std::thread封装
“Web attacks are the greatest threat facing an on-line business today.” This statement may seem overwhelming and yet, over the last few years, we have witnessed many high-profile web attacks that have actually brought down businesses of all sizes – massive-scale data breaches that caused almost irreparable damage to company image, brand value and user trust.
“网络攻击是当今在线业务面临的最大威胁。” 这个说法似乎不言而喻,但是在过去的几年中,我们目睹了许多备受瞩目的Web攻击实际上摧毁了各种规模的企业-大规模的数据泄露事件对公司的形象,品牌价值和用户信任。
For another take on the scope of this problem, one can refer to a recent estimate made by Keith Alexander, Director of the US National Security Agency, who put an incredible annual price tag on total value of time wasted and opportunities lost in the US alone due to cyber-crime – a whopping $388 billion.
关于这个问题的范围的另一种说法,可以参考美国国家安全局局长基思·亚历山大 ( Keith Alexander)的最新估计,他将令人难以置信的年度价格标签仅浪费在美国的时间和浪费的总价值上由于网络犯罪-高达3880亿美元。
Perhaps one of the most alarming and new aspects of cyber-crime today is that the attackers are changing their focus, targeting not only big and prominent websites, but also small and medium businesses. These sites, who until recently were mostly unconcerned with cyber-security, present an easy target for any would-be attacker. As such, several recent security studies show that the number of cyber-attacks on SMB websites in 2012 has doubled, and the numbers continue to grow.
如今,网络犯罪最令人震惊和最新的方面之一是,攻击者正在改变其重点,不仅针对大型和著名的网站,而且还针对中小企业。 这些站点直到最近几乎都与网络安全无关,为任何可能的攻击者提供了轻松的目标。 因此,最近的几项安全性研究表明,2012年SMB网站上的网络攻击数量已经翻了一番,并且还在继续增长。
Luckily, SMB website owners and operators are becoming aware of the numerous security threats and are proactively seeking affordable yet still effective means for online protection. When choosing an online security solution, SMBs should take a multi-layered security approach – starting from simple Bad bot & Automation Protection and moving forward to encompass WAF and DDoS Solutions.
幸运的是,SMB网站所有者和运营商已意识到众多安全威胁,并正在积极寻求负担得起但仍有效的在线保护手段。 在选择在线安全解决方案时,中小型企业应采取多层安全方法-从简单的错误bot和自动化保护开始,然后逐步扩展到WAF和DDoS解决方案。
封装:自动化和不良机器人保护 (Incapsula: Automation & Bad bot Protection)
Bots are non-human entities that operate with various, often malicious, purposes. Recent research by Incapsula showed that on average 51% of web site traffic comes from these non-humans – with 31% of potentially damaging automated traffic from various hackers, scrapers, spammers and vulnerability scanners often used as a vanguard force for a more devastating attack.
机器人是出于各种目的(通常是恶意的)而运作的非人类实体。 Incapsula的最新研究表明,平均51%的网站流量来自这些非人类用户-31%的潜在破坏性自动流量来自各种黑客,抓取工具,垃圾邮件发送者和漏洞扫描程序,通常被用作发动更具破坏性攻击的先锋力量。
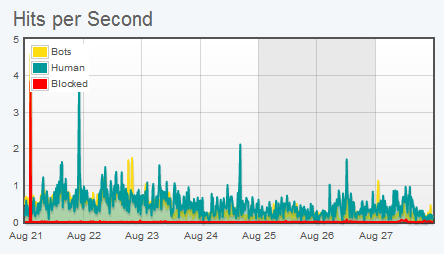
Incapsula Dashboard: Traffic report
封装仪表板:流量报告
Incapsula’s first layer of protection identifies and filters out malicious bots. Since many such bots will try to disguise themselves with fake user-agents and spoofed IPs, the system uses numerous identification techniques, looking for clues in the HTTP Headers and in bot behavior patterns. If needed, the system will also apply a set of challenges: starting with a cookie support challenge, moving on to a JS support challenge and in certain cases even using CAPTCHAs for definitive human identification.
