Description:
In this article, I am going to explain about how to set or grant user Logon As A Service permission/ privilegeusing Local Security Policy, VBScript, Powershell, C# and Command Line tool.Summary:
- Set Logon As A Service right to user using Local Security Policy
- Grant User Logon As A Service privilege via Powershell
- Set User Logon As A Service permission using C#
- Set User Logon As A Service right via Command Line
- Grant Logon As A Service privilege to user via VBScript
Set Logon As A Service right to user using Local Security Policy
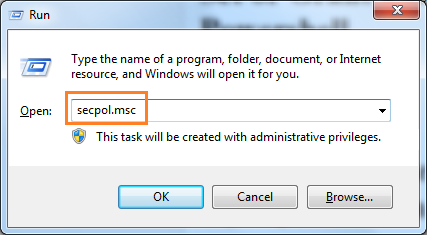
Follow the below steps to set Log on As Service right via Local Security Policy1. Open the Run window by pressing ' Windows' + ' R' keys.
2. Type the command secpol.msc in the text box and click OK.
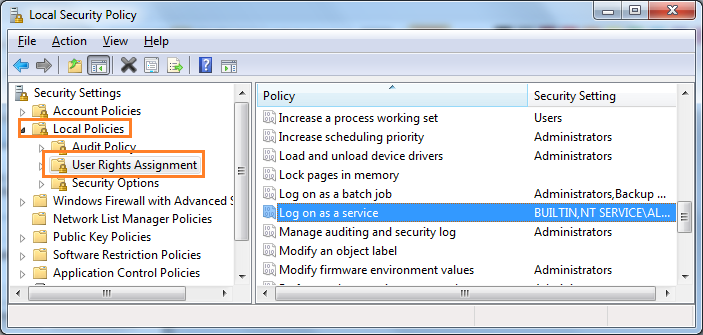
3. Now the Local Security Policy window will be open, in that window navigate to the node User Rights Assignment ( Security Settings -> Local Polices ->User Rights Assignment). In right side pane, search and select the policy Log on as a service.
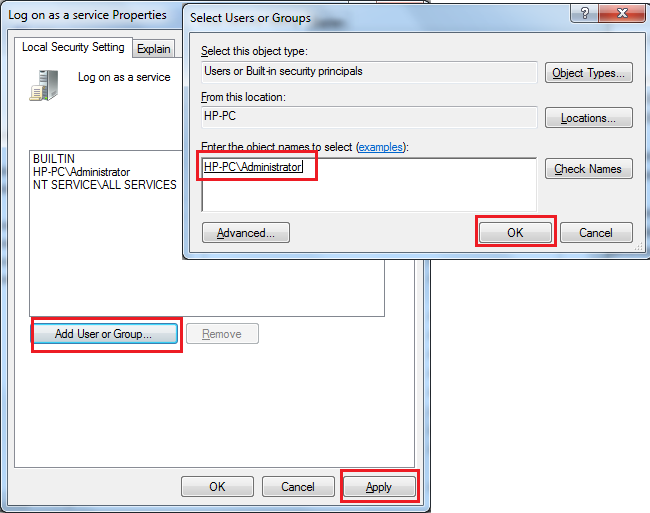
4. Double-click on the policy Log on as a service, in the opened windows click the button Add User or Group,select the user which you want to set logon as a service right and click OK, and click Apply button to finish.
Set or Grant User Logon As A Service right via Powershell
We can set the Logon As A Service right to user in Powershell by importing the third party DLL ( Carbon ). Before you run the below script you need to the download latest Carbon files from here Download Carbon DLL.Steps to follow to set Logon As A Service right via Powershell :
1. Download latest Carbon files from here Download Carbon DLL.
2. If you have downloaded the files, extract the zip file and you could see the Carbon DLL inside bin folder (In my case: C:\Users\Administrator\Downloads \Carbon-1.5.1\Carbon\bin).
