题目
题目给了两个文件。RSA公钥文件public.key,密文文件flag.enc
public.key
-----BEGIN PUBLIC KEY-----
MIIBJDANBgkqhkiG9w0BAQEFAAOCAREAMIIBDAKCAQMlsYv184kJfRcjeGa7Uc/4
3pIkU3SevEA7CZXJfA44bUbBYcrf93xphg2uR5HCFM+Eh6qqnybpIKl3g0kGA4rv
tcMIJ9/PP8npdpVE+U4Hzf4IcgOaOmJiEWZ4smH7LWudMlOekqFTs2dWKbqzlC59
NeMPfu9avxxQ15fQzIjhvcz9GhLqb373XDcn298ueA80KK6Pek+3qJ8YSjZQMrFT
+EJehFdQ6yt6vALcFc4CB1B6qVCGO7hICngCjdYpeZRNbGM/r6ED5Nsozof1oMbt
Si8mZEJ/Vlx3gathkUVtlxx/+jlScjdM7AFV5fkRidt0LkwosDoPoRz/sDFz0qTM
5q5TAgMBAAE=
-----END PUBLIC KEY-----
flag.enc
CQGd9sC/h9lnLpua50/071knSsP4N8WdmRsjoNIdfclrBhMjp7NoM5xy2SlNLLC2
yh7wbRw08nwjo6UF4tmGKKfcjPcb4l4bFa5uvyMY1nJBvmqQylDbiCnsODjhpB1B
JfdpU1LUKtwsCxbc7fPL/zzUdWgO+of/R9WmM+QOBPagTANbJo0mpDYxvNKRjvac
9Bw4CQTTh87moqsNRSE/Ik5tV2pkFRZfQxAZWuVePsHp0RXVitHwvKzwmN9vMqGm
57Wb2Sto64db4gLJDh9GROQN+EQh3yLoSS8NNtBrZCDddzfKHa8wv6zN/5znvBst
sDBkGyi88NzQxw9kOGjCWtwpRw==
解题过程
可以通过openssl可以得到n和e或者利用python中的RSA模块获取n和e
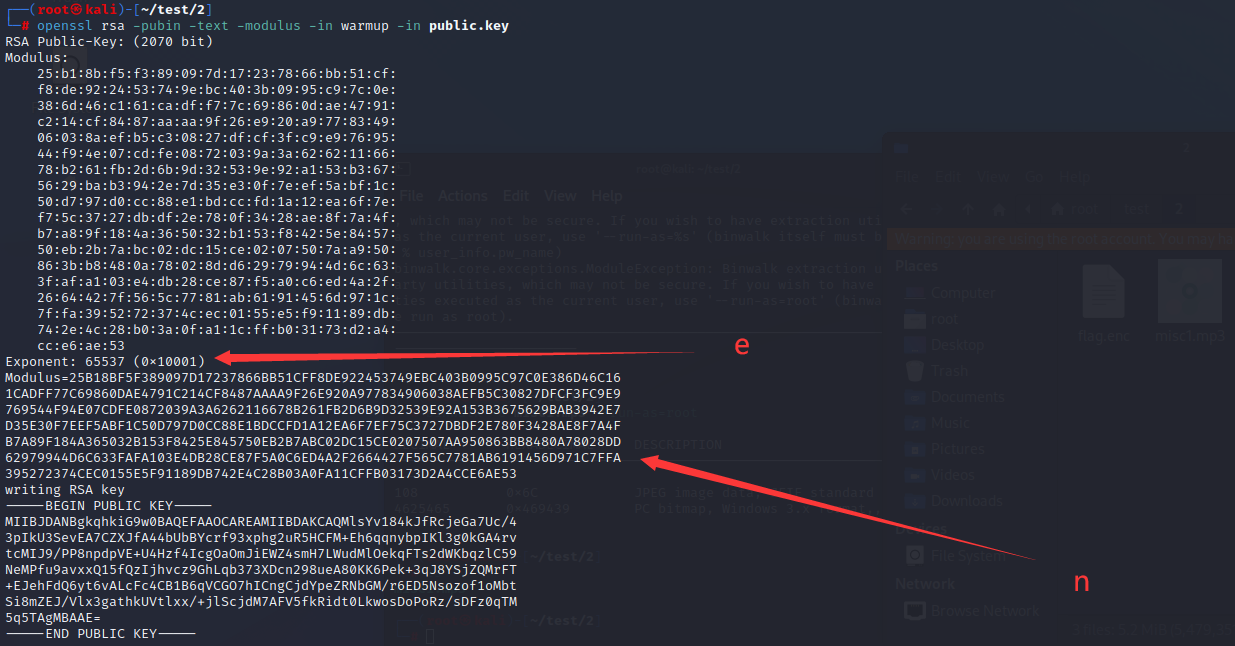
1.openssl获取n和e
openssl rsa -pubin -text -modulus -in warmup -in public.key
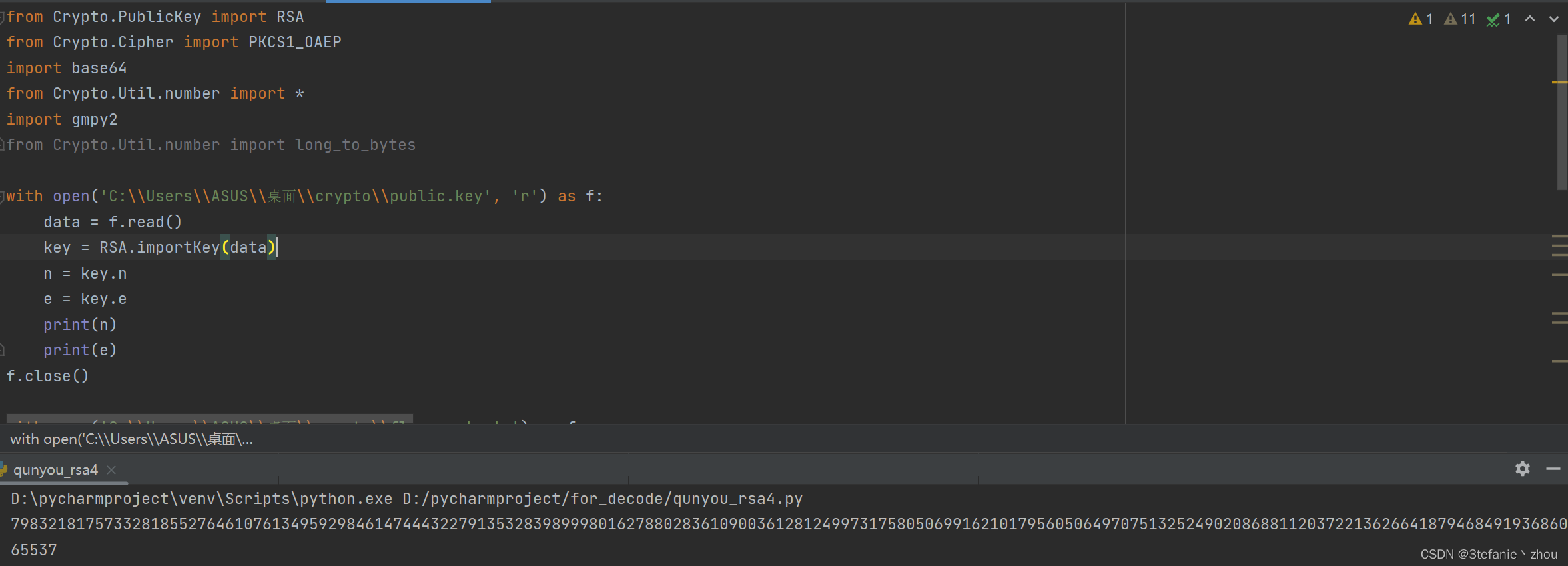
2.利用python中的RSA模块获取n和e
from Crypto.PublicKey import RSA
with open('C:\\Users\\ASUS\\桌面\\crypto\\public.key', 'r') as f:
data = f.read()
key = RSA.importKey(data)
n = key.n
e = key.e
print(n)
print(e)
f.close()
然后读取flag.enc,再进行base64解密得到密文C
with open('C:\\Users\\ASUS\\桌面\\crypto\\flag.enc', 'r') as f:
data = f.read()
enc = base64.b64decode(data)
print(bytes_to_long(enc))
f.close()
使用yafu分解n,得到p和q
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
之后算出phi_n以及d
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
因为加密脚本采用了PKCS1_OAEP模式下的RSA加密,所以我们需要通过手动构造私钥进而才可以去解密密文。采用原始的pow(c,d,n)是无法正确的解密密文的。
