一.实验拓扑
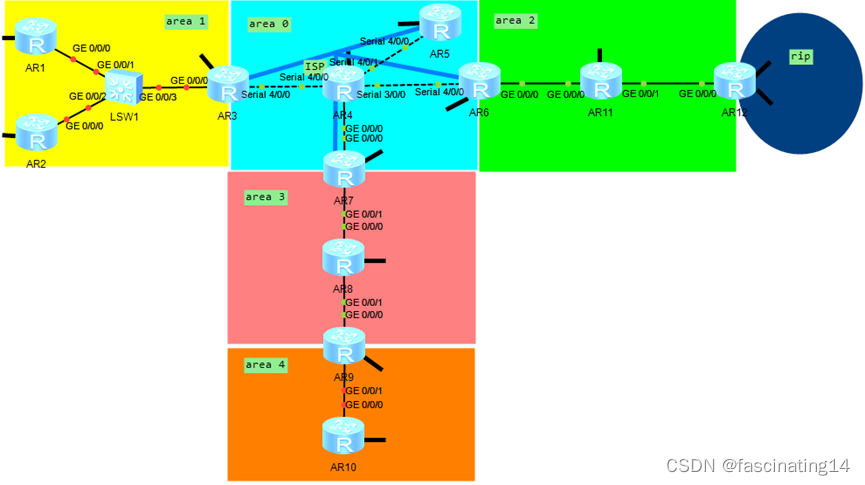
二.实验要求
1.R4为ISP,其上只能配置IP地址;R4与其他所有直连设备间均使用公有IP
2.R3-R5/R6/R7为MGRE环境,R3为中心站点;
3.整个OSPF环境IP基于172.16.0.0/16划分;
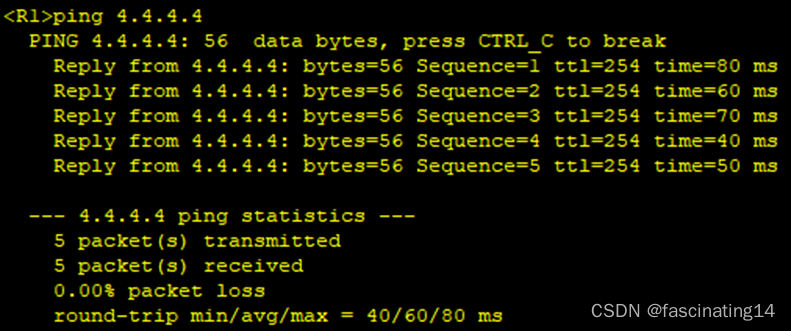
4.所有设备均可访问R4的环回;
5.减少LSA的更新量,加快收敛,保障更新安全;
6.全网可达
三.路由器配置及ip分配
1.ip分配
172.16.0.0/16
172.16.0.0/19---A0
172.16.0.0/24---P2P
172.16.0.0/30
172.16.0.4/30
172.16.0.8/30
……
172.16.1.0/24---MA
172.16.1.0/29
172.16.1.8/29
172.16.1.16/29
……
172.16.2.0/24
……
172.16.31.0/24
172.16.32.0/19---A1
172.16.32.0/24
172.16.33.0/24
……
172.16.63.0/24
172.16.64.0/19---A2
172.16.96.0/19---A3
172.16.128.0/19---A4
172.16.160.0/19---RIP
172.16.160.0/20
172.16.176.0/20
172.16.192.0/19
172.16.224.0/19
2.路由器配置
R1:
[V200R003C00]
#
sysname R1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.33.1 255.255.255.248
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.34.1 255.255.255.0
#
ospf 1 router-id 1.1.1.1
area 0.0.0.1
network 172.16.0.0 0.0.255.255
stub
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R2:
[V200R003C00]
#
sysname R2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.33.2 255.255.255.248
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.35.1 255.255.255.0
#
ospf 1 router-id 2.2.2.2
area 0.0.0.1
network 172.16.0.0 0.0.255.255
stub
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R3:
[V200R003C00]
#
sysname R3
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 172.16.0.0 0.0.255.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ip address 34.0.0.1 255.255.255.0