3. Copy the below Powershell script commands and place it notepad or textfile.
4. Now you can replace your Carbon DLL path in following script for the variable $CarbonDllPath
5. You can also replace the user identity that you are going to set logon as service right in the variable $Identity
6. Now run as Powershell window with Admin Privilege ( Run as Administrator)
7. Copy the edited Powershell script and Run it in Powershell to set logon as a service right.
|
1
2
3
4
5
6
7
8
|
$Identity =
"DomainName\Administrator"
$privilege =
"SeServiceLogonRight"
$CarbonDllPath =
"C:\Users\Administrator\Downloads\Carbon-1.5.1\Carbon\bin\Carbon.dll"
[Reflection.
Assembly
]::LoadFile($CarbonDllPath)
Grant-Privilege -Identity $Identity -Privilege $privilege
|
Powershell output :
Web site links for Carbon DLL:
https://bitbucket.org/splatteredbits/carbon/downloads
http://pshdo.com/
http://get-carbon.org/help/Grant-Privilege.html
Set or Grant User Logon As A Service right/permission to user using C#
You can use the function GrantUserLogOnAsAService to set Logon as a Service right to user using C# code. This function uses the class LsaWrapper.|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
static
void
GrantUserLogOnAsAService(
string
userName)
{
try
{
LsaWrapper lsaUtility =
new
LsaWrapper();
lsaUtility.SetRight(userName,
"SeServiceLogonRight"
);
Console.WriteLine(
"Logon as a Service right is granted successfully to "
+ userName);
}
catch
(Exception ex)
{
Console.WriteLine(ex.<span id=
"IL_AD3"
class
=
"IL_AD"
>Message</span>);
}
}
|
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
|
public
class
LsaWrapper
{
// Import the LSA functions
[DllImport(
"advapi32.dll"
, PreserveSig =
true
)]
private
static
extern
UInt32 LsaOpenPolicy(
ref
LSA_UNICODE_STRING SystemName,
ref
LSA_OBJECT_ATTRIBUTES ObjectAttributes,
Int32 DesiredAccess,
out
IntPtr PolicyHandle
);
[DllImport(
"advapi32.dll"
, SetLastError =
true
, PreserveSig =
true
)]
private
static
extern
long
LsaAddAccountRights(
IntPtr PolicyHandle,
IntPtr AccountSid,
LSA_UNICODE_STRING[] UserRights,
long
CountOfRights);
[DllImport(
"advapi32"
)]
public
static
extern
void
FreeSid(IntPtr pSid);
[DllImport(
"advapi32.dll"
, CharSet = CharSet.Auto, SetLastError =
true
, PreserveSig =
true
)]
private
static
extern
bool
LookupAccountName(
string
lpSystemName,
string
lpAccountName,
IntPtr psid,
ref
int
cbsid,
StringBuilder domainName,
ref
int
cbdomainLength,
ref
int
use);
[DllImport(
"advapi32.dll"
)]
private
static
extern
bool
IsValidSid(IntPtr pSid);
[DllImport(
"advapi32.dll"
)]
private
static
extern
long
LsaClose(IntPtr ObjectHandle);
[DllImport(
"kernel32.dll"
)]
private
static
extern
int
GetLastError();
[DllImport(
"advapi32.dll"
)]
private
static
extern
long
LsaNtStatusToWinError(
long
status);
// define the structures
private
enum
LSA_AccessPolicy :
long
{
POLICY_VIEW_LOCAL_INFORMATION = 0x00000001L,
POLICY_VIEW_AUDIT_INFORMATION = 0x00000002L,
POLICY_GET_PRIVATE_INFORMATION = 0x00000004L,
POLICY_TRUST_ADMIN = 0x00000008L,
POLICY_CREATE_ACCOUNT = 0x00000010L,
POLICY_CREATE_SECRET = 0x00000020L,
POLICY_CREATE_PRIVILEGE = 0x00000040L,
POLICY_SET_DEFAULT_QUOTA_LIMITS = 0x00000080L,
POLICY_SET_AUDIT_REQUIREMENTS = 0x00000100L,
POLICY_AUDIT_LOG_ADMIN = 0x00000200L,
POLICY_SERVER_ADMIN = 0x00000400L,
