欢迎点赞、关注、分享,后期将会有更多的工作小工具分享给大家,嘻嘻
密码,是守护我们数字世界的钥匙。一个强大、复杂的密码,能够有效地抵御黑客攻击和信息泄露的风险。但在日常使用中,许多人因为方便记忆而选择了简单易猜的“弱密码”,这无疑给自己的信息安全埋下了隐患。今天,我们就来使用john来探测下主机上面的弱密码用户,让弱密码无处可逃!
版本环境
| 系统版本 | 备注 |
| uos 1050 桌面专业版 (需要root权限) | 来测试所有用户是否存在弱密码,不是修改密码 |
经测试,只要是系统架构匹配,部分桌面还是服务器都可以使用
效果展示:

小编测试完成后,会自动释放该主机,工作中千万不要学习小编的123456。
弱密码情报站
弱密码通常指的是那些容易被猜测或破解的密码,比如连续的数字(如"123456")、重复的字符(如"aaaaaa")、常见的组合(如"password")等。这些密码对于黑客来说,几乎是不设防的。
来看看你的系统里面有几个弱密码用户
思路
-
安装部署john
-
创建测试账号
-
进行弱密码探测
-
进行验证
john是一个专门的密码爆破工具,当然既然他能爆破密码,那他是不是也可以帮我们测试密码呢?是的,我们可以给john提供弱密码口令本,也可以使用john自己本身的暴力破解,对于弱密码来说,john是可以轻轻松松拿捏。
开搞
一、安装john软件包
1、在桌面空白处,邮件,【在终端中打开】
2、下载john的源码包。
liushuai@liushuai-PC:~/Desktop$ wget https://www.openwall.com/john/k/john-1.9.0.tar.gz--2024-05-09 13:32:31-- https://www.openwall.com/john/k/john-1.9.0.tar.gz正在解析主机 www.openwall.com (www.openwall.com)... 193.110.157.242正在连接 www.openwall.com (www.openwall.com)|193.110.157.242|:443... 已连接。已发出 HTTP 请求,正在等待回应... 200 OK长度:13110145 (13M) [application/octet-stream]正在保存至: “john-1.9.0.tar.gz”john-1.9.0.tar.gz 100%[===========================================================================================>] 12.50M 404KB/s 用时 1m 57s2024-05-09 13:34:30 (110 KB/s) - 已保存 “john-1.9.0.tar.gz” [13110145/13110145])
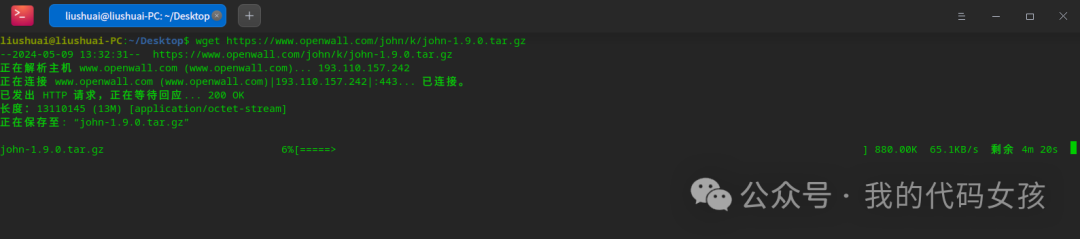
等下载成100%。
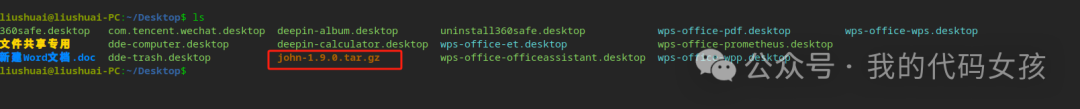
3、检查是否下载成功
liushuai@liushuai-PC:~/Desktop$ ls360safe.desktop com.tencent.wechat.desktop deepin-album.desktop uninstall360safe.desktop wps-office-pdf.desktop wps-office-wps.desktop文件共享专用 dde-computer.desktop deepin-calculator.desktop wps-office-et.desktop wps-office-prometheus.desktop新建Word文档.doc dde-trash.desktop john-1.9.0.tar.gz wps-office-officeassistant.desktop wps-office-wpp.desktop
4、创建解压后的目录。