nat outbound 2000
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 172.16.33.3 255.255.255.248
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.36.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 172.16.1.1 255.255.255.248
tunnel-protocol gre p2mp
source 34.0.0.1
ospf network-type p2mp
ospf timer hello 10
nhrp entry multicast dynamic
nhrp network-id 100
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 172.16.1.1 0.0.0.0
area 0.0.0.1
abr-summary 172.16.32.0 255.255.224.0
network 172.16.32.0 0.0.7.255
stub no-summary
#
ip route-static 0.0.0.0 0.0.0.0 34.0.0.2
ip route-static 172.16.32.0 255.255.224.0 NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R4:
[V200R003C00]
#
sysname R4
#
board add 0/3 2SA
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial3/0/0
link-protocol ppp
ip address 46.0.0.2 255.255.255.0
#
interface Serial3/0/1
link-protocol ppp
#
interface Serial4/0/0
link-protocol ppp
ip address 34.0.0.2 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
ip address 45.0.0.2 255.255.255.0
#
interface GigabitEthernet0/0/0
ip address 47.0.0.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R5:
[V200R003C00]
#
sysname R5
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ip address 45.0.0.1 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.2.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 172.16.1.2 255.255.255.248
tunnel-protocol gre p2mp
source Serial4/0/0
ospf network-type p2mp
ospf timer hello 10
nhrp network-id 100
nhrp entry 172.16.1.1 34.0.0.1 register
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 172.16.0.0 0.0.255.255
#
ip route-static 0.0.0.0 0.0.0.0 45.0.0.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R6:
[V200R003C00]
#
sysname R6
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 172.16.0.0 0.0.255.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ip address 46.0.0.1 255.255.255.0
nat outbound 2000
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
ip address 172.16.65.1 255.255.255.248
ospf authentication-mode md5 1 cipher %$%$7k~<YjI(T1{~83=)U=uFokYP%$%$
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.3.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 172.16.1.3 255.255.255.248
tunnel-protocol gre p2mp
source Serial4/0/0
ospf network-type p2mp
ospf timer hello 10
nhrp network-id 100
nhrp entry 172.16.1.1 34.0.0.1 register
#
ospf 1 router-id 6.6.6.6
area 0.0.0.0
network 172.16.0.0 0.0.3.255
area 0.0.0.2
abr-summary 172.16.64.0 255.255.224.0
network 172.16.65.1 0.0.0.0
nssa no-summary
#
ip route-static 0.0.0.0 0.0.0.0 46.0.0.2
ip route-static 172.16.64.0 255.255.224.0 NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R7:
[V200R003C00]
#
sysname R7
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
acl number 2000