因此,我们需要先采用PKCS1_OAEP模式构造私钥,然后利用这个私钥来解密密文文件。
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
privkey = RSA.construct((int(n),int(e),int(d),int(p),int(q)))
key = PKCS1_OAEP.new(privkey)
flag = key.decrypt(enc)
print(flag)
解题脚本
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
import base64
from Crypto.Util.number import *
import gmpy2
with open('C:\\Users\\ASUS\\桌面\\crypto\\public.key', 'r') as f:
data = f.read()
key = RSA.importKey(data)
n = key.n
e = key.e
print(n)
print(e)
f.close()
with open('C:\\Users\\ASUS\\桌面\\crypto\\flag.enc', 'r') as f:
data = f.read()
enc = base64.b64decode(data)
f.close()
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
e= 65537
c = bytes_to_long(enc)
n = 79832181757332818552764610761349592984614744432279135328398999801627880283610900361281249973175805069916210179560506497075132524902086881120372213626641879468491936860976686933630869673826972619938321951599146744807653301076026577949579618331502776303983485566046485431039541708467141408260220098592761245010678592347501894176269580510459729633673468068467144199744563731826362102608811033400887813754780282628099443490170016087838606998017490456601315802448567772411623826281747245660954245413781519794295336197555688543537992197142258053220453757666537840276416475602759374950715283890232230741542737319569819793988431443
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
privkey = RSA.construct((int(n),int(e),int(d),int(p),int(q)))
key = PKCS1_OAEP.new(privkey)
flag = key.decrypt(enc)
print(flag)
flag:
EKO{classic_rsa_challenge_is_boring_but_necessary}
【青青槐荫,皎皎月光。春风一披拂,百卉各争妍】





















 3229
3229











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








