ssl证书类型rsa
This article was created in partnership with GoGetSSL. Thank you for supporting the partners who make SitePoint possible.
本文是与GoGetSSL合作创建的。 感谢您支持使SitePoint成为可能的合作伙伴。
Over the last decade, the rate of cyber crime has risen sharply. Already, many reputable business organizations and government agencies that haven’t implemented sufficient online security have been caught with their pants down. Google has started taking a strong stand against websites that don’t use HTTPS. Website visitors will be notified if they’re about to submit any information over an unsecured connection.
在过去的十年中,网络犯罪率急剧上升。 许多尚未实施足够的在线安全性的知名商业组织和政府机构已经陷入困境。 Google已开始坚决反对不使用HTTPS的网站。 如果网站访问者即将通过不安全的连接提交任何信息,则会收到通知。
In this article, you’ll learn how to protect your customers and your business from privacy invasion and data theft. You’ll learn how to use SSL technology to secure your websites and your applications from leaking sensitive data to eavesdroppers.
在本文中,您将学习如何保护您的客户和您的企业免遭隐私入侵和数据盗窃。 您将学习如何使用SSL技术来保护您的网站和应用程序,以防止敏感数据泄露给窃听者。
I won’t be able to show you how to install SSL, as that’s an advanced topic. You can find more information on the installation process here.
我将无法向您展示如何安装SSL,因为这是高级主题。 您可以在此处找到有关安装过程的更多信息。
SSL如何以简单的英语工作 (How SSL Works in Plain English)
Imagine you’re in your hotel room, on your laptop, connected to the hotel’s WIFI. You’re about to log in to your bank’s online portal. Meanwhile, a nefarious hacker has cleverly booked a room next to yours and has set up a simple workstation that listens to all network traffic in the hotel building. All traffic using the HTTP protocol can be seen by the hacker in plain text.
想象一下,您在笔记本电脑上的酒店房间中,已连接到酒店的WIFI。 您将要登录到银行的在线门户。 同时,一个邪恶的黑客巧妙地在您房间旁边预订了一个房间,并建立了一个简单的工作站来监听酒店大楼中的所有网络流量。 黑客可以用纯文本格式查看使用HTTP协议的所有流量。
Assuming the bank’s website is using only HTTP, form details such as user name and password will be seen by the hacker as soon you press submit. So how do we protect this data? The answer is obviously encryption. Encryption of data involves converting plain text data to something that looks garbled — aka encrypted data. To encrypt plain text data, you need what’s called an encryption algorithm and a cipher key.
假设银行的网站仅使用HTTP,那么一旦您按下“提交”,黑客就会看到诸如用户名和密码之类的表格详细信息。 那么我们如何保护这些数据呢? 答案显然是加密。 数据加密涉及将纯文本数据转换为看似乱码的东西,也就是加密数据。 要加密纯文本数据,您需要所谓的加密算法和密码密钥。
Let’s say you were to encrypt the following data:
假设您要加密以下数据:
Come on over for hot dogs and soda!It will look something like this in encrypted form:
它看起来像是加密形式:
wUwDPglyJu9LOnkBAf4vxSpQgQZltcz7LWwEquhdm5kSQIkQlZtfxtSTsmaw
q6gVH8SimlC3W6TDOhhL2FdgvdIC7sDv7G1Z7pCNzFLp0lgB9ACm8r5RZOBi
N5ske9cBVjlVfgmQ9VpFzSwzLLODhCU7/2THg2iDrW3NGQZfz3SSWviwCe7G
mNIvp5jEkGPCGcla4Fgdp/xuyewPk6NDlBewftLtHJVf
=PAb3Decrypting the above message without the cipher key can take more than a lifetime using current computing power. No one can read it unless they have the cipher key that was used to encrypt it. This type of encryption is known as symmetric encryption. Now that we’ve figured out how to protect data, we need a safe way to transmit the cipher key to the recipient of the message safely. We can do this by using an asymmetric encryption system known as public key cryptography.