Incapsula的第一层保护可以识别并过滤出恶意机器人。 由于许多此类漫游器会试图伪装成伪造的用户代理和欺骗性IP,因此该系统使用了多种识别技术,以在HTTP标头和漫游器行为模式中寻找线索。 如果需要,该系统还将面临一系列挑战:从cookie支持挑战开始,过渡到JS支持挑战,在某些情况下甚至使用CAPTCHA进行最终人类识别。
All the collected data is gathered and preserved as a “bot signature,” making subsequent bot identification faster and more reliable. Over the years, Incapsula has gathered a large pool of bot data, which was recently consolidated in Botopedia.org – a community-based directory that shares bot information freely, with all who require it.
所有收集的数据都将被收集并保存为“机器人签名”,从而使后续的机器人识别更快,更可靠。 多年来,Incapsula收集了大量的bot数据,最近将这些数据合并到Botopedia.org中。Botopedia.org是一个基于社区的目录,可与所有需要它的人自由共享bot信息。
Users can customize Bot Protection, with an option for white-listing or blacklisting based on user-agent, IP of origin, type of application used (e.g. white-listing of all CURL access) and more.
用户可以自定义Bot Protection,并根据用户代理,原始IP,使用的应用程序类型(例如,所有CURL访问的白名单)进行白名单或黑名单的选择。
Incapsula Settings: IP and Country blocking rules
封装设置:IP和国家/地区阻止规则
Incapsula Settings: Bot Blacklisting/Whitelisting rules
封装设置:Bot黑名单/白名单规则
The rules management GUI is built to be quick and intuitive, using check-boxes and auto-completion features to keep things simple. The system also offers a detailed event log to help keep track of recent bot related activity.
规则管理GUI使用复选框和自动完成功能来使操作简单明了,从而使其构建起来既快速又直观。 该系统还提供详细的事件日志,以帮助跟踪与机器人相关的最新活动。
Web应用程序防火墙(WAF) (Web Application Firewall (WAF))
Incapsula’s PCI DDS compliant WAF serves as second line of defense and protects the website and its database from advanced web threats. To deal with these threats, Incapsula’s WAF monitors user input and application behavior, employing a wide set of security rules to identify and mitigate different attack vectors, and using cross-referencing to prevent false-positives.
Incapsula的符合PCI DDS的WAF是第二道防线,可保护网站及其数据库免受高级Web威胁。 为了应对这些威胁,Incapsula的WAF监视用户输入和应用程序行为,采用各种安全规则来识别和缓解不同的攻击媒介,并使用交叉引用防止误报。
The WAF rules are regularly updated. As a result, this firewall can deal with a large number of existing threats and expand its reach to handle new threats as they arise. Here is how Incapsula’s WAF protects from the most common OWASP Top 10 Threats:
WAF规则会定期更新。 结果,此防火墙可以处理大量现有威胁,并扩大其范围以应对新威胁。 这是Incapsula的WAF如何防御最常见的OWASP十大威胁:
| Threat | Incapsula’s Solution |
| A1: Injections – Injection flaws, particularly SQL injection, are common in web applications. Injection occurs when user-supplied data is sent to an interpreter as part of a command or query. The attacker’s hostile data tricks the interpreter into executing unintended commands or changing data. | Incapsula can detect and block injection attacks through validation of user input using either negative or positive security policies. |
