Misc
misc1
打开txt发现有380行,明显的零宽字符
直接丢在线零宽字符网站解密
https://330k.github.io/misc_tools/unicode_steganography.html
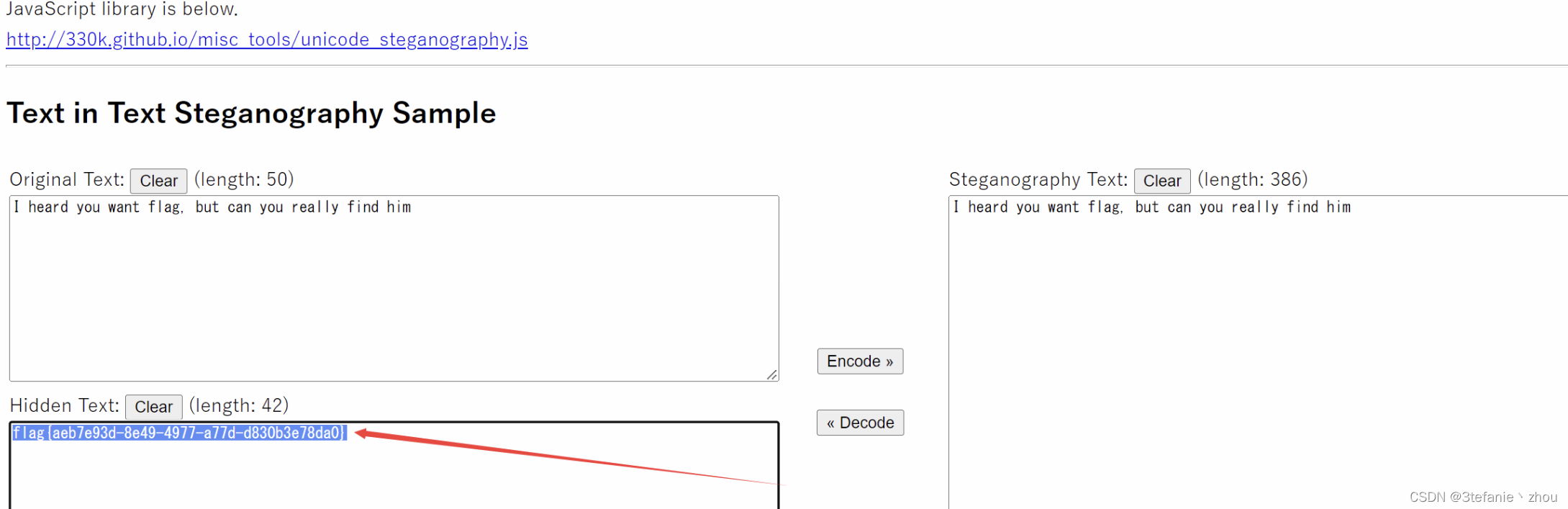
flag:
flag{aeb7e93d-8e49-4977-a77d-d830b3e78da0}
misc2
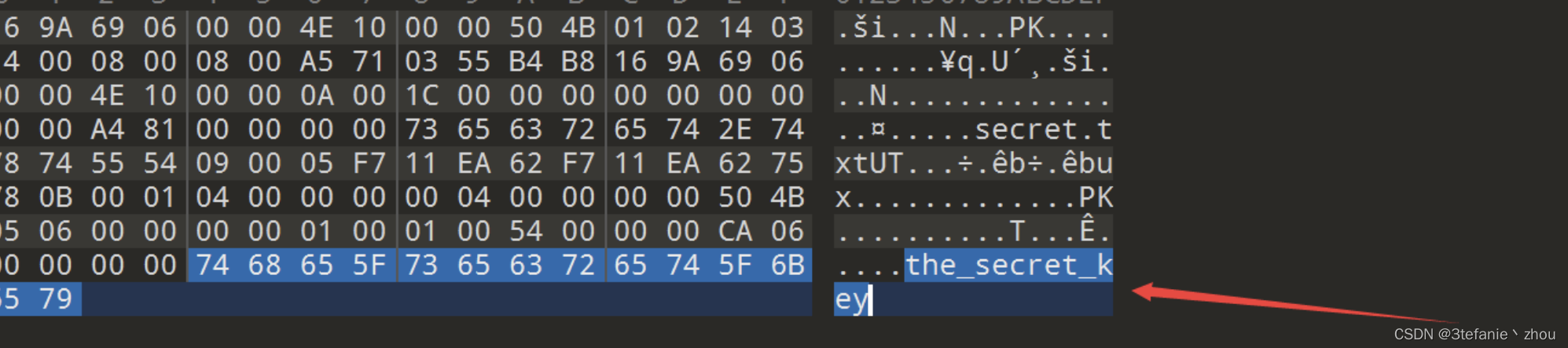
打开压缩包发现是一堆的aes-emoji表情

然后在压缩包中找到key:the_secret_key
aes-emoji解密得到

之后将😊作为-,🙃作为.,空格作为分隔符进行摩斯解密
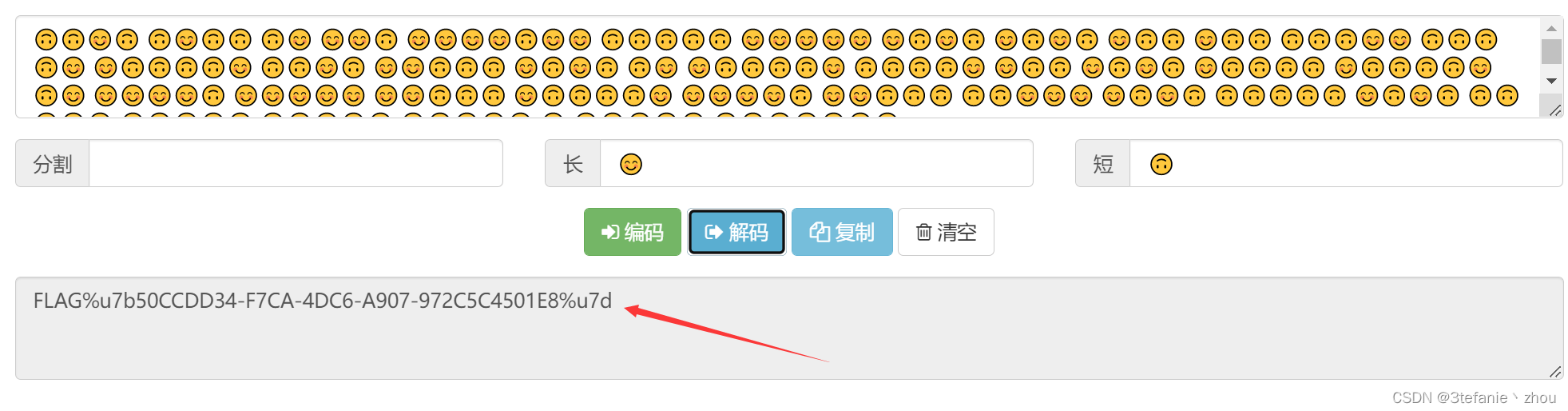
flag:
FLAG{50CCDD34-F7CA-4DC6-A907-972C5C4501E8}
Web
web1
根据题目要求使用Put方法发送message,得到一串base64编码数据
在这里插入图片描述
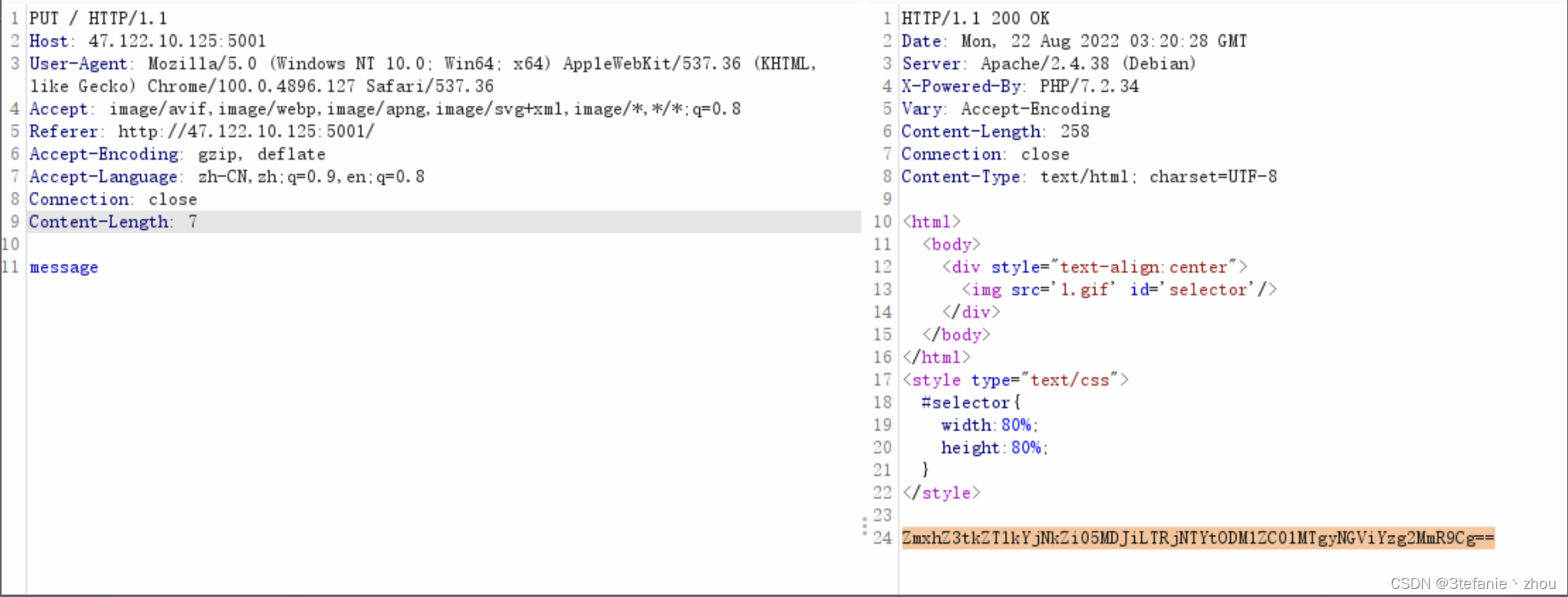
base64解密得到flag
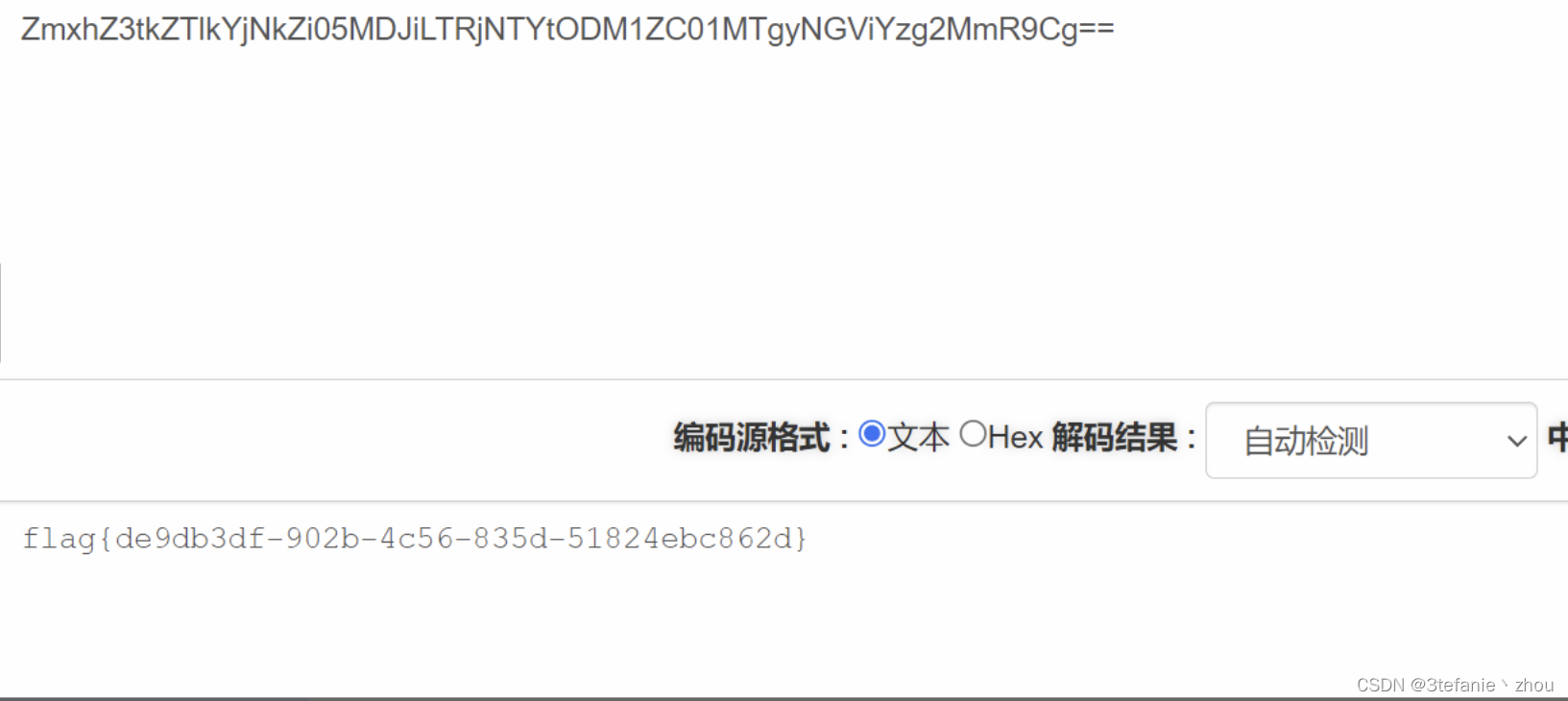
flag:
flag{de9db3df-902b-4c56-835d-51824ebc862d}
Re
re1
解压apk文件
在.so文件中搜索flag发现base64加密的flag
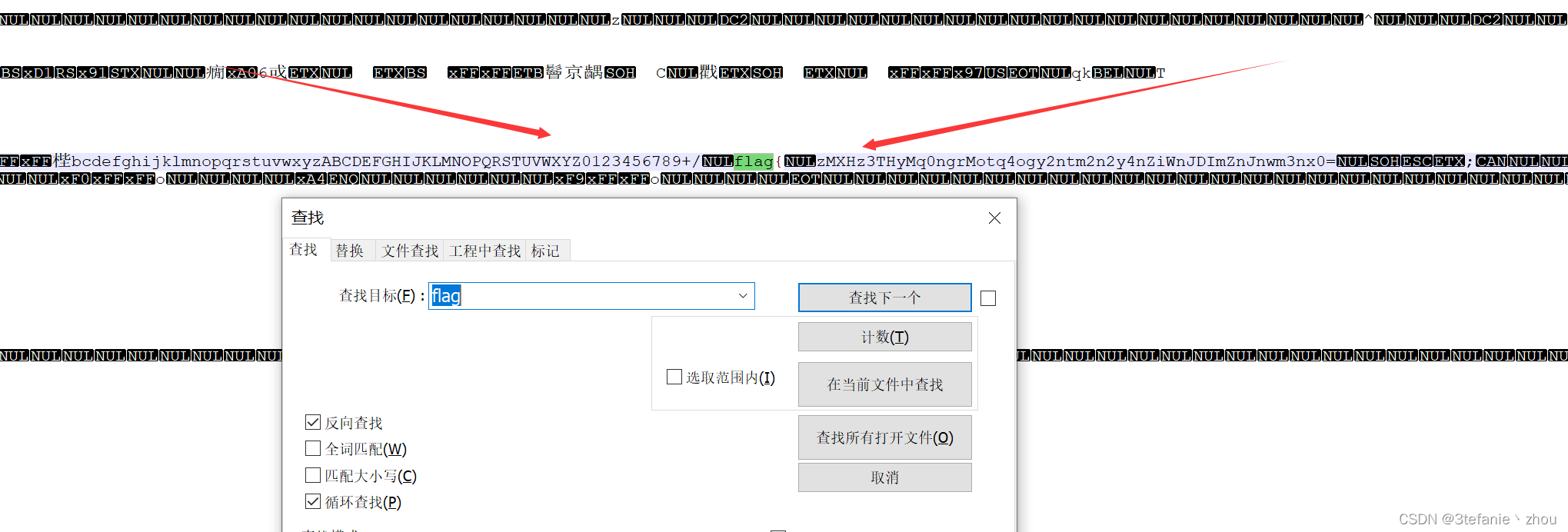
一眼顶针,base64换表。
直接将flag前面的abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/替换base64的新表再解密即可
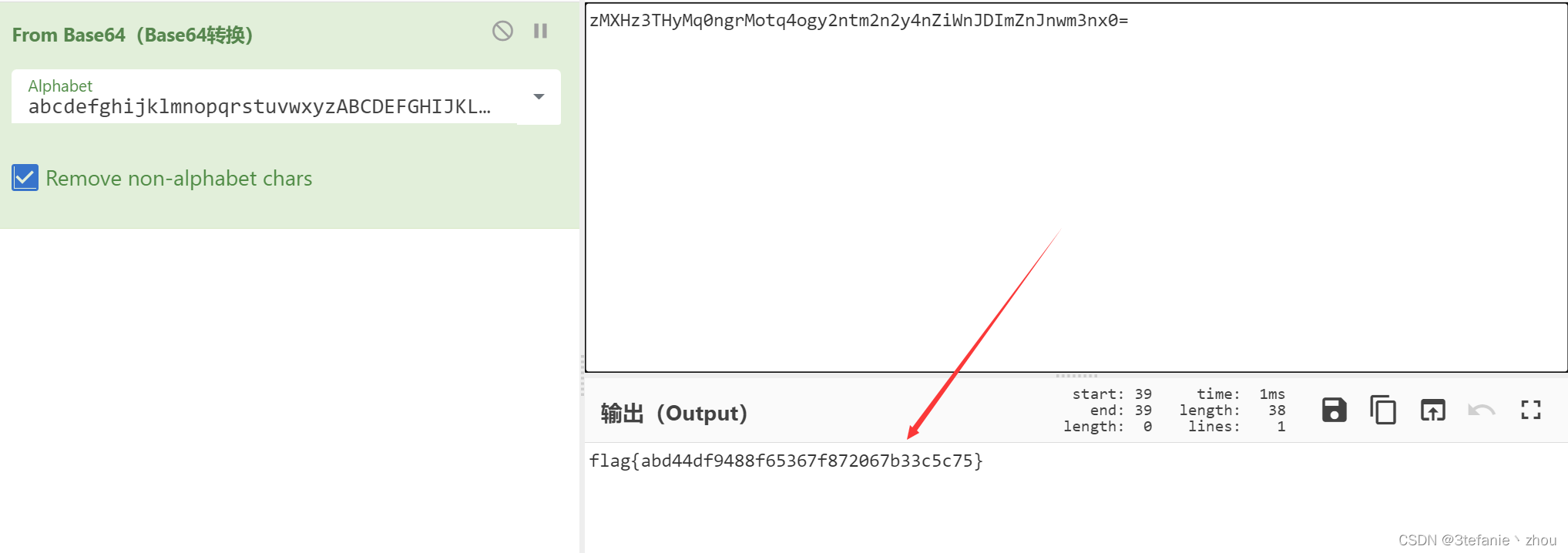
flag:
flag{abd44df9488f65367f872067b33c5c75}
re2
丢尽ida中反编译,发现存在花指令
