Iptables 规则用法小结:https://www.cnblogs.com/kevingrace/p/6265113.html
iptables只是Linux防火墙的管理工具;真正实现防火墙功能的是 netfilter,它是Linux内核中实现包过滤的内部结构。
Iptables采用“表”和“链”的分层结构,在Linux中现在是四张表五个链:(每个链可有N条规则)

iptables数据包报文的处理过程:
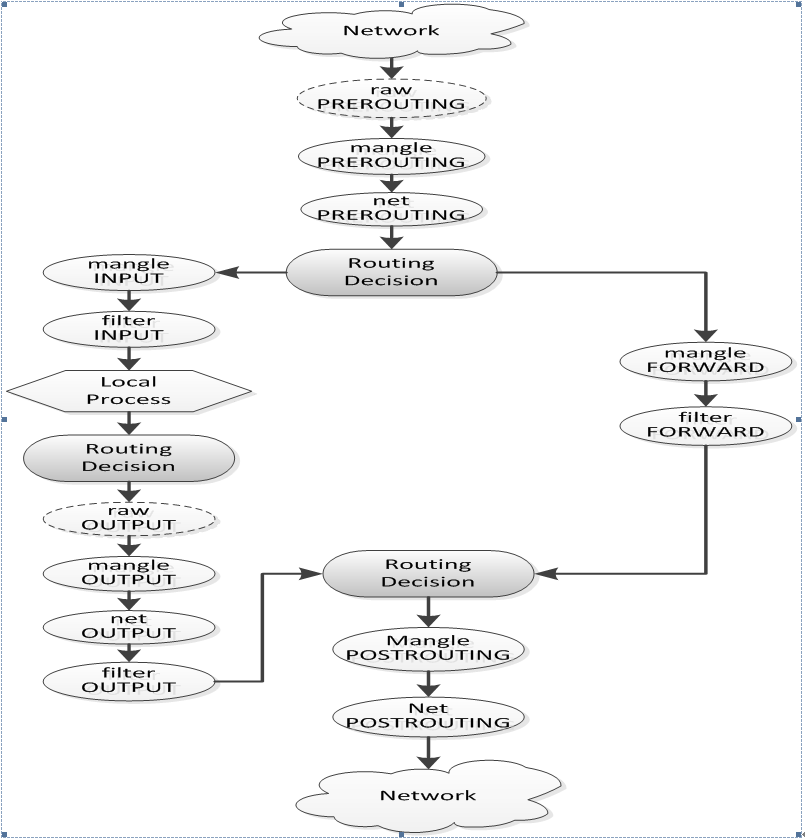
以mangle表中的INPUT链为例:
root@sonic:/home/admin# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination创建一个ssh-acl的规则链(vty):iptables -t mangle -N vty
root@sonic:/home/admin# iptables -t mangle -N vty root@sonic:/home/admin# iptables -t mangle -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination向规则链(vty)中添加规则:(-A 在vty链的尾行添加;-I 默认在vty链的首行添加,配合rulenum使用可以指定位置插入)
root@sonic:/home/admin# iptables -t mangle -A vty -s 192.168.15.0/24 -p tcp --dport 22 -j ACCEPT root@sonic:/home/admin# iptables -t mangle -A vty -s 0.0.0.0/0 -p tcp --dport 22 -j DROP root@sonic:/home/admin# iptables -t mangle -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination ACCEPT tcp -- 192.168.15.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh root@sonic:/home/admin# iptables -t mangle -I vty -s 192.168.14.0/24 -p tcp --dport 22 -j ACCEPT Chain INPUT (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination ACCEPT tcp -- 192.168.14.0/24 anywhere tcp dpt:ssh ACCEPT tcp -- 192.168.15.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh root@sonic:/home/admin# iptables -t mangle -I vty 3 -s 192.168.16.0/24 -p tcp --dport 22 -j ACCEPT Chain INPUT (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination ACCEPT tcp -- 192.168.14.0/24 anywhere tcp dpt:ssh ACCEPT tcp -- 192.168.15.0/24 anywhere tcp dpt:ssh ACCEPT tcp -- 192.168.16.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh将规则链(vty)添加到INPUT链:iptables -t mangle -I INPUT -g vty
root@sonic:/home/admin# iptables -t mangle -I INPUT -g vty root@sonic:/home/admin# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination vty all -- anywhere anywhere [goto] Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain vty (1 references) target prot opt source destination ACCEPT tcp -- 192.168.15.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh将规则链(vty)从INPUT链中摘除:iptables -t mangle -D INPUT -g vty
root@sonic:/home/admin# iptables -t mangle -D INPUT -g vty root@sonic:/home/admin# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination ACCEPT tcp -- 192.168.15.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh将规则链(vty)中的规则删除:iptables -t mangle -F vty
或者逐条规则删除: iptables -t mangle -D vty -s 192.168.15.0/24 -p tcp --dport 22 -j ACCEPT
root@sonic:/home/admin# iptables -t mangle -F vty root@sonic:/home/admin# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain vty (0 references) target prot opt source destination删除mangle表中的规则链(vty):iptables -t mangle -X vty
要想删除vty链,需要保证链中所有规则已经全部删除.
root@sonic:/home/admin# iptables -t mangle -X vty root@sonic:/home/admin# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination
iptables中规则匹配的顺序:(ACL-seq)优先级高的规则先匹配
如下表所示【规则代表只有192.168.16.0/24网段的源IP才能ssh到该设备管理口】,规则表中从上至下顺序执行,如果没遇到匹配的规则,就一条一条往下执行,如果遇到匹配的规则后,就执行相应的动作(accept, drop等),规则表中后续规则不再匹配。
root@sonic:/home/admin# iptables -t mangle -I INPUT -g vty root@sonic:/home/admin# iptables -t mangle -L Chain INPUT (policy ACCEPT) target prot opt source destination vty all -- anywhere anywhere [goto] Chain vty (1 references) target prot opt source destination ACCEPT tcp -- 192.168.16.0/24 anywhere tcp dpt:ssh #高优先级 DROP tcp -- anywhere anywhere tcp dpt:ssh #低优先级
iptables中的创建规则并指定rulenum时,必须从1开始累加赋值,删除rulenum=1的规则后,rulenum=2的规则自动升级为1,以此类推;
root@sonic:/home/admin# iptables -t mangle -I vty 1 -s 192.168.16.0/24 -p tcp --dport 22 -j ACCEPT root@sonic:/home/admin# iptables -t mangle -I vty 2 -s 0.0.0.0/0 -p tcp --dport 22 -j DROP root@sonic:/home/admin# iptables -t mangle -L Chain vty (0 references) target prot opt source destination ACCEPT tcp -- 192.168.16.0/24 anywhere tcp dpt:ssh DROP tcp -- anywhere anywhere tcp dpt:ssh root@sonic:/home/admin# iptables -t mangle -D vty 1 root@sonic:/home/admin# iptables -t mangle -L Chain vty (0 references) target prot opt source destination DROP tcp -- anywhere anywhere tcp dpt:ssh root@sonic:/home/admin# iptables -t mangle -D vty 2 iptables: Index of deletion too big. root@sonic:/home/admin# iptables -t mangle -D vty 1 root@sonic:/home/admin# iptables -t mangle -L Chain vty (0 references) target prot opt source destination






















 897
897











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