rule 5 permit source 172.16.0.0 0.0.255.255
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 47.0.0.1 255.255.255.0
nat outbound 2000
#
interface GigabitEthernet0/0/1
ip address 172.16.97.1 255.255.255.248
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.4.1 255.255.255.0
#
interface Tunnel0/0/0
ip address 172.16.1.4 255.255.255.248
tunnel-protocol gre p2mp
source GigabitEthernet0/0/0
ospf network-type p2mp
ospf timer hello 10
nhrp network-id 100
nhrp entry 172.16.1.1 34.0.0.1 register
#
ospf 1 router-id 7.7.7.7
area 0.0.0.0
network 172.16.0.0 0.0.7.255
area 0.0.0.3
abr-summary 172.16.96.0 255.255.224.0
network 172.16.97.1 0.0.0.0
nssa no-summary
#
ip route-static 0.0.0.0 0.0.0.0 47.0.0.2
ip route-static 172.16.96.0 255.255.224.0 NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R8:
[V200R003C00]
#
sysname R8
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.97.2 255.255.255.248
#
interface GigabitEthernet0/0/1
ip address 172.16.97.9 255.255.255.248
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.98.1 255.255.255.0
#
ospf 1 router-id 8.8.8.8
area 0.0.0.3
network 172.16.0.0 0.0.255.255
nssa
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R9:
[V200R003C00]
#
sysname R9
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.97.10 255.255.255.248
#
interface GigabitEthernet0/0/1
ip address 172.16.129.1 255.255.255.248
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.130.1 255.255.255.0
