tcpdump is a command-line utility which allows us to capture and analyze network traffic going through our system. Depending on the filtering options, we can use this tool to effectively help troubleshoot any kind of network issues. It is a very commonly used tool by sysadmin engineers for these features.
tcpdump是一个命令行实用程序,它使我们可以捕获和分析通过系统的网络流量。 根据筛选选项,我们可以使用此工具有效地帮助排除任何类型的网络问题。 它是sysadmin工程师用于这些功能的非常常用的工具。
In this tutorial, we shall analyze some of the ways of using tcpdump, but not all. This is because there are simply way too many filtering options involved in this command, and it is not possible to cover all of them. We shall only look at some of the commonly used options here. You can find the rest on the man page.
在本教程中,我们将分析一些使用tcpdump的方法,但不是全部。 这是因为此命令中涉及太多的过滤选项,并且不可能涵盖所有这些选项。 在这里,我们仅介绍一些常用选项。 您可以在手册页上找到其余内容。
安装tcpdump命令 (Installing tcpdump command)
You can check if your system has the tcpdump command, by typing
您可以通过键入以下内容来检查系统是否具有tcpdump命令:
tcpdump --version
If the output shows that it is not installed, you can directly get it using your system’s package manager.
如果输出显示未安装,则可以使用系统的软件包管理器直接获取。
NOTE: Since we will be capturing packets, we need elevated permissions. (sudo is required). We will be prefixing all tcpdump commands with sudo as a result.
注意 :由于我们将捕获数据包,因此需要提升的权限。 (需要sudo )。 结果,我们将在所有tcpdump命令前加上sudo前缀。
列出用于数据包捕获的接口 (List interfaces for packet capture)
Before actively capturing packets, we shall look at the available interfaces fortcpdump.
在主动捕获数据包之前,我们将查看tcpdump的可用接口。
We can list interfaces using the -D (Display) option.
我们可以使用-D (显示)选项列出接口。
sudo tcpdump -D
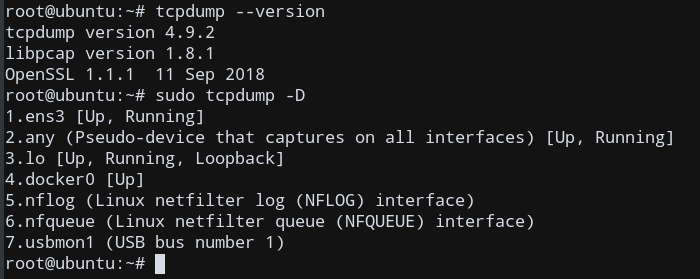
You will get a list of all available interfaces on your machine. This will depend from system to system, so mine has some other interfaces like Docker, since the Docker service is running, apart from typical network interfaces.
您将获得计算机上所有可用接口的列表。 这将因系统而异 ,因此,除了典型的网络接口之外,由于Docker服务正在运行,我的还有其他一些接口,例如Docker 。
The special interface any allows capturing in any active interface.
特殊接口any允许在任何活动接口中捕获。
Now that we know the available interfaces on our machine, let’s start capturing packets!
现在我们知道了机器上的可用接口,让我们开始捕获数据包!
使用tcpdump捕获数据包 (Capture Packets using tcpdump)
Capture all packets in any interface by running this command:
通过运行以下命令捕获任何接口中的所有数据包:
sudo tcpdump -i any
This will specify the interface to be any, the special interface mentioned earlier.
这将指定接口为any ,前面提到的特殊接口。
tcpdump continues to capture packets until it receives an interrupt signal. You can interrupt capturing by pressing Ctrl+C.
tcpdump继续捕获数据包,直到收到中断信号为止。 您可以通过按Ctrl+C中断捕获。
The Output will list all packet captures until the interrupt signal was received to terminate tcpdump.
输出将列出所有捕获的数据包,直到收到中断信号以终止tcpdump为止。
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
10:49:32.841984 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 4132693749:4132693857, ack 3344962610, win 1002, options [nop,nop,TS val 135269404 ecr 1623818400], length 108
10:49:32.842057 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 108:144, ack 1, win 1002, options [nop,nop,TS val 135269404 ecr 1623818400], length 36
10:49:32.842101 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 144:260, ack 1, win 1002, options [nop,nop,TS val 135269404 ecr 1623818400], length 116
10:49:32.842135 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 260:296, ack 1, win 1002, options [nop,nop,TS val 135269404 ecr 1623818400], length 36
...
...
^C
264 packets captured
361 packets received by filter
91 packets dropped by kernel
As you can observe, tcpdump had captured 264 packets. For example, since I am connected to this server using ssh, tcpdump captured all these packets.