liushuai@liushuai-PC:~/Desktop$ mkdir johnliushuai@liushuai-PC:~/Desktop$ ls360safe.desktop com.tencent.wechat.desktop deepin-album.desktop john-1.9.0.tar.gz wps-office-officeassistant.desktop wps-office-wpp.desktop文件共享专用 dde-computer.desktop deepin-calculator.desktop uninstall360safe.desktop wps-office-pdf.desktop wps-office-wps.desktop新建Word文档.doc dde-trash.desktop john wps-office-et.desktop wps-office-prometheus.desktop
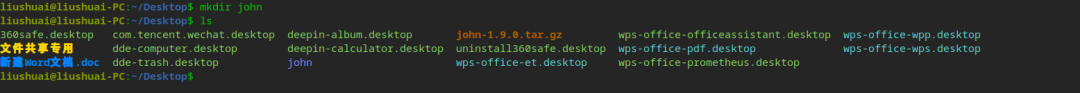
5、对源码进行解压到指定目录
liushuai@liushuai-PC:~/Desktop$ tar -xvf john-1.9.0.tar.gz -C john/john-1.9.0/doc/CHANGESjohn-1.9.0/doc/CONFIG。。省略部分。。john-1.9.0/src/x86-any.hjohn-1.9.0/src/x86-mmx.Sjohn-1.9.0/src/x86-mmx.hjohn-1.9.0/src/x86-sse.Sjohn-1.9.0/src/x86-sse.hjohn-1.9.0/src/x86.S
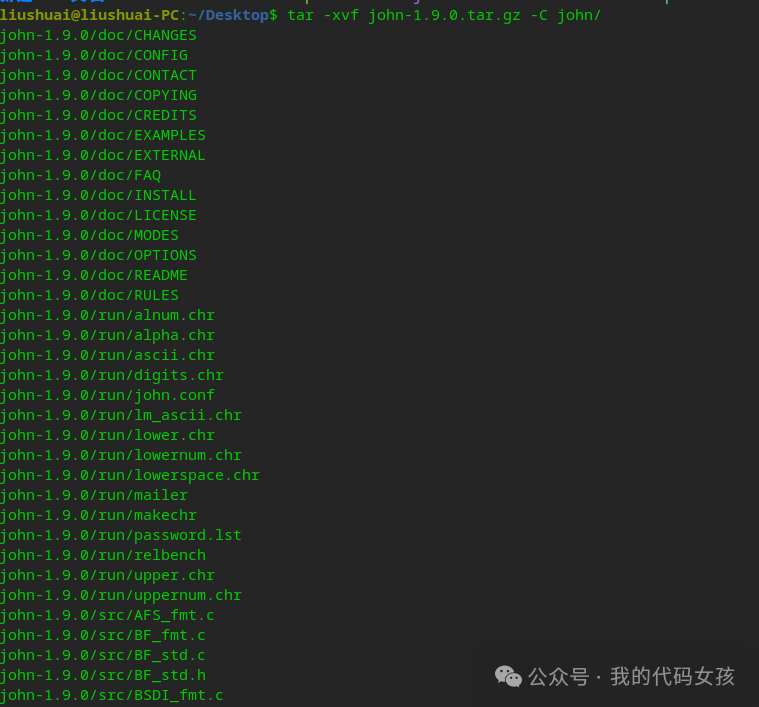
6、检查解压情况。
liushuai@liushuai-PC:~/Desktop$ cd john/liushuai@liushuai-PC:~/Desktop/john$ lsjohn-1.9.0liushuai@liushuai-PC:~/Desktop/john$ cd john-1.9.0/liushuai@liushuai-PC:~/Desktop/john/john-1.9.0$ lsdoc run src
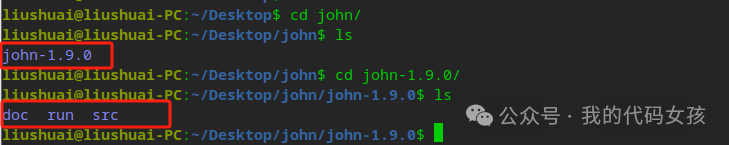
其中doc为文档目录 run为john命令所在目录 src为需要编译的目录
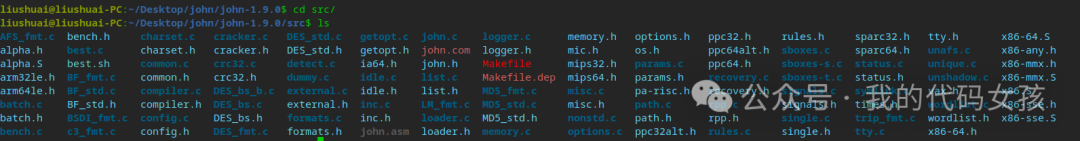
7、切换到src目录里面,开始进行编译
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0$ cd src/liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ lsAFS_fmt.c bench.h charset.c cracker.c DES_std.c getopt.c john.c logger.c memory.h options.h ppc32.h rules.h sparc32.h tty.h x86-64.Salpha.h best.c charset.h cracker.h DES_std.h getopt.h john.com logger.h mic.h os.h ppc64alt.h sboxes.c sparc64.h unafs.c x86-any.halpha.S best.sh common.c crc32.c detect.c ia64.h john.h Makefile mips32.h params.c ppc64.h sboxes-s.c status.c unique.c x86-mmx.harm32le.h BF_fmt.c common.h crc32.h dummy.c idle.c list.c Makefile.dep mips64.h params.h recovery.c sboxes-t.c status.h unshadow.c x86-mmx.Sarm64le.h BF_std.c compiler.c DES_bs_b.c external.c idle.h list.h MD5_fmt.c