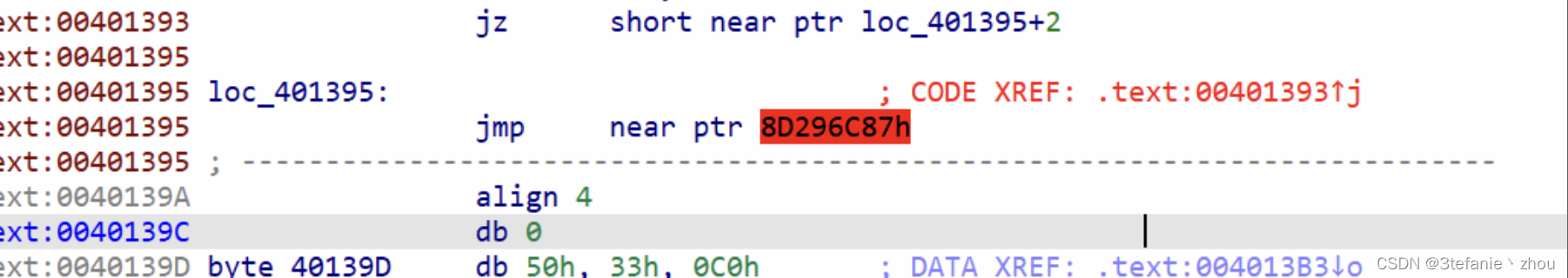
在ida中去除花指令,继续查看,发现还存在花指令
去除多个花指令后得到如下代码
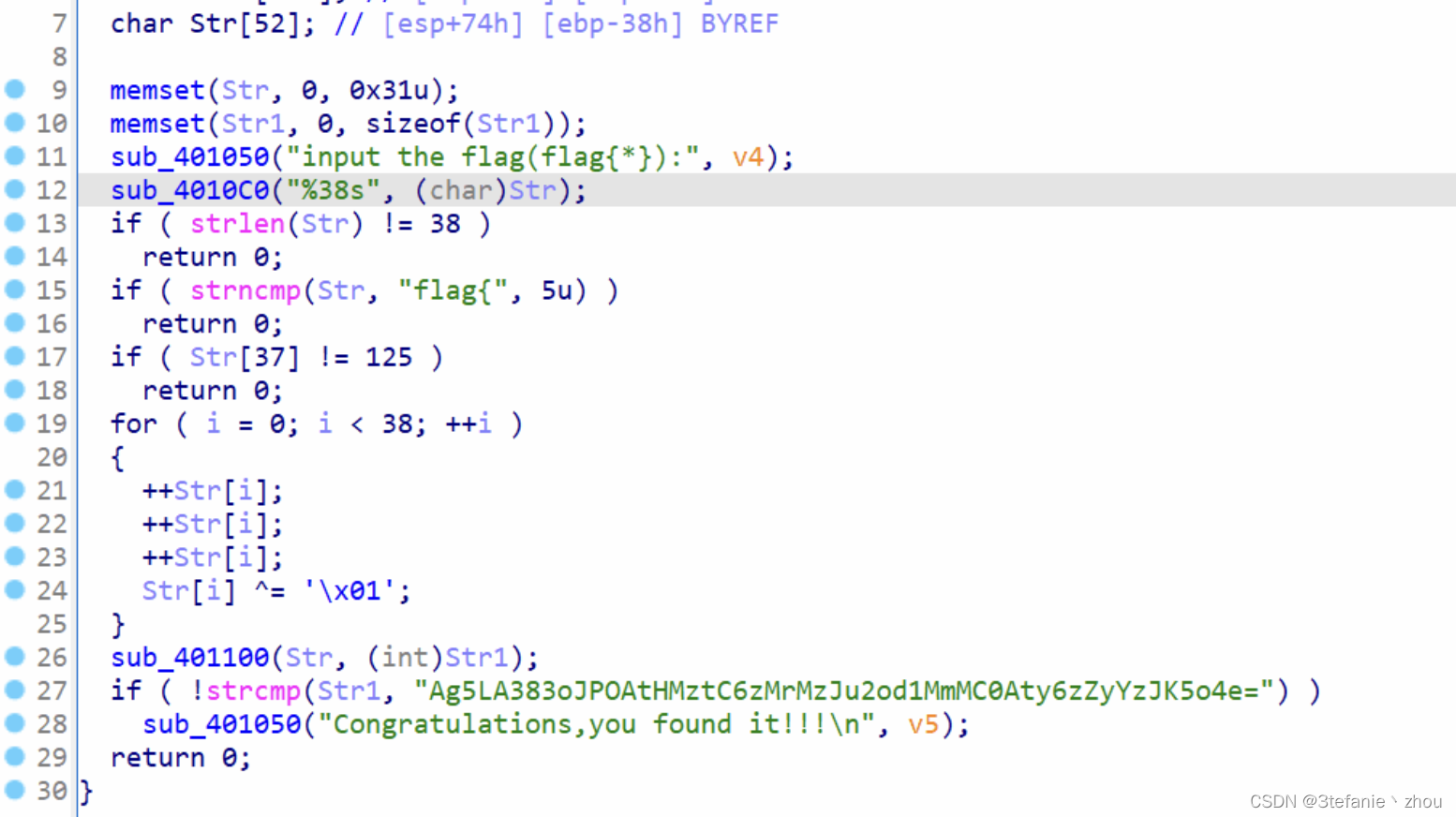
经过代码分析,是base64换表

将换表后的密文进行解密,然后将解密后的值与0x01进行异或再减去3,最后将值转换为字符拼接起来即可得到flag
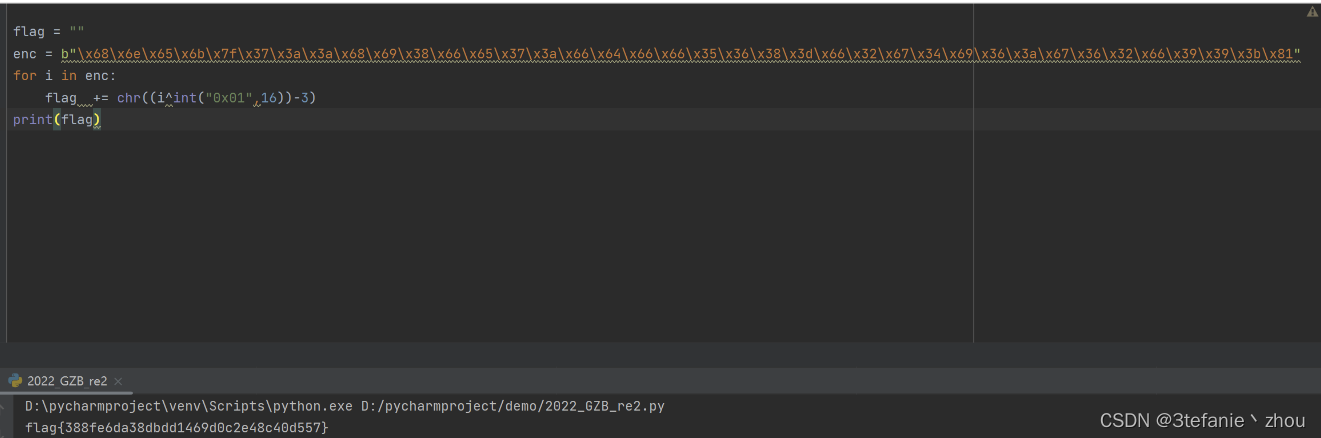
flag:
flag{388fe6da38dbdd1469d0c2e48c40d557}
PS:24佬,逆向滴神
Crypto
crypto1
题目脚本:
from Crypto.Util.number import getPrime, bytes_to_long
from private import flag
def prod(lst):
ret = 1
for num in lst:
ret *= num
return ret
m = bytes_to_long(flag)
primes = [getPrime(32) for _ in range(128)]
n = prod(primes)
e = 65537
print(n)
print(pow(m, e, n))
题目分析:该题循环128次生成32位内的素数,并逐一相乘得到n。此题关键在于分解n,可以利用在线的factordb网站分解(速度会慢一点)。更好的方式是利用sage中的factor去获取n的质因子,然后逐一减一再相乘获取phi_n。
经la佬指点,sage中还有更好用的欧拉函数直接求得phi_n,即euler_phi(n)
PS:呜呜呜,la佬,永远的密码神
解题sage脚本1:
import libnum
import gmpy2
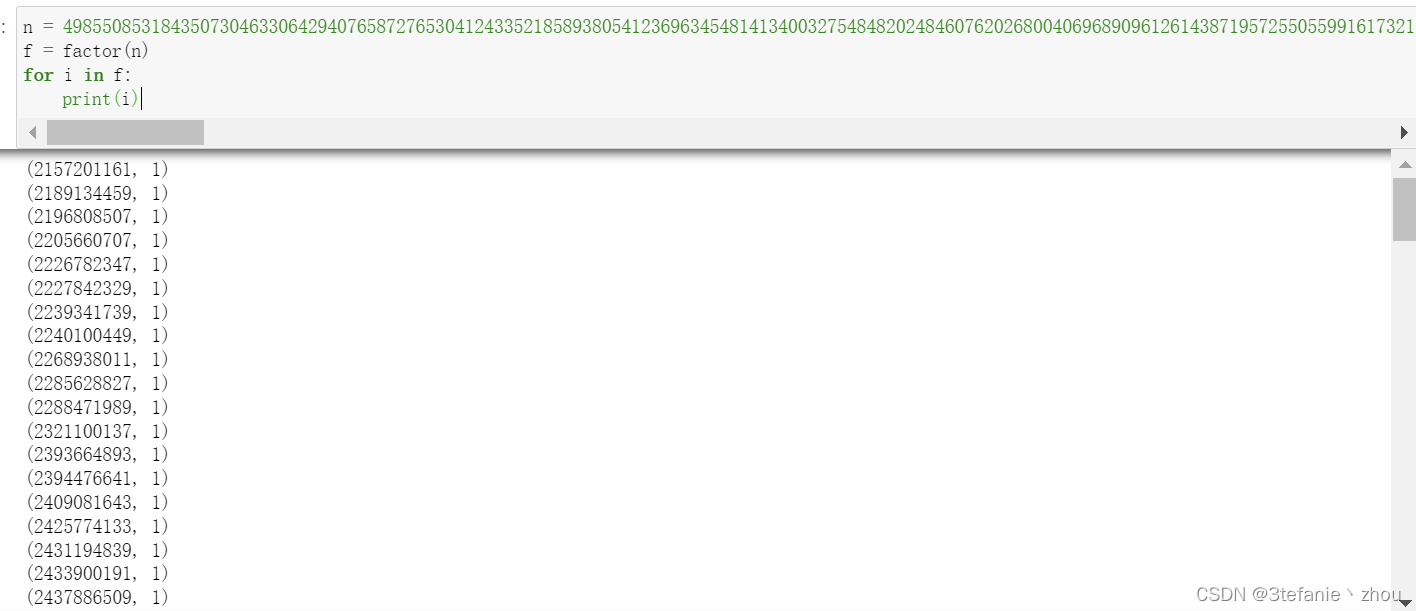