| A2: Cross-Site Scripting (XSS) – XSS flaws occur whenever an application takes user supplied data and sends it to a web browser without first validating or encoding that content. XSS allows attackers to execute script in the victim’s browser which can hijack user sessions, deface web sites, introduce worms, etc. | Incapsula detects and blocks Cross Site Scripting (XSS) attacks through validation of user input using either negative or positive security policies. |
| A3: Broken Authentication & Session Management Account credentials and session tokens are often not properly protected. Attackers compromise passwords, keys, or authentication tokens to assume other users’ identities. | Incapsula detects and blocks Insecure Direct Object Reference attacks through validation of user input against known attack vectors, behaviors, and deviations. Incapsula also analyzes the desired application behavior and access rules, applying specific policies per customer application. |
| A5: Cross-Site Request Forgery (CSRF) – A CSRF attack creates forged HTTP requests and tricks a victim into submitting them via image tags, XSS, or other techniques. If the user is authenticated, the attacker succeeds. CSRF takes advantage of Web applications that allow attackers to predict all the details of the transaction. Since browsers send credentials like session cookies automatically, attackers can create malicious web pages which generate forged requests that are indistinguishable from legitimate ones. | Incapsula constantly monitors referral usage patterns and in conjunctions with its other external feeds, uses a blacklisting security model to detect potential malicious behavioral patterns and offending sites. |
| A6: Security Misconfiguration – Security misconfiguration can happen at any level of an application attack, including the platform, web server, application server, framework, and custom code. Such flaws can give attackers access to default accounts, unused pages, unpatched flaws, unprotected files, and directories to gain unauthorized access to system data. | Incapsula applies both generic and application specific security measures to accommodate for security misconfiguration. This mitigates administrative and other access vulnerabilities and also includes application specific “virtual patching”. |
| A7: Insecure Cryptographic Storage – Many web applications do not properly protect sensitive data such as credit cards, Social Security Numbers (SSNs), and authentication credentials with appropriate encryption or hashing. Attackers may use this weakly protected data to conduct identity theft, credit card fraud, or other crimes. | Incapsula does not directly store confidential data. |
| A8: Failure to Restrict URL Access – Frequently, an application only protects sensitive functionality by preventing the display of links or URLs to unauthorized users. Attackers can use this weakness to access and perform unauthorized operations by accessing those URLs directly. | Incapsula applies application specific, as well as signature and client based illegal resource access policies. |