misc.c pa-risc.h recovery.h signals.c symlink.c vax.h x86.Sbatch.c BF_std.h compiler.h DES_bs.c external.h inc.c LM_fmt.c MD5_std.c misc.h path.c rpp.c signals.h times.h wordlist.c x86-sse.hbatch.h BSDI_fmt.c config.c DES_bs.h formats.c inc.h loader.c MD5_std.h nonstd.c path.h rpp.h single.c trip_fmt.c wordlist.h x86-sse.Sbench.c c3_fmt.c config.h DES_fmt.c formats.h john.asm loader.h memory.c options.c ppc32alt.h rules.c single.h tty.c x86-64.h
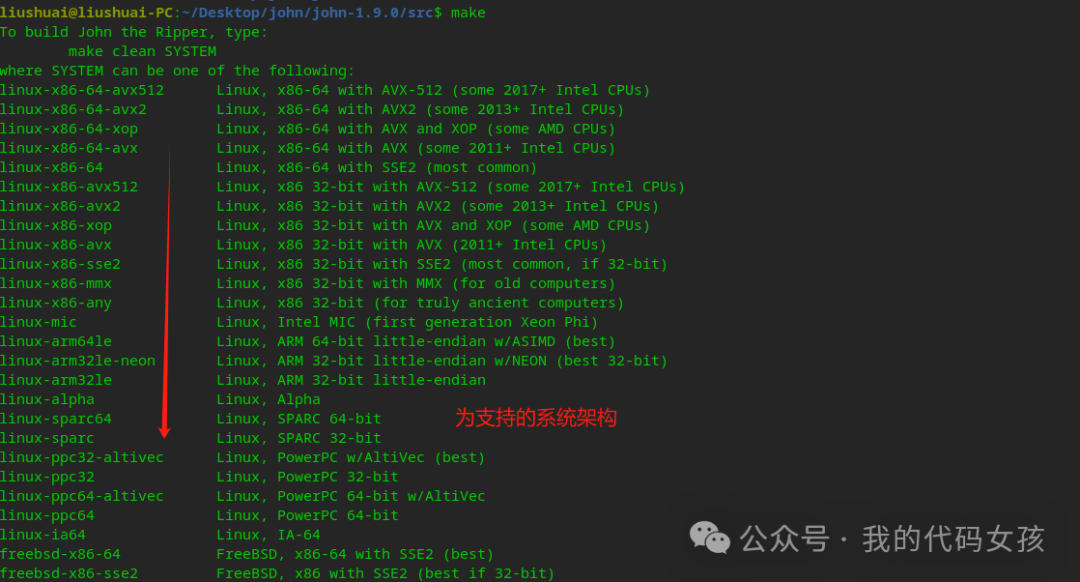
8、确认下支持的系统情况,通过“make"
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ makeTo build John the Ripper, type:make clean SYSTEMwhere SYSTEM can be one of the following:linux-x86-64-avx512 Linux, x86-64 with AVX-512 (some 2017+ Intel CPUs)linux-x86-64-avx2 Linux, x86-64 with AVX2 (some 2013+ Intel CPUs)linux-x86-64-xop Linux, x86-64 with AVX and XOP (some AMD CPUs)linux-x86-64-avx Linux, x86-64 with AVX (some 2011+ Intel CPUs)linux-x86-64 Linux, x86-64 with SSE2 (most common)linux-x86-avx512 Linux, x86 32-bit with AVX-512 (some 2017+ Intel CPUs)linux-x86-avx2 Linux, x86 32-bit with AVX2 (some 2013+ Intel CPUs)linux-x86-xop Linux, x86 32-bit with AVX and XOP (some AMD CPUs)linux-x86-avx Linux, x86 32-bit with AVX (2011+ Intel CPUs)linux-x86-sse2 Linux, x86 32-bit with SSE2 (most common, if 32-bit)linux-x86-mmx Linux, x86 32-bit with MMX (for old computers)linux-x86-any Linux, x86 32-bit (for truly ancient computers)linux-mic Linux, Intel MIC (first generation Xeon Phi)linux-arm64le Linux, ARM 64-bit little-endian w/ASIMD (best)linux-arm32le-neon Linux, ARM 32-bit little-endian w/NEON (best 32-bit)linux-arm32le Linux, ARM 32-bit little-endianlinux-alpha Linux, Alphalinux-sparc64 Linux, SPARC 64-bitlinux-sparc Linux, SPARC 32-bitlinux-ppc32-altivec Linux, PowerPC w/AltiVec (best)linux-ppc32 