.4.23.tar.gz
相关网址:http://haproxy.1wt.eu/
HAProx提供高可用性、负载均衡以及基于TCP和HTTP应用的代理,支持虚拟主机,它是免费、快速并且可靠的一种解决方案。HAProxy 特别适用于那些负载特大的web站点, 这些站点通常又需要会话保持或七层处理。HAProxy运行在当前的硬件上,完全可以支持数以万计的并发连接。并且它的运行模式使得它可以很简单安全的整合进您当前的架构中, 同时可以保护你的web服务器不被暴露到网络上。

#安装haproxy
以下步骤在server19或server25上实施:
[root@server19 kernel]# yum install rpm-build -y
[root@server19 kernel]# rpmbuild -tb haproxy-1.4.23.tar.gz
此时会出现以下错误:
(1)error: Failed build dependencies:
pcre-devel is needed by haproxy-1.4.23-1.x86_64
(2)/var/tmp/rpm-tmp.9z0hXn: line 28: /usr/bin/make: No such file or directory
(3) make: gcc: Command not found
解决方法如下:
(1)[root@server19 kernel]# yum install pcre-devel -y
(2)[root@server19 kernel]# yum install make -y
(3)[root@server19 kernel]# yum install gcc -y
[root@server19 kernel]# cd ~/rpmbuild/RPMS/x86_64/
[root@server19 x86_64]# rpm -ivh haproxy-1.4.23-1.x86_64.rpm
注:在企业6和企业7的镜像文件中均集成了haproxy,可以直接yum install haproxy -y进行安装
#配置haproxy
以下步骤在server63和server93上实施:
[root@server63 ~]# yum install httpd -y
[root@server63 ~]# echo `hostname` > /var/www/html/index.html
[root@server63 ~]# /etc/init.d/httpd start
以下步骤在server19或server25上实施:
[root@server19 x86_64]# cd /etc/haproxy/
[root@server19 haproxy]# vim haproxy.cfg
global
log 127.0.0.1 local0 #执行日志设备
log 127.0.0.1 local1 notice
#log loghost local0 info #指定日志类型,还有err,warning,debug
maxconn 4096 #并发最大连接数
chroot /usr/share/haproxy #jail目录
uid 99 #用户
gid 99 #组
daemon #后台运行
#debug
#quiet
defaults
log global
mode http #默认使用http的7层模式tcp:4层
option httplog #http日志格式
option dontlognull #禁止空链接日志
retries 3 #重试3次失败认为服务器不可用
option redispatch #当client连接到挂掉的设备时,重新分配到健康的主机
maxconn 2000
contimeout 5000 #连接超时
clitimeout 50000 #客户端超时
srvtimeout 50000 #服务器超时
stats uri /status #开启haproxy监控页面
listen www.example.com *:80 #监听的实例名称,地址和端口
cookie SERVERID rewrite
balance roundrobin #负载均衡算法
server app1_1 192.168.122.163:80 cookie app1inst1 check inter 2000 rise 2 fall 5
server app1_2 192.168.122.193:80 cookie app1inst2 check inter 2000 rise 2 fall 5
注释: cookie app1inst1 表示serverid为applinst1
check inter2000 检测心跳频率
rise 2 表示2次正确认为服务器可用
fall 5 表示5次失败认为服务器不可用
[root@server19 haproxy]# mkdir /usr/share/haproxy
[root@server19 haproxy]# /etc/init.d/haproxy start
测试:
访问www.example.com 反复刷新,若每次出现的页面不同说明配置成功.(注:访问前先写好解析)
访问haproxy监控页面:www.example.com/status出现如下页面说明配置成功

# 以前端后端的方式进行配置
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
default_backend back1
backend back1
balance roundrobin #负载均衡算法
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
[root@server19 ~]# /etc/init.d/haproxy reload
# 当后端服务全down,由本机提供服务
[root@server19 ~]# yum install httpd -y
[root@server19 ~]# vim /etc/httpd/conf/httpd.conf
Listen 127.0.0.1:8008
[root@server19 ~]# echo server19.example.com > /var/www/html/index.html
[root@server19 ~]# /etc/init.d/httpd restart
注:一定要更换apache的端口,否则将会与haproxy监听的端口冲突,发生错误
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
default_backend back1
backend back1
balance roundrobin #负载均衡算法
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
server backup 127.0.0.1:8008 backup
[root@server19 ~]# /etc/init.d/haproxy reload
测试:
将后端的server63和server93上的httpd服务关闭,然后访问192.168.122.119能访问到server19上的页面就是表示配置成功。
注:只要server63和server93有一台机子上的httpd服务是好的,就访问不到server19上的页面,server19只作为备机用
# haproxy的acl配置
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
default_backend back1
acl badguys src 192.168.122.1
tcp-request content reject if badguys 不允许192.168.122.1连接
backend back1
balance roundrobin #负载均衡算法
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
server backup 127.0.0.1:8008 backup
[root@server19 ~]# /etc/init.d/haproxy reload
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
default_backend back1