POLICY_LOOKUP_NAMES = 0x00000800L,
POLICY_NOTIFICATION = 0x00001000L
}
[StructLayout(LayoutKind.Sequential)]
private
struct
LSA_OBJECT_ATTRIBUTES
{
public
int
Length;
public
IntPtr RootDirectory;
public
readonly
LSA_UNICODE_STRING ObjectName;
public
UInt32 Attributes;
public
IntPtr SecurityDescriptor;
public
IntPtr SecurityQualityOfService;
}
[StructLayout(LayoutKind.Sequential)]
private
struct
LSA_UNICODE_STRING
{
public
UInt16 Length;
public
UInt16 MaximumLength;
public
IntPtr Buffer;
}
///
//Adds a privilege to an account
/// Name of an account - "domain\account" or only "account"
/// Name ofthe privilege
/// The windows error code returned by LsaAddAccountRights
public
long
SetRight(String accountName, String privilegeName)
{
long
winErrorCode = 0;
//contains the last error
//pointer an size for the SID
IntPtr sid = IntPtr.Zero;
int
sidSize = 0;
//StringBuilder and size for the domain name
var domainName =
new
StringBuilder();
int
nameSize = 0;
//account-type variable for <span id="IL_AD9" class="IL_AD">lookup</span>
int
accountType = 0;
//get required buffer size
LookupAccountName(String.Empty, accountName, sid,
ref
sidSize, domainName,
ref
nameSize,
ref
accountType);
//allocate buffers
domainName =
new
StringBuilder(nameSize);
sid = Marshal.AllocHGlobal(sidSize);
//lookup the SID for <span id="IL_AD4" class="IL_AD">the account</span>
bool
result = LookupAccountName(String.Empty, accountName, sid,
ref
sidSize, domainName,
ref
nameSize,
ref
accountType);
//say what you're doing
Console.WriteLine(
"LookupAccountName result = "
+ result);
Console.WriteLine(
"IsValidSid: "
+ IsValidSid(sid));
Console.WriteLine(
"LookupAccountName domainName: "
+ domainName);
if
(!result)
{
winErrorCode = GetLastError();
Console.WriteLine(
"LookupAccountName failed: "
+ winErrorCode);
}
else
{
//initialize an empty unicode-string
var systemName =
new
LSA_UNICODE_STRING();
//combine all policies
var access = (
int
) (
LSA_AccessPolicy.POLICY_AUDIT_LOG_ADMIN |
LSA_AccessPolicy.POLICY_CREATE_ACCOUNT |
LSA_AccessPolicy.POLICY_CREATE_PRIVILEGE |
LSA_AccessPolicy.POLICY_CREATE_SECRET |
LSA_AccessPolicy.POLICY_GET_PRIVATE_INFORMATION |
LSA_AccessPolicy.POLICY_LOOKUP_NAMES |
LSA_AccessPolicy.POLICY_NOTIFICATION |
LSA_AccessPolicy.POLICY_SERVER_ADMIN |
LSA_AccessPolicy.POLICY_SET_AUDIT_REQUIREMENTS |
LSA_AccessPolicy.POLICY_SET_DEFAULT_QUOTA_LIMITS |
LSA_AccessPolicy.POLICY_TRUST_ADMIN |
LSA_AccessPolicy.POLICY_VIEW_AUDIT_INFORMATION |
LSA_AccessPolicy.POLICY_VIEW_LOCAL_INFORMATION
);
//initialize a pointer for the policy handle
IntPtr policyHandle = IntPtr.Zero;
//these attributes are not used, but LsaOpenPolicy wants them to exists
var ObjectAttributes =
new
LSA_OBJECT_ATTRIBUTES();
ObjectAttributes.Length = 0;
ObjectAttributes.RootDirectory = IntPtr.Zero;
ObjectAttributes.Attributes = 0;
ObjectAttributes.SecurityDescriptor = IntPtr.Zero;
ObjectAttributes.SecurityQualityOfService = IntPtr.Zero;
//get a policy handle
uint
resultPolicy = LsaOpenPolicy(
ref
systemName,
ref
ObjectAttributes, access,
out
policyHandle);
winErrorCode = LsaNtStatusToWinError(resultPolicy);
if
(winErrorCode != 0)
{
Console.WriteLine(
"OpenPolicy failed: "
+ winErrorCode);
}
else
{
//Now that we have the SID an the policy,
//we can add rights to the account.
