一、优缺点
优点:
比xp框架适用范围广,大部分软件都没有检测frida,能绕过绝大部分单向证书绑定。
缺点:
还是不适用双向证书,还是需要分析app包逆向分析证书密码。
二、步骤:
1.安装frida
客户端(PC)
pip install frida
pip install frida-tools服务端(安卓手机)
在https://github.com/frida/frida/releases下载对应平台的服务端
然后解压,移动到Android设备
adb push frida-server-12.5.7-android-x86 /data/local/tmp/
adb shell
cd /data/local/tmp/
chmod 777 frida-server-12.5.7-android-x862.运行frida服务
./frida-server-12.5.7-android-x86
adb forward tcp:27042 tcp:27042
adb forward tcp:27043 tcp:270433.启动一键Hook
首先打开APP,查询包名
adb shell "dumpsys window | grep mCurrentFocus"从某个师傅那里搞来的脚本,也是用来绕过SSL Pinning,一键自动化抓取Https流量
frida.exe -U -f cn.soulapp.android -l C:\Users\admin\Desktop\app\hook-ssl.js --no-pause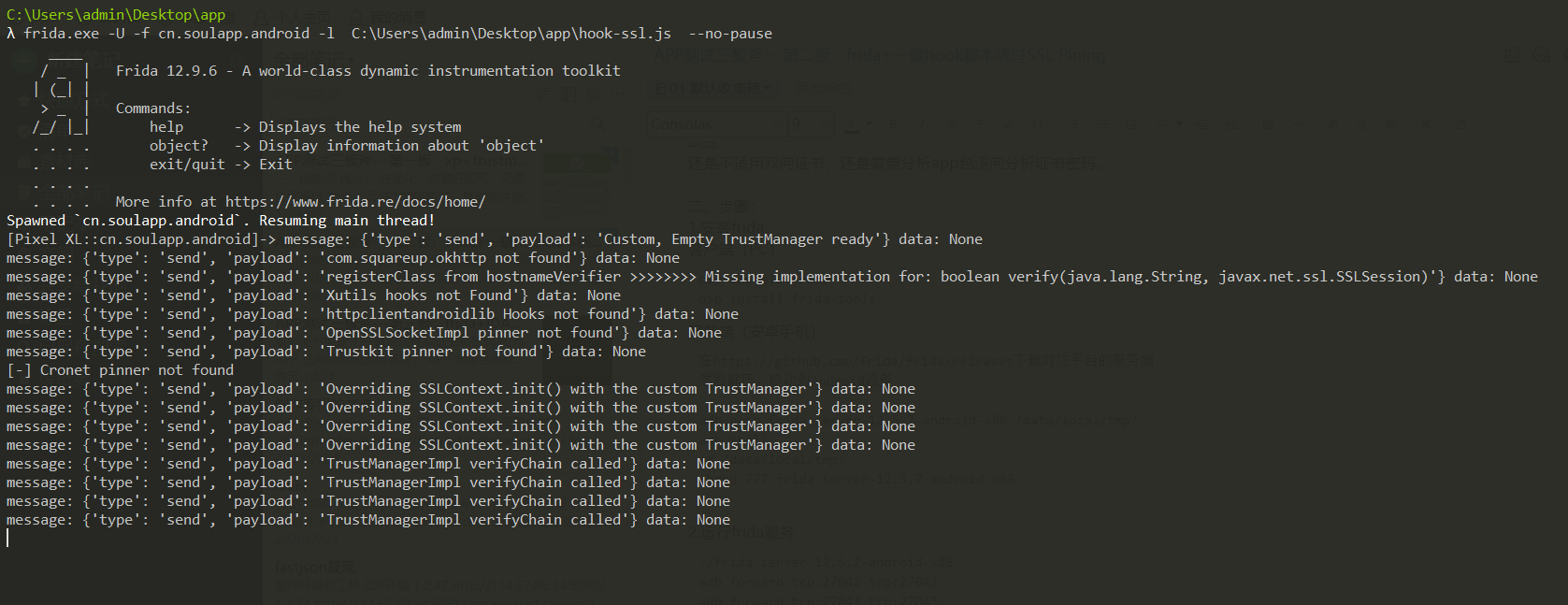
一键Hook脚本 hook-ssl.js
Java.perform(function() {
/*
hook list:
1.SSLcontext
2.okhttp
3.webview
4.XUtils
5.httpclientandroidlib
6.JSSE
7.network\_security\_config (android 7.0+)
8.Apache Http client (support partly)
9.OpenSSLSocketImpl
10.TrustKit
11.Cronet
*/
// Attempts to bypass SSL pinning implementations in a number of
// ways. These include implementing a new TrustManager that will
// accept any SSL certificate, overriding OkHTTP v3 check()
// method etc.
var X509TrustManager = Java.use('javax.net.ssl.X509TrustManager');
var HostnameVerifier = Java.use('javax.net.ssl.HostnameVerifier');
var SSLContext = Java.use('javax.net.ssl.SSLContext');
var quiet_output = false;
// Helper method to honor the quiet flag.
function quiet_send(data) {
if (quiet_output) {
return;
}
send(data)
}
// Implement a new TrustManager
// ref: https://gist.github.com/oleavr/3ca67a173ff7d207c6b8c3b0ca65a9d8
// Java.registerClass() is only supported on ART for now(201803). 所以android 4.4以下不兼容,4.4要切换成ART使用.
/*
06-07 16:15:38.541 27021-27073/mi.sslpinningdemo W/System.err: java.lang.IllegalArgumentException: Required method checkServerTrusted(X509Certificate[], String, String, String) missing
06-07 16:15:38.542 27021-27073/mi.sslpinningdemo W/System.err: at android.net.http.X509TrustManagerExtensions.<init>(X509TrustManagerExtensions.java:73)
at mi.ssl.MiPinningTrustManger.<init>(MiPinningTrustManger.java:61)
06-07 16:15:38.543 27021-27073/mi.sslpinningdemo W/System.err: at mi.sslpinningdemo.OkHttpUtil.getSecPinningClient(OkHttpUtil.java:112)
at mi.sslpinningdemo.OkHttpUtil.get(OkHttpUtil.java:62)
at mi.sslpinningdemo.MainActivity$1$1.run(MainActivity.java:36)
*/
var X509Certificate = Java.use("java.security.cert.X509Certificate");
var TrustManager;
try {
TrustManager = 







 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 1244
1244











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