acl goodguys src 192.168.122.1
tcp-request content accept if goodguys
tcp-request content reject 只允许192.168.122.1访问
backend back1
balance roundrobin #负载均衡算法
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
server backup 127.0.0.1:8008 backup
[root@server19 ~]# /etc/init.d/haproxy reload
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
default_backend back1
acl goodguys src 192.168.122.0/24
tcp-request content accept if goodguys
tcp-request content reject
acl badguys src 192.168.122.1
block if badguys
errorloc 403 http://www.baidu.com 只允许192.168.122.0这个网段的访问,并且当192.168.122.1访问时,允许连接,但是拒绝访问,并将其重定向到百度首页
backend back1
balance roundrobin #负载均衡算法
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
server backup 127.0.0.1:8008 backup
[root@server19 ~]# /etc/init.d/haproxy reload
# haproxy的动静分离配置
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
acl url_static path_end -i .jpg
use_backend back2 if url_static
default_backend back1
acl goodguys src 192.168.122.0/24
tcp-request content accept if goodguys
tcp-request content reject
backend back1
balance roundrobin
server appl_1 192.168.122.163:80 check
server appl_2 192.168.122.193:80 check
backend back2
balance roundrobin
server static 127.0.0.1:8008 check 默认的访问back1的后端服务(动态),当访问的是以*.jpg结尾的时候,访问back2的后端服务(静态)
[root@server19 ~]# /etc/init.d/haproxy reload
# haproxy的读写分离配置
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
frontend www.example.com *:80
acl url_static path_end -i .jpg
use_backend back2 if url_static
default_backend back1
acl read method GET
acl write method POST
use_backend back1 if read
use_backend back3 if write
acl goodguys src 192.168.122.0/24
tcp-request content accept if goodguys
tcp-request content reject
backend back1
balance roundrobin
server read 192.168.122.163:80 check
backend back2
balance roundrobin
server static 127.0.0.1:8008 check
backend back3
balance roundrobin
server write 192.168.122.193:80 check
[root@server19 ~]# /etc/init.d/haproxy reload
以下步骤在server63和server93上实施:
[root@server63 ~]# yum install php -y
[root@server63 ~]# cd /var/www/html/
[root@server63 html]# vim index.php
<html>
<body>
<form action="upload_file.php" method="post"
enctype="multipart/form-data">
<label for="file">Filename:</label>
<input type="file" name="file" id="file" />
<br />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</html>
[root@server63 html]# vim upload_file.php
<?php
if ((($_FILES["file"]["type"] == "image/gif")
|| ($_FILES["file"]["type"] == "image/jpeg")
|| ($_FILES["file"]["type"] == "image/pjpeg"))
&& ($_FILES["file"]["size"] < 20000))
{
if ($_FILES["file"]["error"] > 0)
{
echo "Return Code: " . $_FILES["file"]["error"] . "<br />";
}
else
{
echo "Upload: " . $_FILES["file"]["name"] . "<br />";
echo "Type: " . $_FILES["file"]["type"] . "<br />";
echo "Size: " . ($_FILES["file"]["size"] / 1024) . " Kb<br />";
echo "Temp file: " . $_FILES["file"]["tmp_name"] . "<br />";
if (file_exists("upload/" . $_FILES["file"]["name"]))
{
echo $_FILES["file"]["name"] . " already exists. ";
}
else
{
move_uploaded_file($_FILES["file"]["tmp_name"],
"upload/" . $_FILES["file"]["name"]);
echo "Stored in: " . "upload/" . $_FILES["file"]["name"];
}
}
}
else
{
echo "Invalid file";
}
?>
[root@server63 html]# mkdir upload
[root@server63 html]# chmod 777 upload
[root@server63 html]# /etc/init.d/httpd restart
# 给监控页面添加认证
以下步骤在server19或server25上实施:
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
listen status_auth 192.168.122.119:8080
stats enable
stats uri /status #监控页面地址
stats auth admin:westos #管理帐号和密码
stats refresh 5s #刷新频率
[root@server19 ~]# /etc/init.d/haproxy reload
测试:
访问192.168.122.119:8080/status若出现如下认证页面说明配置成功.