Linux, PowerPC 32-bitlinux-ppc64-altivec Linux, PowerPC 64-bit w/AltiVeclinux-ppc64 Linux, PowerPC 64-bitlinux-ia64 Linux, IA-64freebsd-x86-64 FreeBSD, x86-64 with SSE2 (best)freebsd-x86-sse2 FreeBSD, x86 with SSE2 (best if 32-bit)freebsd-x86-mmx FreeBSD, x86 with MMXfreebsd-x86-any FreeBSD, x86freebsd-alpha FreeBSD, Alphaopenbsd-x86-64 OpenBSD, x86-64 with SSE2 (best)openbsd-x86-sse2 OpenBSD, x86 with SSE2 (best if 32-bit)openbsd-x86-mmx OpenBSD, x86 with MMXopenbsd-x86-any OpenBSD, x86openbsd-alpha OpenBSD, Alphaopenbsd-sparc64 OpenBSD, SPARC 64-bit (best)openbsd-sparc OpenBSD, SPARC 32-bitopenbsd-ppc32 OpenBSD, PowerPC 32-bitopenbsd-ppc64 OpenBSD, PowerPC 64-bitopenbsd-pa-risc OpenBSD, PA-RISCopenbsd-vax OpenBSD, VAXnetbsd-sparc64 NetBSD, SPARC 64-bitnetbsd-vax NetBSD, VAXsolaris-sparc64-cc Solaris, SPARC V9 64-bit, cc (best)solaris-sparc64-gcc Solaris, SPARC V9 64-bit, gccsolaris-sparcv9-cc Solaris, SPARC V9 32-bit, ccsolaris-sparcv8-cc Solaris, SPARC V8 32-bit, ccsolaris-sparc-gcc Solaris, SPARC 32-bit, gccsolaris-x86-64-cc Solaris, x86-64 with SSE2, cc (best)solaris-x86-64-gcc Solaris, x86-64 with SSE2, gccsolaris-x86-sse2-cc Solaris 9 4/04+, x86 with SSE2, ccsolaris-x86-sse2-gcc Solaris 9 4/04+, x86 with SSE2, gccsolaris-x86-mmx-cc Solaris, x86 with MMX, ccsolaris-x86-mmx-gcc Solaris, x86 with MMX, gccsolaris-x86-any-cc Solaris, x86, ccsolaris-x86-any-gcc Solaris, x86, gcctru64-alpha Tru64 (Digital UNIX, OSF/1), Alphaaix-ppc32 AIX, PowerPC 32-bitmacosx-x86-64 Mac OS X 10.5+, Xcode 3.0+, x86-64 with SSE2 (best)macosx-x86-sse2 Mac OS X, x86 with SSE2macosx-ppc32-altivec Mac OS X, PowerPC w/AltiVec (best)macosx-ppc32 Mac OS X, PowerPC 32-bitmacosx-ppc64 Mac OS X 10.4+, PowerPC 64-bitmacosx-universal Mac OS X, Universal Binary (x86 + x86-64 + PPC)hpux-pa-risc-gcc