这里选择不对root进行直接操作,也就是会出现各个用户所对应的key
1.新增登陆用户,分配root权限组
[root@localhost ~]# adduser zhw2
[root@localhost ~]# passwd zhw2
Changing password for user zhw2.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.
分配权限组
[root@localhost ~]# visudoroot ALL=(ALL) ALL
zhw ALL=(ALL) ALL #添加
zhw2 ALL=(ALL) ALL #添加
2.修改ssh服务器配置文件
[root@localhost ~]# vim /etc/ssh/sshd_config修改对应位置
#允许root认证登录
PermitRootLogin yes
#允许密钥认证
#RSAAuthentication (rsa认证)是只支持第1代ssh通讯协议使用的配置项,在CentOS7.4中被废除了,而且前面提到过CentOS7开始预设使用第二代通讯协议,在CentOS7.4中没有找到指定协议版本的配置行,
RSAAuthentication yes
#第2代ssh通讯协议的密钥验证选项是
PubkeyAuthentication yes
#默认公钥存放的位置
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication yes #可使用密码进行ssh登录3.重启ssh服务器
service sshd restart4.切换用户到zhw2
[zhw2@localhost ~]$ ssh-keygen -t rsa
回车到结束!
id_rsa.pub(公钥)
id_rsa(私钥)
[zhw2@localhost ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/zhw2/.ssh/id_rsa):
Created directory '/home/zhw2/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/zhw2/.ssh/id_rsa.
Your public key has been saved in /home/zhw2/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:ejpL30daxTyQHAKqBZQ5omG+9krbXovtt75ZAR6Wikg zhw2@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
| .oo .....o |
|... +. .. .+ |
|oE . .o= + |
|o.. .o+ o = |
| ..... .S. . . |
| o . . o |
|... .o .. + |
|. o.+.o=o.. . |
| oo+.+=B+ .. |
+----[SHA256]-----+
切换到用户目录,将公钥文件重命名为authorized_keys
[zhw2@localhost ~]$ cd /home/zhw2/.ssh/
[zhw2@localhost .ssh]$ mv id_rsa.pub authorized_keys
将目录.ssh权限设置为700,公钥文件authorized_keys设置为644
[zhw2@localhost .ssh]$ chmod 700 ../.ssh/
[zhw2@localhost .ssh]$ chmod 644 authorized_keys
5.进行ssh测试(针对生成key的用户组)
[zhw2@localhost ~]$ ssh 192.168.163.122
The authenticity of host '192.168.163.122 (192.168.163.122)' can't be established.
ECDSA key fingerprint is SHA256:jROccStnTU3ONKCFDDWC7hDJe/uFppaZ45LImsl8SNQ.
ECDSA key fingerprint is MD5:f9:09:ad:29:66:06:1d:13:ab:7f:71:f9:25:6e:99:e0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.163.122' (ECDSA) to the list of known hosts.
Last login: Tue Mar 12 02:20:39 2019
[zhw2@localhost ~]$
6.下载私钥,putty远程登陆。切换到root。下载私钥文件到本地(也可用winscp 直接下载)
使用puttygen.exe,生成ppk文件
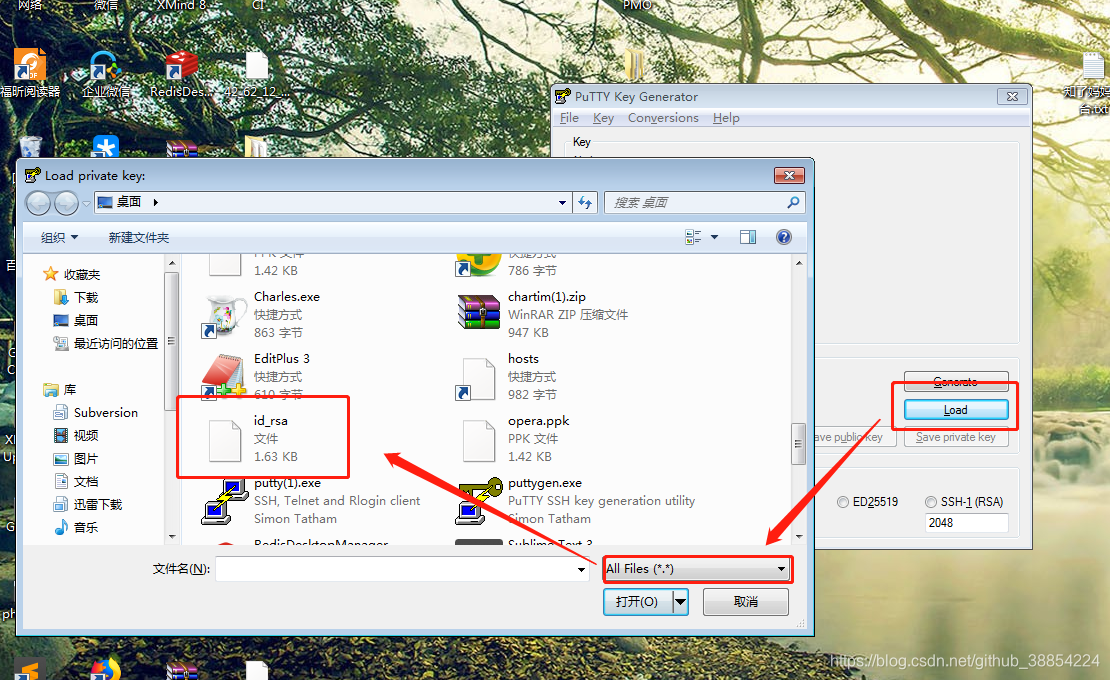
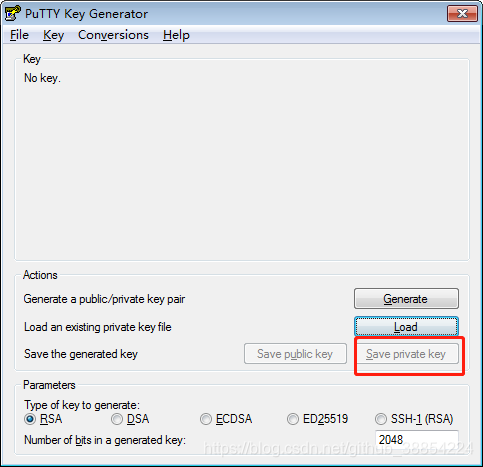
备注:如若想禁止root登陆,密码登录。。修改上面对应的参数。





















 1682
1682











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








