一HPA 控制器简介与实现
1.1 HPA介绍https://github.com/kubernetes-sigs/metrics-server
简介


计算公式当前cpu利用率除以阈值,在跟当前pod数量进行比较,看是否增加
比如:pod1和pod2 两个cpu利用率加起来 90+90=180 然后除以 80=2.25 (阈值)得到的值再跟现有的pod数量去对比,现有是2个,2,25向上取值为3,所以pod增加1个。1.2 部署 metrics-server
hap依赖于metrics-server
里面的images的地址需要根据自己的情况去更改
[root@k8s-master1 hpa]# cat metrics-server-v0.6.1.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: metrics-server
rbac.authorization.k8s.io/aggregate-to-admin: "true"
rbac.authorization.k8s.io/aggregate-to-edit: "true"
rbac.authorization.k8s.io/aggregate-to-view: "true"
name: system:aggregated-metrics-reader
rules:
- apiGroups:
- metrics.k8s.io
resources:
- pods
- nodes
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: metrics-server
name: system:metrics-server
rules:
- apiGroups:
- ""
resources:
- nodes/metrics
verbs:
- get
- apiGroups:
- ""
resources:
- pods
- nodes
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: metrics-server
name: metrics-server-auth-reader
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: extension-apiserver-authentication-reader
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: metrics-server
name: metrics-server:system:auth-delegator
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:auth-delegator
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: metrics-server
name: system:metrics-server
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:metrics-server
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: v1
kind: Service
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
spec:
ports:
- name: https
port: 443
protocol: TCP
targetPort: https
selector:
k8s-app: metrics-server
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
spec:
selector:
matchLabels:
k8s-app: metrics-server
strategy:
rollingUpdate:
maxUnavailable: 0
template:
metadata:
labels:
k8s-app: metrics-server
spec:
containers:
- args:
- --cert-dir=/tmp
- --secure-port=4443
- --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname
- --kubelet-use-node-status-port
- --metric-resolution=15s
image: harbor.magedu.com/magedu/metrics:v0.6.1
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 3
httpGet:
path: /livez
port: https
scheme: HTTPS
periodSeconds: 10
name: metrics-server
ports:
- containerPort: 4443
name: https
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /readyz
port: https
scheme: HTTPS
initialDelaySeconds: 20
periodSeconds: 10
resources:
requests:
cpu: 100m
memory: 200Mi