HP-UX, PA-RISC, gcchpux-pa-risc-cc HP-UX, PA-RISC, ANSI ccirix-mips64-r10k IRIX, MIPS 64-bit (R10K) (best)irix-mips64 IRIX, MIPS 64-bitirix-mips32 IRIX, MIPS 32-bitdos-djgpp-x86-mmx DOS, DJGPP, x86 with MMXdos-djgpp-x86-any DOS, DJGPP, x86win32-cygwin-x86-sse2 Win32, Cygwin, x86 with SSE2 (best)win32-cygwin-x86-mmx Win32, Cygwin, x86 with MMXwin32-cygwin-x86-any Win32, Cygwin, x86beos-x86-sse2 BeOS, x86 with SSE2 (best)beos-x86-mmx BeOS, x86 with MMXbeos-x86-any BeOS, x86generic Any other Unix-like system with gcc
9、确认自己的系统架构
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ lscpuArchitecture: x86_64CPU op-mode(s): 32-bit, 64-bitByte Order: Little Endian。。省略部分。。NUMA node0 CPU(s): 0-3Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ss ht syscall nx pdpe1gb rdtscp lm constant_tsc arch_perfmon nopl xtopology tsc_reliable nonstop_tsc cpuid pni pclmulqdq ssse3 fma cx16 pcid sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand hypervisor lahf_lm abm 3dnowprefetch cpuid_fault invpcid_single pti ssbd ibrs ibpb stibp fsgsbase tsc_adjust bmi1 avx2 smep bmi2 invpcid rdseed adx smap clflushopt xsaveopt xsavec xgetbv1 xsaves arat md_clear flush_l1d arch_capabilities
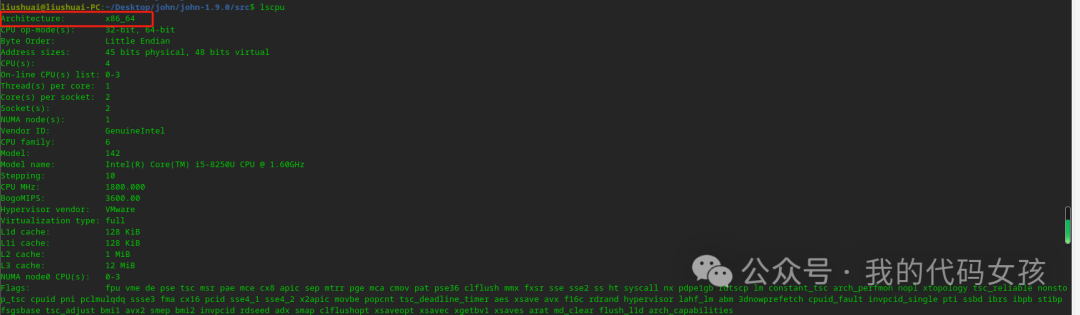
从返回结果来看,我的系统是X86_64。
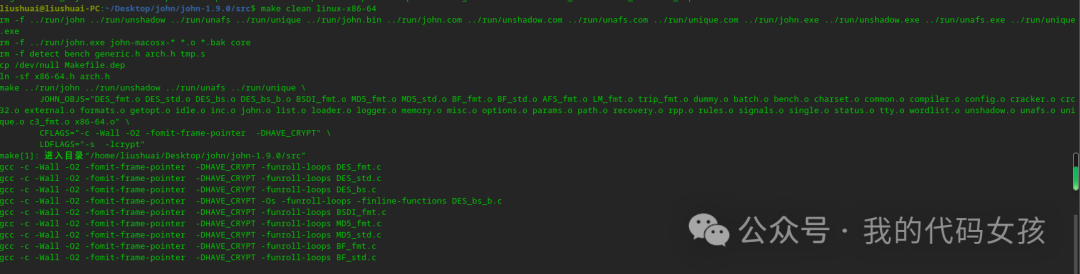
10、进行编译
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ make clean linux-x86-64rm -f ../run/john ../run/unshadow ../run/unafs ../run/unique ../run/john.bin ../run/john.com ../run/unshadow.com ../run/unafs.com ../run/unique.com ../run/john.exe ../run/unshadow.exe ../run/unafs.exe ../run/unique.exerm -f ../run/john.exe john-macosx-* *.o *.bak corerm -f detect bench generic.h arch.h tmp.scp /dev/null Makefile.depln -sf x86-64.h arch.hmake ../run/john ../run/unshadow ../run/unafs ../run/unique \JOHN_OBJS="DES_fmt.o