#
ospf 1 router-id 9.9.9.9
asbr-summary 172.16.128.0 255.255.224.0
import-route ospf 2
area 0.0.0.3
network 172.16.97.10 0.0.0.0
nssa
#
ospf 2 router-id 9.9.9.9
area 0.0.0.4
network 172.16.128.0 0.0.3.255
#
ip route-static 172.16.128.0 255.255.224.0 NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R10:
[V200R003C00]
#
sysname R10
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.129.2 255.255.255.248
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.131.1 255.255.255.0
#
ospf 1 router-id 10.10.10.10
area 0.0.0.4
network 172.16.0.0 0.0.255.255
#
ip route-static 0.0.0.0 0.0.0.0 172.16.129.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R11:
[V200R003C00]
#
sysname R11
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.65.2 255.255.255.248
ospf authentication-mode md5 1 cipher %$%$^tz]NU2ZlJdcdhYT|hxMolh%%$%$
#
interface GigabitEthernet0/0/1
ip address 172.16.65.9 255.255.255.248
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.66.1 255.255.255.0
#
ospf 1 router-id 11.11.11.11
area 0.0.0.2
network 172.16.0.0 0.0.255.255
nssa
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
R12:
[V200R003C00]
#
sysname R12
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.65.10 255.255.255.248
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 172.16.160.1 255.255.240.0
#
interface LoopBack1
ip address 172.16.176.1 255.255.240.0
#
ospf 1 router-id 12.12.12.12