n = 49855085318435073046330642940765872765304124335218589380541236963454814134003275484820248460762026800406968909612614387195725505599161732173392638922786803311634545787045750985305489377942134248021067866421562958650150294230888228985465349786699479689256807465768291737611710217406103274112513343522220579775846598432707064257755776968832655194007245146498098969678280994239966324629884465410583122858282366628813265851968510470965791399482347740834450388330114047756336958735465527462814834713103520953935529330042307850614270340063658350328792248313740537076253637843721024504644597206697381299557947444980226466873318668287989717967944585523926884053786776312597480545886246474490223835791688488128381319614090743542249712583034478626526803646151613891095908533705664756543044233211912755029579409820701593827537415071352230125454228067829708365542363728928615026085295070159189419017700579134399189094919696859791164271004180260539313586898823659478287374563448765508515448239946223017459137307294211786033013932581750061197281833829139141387627759828251411177434140137846483051746471223623874561111161396582813759688262897508032776273734870302625894327342010642833281804636297142996523583625528835539148769210703
c = 16402842294493057983664243934220410367922940064827442432635311538480259276693509061580178099156672734935071591984975846251552151158996555441540673736782655511109689242530218909623902239361387976253099488694749080041058601946401795438420778732039723942603210906137778277751920492456089120157084624625689393856644681236531481555553310179396715881794304350662061591378357548647386383226829059901411963596970110005082851173119873959506608820974202852298513582148730122250099666503479885504873701010178419440534561313370798381801403824394868772907174238263809571599191928663819277131853753740167401508603150166842871600719845855581570148319435027636716776848101223730745987468157963881450392354186721122591613234449764063117158539030391228797346711154877572896981921225969509518