DES_std.o DES_bs.o DES_bs_b.o BSDI_fmt.o MD5_fmt.o MD5_std.o BF_fmt.o BF_std.o AFS_fmt.o LM_fmt.o trip_fmt.o dummy.o batch.o bench.o charset.o common.o compiler.o config.o cracker.o crc32.o external.o formats.o getopt.o idle.o inc.o john.o list.o loader.o logger.o memory.o misc.o options.o params.o path.o recovery.o rpp.o rules.o signals.o single.o status.o tty.o wordlist.o unshadow.o unafs.o unique.o c3_fmt.o x86-64.o" \CFLAGS="-c -Wall -O2 -fomit-frame-pointer -DHAVE_CRYPT" \LDFLAGS="-s -lcrypt"make[1]: 进入目录“/home/liushuai/Desktop/john/john-1.9.0/src”gcc -c -Wall -O2 -fomit-frame-pointer -DHAVE_CRYPT -funroll-loops DES_fmt.c。。省略部分。。gcc DES_fmt.o DES_std.o DES_bs.o DES_bs_b.o BSDI_fmt.o MD5_fmt.o MD5_std.o BF_fmt.o BF_std.o AFS_fmt.o LM_fmt.o trip_fmt.o dummy.o batch.o bench.o charset.o common.o compiler.o config.o cracker.o crc32.o external.o formats.o getopt.o idle.o inc.o john.o list.o loader.o logger.o memory.o misc.o options.o params.o path.o recovery.o rpp.o rules.o signals.o single.o status.o tty.o wordlist.o unshadow.o unafs.o unique.o c3_fmt.o x86-64.o -s -lcrypt -o ../run/johnrm -f ../run/unshadowln -s john ../run/unshadowrm -f ../run/unafsln -s john ../run/unafsrm -f ../run/uniqueln -s john ../run/uniquemake[1]: 离开目录“/home/liushuai/Desktop/john/john-1.9.0/src”
11、确认下上面的命令是否执行成功
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ echo $?0
![]()
结果为0,说明执行成功,非0则失败。
12、切换目录到run里面,确认john命令是否正常
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/src$ cd ../run/liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/run$ ./johnJohn the Ripper password cracker, version 1.9.0Copyright (c) 1996-2019 by Solar DesignerHomepage: http://www.openwall.com/john/Usage: john [OPTIONS] [PASSWORD-FILES]--single "single crack" mode--wordlist=FILE --stdin wordlist mode, read