一、前文
二、打开日志
2.1 修改配置
vim /etc/firewalld/firewalld.conf
LogDenied=all
- 重启firewalld
systemctl restart firewalld
systemctl status firewalld
2.2 测试验证
- 切换个WiFi,查询本机IP地址
- 使用DataGrip查询下MySQL
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# dmesg | grep -i reject
[47097724.295920] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=173.82.163.104 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=105 ID=55127 DF PROTO=TCP SPT=24717 DPT=3306 WINDOW=29200 RES=0x00 SYN URGP=0
[47097724.305959] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=173.82.163.104 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=91 ID=27553 DF PROTO=TCP SPT=56131 DPT=3389 WINDOW=64240 RES=0x00 SYN URGP=0
[47097734.793855] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=95 ID=15043 DF PROTO=TCP SPT=14917 DPT=3389 WINDOW=64240 RES=0x00 SYN URGP=0
[47097734.802632] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=93 ID=35103 DF PROTO=TCP SPT=4657 DPT=3306 WINDOW=29200 RES=0x00 SYN URGP=0
[47097735.945460] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=87 ID=65303 DF PROTO=TCP SPT=27778 DPT=3306 WINDOW=29200 RES=0x00 SYN URGP=0
[47097735.945936] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=91 ID=4503 DF PROTO=TCP SPT=33155 DPT=3389 WINDOW=29200 RES=0x00 SYN URGP=0
[47097738.009845] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=87 ID=65303 DF PROTO=TCP SPT=27778 DPT=3306 WINDOW=29200 RES=0x00 SYN URGP=0
[47097738.010305] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=45.77.32.235 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=91 ID=4503 DF PROTO=TCP SPT=33155 DPT=3389 WINDOW=29200 RES=0x00 SYN URGP=0
[47097960.728848] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=27.149.45.24 DST=172.20.125.57 LEN=52 TOS=0x14 PREC=0x00 TTL=114 ID=47356 DF PROTO=TCP SPT=9096 DPT=3306 WINDOW=64240 RES=0x00 SYN URGP=0
[47097961.752929] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=27.149.45.24 DST=172.20.125.57 LEN=52 TOS=0x14 PREC=0x00 TTL=114 ID=47357 DF PROTO=TCP SPT=9096 DPT=3306 WINDOW=64240 RES=0x00 SYN URGP=0
[47097963.768618] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=27.149.45.24 DST=172.20.125.57 LEN=52 TOS=0x14 PREC=0x00 TTL=114 ID=47358 DF PROTO=TCP SPT=9096 DPT=3306 WINDOW=64240 RES=0x00 SYN URGP=0
[47097965.402544] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=65.108.245.43 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=112 ID=31227 DF PROTO=TCP SPT=569 DPT=3389 WINDOW=64240 RES=0x00 SYN URGP=0
[47097965.626134] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=65.108.245.43 DST=172.20.125.57 LEN=64 TOS=0x14 PREC=0x00 TTL=112 ID=31227 DF PROTO=TCP SPT=569 DPT=3389 WINDOW=64240 RES=0x00 SYN URGP=0
[47097967.768565] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=27.149.45.24 DST=172.20.125.57 LEN=52 TOS=0x14 PREC=0x00 TTL=114 ID=47366 DF PROTO=TCP SPT=9096 DPT=3306 WINDOW=64240 RES=0x00 SYN URGP=0
[47097975.768955] FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=27.149.45.24 DST=172.20.125.57 LEN=52 TOS=0x14 PREC=0x00 TTL=114 ID=47367 DF PROTO=TCP SPT=9099 DPT=3306 WINDOW=64240 RES=0x00 SYN URGP=0
2.3 日志保存到本地
- 创建firewalld的运行时日志文件