//initialize an unicode-string for the privilege name
var userRights =
new
LSA_UNICODE_STRING[1];
userRights[0] =
new
LSA_UNICODE_STRING();
userRights[0].Buffer = Marshal.StringToHGlobalUni(privilegeName);
userRights[0].Length = (UInt16) (privilegeName.Length*UnicodeEncoding.CharSize);
userRights[0].MaximumLength = (UInt16) ((privilegeName.Length + 1)*UnicodeEncoding.CharSize);
//add the right to the account
long
res = LsaAddAccountRights(policyHandle, sid, userRights, 1);
winErrorCode = LsaNtStatusToWinError(res);
if
(winErrorCode != 0)
{
Console.WriteLine(
"LsaAddAccountRights failed: "
+ winErrorCode);
}
LsaClose(policyHandle);
}
FreeSid(sid);
}
return
winErrorCode;
}
}
|
Set Logon As A Service right to user via Command Line
You can use the NTRights.exe utility to grant or deny user rights to users and groups from a command line or a batch file. The NTRights.exe utility is included in the Windows NT Server 4.0 Resource Kit Supplement 3. Refer: http://support.microsoft.com/kb/266280Set Logon As A Service right
ntrights +r SeServiceLogonRight -u "Domain\Administrator"Revoke Logon As A Service right
ntrights -r SeServiceLogonRight -u "Domain\Administrator"
Set or Grant Logon As Service right/privilege to user via VBScript
1. Copy the below example VBScript code and paste it in notepad or a VBScript editor.2. Change the value for strUserName if you want to give your own name otherwise simply leave it.
3. Save the file with a .vbs extension, for example: SetLogonAsAServiceRight.vbs
4. Double-click the VBScript file (or Run this file from command window) to Set Logon As Service right/permission to user.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
' SetLogonAsAServiceRight.vbs
' Sample VBScript to set or grant Logon As A Service Right.
' Author: http://www.morgantechspace.com/
' ------------------------------------------------------'
Dim
strUserName,ConfigFileName,OrgStr,RepStr,inputFile,strInputFile,outputFile,obj
strUserName =
"work2008\DevUser"
Dim
oShell
Set
oShell = CreateObject (
"WScript.Shell"
)
oShell.Run
"secedit /export /cfg config.inf"
, 0, true
oShell.Run
"secedit /import /cfg config.inf /db database.sdb"
, 0, true
ConfigFileName =
"config.inf"
OrgStr =
"SeServiceLogonRight ="
RepStr =
"SeServiceLogonRight = "
& strUserName &
","
Set
inputFile = CreateObject(
"Scripting.FileSystemObject"
).OpenTextFile(
"config.inf"
, 1,1,-1)
strInputFile = inputFile.ReadAll
inputFile.Close
Set
inputFile =
Nothing
Set
outputFile = CreateObject(
"Scripting.FileSystemObject"
).OpenTextFile(
"config.inf"
,2,1,-1)
outputFile.Write (Replace(strInputFile,OrgStr,RepStr))
outputFile.Close
Set
outputFile =
Nothing
oShell.Run
"secedit /configure /db database.sdb /cfg config.inf"
,0,true
set oShell=
Nothing
Set
obj = CreateObject(
"Scripting.FileSystemObject"
)
obj.DeleteFile(
"config.inf"
)
obj.DeleteFile(
"database.sdb"
)
Msgbox
"Logon As A Service Right granted to user '"
& strUserName &
"' using Vbscript code"
|
Thanks,
Morgan
Software Developer
---------------------
























 2597
2597

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