words from FILE or stdin--rules enable word mangling rules for wordlist mode--incremental[=MODE] "incremental" mode [using section MODE]--external=MODE external mode or word filter--stdout[=LENGTH] just output candidate passwords [cut at LENGTH]--restore[=NAME] restore an interrupted session [called NAME]--session=NAME give a new session the NAME--status[=NAME] print status of a session [called NAME]--make-charset=FILE make a charset, FILE will be overwritten--show show cracked passwords--test[=TIME] run tests and benchmarks for TIME seconds each--users=[-]LOGIN|UID[,..] [do not] load this (these) user(s) only--groups=[-]GID[,..] load users [not] of this (these) group(s) only--shells=[-]SHELL[,..] load users with[out] this (these) shell(s) only--salts=[-]N load salts with[out] at least N passwords only--save-memory=LEVEL enable memory saving, at LEVEL 1..3--node=MIN[-MAX]/TOTAL this node's number range out of TOTAL count--fork=N fork N processes--format=NAME force hash type NAME: descrypt/bsdicrypt/md5crypt/bcrypt/LM/AFS/tripcode/dummy/crypt
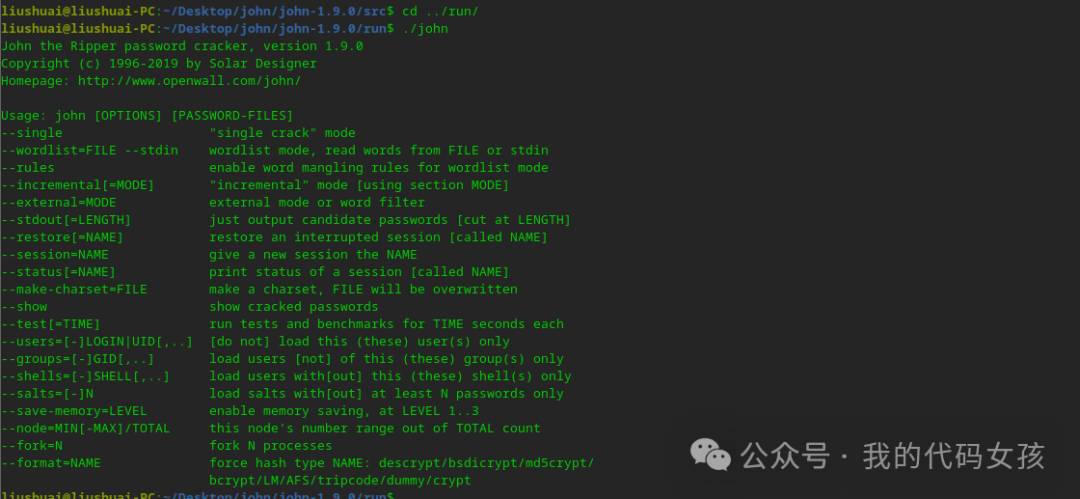
出现以上情况则代表命令是正常的,可以正常使用。
二、创建测试用户
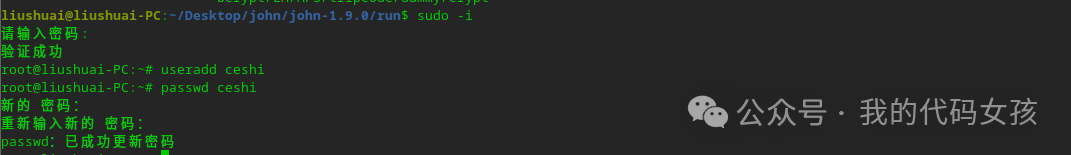
1、切换到root用户,创建一个弱口令密码的用户
liushuai@liushuai-PC:~/Desktop/john/john-1.9.0/run$ sudo -i请输入密码:验证成功root@liushuai-PC:~# useradd ceshiroot@liushuai-PC:~# passwd ceshi新的 密码:重新输入新的 密码:passwd:已成功更新密码
2、切换到john所在的目录
root@liushuai-PC:~# cd /home/liushuai/Desktop/john/john-1.9.0/runroot@liushuai-PC:/home/liushuai/Desktop/john/john-1.9.0/run# lsalnum.chr alpha.chr ascii.chr digits.chr john john.conf lm_ascii.chr lower.chr lowernum.chr lowerspace.chr mailer makechr password.lst relbench unafs unique unshadow upper.chr uppernum.chr
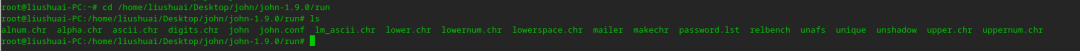
cd /home/liushuai/Desktop/john/john-1.9.0/run ,如果你的这步执行报错,原因是你没有这个路径,请将路径中的 liushuai 换成安装john所用的 用户名