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# vim /etc/rsyslog.d/firewalld.conf
kern.* /var/log/firewalld.log
- 修改日志管理工具
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# vim /etc/logrotate.d/syslog
/var/log/cron
/var/log/maillog
/var/log/messages
/var/log/secure
/var/log/firewalld.log
/var/log/spooler
{
missingok
sharedscripts
postrotate
/usr/bin/systemctl kill -s HUP rsyslog.service >/dev/null 2>&1 || true
endscript
}
- 重启日志服务
- 打开firewalld.log日志
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# systemctl restart rsyslog.service
[root@iZ2ze30dygwd6yh7gu6lskZ ~]# more /var/log/firewalld.log
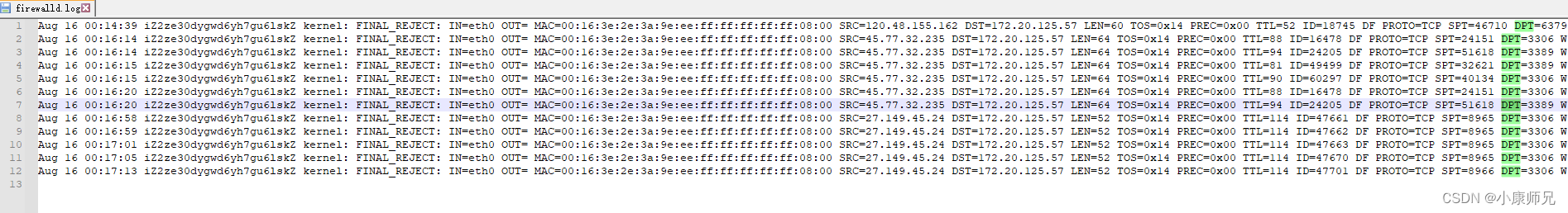
Aug 16 00:14:39 iZ2ze30dygwd6yh7gu6lskZ kernel: FINAL_REJECT: IN=eth0 OUT= MAC=00:16:3e:2e:3a:9e:ee:ff:ff:ff:ff:ff:08:00 SRC=120.48.155.162 DST=172.20.125.57 LEN=60 TOS=0x14 PREC=0x00 TTL=52 ID=18745 DF PROTO=TCP SPT=46710 DPT=6379 WINDOW=29200 RES=0x00 SYN URGP=0
三、允许IP网段
- 早上才查询了办公室的IP是:
117.30.82.11 - 下午一测就发现访问不了服务器的数据库了,再查IP,就发现IP变了
- 所以,我们允许IP访问的时候,不能只允许单个IP,应该允许某个IP网段
- IP网段知识点学习请查阅:IP网段知识点学习(IP地址/数字 IP地址段 IP网段 Linux子网掩码 子网/掩码位 IP段起始 IP段结束)
- 操作如下
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports: 80/tcp 8080/tcp 443/tcp 8443/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="59.61.25.232" port port="22" protocol="tcp" accept
rule family="ipv4" source address="59.61.25.232" port port="3306" protocol="tcp" accept
rule family="ipv4" source address="59.61.25.232" port port="6379" protocol="tcp" accept
rule family="ipv4" source address="117.30.82.11" port port="22" protocol="tcp" accept
rule family="ipv4" source address="117.30.82.11" port port="3306" protocol="tcp" accept
rule family="ipv4" source address="117.30.82.11" port port="6379" protocol="tcp" accept
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --remove-rich-rule='rule family="ipv4" source address="117.30.82.11" port port="6379" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --remove-rich-rule='rule family="ipv4" source address="117.30.82.11" port port="22" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --remove-rich-rule='rule family="ipv4" source address="117.30.82.11" port port="3306" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="117.30.82.0/24" port port="3306" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="117.30.82.0/24" port port="22" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="117.30.82.0/24" port port="6379" protocol="tcp" accept'
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --reload
success
[root@iZ2ze30dygwd6yh7gu6lskZ log]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports: 80/tcp 8080/tcp 443/tcp 8443/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="117.30.82.0/24" port port="3306" protocol="tcp" accept
rule family="ipv4" source address="117.30.82.0/24" port port="22" protocol="tcp" accept
rule family="ipv4" source address="117.30.82.0/24" port port="6379" protocol="tcp" accept
四、关闭ssh
- 慎用!慎用!慎用!重要的事情说三遍!
- firewalld防火墙默认开启ssh服务,而如果我们需要ssh限制特定ip才能使用
- 那么就需要关闭ssh service
觉得好,就一键三连呗(点赞+收藏+关注)























 1437
1437











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