asbr-summary 172.16.160.0 255.255.224.0
import-route rip 1
area 0.0.0.2
network 172.16.65.10 0.0.0.0
nssa
#
rip 1
version 2
network 172.16.0.0
#
ip route-static 172.16.160.0 255.255.224.0 NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
Return
四.实验结果
1.通过配置ip和做一条指向R4的缺省做通公网area 0。
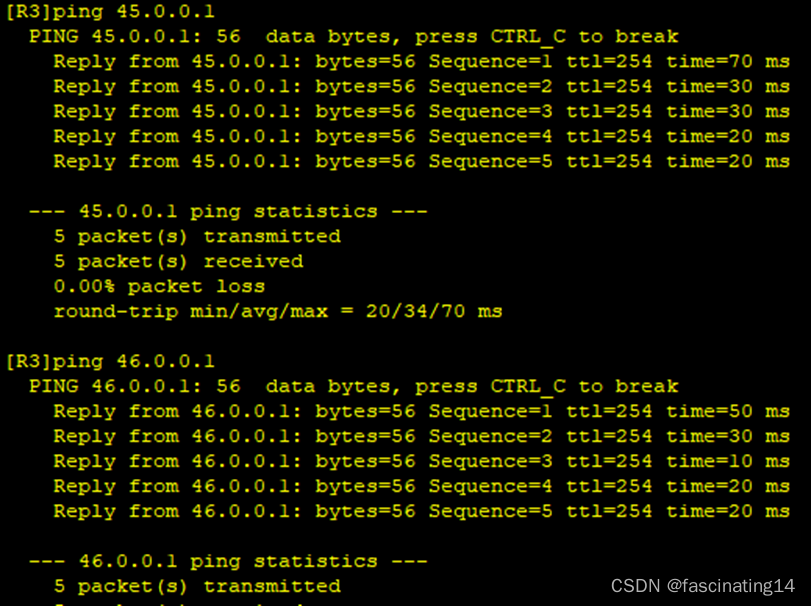
2.配置MGRE且在中心站点开启伪广播
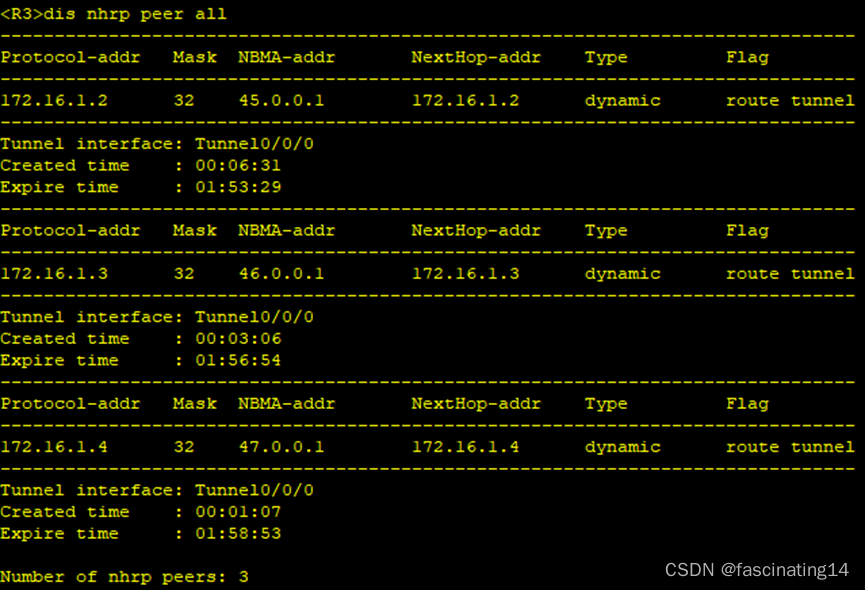
3.配置ospf,修改Tunnel的网络类型为p2mp,不需要进行DR、BDR选举。

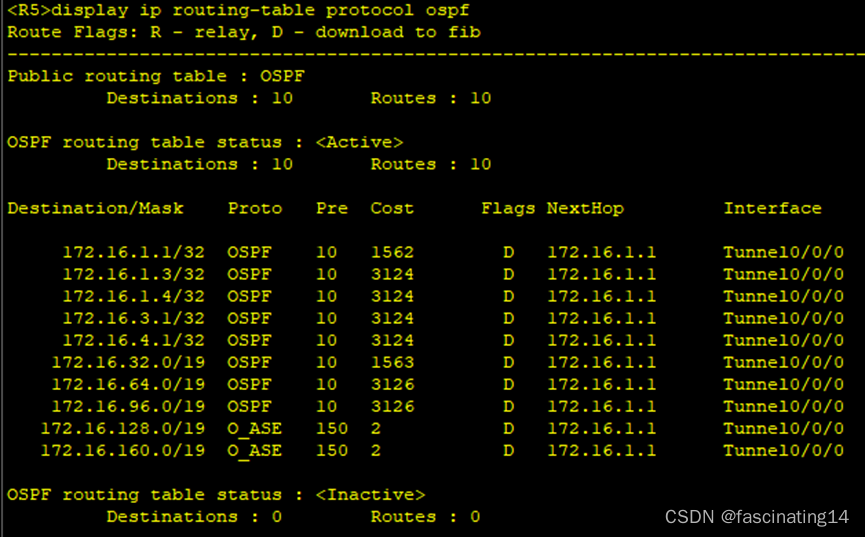
4.在rip处配置重发布,在区域4进行双向重发布,得到一张完成的路由表。
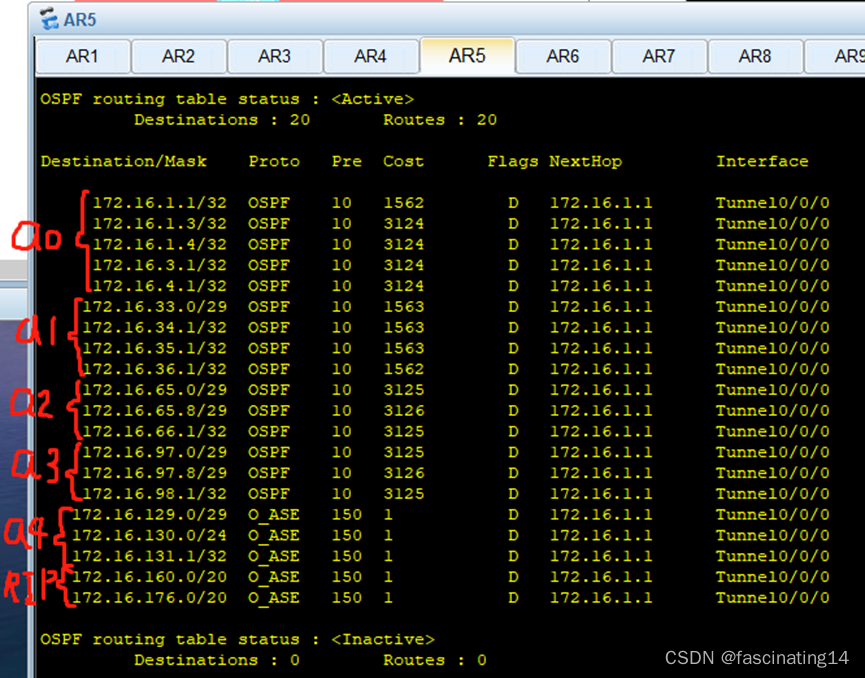
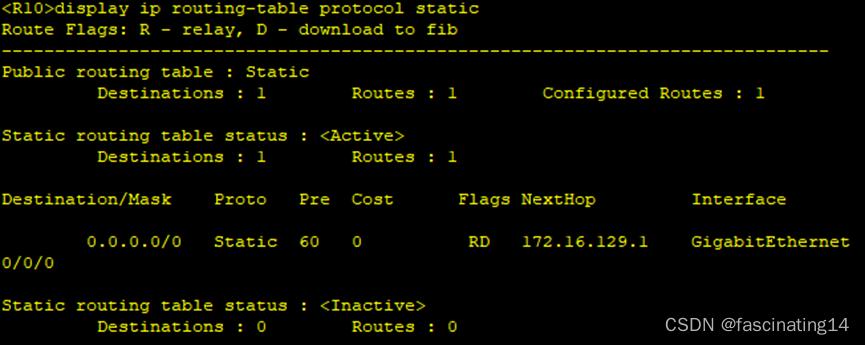
5.在R10写一条指向R9的缺省,使10可以正常ping通私网路由,至此全网通。

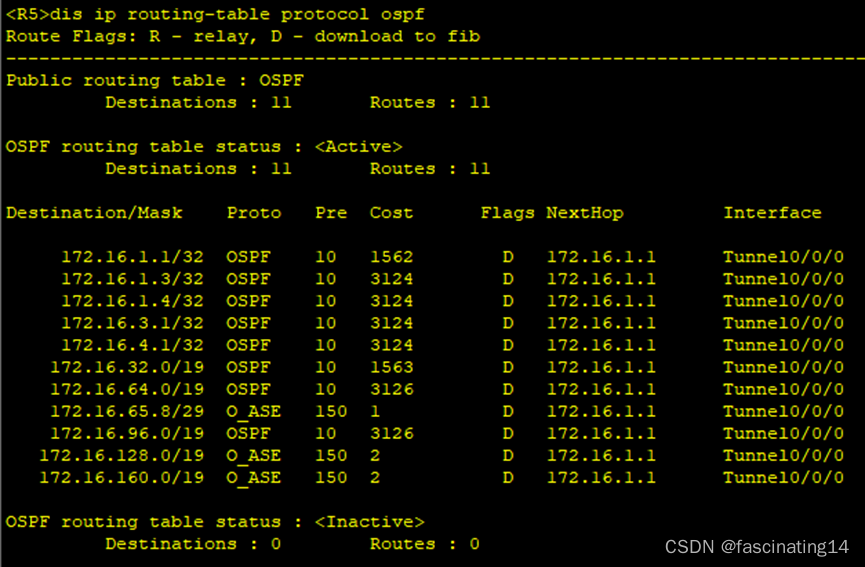
6.通过在abr和asbr设备上做汇总以减少路由条目
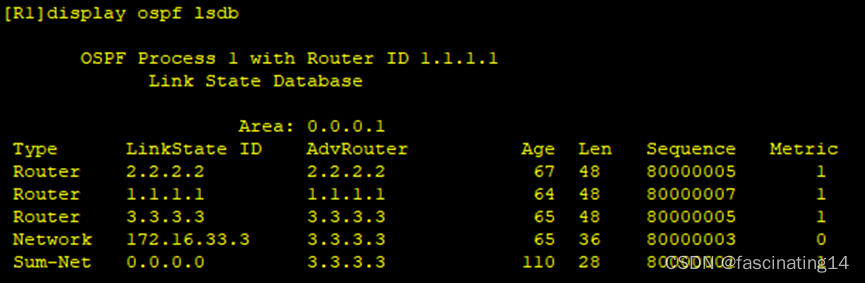
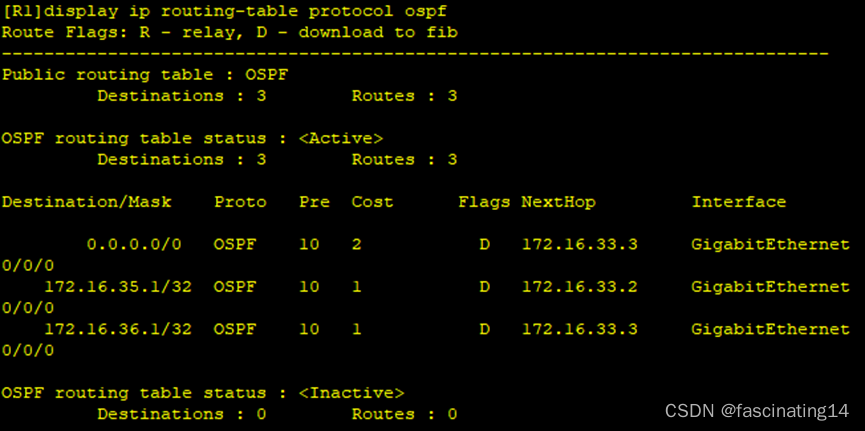
7.通过做特殊区域进一步减少路由条目
Area1:区域以只剩下一类二类和一个三类缺省
Area2:区域2只剩下一类二类三类七类
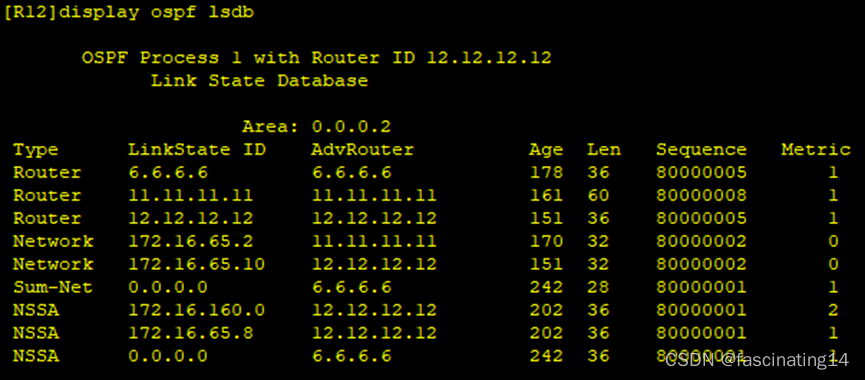
Area3:区域3只剩下一类二类三类七类
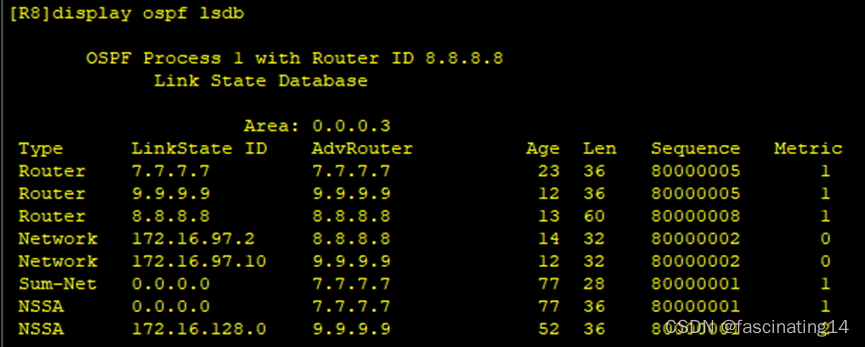
骨干区域路由条目:
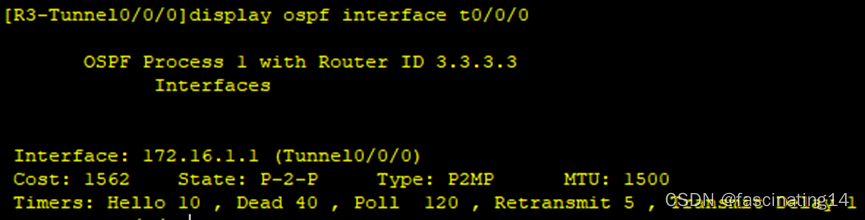
8.通过修改hello时间加快收敛。
9.通过认证保证更新安全。
ospf authentication-mode md5 1 cipher 123456
10.防环
[R3]ip route-static 172.16.32.0 19 NULL 0
[R6]ip route-static 172.16.64.0 19 NULL 0
[R7]ip route-static 172.16.96.0 19 NULL 0
[R9]ip route-static 172.16.128.0 19 NULL 0
[R12]ip route-static 172.16.160.0 19 NULL 0
11.通过配置nat使所有设备均可访问R4环回。






















 927
927











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