759322541659341488322332946673447777165338449931340249620317959955132691469504297273159896092178954211618661250417995610050958199243935927131725491363126509229036071515630335776479789450713314042438409774423384617410164068629188030711022989650783699334538536380642780758730693752953836987618960789409525401409412421619923140599348899209332612164802489097000673103781114195396843813456784010847708400021027265621140506331350848438181967123625314
e = 65537
phi = 1
for i in factor(n):
phi *= i[0]-1
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(libnum.n2s(int(m)))
解题sage脚本2:
import libnum
import gmpy2
n = 49855085318435073046330642940765872765304124335218589380541236963454814134003275484820248460762026800406968909612614387195725505599161732173392638922786803311634545787045750985305489377942134248021067866421562958650150294230888228985465349786699479689256807465768291737611710217406103274112513343522220579775846598432707064257755776968832655194007245146498098969678280994239966324629884465410583122858282366628813265851968510470965791399482347740834450388330114047756336958735465527462814834713103520953935529330042307850614270340063658350328792248313740537076253637843721024504644597206697381299557947444980226466873318668287989717967944585523926884053786776312597480545886246474490223835791688488128381319614090743542249712583034478626526803646151613891095908533705664756543044233211912755029579409820701593827537415071352230125454228067829708365542363728928615026085295070159189419017700579134399189094919696859791164271004180260539313586898823659478287374563448765508515448239946223017459137307294211786033013932581750061197281833829139141387627759828251411177434140137846483051746471223623874561111161396582813759688262897508032776273734870302625894327342010642833281804636297142996523583625528835539148769210703