| A9: Insufficient Transport Layer Protection – Applications frequently fail to encrypt network traffic when it is necessary to protect sensitive communications. | Incapsula fully support HTTPS Traffic. Incapsula is able to terminate HTTPS traffic, inspect it and re-encrypt the traffic, prior to transmitting it to the protected host. Incapsula also ensures the level of encryption of the SSL protocol (such as encryption strength). |
| A10: Invalidated Redirects and Forwards – Applications frequently fail to encrypt network traffic when it is necessary to protect sensitive communications. | Incapsula analyzes the application behavior, mitigating known security vulnerabilities, such as unauthenticated redirects and forwards. |
威胁 | 封装解决方案 |
| 解答1:注入–注入缺陷,尤其是SQL注入,在Web应用程序中很常见。 当用户提供的数据作为命令或查询的一部分发送到解释器时,就会发生注入。 攻击者的敌对数据会诱使解释器执行意外的命令或更改数据。 | 通过使用否定或肯定的安全策略验证用户输入,Incapsula可以检测和阻止注入攻击。 |
| 解答2:跨站点脚本(XSS)–每当应用程序获取用户提供的数据并将其发送到Web浏览器而未首先验证或编码该内容时,就会发生XSS漏洞。 XSS允许攻击者在受害者的浏览器中执行脚本,该脚本可能劫持用户会话,破坏网站,引入蠕虫等。 | Incapsula通过使用否定或肯定的安全策略验证用户输入来检测并阻止跨站点脚本(XSS)攻击。 |
| A3:身份验证和会话管理中断 帐户凭据和会话令牌通常没有得到适当的保护。 攻击者会破坏密码,密钥或身份验证令牌,以假定其他用户的身份。 | Incapsula通过针对已知攻击向量,行为和偏差验证用户输入来检测和阻止不安全的直接对象引用攻击。 Incapsula还可以分析所需的应用程序行为和访问规则,并针对每个客户应用程序应用特定的策略。 |
| 解答5:跨站请求伪造(CSRF)– CSRF攻击会创建伪造的HTTP请求,并诱使受害者通过图像标签,XSS或其他技术提交请求。 如果用户通过身份验证,则攻击者成功。 CSRF利用Web应用程序使攻击者能够预测交易的所有详细信息。 由于浏览器会自动发送会话cookie之类的凭据,因此攻击者可以创建恶意网页,这些网页生成与合法请求无法区分的伪造请求。 | Incapsula不断监视引荐使用模式,并与其其他外部提要结合使用,使用列入黑名单的安全模型来检测潜在的恶意行为模式和有问题的站点。 |
| 解答6:安全性配置错误–安全性配置错误可能发生在应用程序攻击的任何级别,包括平台,Web服务器,应用程序服务器,框架和自定义代码。 此类漏洞可以使攻击者访问默认帐户,未使用的页面,未打补丁的漏洞,未受保护的文件和目录,从而获得对系统数据的未授权访问。 | 封装应用通用和特定于应用程序的安全措施以适应安全性错误配置。 这可以缓解管理和其他访问漏洞,还包括特定于应用程序的“虚拟补丁程序”。 |
| 解答7:不安全的密码存储–许多Web应用程序无法通过适当的加密或散列来适当地保护敏感数据,例如信用卡,社会安全号码(SSN)和身份验证凭据。 攻击者可能会使用受保护程度较弱的数据来进行身份盗用,信用卡欺诈或其他犯罪。 | Incapsula不会直接存储机密数据。 |
| A8:无法限制URL访问–通常,应用程序只能通过阻止向未经授权的用户显示链接或URL来保护敏感功能。 攻击者可以通过直接访问这些URL来利用此漏洞来访问和执行未经授权的操作。 | Incapsula应用特定于应用程序的信息,以及基于签名和基于客户端的非法资源访问策略。 |
| A9:传输层保护不足–在必须保护敏感通信时,应用程序经常无法加密网络流量。 | 封装完全支持HTTPS流量。 在将HTTPS流量传输到受保护的主机之前,它能够终止HTTPS流量,对其进行检查并重新加密。 封装还确保SSL协议的加密级别(例如加密强度)。 |
| A10:无效的重定向和转发–当必须保护敏感通信时,应用程序经常无法加密网络流量。 | 封装分析应用程序行为,从而缓解已知的安全漏洞,例如未经身份验证的重定向和转发。 |
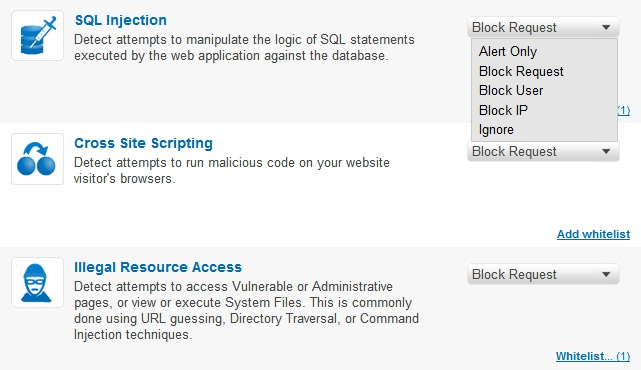
Incapsula Settings: WAF custom Rules Screen
封装设置:WAF自定义规则屏幕
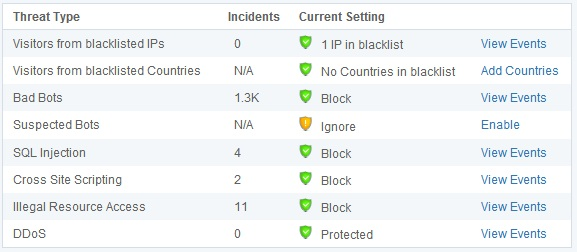
Incapsula Dashboard: Security Threat Monitoring
封装仪表板:安全威胁监视
Incapsula’s WAF behavior can be customized to deal differently with each type of attack, with options ranging from “Alert Only” to an auto-blocking of all access from the attacking IP.
可以自定义Incapsula的WAF行为,以针对每种类型的攻击进行不同的处理,其选项范围从“仅警报”到自动阻止来自攻击IP的所有访问。
The system can also automatically issue a PCI DDS 6.6 compliancy audit report on a weekly, monthly or quarterly basis. As with bad and suspicious bots visits, all WAF-related occurrences appear in Incapsula’s Dashboard and are also documented in the security event log, for future referencing.