如您所见, tcpdump捕获了264个数据包。 例如,由于我使用ssh连接到此服务器,因此tcpdump捕获了所有这些数据包。
数据包捕获的限制数量 (Limit number of Packet captures)
To limit the number of packets captured and stop tcpdump, use the -c (capture limit) option:
要限制捕获的数据包数量并停止tcpdump ,请使用-c (捕获限制)选项:
sudo tcpdump -i any -c 2
This will cause tcpdump command to stop capturing automatically after 2 packets. We won’t necessarily need to use the interrupt signal to terminate it manually in this case.
这将导致tcpdump命令在2个数据包后自动停止捕获。 在这种情况下,我们不一定需要使用中断信号来手动终止它。
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
10:57:31.284198 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 4132754245:4132754353, ack 3344963698, win 1002, options [nop,nop,TS val 135747845 ecr 1624296856], length 108
10:57:31.284275 IP 111.11.111.11.vultr.com.ssh > 123.45.678.90.48006: Flags [P.], seq 108:144, ack 1, win 1002, options [nop,nop,TS val 135747845 ecr 1624296856], length 36
2 packets captured
16 packets received by filter
8 packets dropped by kernel
This option can be quite useful in monitoring network connections for troubleshooting any problem, if there are network issues.
如果存在网络问题,此选项在监视网络连接以解决任何问题时非常有用。
禁用名称和端口解析 (Disable name and port resolution)
By default, tcpdump command resolves IP addresses and ports into names (such as vultr.com.ssh, which does the name resolution from the IP addresses and ports).
默认情况下, tcpdump命令将IP地址和端口解析为名称(例如vultr.com.ssh ,它从IP地址和端口进行名称解析)。
When troubleshooting network issues, it is often easier to use the IP addresses and port numbers; We can disable name resolution by using the option -n and port resolution with -nn.
解决网络问题时,通常更容易使用IP地址和端口号。 我们可以通过使用选项-n和端口解析与-nn来禁用名称解析。
sudo tcpdump -i any -c 2 -nn
The above command captures 2 packets on any interface, while disabling port resolution.
上面的命令在禁用端口解析的同时捕获任何接口上的2个数据包。
So the output will now stop any name resolution, and simply return the IP addresses and port numbers.
因此,输出现在将停止任何名称解析,仅返回IP地址和端口号。
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
11:00:36.459922 IP 111.11.111.11.22 > 123.45.678.90.48006: Flags [P.], seq 4132755513:4132755621, ack 3344963838, win 1002, options [nop,nop,TS val 135933020 ecr 1624482048], length 108
11:00:36.459982 IP 111.11.111.11.22 > 123.45.678.90.48006: Flags [P.], seq 108:144, ack 1, win 1002, options [nop,nop,TS val 135933020 ecr 1624482048], length 36
2 packets captured
8 packets received by filter
0 packets dropped by kernel
Here, let us examine a line of the output.
在这里,让我们检查输出的一行。
11:00:36.459922 IP 111.11.111.11.22 > 123.45.678.90.48006: Flags [P.], seq 4132755513:4132755621, ack 3344963838, win 1002, options [nop,nop,TS val 135933020 ecr 1624482048], length 108
This is a typical TCP packet capture. Other protocol packets and formats can be referred to in the tcpdump command manual page.
这是典型的TCP数据包捕获。 其他协议数据包和格式可以在tcpdump命令手册页中参考 。
The first field, 11:00:36.459922, represents the timestamp of the received packet as per the local clock.
第一个字段11:00:36.459922表示根据本地时钟接收的数据包的时间戳。
Next, IP represents the network layer protocol—in this case, IPv4. For IPv6 packets, the value is IP6.
接下来, IP代表网络层协议,在本例中为IPv4 。 对于IPv6数据包,该值为IP6 。
The next field, 111.11.111.11.22, is the source IP address and port. This is followed by the destination IP address and port, represented by 123.45.678.90.48006.
下一个字段111.11.111.11.22是源IP地址和端口。 随后是目标IP地址和端口,由123.45.678.90.48006表示。
Now that we know how the basic output format is, let us analyze some filtering options for tcpdump
现在我们知道基本的输出格式了,让我们分析一下tcpdump一些过滤选项
过滤数据包 (Filtering Packets)
One of tcpdump command’s most powerful features is its ability to filter the captured packets using a variety of parameters, such as source and destination IP addresses, ports, protocols, etc. Let’s look at some of the most common ones.
tcpdump命令最强大的功能之一是它能够使用各种参数(例如源和目标IP地址,端口,协议等) 过滤捕获的数据包的能力。让我们看一些最常见的参数。
根据协议过滤 (Filter based on Protocol)
To filter packets based on protocol, we need to specify the protocol in the command.