使用当前的计算能力,不使用密码密钥对以上消息进行解密可能要花费一生以上的时间。 除非他们拥有用于加密它的密码密钥,否则任何人都无法读取它。 这种加密方式称为对称加密。 现在,我们已经找到了保护数据的方法,我们需要一种安全的方法来将密码密钥安全地传输到邮件的收件人。 我们可以通过使用称为公钥加密的非对称加密系统来做到这一点。
Public Key Cryptography uses a pair of mathematically related cipher keys:
公钥密码术使用一对数学上相关的密码密钥:
Public key: can be safely shared with anyone
公钥 :可以与任何人安全共享
Private key: must never be transmitted, stored in secret
私钥 :绝不能传输,秘密存储
When one key is used to encrypt, the other one is used to decrypt. The same key can’t be used to decrypt what it encrypted. Below is a depiction of how it works:
当一个密钥用于加密时,另一密钥用于解密。 不能使用同一密钥来解密它加密的内容。 以下是其工作方式的描述:

However, we can’t trust any public key issued to us since they can be generated by anyone. To ensure authenticity of public keys, they need to be packaged in what’s called an SSL certificate. This is a signed digital file that contains the following information:
但是,我们不能信任任何发给我们的公钥,因为它们可以由任何人生成。 为了确保公钥的真实性,需要将它们打包在所谓的SSL证书中。 这是一个签名的数字文件,包含以下信息:
- Subject’s name: individual, organization or machine name 主题名称:个人,组织或机器名称
- Public Key 公钥
- Digital Signature (certificate’s fingerprint) 数字签名(证书的指纹)
- Issuer (the entity that signed the certificate) 颁发者(签署证书的实体)
- Valid dates (start and expiry) 有效日期(开始和到期)
I’ve only listed the necessities. SSL certificates usually contain more information. Here’s a real-world example:
我只列出了必需品。 SSL证书通常包含更多信息。 这是一个真实的示例:
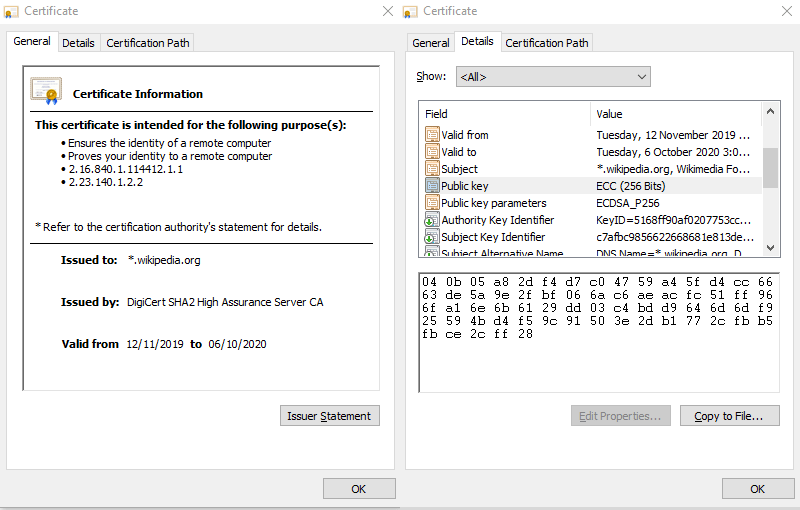
As you can see, the above certificate has been signed (see thumbnail section). A digital signature is simply an encrypted hash of a file. Let’s first explain what a hash is. Say you have a 100-word document, and you run it through a hashing program. You’ll get the following hash:
如您所见,以上证书已签名(请参见缩略图部分)。 数字签名只是文件的加密哈希。 让我们首先解释什么是哈希。 假设您有一个100字的文档,并通过一个哈希程序运行它。 您将获得以下哈希值:
46798b5cfca45c46a84b7419f8b74735If you change anything in the document, even if it’s adding single full stop, a completely new hash will be generated when you run the hashing function again:
如果您更改了文档中的任何内容,即使它添加了一个句号,当您再次运行哈希函数时,也会生成一个全新的哈希:
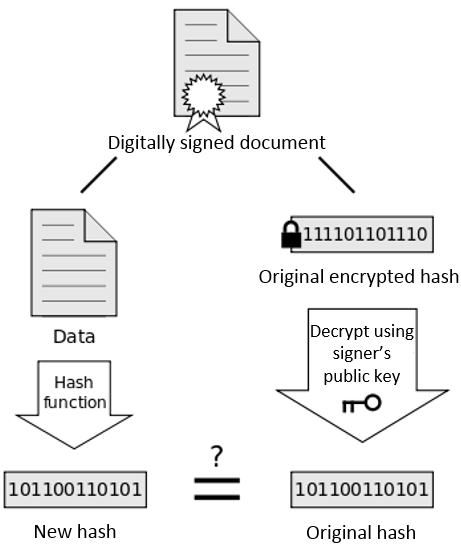
bc527343c7ffc103111f3a694b004e2fA mismatch in the hash between the hash sent and the one generated means that the file has been altered. This is the first line of defense for ensuring that an SSL certificate hasn’t been altered. However, we need to verify that sent hash was created by the issuer of the certificate. This is done by encrypting the hash using the issuer’s private key. When we perform a local hash of the certificate, then decrypt the certificate’s signature to obtain the sent hash, we can compare the two. If there’s a match, it means:
发送的散列和生成的散列之间的散列不匹配意味着该文件已被更改。 这是确保未更改SSL证书的第一道防线。 但是,我们需要验证发送的哈希是由证书的颁发者创建的。 这是通过使用发行者的私钥加密哈希来完成的。 当我们执行证书的本地哈希,然后解密证书的签名以获得发送的哈希时,我们可以将两者进行比较。 如果有匹配项,则表示:
- the certificate hasn’t been altered by someone else 证书未被其他人更改
- we have proof the certificate came from the issuer, since we’ve successfully decrypted the signature using their public key 我们已经证明证书来自颁发者,因为我们已经使用他们的公钥成功解密了签名
- we can trust the authenticity of the public key attached in the SSL certificate. 我们可以信任SSL证书中附加的公钥的真实性。
Now, you may be wondering where we get the issuer’s public key and why we should trust it. Well, the issuer’s public key already comes pre-installed inside our operating systems and browsers. An issuer is a trusted certificate authority (CA) that signs certificates in compliance with the official CA/Browser Forum guidelines and NIST recommendations. For example, here’s a list of trusted issuers/CAs that you’ll find on Microsoft’s Operating System. Even smartphones and tablets have a similar list pre-installed on the OS and browser.
现在,您可能想知道我们在哪里获得发行者的公钥以及为什么我们应该信任它。 好吧,发行人的公钥已经预先安装在我们的操作系统和浏览器中。 颁发者是受信任的证书颁发机构(CA),它按照官方的CA /浏览器论坛指南和NIST的建议对证书进行签名。 例如,这是您可以在Microsoft操作系统上找到的受信任的颁发者/ CA的列表 。 甚至智能手机和平板电脑都在操作系统和浏览器上预装了类似的列表。
According to a survey conducted by W3Techs on May 2018, the following issuers account for about 90% of valid certificates signed globally:
根据W3Techs在2018年5月进行的一项调查,以下发行人约占全球签署的有效证书的90%:
- IdenTrust IdenTrust
- Comodo 科莫多
- DigiCert (acquired by Symantec) DigiCert(赛门铁克收购)
- GoDaddy 去吧爸爸
- GlobalSign GlobalSign
Now that you have an understanding of encryption and SSL technology, it’s best to go over how you can safely sign in to your bank’s portal using HTTPS without the hacker next door reading your traffic.
既然您已经了解了加密和SSL技术,那么最好再研究一下如何使用HTTPS安全地登录银行门户,而无需让隔壁的黑客阅读您的流量。
- Your laptop’s browser starts by requesting the bank’s servers for its SSL certificate. 您的笔记本电脑的浏览器首先向银行的服务器请求其SSL证书。
- The server sends it. Then the browser checks the certificate is authentic against a list of trusted CAs. It also checks that it hasn’t expired and hasn’t been revoked. 服务器发送它。 然后,浏览器根据受信任的CA列表检查证书的真实性。 它还会检查它是否尚未过期并且尚未被吊销。
If everything checks out, the browser generates a new cipher key (also known as the session key). Using the public key found on the SSL certificate, it’s encrypted and then sent to the server.
