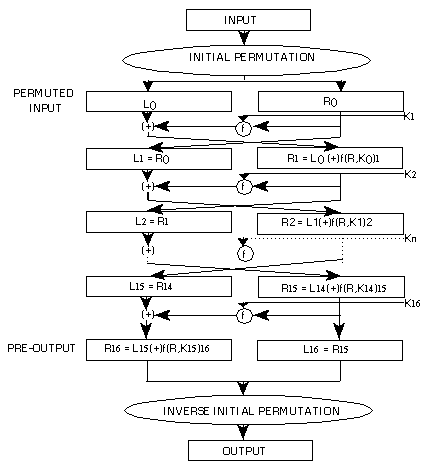
From the figure we can see that the mainly attention should be take in the following item
1. What is the Initial Permutation?
2. How the K1 K2 to K16 generate?
3. What is the cipher function f in the figure?
4. What is the Inverse Initial Permutation? this is similar with the question 1
Initial Permutation
So first let me explanation what is the Initial Permutation.
The input block which consist 64 bits plain text take permute transform at first. The table of the permute transform as below.
IP
58 50 42 34 26 18 10 2
60 52 44 36 28 20 12 4
62 54 46 38 30 22 14 6
64 56 48 40 32 24 16 8
57 49 41 33 25 17 9 1
59 51 43 35 27 19 11 3
61 53 45 37 29 21 13 5
63 55 47 39 31 23 15 7
The table is called as IP(Initial Permutation), and denoted as the block of the 64 bits’ bit 58 is used as the new block’s first bit, and 50 of the old as the next bit of the new block, and so on , the bit 7 as the last bit of the new output block.
And the inverse Initial Permutation is the inverse of the IP
IP-1
40 8 48 16 56 24 64 32
39 7 47 15 55 23 63 31
38 6 46 14 54 22 62 30
37 5 45 13 53 21 61 29
36 4 44 12 52 20 60 28
35 3 43 11 51 19 59 27
34 2 42 10 50 18 58 26
33 1 41 9 49 17 57 25
How The K1 to K16 generate?
The Sketch of Key Generation is shown below:
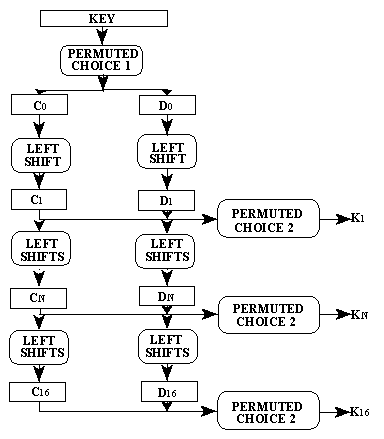
The Primitive key takes a permuted choice according the table below:
PC-1
57 49 41 33 25 17 9
1 58 50 42 34 26 18
10 2 59 51 43 35 27
19 11 3 60 52 44 36
63 55 47 39 31 23 15
7 62 54 46 38 30 22
14 6 61 53 45 37 29
21 13 5 28 20 12 4
The permutation produce two group bits: first group of the permutation is denoted as C0 and the second denoted as D0. Then both C0 and D0 performed LEFT SHIFTS by 1 or 2 bits and produce C1 and D1. Then the combination of C1 and D1 perform another PERMUTED CHOICE and produce K1. And so on, the K1 and D1 perform LEFT SHIFTS and PERMUTED CHOICE and produce K2 and then K3 to K16. And the iteration number is different in each round. The iteration number for each round and PERMUTED CHOICE 2 after LEFT SHIFTS are described in the figures below.
PC-1
14 17 11 24 1 5
3 28 15 6 21 10
23 19 12 4 26 8
16 7 27 20 13 2
41 52 31 37 47 55
30 40 51 45 33 48
44 49 39 56 34 53
46 42 50 36 29 32
| Iteration number | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
| Left Shift number | 1 | 1 | 2 | 2 | 2 | 2 | 2 | 2 | 1 | 2 | 2 | 2 | 2 | 2 | 2 | 1 |
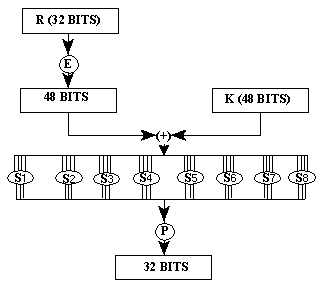
what is the funciton f
A sketch of the calculation of f(R,K) is given in Figure below
Which the E denote as Expansion Permutation. During the Expansion Permutation the 32bits input
is expanded to 48 bits. The E denote a function which takes a block of 32 bits as
input and yield a block of 48 bits as output. The Expansion Permutation table is
shown below.