要基于协议过滤数据包,我们需要在命令中指定协议。
To capture ICMP packets only, we can filter based on ICMP protocol.
仅捕获ICMP数据包,我们可以基于ICMP协议进行过滤。
sudo tcpdump -i any -c 5 icmp
Since the ping command uses ICMP packets, we can analyze incoming packets due to ping from another machine.
由于ping命令使用ICMP数据包,因此我们可以分析由于来自另一台计算机的ping而引起的传入数据包。
Let’s ping our current machine and capture the incoming ping packets.
让我们ping我们当前的计算机并捕获传入的ping数据包。
Open a terminal session on another machine, and type
在另一台计算机上打开终端会话,然后键入
ping IP_ADDRESS_MACHINE_1
Now, in our tcpdump terminal session, we can now see that it captures those ICMP ping reply packets.
现在,在我们的tcpdump终端会话中,我们现在可以看到它捕获了那些ICMP ping应答数据包。
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
11:18:47.947475 IP 123.45.678.90 > 111.11.111.11.vultr.com: ICMP echo request, id 6068, seq 1, length 64
11:18:47.947554 IP 111.11.111.11.vultr.com > 123.45.678.90: ICMP echo reply, id 6068, seq 1, length 64
11:18:48.947669 IP 123.45.678.90 > 111.11.111.11.vultr.com: ICMP echo request, id 6068, seq 2, length 64
11:18:48.947752 IP 111.11.111.11.vultr.com > 123.45.678.90: ICMP echo reply, id 6068, seq 2, length 64
11:18:49.947853 IP 123.45.678.90 > 111.11.111.11.vultr.com: ICMP echo request, id 6068, seq 3, length 64
5 packets captured
6 packets received by filter
0 packets dropped by kernel
Here, 123.45.678.90 is the IP Address of the machine (Machine 2) which sends ping to our tcpdump system, and 111.11.111.11 is the IP Address of the packet filtering machine (Machine 1).
在这里, 123.45.678.90是将ping发送到我们的tcpdump系统的机器(机器2)的IP地址,而111.11.111.11是包过滤机器(机器1)的IP地址。
Since I was using ssh to send the ping requests, there is a domain resolution (but no name resolution) to vultr.com.
由于我使用ssh发送ping请求,因此vultr.com有一个域解析(但没有名称解析)。
根据主机过滤 (Filter based on Host)
To limit capture to only packets related to a specific host, we can use the host filter
为了将捕获限制为仅与特定主机相关的数据包,我们可以使用host过滤器
sudo tcpdump -i any -c5 -nn host 192.168.1.2
In this example, tcpdump captures and displays only packets to and from host 192.168.1.2.
在此示例中, tcpdump仅捕获并显示往返于主机192.168.1.2数据包。
根据端口过滤 (Filter based on Port)
To filter packets based on the desired service or port, use the port filter. For example, capture packets related to an ssh session by using this command (port 22 filtering):
要根据所需的服务或端口过滤数据包,请使用port过滤器。 例如,使用以下命令捕获与ssh会话相关的数据包(端口22过滤):
sudo tcpdump -i any -c5 -nn port 22
根据源IP /主机名过滤 (Filter based on Source IP/hostname)
You can also filter packets based on the source or destination IP Address or hostname. For example, to capture packets from host 192.168.1.2
您还可以根据源或目标IP地址或主机名过滤数据包。 例如,从主机192.168.1.2捕获数据包
sudo tcpdump -i any -c 5 -nn src 192.168.1.2
We can use dst to filter by destination IP/hostname also.
我们也可以使用dst按目标IP /主机名进行过滤。
sudo tcpdump -i any -c 5 -nn src 172.168.1.2
保存数据包捕获 (Save Packet captures)
We can save the results of the packet captures into a file for analysis later.
我们可以将数据包捕获的结果保存到文件中以供以后分析。
To save packets to a file instead of displaying them on screen, use the option -w:
要将数据包保存到文件而不是在屏幕上显示,请使用选项-w :
sudo tcpdump -i any -c 5 -nn -w sample.pcap port 22
This command saves the output in a file named sample.pcap. The .pcap the extension stands for “packet capture” and is the convention for this file format.
此命令将输出保存在名为sample.pcap的文件中。 扩展名.pcap表示“数据包捕获”,并且是此文件格式的约定。
结论 (Conclusion)
In this tutorial, we learned how we could perform packet capturing and filtering based on different options, using the tcpdump command.
在本教程中,我们学习了如何使用tcpdump命令基于不同的选项执行数据包捕获和过滤。





















 292
292

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








