nas和nsa
We all heard the rumors regarding NSA mass espionage over the internet using the MITM (man in the middle) technique, or if anyone didn’t read about, in few Google searches can find the whole story.
我们都听到了关于使用MITM(中间人)技术在互联网上进行NSA大规模间谍活动的谣言,或者如果没有人读过,则很少有Google搜索可以找到整个故事。
This article is intended for people who use Mozilla, does not involve the use of VPNs and just simply reveals how to configure some settings in the Firefox browser to increase safety when traffic decryption is attempted.
本文适用于使用Mozilla的用户,不涉及VPN的使用,仅介绍了如何在Firefox浏览器中配置某些设置,以在尝试进行流量解密时提高安全性。
If you don’t know anything about MITM attacks, take a look over the following image that illustrates very well the concept of these kind of attacks (feel free to read more about, the subject is discussed extensively in a lot of forums, blogs, articles).
如果您对MITM攻击一无所知,请查看下图,该图很好地说明了这类攻击的概念(欢迎阅读更多信息,许多论坛,博客,文章)。

The first thing I recommend is to install this add-on for Firefox:
我建议的第一件事是为Firefox安装此插件:
https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/
https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/

The add-on is very useful because:
该加载项非常有用,因为:
- it allows you to see how strong the encryption used on sites visited is, in a very simple style 它可以让您以非常简单的方式查看所访问网站上使用的加密的强度
- it allows you to see in detail how the encryption was done, using “points” for the algorithms used 它使您可以详细了解加密的完成方式,使用“点”表示所使用的算法
- it allows you to make change useful settings. 它使您可以进行有用的更改设置。
While I was researching this article, I noticed that major sites including Facebook, Google, Paypal and so on, provide by default a very weak encryption: RC4 – 128 bits! More details about the RC4 algorithm and its problems can be found here.
在研究本文时,我注意到包括Facebook,Google,Paypal等在内的主要网站默认情况下都提供非常弱的加密:RC4 – 128位! 有关RC4算法及其问题的更多详细信息,请参见此处 。
让我们看一下SSL / TLS (Let’s take a look at SSL/TLS)
I do not want this article to turn into an article about SSL / TLS, but I must say a few basic things.
我不希望本文变成有关SSL / TLS的文章,但我必须说一些基本的事情。
- SSL / TLS are some protocols and rules that must be met in order to achieve a secure connection between your computer and the site you visit. TLS is basically an upgraded version of SSLs. SSL / TLS是为了在计算机和访问的站点之间建立安全连接而必须满足的一些协议和规则。 TLS基本上是SSL的升级版本。
- SSL versions 1.0, 2.0 and 3.0 are old and should not be used, especially since it is known that they have security problems. TLS 1.0 is an enhanced version of SSL 3.0 and TLS 1.1 and TLS 1.2 are newer versions of TLS. SSL版本1.0、2.0和3.0很旧,不应使用,尤其是因为已知它们存在安全问题。 TLS 1.0是SSL 3.0的增强版本,而TLS 1.1和TLS 1.2是TLS的较新版本。
Creating a SSL connection is as follows:
创建SSL连接如下:
- TCP connection is made 建立TCP连接
- The client (browser) sends “Client Hello” to the server. Also sends its SSL / TLS version. i.e. TLS 1.0 客户端(浏览器)将“客户端问候”发送到服务器。 还发送其SSL / TLS版本。 即TLS 1.0
- The server responds with “Hello World” also specify supported encryption version, (i.e.TLS 1.0) and TLS chosen cipher suite(algorithm used for Encryption) 服务器以“ Hello World”作为响应,还指定了受支持的加密版本(即TLS 1.0)和TLS选择的密码套件(用于加密的算法)
- The server sends the certificate (or certificates) to identify. Specifically, says: “Look, this is a proof that I am “www.sitepoint.com”. In order to be recognized by the browser as valid, the certificates must be signed by an authority in this field: VeriSign and other companies recognized as legitimate to sign certificates 服务器发送一个或多个证书以进行标识。 具体来说,说:“看,这证明我是” www.sitepoint.com”。 为了被浏览器识别为有效,证书必须由该字段中的授权机构签名:VeriSign和其他被认为是合法签署证书的公司
- The client verifies that the received certificate is okay, and if everything is fine, client and server exchanges keys (handshake). 客户端验证收到的证书还可以,如果一切正常,则客户端和服务器交换密钥(握手)。
Using keys exchanged above data encryption is performed using symmetric encryption algorithm (AES for example) using the change in “Key Exchange”. The size depends on the cipher-suite keys. (For example, on 128-bit AES encryption, to bruteforce the data sent, it is necessary to attempt 2 ^ 128 keys; BUT If the algorithm is RC4, there are many known attacks against this algorithm, so the chances are much greater that such encryption can be broken in a shorter time.)
使用以上交换的密钥,使用“密钥交换”中的更改,使用对称加密算法(例如AES)执行数据加密。 大小取决于密码套件密钥。 (例如,在128位AES加密上,要对发送的数据进行暴力破解,必须尝试使用2 ^ 128个密钥;但是,如果算法为RC4,则有很多已知的针对此算法的攻击,因此发生这种攻击的可能性要大得多。这样的加密可以在更短的时间内打破。)
我们可以做什么? (What can we do?)
As I said, by default, browsers send the full list of cipher-suite and server usually choose a simple and fast algorithm as RC4, for page loading speed and compatibility with older browsers. We can force the browser to choose a stronger cipher simply by changing the list of cipher-suites that the browser sends to the server, eliminating “weak” cipher like RC4.
就像我说的那样,默认情况下,浏览器会发送密码套件的完整列表,服务器通常会选择一种简单且快速的算法作为RC4,以提高页面加载速度并与旧版浏览器兼容。 我们可以通过更改浏览器发送到服务器的密码套件列表来强制浏览器选择更强的密码,消除像RC4这样的“弱”密码。
To do that, go to the configuration page in Firefox with about:config (in the url), after that, search for security.ssl.
为此,请使用about:config (位于URL中)转到Firefox中的配置页面,然后搜索security.ssl 。
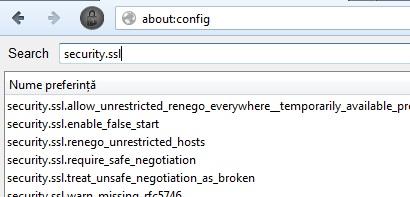
From here we can disable certain cipher suites. I cannot say with certainty which are safe and which are not, but I can recommend you to choose RSA (key exchange) and AES (256-bit). I have disabled all except RSA_AES_256_SHA.
从这里我们可以禁用某些密码套件。 我不能肯定地说哪些是安全的,哪些不是,但是我建议您选择RSA(密钥交换)和AES(256位)。 我已禁用除RSA_AES_256_SHA以外的所有内容。
结果 (The result)
Close the browser and reopen it and:
关闭浏览器并重新打开它,然后:

I hope this information will help you to browse over the internet in a safe way, avoiding at least MTIM attacks.
我希望这些信息将帮助您以安全的方式浏览Internet,至少避免MTIM攻击。
资源资源 (Resources)
- SSL/TLS – http://en.wikipedia.org/wiki/Transport_Layer_Security SSL / TLS – http://en.wikipedia.org/wiki/Transport_Layer_Security
- MITM – http://en.wikipedia.org/wiki/Man-in-the-middle_attack MITM – http://en.wikipedia.org/wiki/Man-in-the-middle_attack
- Calomel – https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/ Calomel – https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/
nas和nsa





















 788
788

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