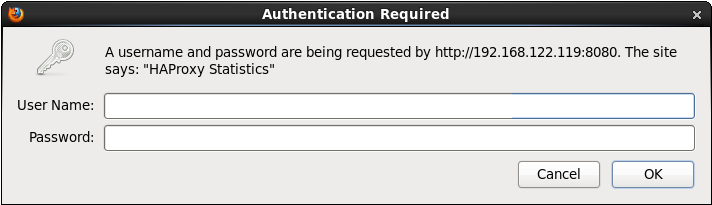

#haproxy日志
以下步骤在server19或server25上实施:
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
global
log 127.0.0.1 local0
#log 127.0.0.1 local1 notice
log 192.168.122.119 local0 info
…
[root@server19 ~]# vim /etc/rsyslog.conf
# Provides UDP syslog reception
$ModLoad imudp (去掉注释) #接受haproxy日志
$UDPServerRun 514 (去掉注释)
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none;local0.none /var/log/messages
# Save boot messages also to boot.log
local7.* /var/log/boot.log
local0.* /var/log/haproxy.log
#指定日志文件位置
[root@server19 ~]# /etc/init.d/rsyslog restart
[root@server19 ~]# /etc/init.d/haproxy reload
测试:
执行tail -f /var/log/haproxy.log查看是否将日志记录在此文件中.
#将haproxy和keepalived整合
注:keepalived的安装方法请看Rhel6-keepalived+lvs.pdf
以下步骤在server19和server25上实施:
[root@server19 x86_64]# rpm -ivh haproxy-1.4.23-1.x86_64.rpm
以下步骤在server19上实施:
[root@server19 ~]# vim /etc/haproxy/haproxy.cfg
global
log 127.0.0.1 local0 #执行日志设备
log 127.0.0.1 local1 notice
#log loghost local0 info #指定日志类型,还有err,warning,debug
maxconn 4096 #并发最大连接数
chroot /usr/share/haproxy #jail目录
uid 99 #用户
gid 99 #组
daemon #后台运行
#debug
#quiet
defaults
log global
mode http #默认使用http的7层模式tcp:4层
option httplog #http日志格式
option dontlognull #禁止空链接日志
retries 3 #重试3次失败认为服务器不可用
option redispatch #当client连接到挂掉的设备时,重新分配到健康的主机
maxconn 2000
contimeout 5000 #连接超时
clitimeout 50000 #客户端超时
srvtimeout 50000 #服务器超时
stats uri /status #开启haproxy监控页面
listen www.example.com *:80 #监听的实例名称,地址和端口
cookie SERVERID rewrite
balance roundrobin #负载均衡算法
server app1_1 192.168.122.163:80 cookie app1inst1 check inter 2000 rise 2 fall 5
server app1_2 192.168.122.193:80 cookie app1inst2 check inter 2000 rise 2 fall 5
注释: cookie app1inst1 表示serverid为applinst1
check inter2000 检测心跳频率
rise 2 表示2次正确认为服务器可用
fall 5 表示5次失败认为服务器不可用
[root@server19 ~]# vim /etc/keepalived/keepalived.conf
vrrp_script check_haproxy {
script "/opt/check_haproxy.sh"
interval 2
weight 2
}
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@server19.example.com
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.122.178
}
track_script {
check_haproxy
}
}
[root@server19 ~]# vim /opt/check_haproxy.sh (脚本内容任选其一即可)
脚本一: #!/bin/bash
/etc/init.d/haproxy status &> /dev/null || /etc/init.d/haproxy restart &> /dev/null
if [ $? -ne 0 ];then
/etc/init.d/keepalived stop &> /dev/null
fi
脚本二:#!/bin/bash
[ -f /var/run/haproxy.pid ] || /etc/init.d/haproxy restart &> /dev/null
if [ $? -ne 0 ];then
/etc/init.d/keepalived stop &> /dev/null
fi
脚本for rhel7:
#!/bin/bash
systemctl status haproxy &> /dev/null || systemctl restart haproxy &> /dev/null
if [ $? -ne 0 ];then
systemctl stop keepalived
fi
[root@server19 ~]# chmod +x /opt/check_haproxy.sh
以下步骤在server25上实施:
[root@server25 ~]# vim /etc/haproxy/haproxy.cfg
global
log 127.0.0.1 local0 #执行日志设备
log 127.0.0.1 local1 notice
#log loghost local0 info #指定日志类型,还有err,warning,debug
maxconn 4096 #并发最大连接数
chroot /usr/share/haproxy #jail目录
uid 99 #用户
gid 99 #组
daemon #后台运行
#debug
#quiet
defaults
log global
mode http #默认使用http的7层模式tcp:4层
option httplog #http日志格式
option dontlognull #禁止空链接日志
retries 3 #重试3次失败认为服务器不可用
option redispatch #当client连接到挂掉的设备时,重新分配到健康的主机
maxconn 2000
contimeout 5000 #连接超时
clitimeout 50000 #客户端超时
srvtimeout 50000 #服务器超时
stats uri /status #开启haproxy监控页面
listen www.example.com *:80 #监听的实例名称,地址和端口
cookie SERVERID rewrite
balance roundrobin #负载均衡算法
server app1_1 192.168.122.163:80 cookie app1inst1 check inter 2000 rise 2 fall 5
server app1_2 192.168.122.193:80 cookie app1inst2 check inter 2000 rise 2 fall 5
注释: cookie app1inst1 表示serverid为applinst1
check inter2000 检测心跳频率
rise 2 表示2次正确认为服务器可用
fall 5 表示5次失败认为服务器不可用
[root@server25 ~]# vim /etc/keepalived/keepalived.conf
vrrp_script check_haproxy {
script "/opt/check_haproxy.sh"
interval 2
weight 2
}
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@server25.example.com
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
priority 50
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.122.178
}
track_script {
check_haproxy
}
}
[root@server25 ~]# vim /opt/check_haproxy.sh (脚本内容任选其一即可)
脚本一: #!/bin/bash
/etc/init.d/haproxy status &> /dev/null || /etc/init.d/haproxy restart &> /dev/null
if [ $? -ne 0 ];then
/etc/init.d/keepalived stop &> /dev/null
fi
脚本二:#!/bin/bash
[ -f /var/run/haproxy.pid ] || /etc/init.d/haproxy restart &> /dev/null
if [ $? -ne 0 ];then
/etc/init.d/keepalived stop &> /dev/null
fi
脚本for rhel7:
#!/bin/bash
systemctl status haproxy &> /dev/null || systemctl restart haproxy &> /dev/null
if [ $? -ne 0 ];then
systemctl stop keepalived
fi
[root@server25 ~]# chmod +x /opt/check_haproxy.sh
以下步骤在server19和server25上实施:
[root@server19 ~]# /etc/init.d/keepalived start (此处只需手动把keepalived启动,keepalived将调用check_haproxy.sh脚本把haproxy启动)
测试:
访问192.168.122.178反复刷新页面,每次出现的页面都不同,将server19的keepalived关闭,执行ip addr show查看虚拟IP是否浮动到server25上,然后再 将server19上的keepalived启动,执行ip addr show查看虚拟IP是否会浮动回server19上.





















 115
115

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