系统还可以每周,每月或每季度自动发布PCI DDS 6.6合规性审核报告。 与恶意和可疑的bot访问一样,所有与WAF相关的事件都显示在Incapsula的仪表板上,并记录在安全事件日志中,以备将来参考。
DDoS缓解服务 (DDoS Mitigation Services )
Incapsula’s Enterprise plan offers full protection against all types of DDoS threats, including network-based (Layer 3 – 4) attacks, like SYN or UDP floods, and application (Layer 7) attacks that attempt to overwhelm server resources. The service can also block advanced attacks that exploit application and web server vulnerabilities, such as Slowloris DDoS, HTTP Flood, Apache Killer and etc.
Incapsula的企业计划可针对所有类型的DDoS威胁提供全面保护,包括基于网络的(第3层至第4层)攻击(如SYN或UDP泛洪)以及应用程序(第7层)攻击,这些攻击企图淹没服务器资源。 该服务还可以阻止利用应用程序和Web服务器漏洞的高级攻击,例如Slowloris DDoS,HTTP Flood,Apache Killer等。
Incapsula’s global network of scrubbing centers is able to scale on demand to counter multi-gigabyte DDoS attacks. As this is cloud service, the mitigation is applied outside of the client’s network, allowing only filtered traffic to reach the hosts.
Incapsula的全球清理中心网络能够按需扩展,以应对数GB的DDoS攻击。 由于这是云服务,因此缓解措施适用于客户端网络之外,仅允许经过过滤的流量到达主机。
Incapsula’s bot identification capabilities help mitigate application (Layer 7) DDoS attacks, where the DDoS requests look like legitimate visitor sessions. While most DDoS protection services are based on easy-to-evade and false positive-prone techniques, like rate limiting or showing an annoying delay screen to every visitor, Incapsula can actually differentiate between humans and bots, thus ensuring that legitimate visitors can continue to access the site unimpeded.
Incapsula的漫游器识别功能有助于缓解应用程序(第7层)DDoS攻击,其中DDoS请求看起来像合法的访客会话。 尽管大多数DDoS保护服务都是基于易于逃避的和虚假的易错技术,例如速率限制或向每个访问者显示讨厌的延迟屏幕,但Incapsula可以真正区分人与机器人,从而确保合法访问者可以继续畅通无阻地访问该网站。
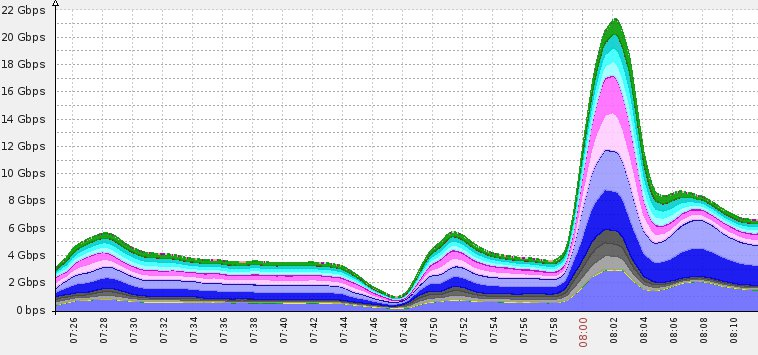
22Gbps DDoS attack mitigated across scrubbing centers.
跨洗涤中心缓解了22Gbps DDoS攻击。
结论: (In Conclusion:)
Incapsula’s message is that of “affordable high-end security” and it delivers on its promise. While implementing its “economy of scale” principles, Incapsula protects websites by leveraging a collective knowledge base of known threats, including new and emerging attack methods. Working behind the scenes, the Incapsula security team makes sure that all new information is aggregated across the entire service network, for the benefit of all service users.
Incapsula传达的信息是“负担得起的高端安全性”,它兑现了诺言。 在实施“规模经济”原则时,Incapsula通过利用已知威胁(包括新兴攻击方法)的集体知识库来保护网站。 Incapsula安全团队在幕后工作,确保所有新信息都在整个服务网络中聚合,以造福所有服务用户。
翻译自: https://www.sitepoint.com/incapsula-a-multi-layered-website-security-solution/
std::thread封装






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