如果一切顺利,浏览器将生成一个新的密码密钥 (也称为会话密钥 )。 使用在SSL证书上找到的公共密钥,将其加密,然后发送到服务器。
- The server decrypts the session key using its private key. 服务器使用其私钥解密会话密钥。
- From now on, all communication sent back and forth will be encrypted using the session key. Symmetric encryption is faster than asymmetric. 从现在开始,所有来回发送的通信都将使用会话密钥进行加密。 对称加密比非对称加密更快。
This means both form data going from the laptop, and HTML data coming from the server, will be encrypted using a cipher key that the hacker won’t have access to. All that will be seen in the captured traffic logs will be garbled letters and numbers. Your information has now been protected and kept private from prying eyes.
这意味着来自笔记本电脑的表单数据和来自服务器HTML数据都将使用黑客无法访问的密码密钥进行加密。 在捕获的流量日志中将看到的所有字母和数字都是乱码。 您的信息现已受到保护,并且不会被他人窥探。
Now that you understand how SSL in general works, let’s move on to the next section an look at the different types of SSL certificates we can use.
既然您已经了解了SSL的一般工作原理,那么让我们继续下一部分,看看我们可以使用的不同类型的SSL证书。
SSL类型 (Types of SSL)
域验证SSL证书 (Domain Validation SSL Certificates)
Domain Validation is the most affordable and common type of SSL certificates that can be issued to anyone to protect public domain websites. In order to purchase this type of SSL certificate, you need to prove you are the owner of the domain you want to protect. This is why it’s called domain validation. This is done through one or more of the following ways:
域验证是最经济,最常见的SSL证书类型,可以颁发给任何人以保护公共域网站。 为了购买这种SSL证书,您需要证明自己是要保护的域的所有者。 这就是为什么将其称为域验证的原因。 通过以下一种或多种方式完成此操作:
- creating a DNS TXT record 创建DNS TXT记录
responding to an email sent to the email contact registered in the domain’s whois records
回复发送给在域Whois记录中注册的电子邮件联系人的电子邮件
responding to an email sent to a well known administrative contact in your domain — such as
admin@domain.com回复发送到您域中知名管理联系人的电子邮件,例如
admin@domain.com- publishing a nonce provided by an automated certificate issuing system 发布自动证书颁发系统提供的随机数
Google Chrome is currently the most popular web browser with about 70% global desktop browser market share, as of September 2019. Google has recently stepped up its stance on enforcing security protocols on website owners to ensure end-user privacy is protected. Websites that aren’t protected are marked unsecure. Users are also highly discouraged if they try to submit a form to an unprotected website. If the website has an expired or invalid SSL certificate, the site will be temporarily blocked.
截至2019年9月,Google Chrome当前是最受欢迎的Web浏览器,在全球桌面浏览器市场中占有约70%的份额。Google最近加强了对网站所有者实施安全协议以确保最终用户隐私受到保护的立场。 未受保护的网站被标记为不安全。 如果用户尝试向不受保护的网站提交表单,也强烈建议他们不要这样做。 如果该网站具有过期或无效的SSL证书,则该网站将被暂时阻止。
If you don’t want to lose valuable traffic because your website is unprotected, you need to make sure you at least acquire a Domain Validation SSL certificate. It only takes 5–8 minutes to get issued with one.
如果您不想因为网站不受保护而损失宝贵的流量,则需要确保至少获得“ 域验证SSL”证书 。 只需要5到8分钟就能收到一张。
公共IP San SSL (Public IP San SSL)
SSL certificates are generally issued to protect a fully qualified domain name — such as www.domain.com. If you’d like to protect a public IP address, you’ll need to acquire a Public IP SAN SSL certificate. SAN stands for Subjective Alternative Name, which is a field on the certificate field that can be used to hold the IP Address.