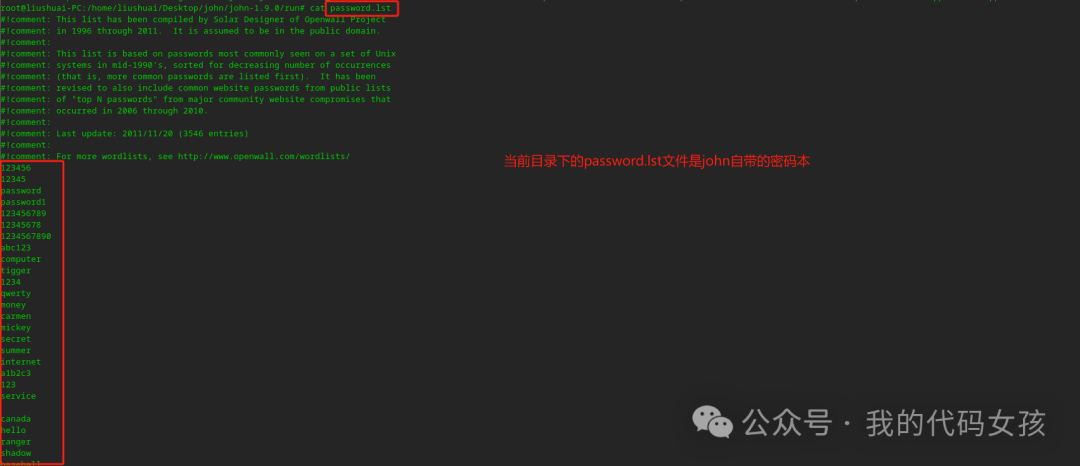
3、查看john自带的密码本
root@liushuai-PC:/home/liushuai/Desktop/john/john-1.9.0/run# cat password.lst#!comment: This list has been compiled by Solar Designer of Openwall Project#!comment: in 1996 through 2011. It is assumed to be in the public domain.#!comment:#!comment: This list is based on passwords most commonly seen on a set of Unix#!comment: systems in mid-1990's, sorted for decreasing number of occurrences#!comment: (that is, more common passwords are listed first). It has been#!comment: revised to also include common website passwords from public lists#!comment: of "top N passwords" from major community website compromises that#!comment: occurred in 2006 through 2010.#!comment:#!comment: Last update: 2011/11/20 (3546 entries)#!comment:#!comment: For more wordlists, see http://www.openwall.com/wordlists/12345612345passwordpassword1123456789123456781234567890以下进行省略
三、开始测试是否存在弱密码
1、开始测试
root@liushuai-PC:/home/liushuai/Desktop/john/john-1.9.0/run# ./john -w:password.lst /etc/shadowLoaded 4 password hashes with 4 different salts (crypt, generic crypt(3) [?/64])Press 'q' or Ctrl-C to abort, almost any other key for status123456 (liushuai)123456 (root)123456 (ceshi)123456 (test)4g 0:00:00:00 100% 4.347g/s 104.3p/s 417.3c/s 417.3C/s 123456..pepperUse the "--show" option to display all of the cracked passwords reliablySession completed
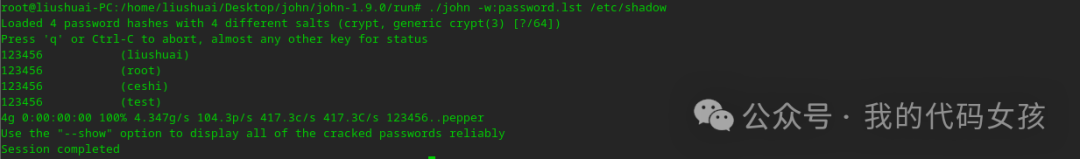
本机上的弱口令用户,无处可逃了,统统拿下
结束语
加油吧!你一定会感谢现在努力的自己
如果你是linux,unix(含aix小机)的其他系统,还请查阅以下技术文档
linux密码破解[离线]--john 探测(爆破)弱口令(包含linux机器,aix小机)/linux上的shadow文件破解,亲测可用_john jumbo-CSDN博客
号外
小编最近在弄一个微信公众号,当前没有几篇文章,但是小编会努力的,博客和公众号同步更新,如果有需要的,还请关注下小编,谢谢

























 715
715

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