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 1000
volumeMounts:
- mountPath: /tmp
name: tmp-dir
nodeSelector:
kubernetes.io/os: linux
priorityClassName: system-cluster-critical
serviceAccountName: metrics-server
volumes:
- emptyDir: {}
name: tmp-dir
---
apiVersion: apiregistration.k8s.io/v1
kind: APIService
metadata:
labels:
k8s-app: metrics-server
name: v1beta1.metrics.k8s.io
spec:
group: metrics.k8s.io
groupPriorityMinimum: 100
insecureSkipTLSVerify: true
service:
name: metrics-server
namespace: kube-system
version: v1beta1
versionPriority: 100创建完之后,去查看node和pod的资源
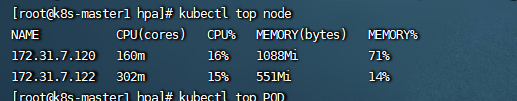
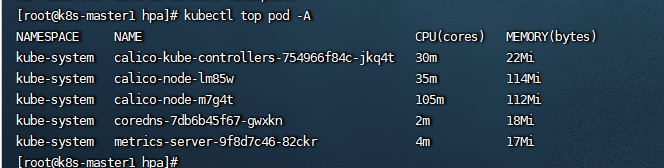
1.3 设置hpa控制器
[root@k8s-master1 hpa]# cat hpa.yaml
#apiVersion: autoscaling/v2beta1
apiVersion: autoscaling/v1
kind: HorizontalPodAutoscaler
metadata:
namespace: magedu
name: magedu-tomcat-app1-podautoscaler
labels:
app: magedu-tomcat-app1
version: v2beta1
spec:
scaleTargetRef:
apiVersion: apps/v1
#apiVersion: extensions/v1beta1
kind: Deployment
name: magedu-tomcat-app1-deployment
minReplicas: 3
maxReplicas: 10
targetCPUUtilizationPercentage: 60查看hpa
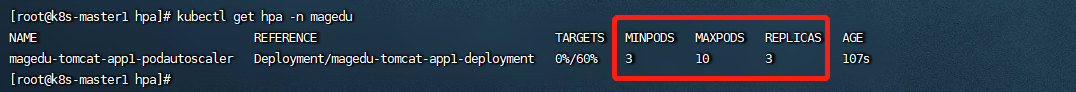
额外命令
kubectl get horizontalpodautoscalers.autoscaling -n magedu #查看hpa的设置
kubectl describe horizontalpodautoscalers.autoscaling magedu-tomcat-app1-podautoscaler -n magedu #查看pod的创建过程1.4 部署一个测试服务
注意:pod必须设置资源限制,否则hpa收集不到利用率
[root@k8s-master1 hpa]# cat tomcat-app1.yaml
kind: Deployment
#apiVersion: extensions/v1beta1
apiVersion: apps/v1
metadata:
labels:
app: magedu-tomcat-app1-deployment-label
name: magedu-tomcat-app1-deployment
namespace: magedu
spec:
replicas: 2
selector:
matchLabels:
app: magedu-tomcat-app1-selector
template:
metadata:
labels:
app: magedu-tomcat-app1-selector
spec:
containers:
- name: magedu-tomcat-app1-container
#image: harbor.magedu.local/magedu/tomcat-app1:v7
image: tomcat:7.0.93-alpine
#image: lorel/docker-stress-ng
#args: ["--vm", "2", "--vm-bytes", "256M"]
##command: ["/apps/tomcat/bin/run_tomcat.sh"]
imagePullPolicy: IfNotPresent
##imagePullPolicy: Always
ports:
- containerPort: 8080
protocol: TCP
name: http
env:
- name: "password"
value: "123456"
- name: "age"
value: "18"
resources:
limits:
cpu: 1
memory: "512Mi"
requests:
cpu: 500m
memory: "512Mi"
---
kind: Service
apiVersion: v1
metadata:
labels:
app: magedu-tomcat-app1-service-label
name: magedu-tomcat-app1-service
namespace: magedu
spec:
type: NodePort
ports:
- name: http
port: 80
protocol: TCP
targetPort: 8080
#nodePort: 40003
selector:
app: magedu-tomcat-app1-selector这个yaml文件里定义的是2个pod,当创建完之后会默认变成3个,是因为hpa里设置了最小是3个

二RBAC简介及账户授权
鉴权概述 | Kubernetes 鉴权类型
node节点认证 webhook ABAC RBAC 四种类型
这里主要介绍rbac
2.1 rbac介绍
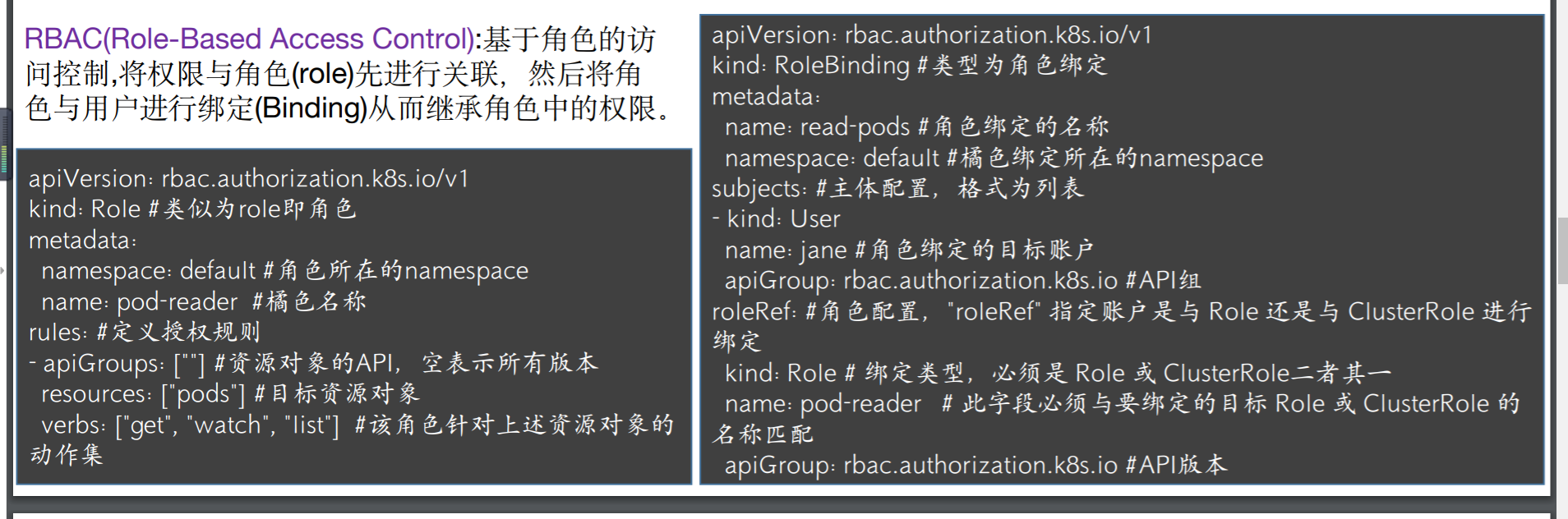

2.2 第一种方式直接用token 去登录dashboard
2.2.1在指定namespace创建账户:
# kubectl create serviceaccount magedu -n magedu
serviceaccount/magedu created
kubectl get sa -n magedu
kubectl delete sa magedu-user -n magedu #删除
[root@k8s-master1 shili]# kubectl describe sa magedu -n magedu
Name: magedu
Namespace: magedu
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: magedu-token-czcrb
Tokens: magedu-token-czcrb
Events: <none>2.2.2 创建role规则:
# kubectl apply -f magedu-role.yaml
role.rbac.authorization.k8s.io/magedu-role created
# cat magedu-role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: magedu
name: magedu-role
rules:
- apiGroups: ["*"]
resources: ["pods","pods/exec"]
verbs: ["*"]
##RO-Role
#verbs: ["get", "watch", "list"]
- apiGroups: ["extensions", "apps/v1"]
resources: ["deployments"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
##RO-Role
#verbs: ["get", "watch", "list"]
# 查看role
[root@k8s-master1 RBAC-yaml-case]# kubectl get role -n magedu
NAME CREATED AT
magedu-role 2022-05-27T14:17:38Z
# 查看role有哪些权限
kubectl describe role magedu-role -n magedu2.2.3 将规则与账户进行绑定
# kubectl apply -f magedu-role-bind.yaml
rolebinding.rbac.authorization.k8s.io/role-bind-magedu created
# cat magedu-role-bind.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: role-bind-magedu
namespace: magedu
subjects:
- kind: ServiceAccount
name: magedu
namespace: magedu
roleRef:
kind: Role
name: magedu-role
apiGroup: rbac.authorization.k8s.io2.2.4 查看绑定信息
#######################
kubectl get rolebindings.rbac.authorization.k8s.io -n magedu
NAME ROLE AGE
role-bind-magedu Role/magedu-role 75m
kubectl describe rolebindings.rbac.authorization.k8s.io role-bind-magedu -n magedu
Name: role-bind-magedu
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: magedu-role
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount dev magedu2.2.5 获取token 查看secret登录
1.4:获取token名称:
# kubectl get secret -n magedu | grep magedu
magedu-token-8d897 kubernetes.io/service-account-token 3 5m45s
1.5 查看secret内容
kubectl describe secrets magedu-token-8d897 -n magedu
也可以这样
# kubectl get secret magedu-token-8d897 -o jsonpath={.data.token} -n magedu |base64 -d
1.6:登录dashboard测试:
只能查看magedu的命名空间里的内容访问dashboard,把查看到的token粘贴到里面进行登录
2.3 基于kube-config文件登录:
基于2.2的一切操作,继续执行下列操作