通常颁发SSL证书来保护完全合格的域名,例如www.domain.com 。 如果要保护公共IP地址,则需要获取公共IP SAN SSL证书。 SAN代表主观备用名称,它是证书字段中的一个字段,可用于保存IP地址。
通配符SSL (Wildcard SSL)
A normal SSL certificate only applies to a single domain — such as www.domain.com. If you want to protect a subdomain, you’ll have to purchase a new SSL certificate for it. Instead of purchasing a new SSL certificate for every subdomain you manage, you can simply purchase a Wildcard SSL certificate, which will apply to your subdomains —that is, *.domain.com. It’s more cost effective than purchasing multiple SSL certificates. It’s also easier to to administrate using one SSL certificate.
普通SSL证书仅适用于单个域,例如www.domain.com 。 如果要保护子域,则必须为其购买新的SSL证书。 您无需为所管理的每个子域购买新的SSL证书,只需购买通配符SSL证书即可 ,该证书将应用于您的子域,即*.domain.com 。 它比购买多个SSL证书更具成本效益。 使用一个SSL证书进行管理也更加容易。
However, if a subdomain is compromised, it means all subdomains using the same certificate are compromised. You’ll need to revoke it and request for a new certificate. You can also purchase one separately if you don’t to face this type of issue.
但是,如果某个子域遭到破坏,则意味着使用同一证书的所有子域都受到破坏。 您需要吊销它并请求新证书。 如果您不面对此类问题,也可以单独购买 。
多域SSL证书 (Multi-domain SSL certificates)
As the name suggest, you can purchase a Multi-domain SSL certificate, which provides protection for up to 250 domains and subdomains. This type of certificate is particularly useful for protecting hundreds of office communication servers that may span across different geographic regions. Even if traffic is restricted to within a corporate network, it’s best to protect it as well using SSL, as it’s easy for a rogue employee to monitor and log everyone’s traffic.
顾名思义,您可以购买一个多域SSL证书,该证书可为多达250个域和子域提供保护。 这种类型的证书对于保护可能跨越不同地理区域的数百个办公室通信服务器特别有用。 即使流量仅限于公司网络内,最好还是使用SSL对其进行保护,因为流氓员工很容易监视和记录每个人的流量。
使用LEI代码更快地进行业务验证 (Faster Business Verification with LEI Code)
Since 2019, it has been possible to verify organizations using an LEI (Legal Entity Identifier) code globally. This simplifies and significantly speeds up the verification process. Businesses can receive an LEI code via official GLEIF registration agents.
自2019年以来,可以在全球范围内使用LEI(法律实体标识符)代码来验证组织。 这简化并大大加快了验证过程。 企业可以通过GLEIF官方注册代理获得LEI代码。
Legal Entity Identifier (LEI) is a unique code to identify any company worldwide participating in financial transactions. The process is done in accordance with the international standard ISO 17442. The goal is to help monitor and measure systemic risk, and effectively and inexpensively support compliance with regulatory reporting requirements.
法人实体标识符(LEI)是唯一的代码,用于标识全球范围内参与金融交易的任何公司。 该过程是根据国际标准ISO 17442完成的。目标是帮助监视和衡量系统性风险,并有效,廉价地支持对法规报告要求的遵守。
摘要 (Summary)
I hope you now have enough information to decide which SSL certificate to buy. Do note that SSL certificates are valid for only two years. This is a security feature to ensure information on certificates is kept up to date. It also ensures that any misplaced keys aren’t used to infiltrate traffic. Free SSL certificates are usually valid for 90 days. If you want to ensure you don’t forget to purchase a renewal, you can get a 3 or 4 year subscription plan. Do note the two-year limit rate applies. You’ll be contacted towards the end of the expiration date to replace the certificate with a new one. The advantage of choosing a longer subscription plan is that you save money as opposed to purchasing yearly.
我希望您现在有足够的信息来决定要购买哪个SSL证书。 请注意,SSL证书仅有效两年。 这是一项安全功能,可确保有关证书的信息保持最新。 它还可确保不会将任何放错位置的密钥用于渗透流量。 免费的SSL证书通常有效期为90天。 如果您想确保您不会忘记购买续订,则可以获取3或4年的订阅计划 。 请注意,适用两年限制率。 将会在有效期结束时与您联系,以将证书替换为新证书。 选择更长的订阅计划的优势在于,您可以省钱,而不是每年购买。
ssl证书类型rsa





















 400
400

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