32 1 2 3 4 5
4 5 6 7 8 9
8 9 10 11 12 13
12 13 14 15 16 17
16 17 18 19 20 21
20 21 22 23 24 25
24 25 26 27 28 29
28 29 30 31 32 1
Then the out put of E perform a XOR with the 48bits key. The result of XOR is writed as 8 blocks ,
each block has 6 bits. Every block in 8 blocks corresponding a Substitution table,which Substitution boxes
(also called S-boxes) S-boxes take a block of 6 bits as input and yield a block of 4 bits as output.
the 8 S-boxes tables a shown below.
S1
14 4 13 1 2 15 11 8 3 10 6 12 5 9 0 7
O 15 7 4 14 2 13 1 10 6 12 11 9 5 3 8
4 1 14 8 13 6 2 11 15 12 9 7 3 10 5 0
15 12 8 2 4 9 1 7 5 11 3 14 10 O 6 13
S2
15 1 8 14 6 11 3 4 9 7 2 13 12 O 5 10
3 13 4 7 15 2 8 14 12 0 1 10 6 9 11 5
0 14 7 11 10 4 13 1 5 8 12 6 9 3 2 15
13 8 10 1 3 15 4 2 11 6 7 12 0 5 14 9
S3
10 0 9 14 6 3 15 5 1 13 12 7 11 4 2 8
13 7 O 9 3 4 6 10 2 8 5 14 12 11 15 1
13 6 4 9 8 15 3 0 11 1 2 12 5 10 14 7
1 10 13 0 6 9 8 7 4 15 14 3 11 5 2 12
S4
7 13 14 3 0 6 9 10 1 2 8 5 11 12 4 15
13 8 11 5 6 15 O 3 4 7 2 12 1 10 14 9
10 6 9 0 12 11 7 13 15 1 3 14 5 2 8 4
3 15 O 6 10 1 13 8 9 4 5 11 12 7 2 14
S5
2 12 4 1 7 10 11 6 8 5 3 15 13 O 14 9
14 11 2 12 4 7 13 1 5 0 15 10 3 9 8 6
4 2 1 11 10 13 7 8 15 9 12 5 6 3 O 14
11 8 12 7 1 14 2 13 6 15 O 9 10 4 5 3
S6
12 1 10 15 9 2 6 8 O 13 3 4 14 7 5 11
10 15 4 2 7 12 9 5 6 1 13 14 O 11 3 8
9 14 15 5 2 8 12 3 7 0 4 10 1 13 11 6
4 3 2 12 9 5 15 10 11 14 1 7 6 0 8 13
S7
4 11 2 14 15 0 8 13 3 12 9 7 5 10 6 1
13 0 11 7 4 9 1 10 14 3 5 12 2 15 8 6
1 4 11 13 12 3 7 14 10 15 6 8 0 5 9 2
6 11 13 8 1 4 10 7 9 5 0 15 14 2 3 12
S8
13 2 8 4 6 15 11 1 10 9 3 14 5 0 12 7
1 15 13 8 10 3 7 4 12 5 6 11 0 14 9 2
7 11 4 1 9 12 14 2 0 6 10 13 15 3 5 8
2 1 14 7 4 10 8 13 15 12 9 0 3 5 6 11
Now Let's the input of 6 bits is B. we take the first and the last bits combined as a
2 based number range from 0 to 3. Let that number be R the combine the middle 4 bits of the B as another 2
based nuumber range from 0 to 7. Let that number be C. So the input of block will take
the number Si S-boxes table's row R and Column C as it's output. you can see that all the
number in the S-boxes are all range from 0 to 15. you can use 4 bits to denote the number
so the output is 4 bits.
All the 8 group of s-boxes combine as a 32 bits output and perform Permutation straight
we call it P-box Permutation
P-box Permutation
16 7 20 21 29 12 28 17
1 15 23 26 5 18 31 10
2 8 24 14 32 27 3 9
19 13 30 6 22 11 4 25
until this i have finished the introduce about DES. There must be many errores in this article
this is my first article write in English. if you find any errors please let me know. i will very
glad to modify it.






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