2.1:创建csr文件:
# cat magedu-csr.json
{
"CN": "China",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
2.2:签发证书:
# ln -sv /etc/kubeasz/bin/cfssl* /usr/bin/
cfssl gencert -ca=/etc/kubernetes/ssl/ca.pem -ca-key=/etc/kubernetes/ssl/ca-key.pem -config=/etc/kubeasz/clusters/k8s-cluster01/ssl/ca-config.json -profile=kubernetes magedu-user-csr.json | cfssljson -bare magedu
# ls magedu*
magedu-csr.json magedu-key.pem magedu-role-bind.yaml magedu-role.yaml magedu.csr magedu.pem
2.3:生成普通用户kubeconfig文件:
# cluster1 集群名字
kubectl config set-cluster cluster1 --certificate-authority=/etc/kubernetes/ssl/ca.pem --embed-certs=true --server=https://172.31.7.120:6443 --kubeconfig=magedu.kubeconfig
#--embed-certs=true #为嵌入证书信息
2.4:设置客户端认证参数:
# cp *.pem /etc/kubernetes/ssl/
kubectl config set-credentials magedu \
--client-certificate=/etc/kubernetes/ssl/magedu.pem \
--client-key=/etc/kubernetes/ssl/magedu-key.pem \
--embed-certs=true \
--kubeconfig=magedu.kubeconfig
2.5:设置上下文参数(多集群使用上下文区分)
https://kubernetes.io/zh/docs/concepts/configuration/organize-cluster-access-kubeconfig/
# kubectl config set-context cluster1 \
--cluster=cluster1 \
--user=magedu \
--namespace=magedu \
--kubeconfig=magedu.kubeconfig
2.5: 设置默认上下文
# kubectl config use-context cluster1 --kubeconfig=magedu.kubeconfig
2.7:获取token:
# kubectl get secrets -n magedu | grep magedu
# kubectl describe secrets magedu-token-8d897 -n magedu
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlYwMDNHdWJwTmtoaTJUMFRPTVlwV3RiVWFWczJYRHJCNkFkMGRtQWFqRTgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJtYWdlZHUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoibWFnZWR1LXRva2VuLThkODk3Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6Im1hZ2VkdSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjBlZmNiNGI0LWM3YTUtNGJkZS1iZjk4LTFiNTkwNThjOTFjNiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDptYWdlZHU6bWFnZWR1In0.SJHLgshKcGtIf-ycivn_4SWVRdWw4SuWymBVaA8YJXHPd5PYnwERVNtfUPX88nv-wXkCuZY7fIjGYkoYj6AJEhSPoG15fcmUPaojYeyjkQYghan3CBsZR8C12buSB6t5zCCt22GdG_ScZymxLU7n3Z0PhOzTLzgpXRs1Poqz4DOYylqZyLmW_BPgoNhtQYKlBH6OFzDe8v3JytnaaJUObVZCRxtI6x4iKLt2Evhs8XKfczqqesgoo61qTqtbU4jzlXuHeW7cUMhWoipUc-BkEdV6OtKWOetecxu5uB-44eTRHa1FBjnRMv9SEGj0hxTJCQ08ZNlP0Kc01JZlKXBGdQ
2.8:将token写入用户kube-config文件:
编辑magedu.kubecofig
在最下面加入 token: xxxx
3.9:dashboard登录测试:
https://172.31.7.111:30002/#/login如图所示






















 249
249











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