c = 16402842294493057983664243934220410367922940064827442432635311538480259276693509061580178099156672734935071591984975846251552151158996555441540673736782655511109689242530218909623902239361387976253099488694749080041058601946401795438420778732039723942603210906137778277751920492456089120157084624625689393856644681236531481555553310179396715881794304350662061591378357548647386383226829059901411963596970110005082851173119873959506608820974202852298513582148730122250099666503479885504873701010178419440534561313370798381801403824394868772907174238263809571599191928663819277131853753740167401508603150166842871600719845855581570148319435027636716776848101223730745987468157963881450392354186721122591613234449764063117158539030391228797346711154877572896981921225969509518759322541659341488322332946673447777165338449931340249620317959955132691469504297273159896092178954211618661250417995610050958199243935927131725491363126509229036071515630335776479789450713314042438409774423384617410164068629188030711022989650783699334538536380642780758730693752953836987618960789409525401409412421619923140599348899209332612164802489097000673103781114195396843813456784010847708400021027265621140506331350848438181967123625314
e = 65537
phi2 = euler_phi(n)
d = gmpy2.invert(e,phi2)
m = pow(c,d,n)
print(libnum.n2s(int(m)))
flag:
flag{d7ec0101f0d87bf4e7dd097205fd2e04}
crypto2
题目代码:
from sage.all import *
from hashlib import sha256
from Crypto.Cipher import AES
from secret import flag
def pad(msg):
return msg + bytes([0 for _ in range(16-len(msg)%16)])
def my_func(f, k):
g = x
while k > 0:
if k % 2 == 1:
g = f(g)
k = k // 2
f = f(f)
return g
p = random_prime(2**512)
R = PolynomialRing(GF(p),'x')
x = R.gens()[0]
fa,fb,fc,fd = 114,514,1919,810
ga,gb,gc,gd = 33,44,5,21
f = (fa*x+fb)/(fc*x+fd)
g = (ga*x+gb)/(gc*x+gd)
x0 = randint(0, 2**128)
x1 = randint(0, 2**128)
y0 = randint(0, 2**128)
y1 = randint(0, 2**128)
C1 = my_func(f, x0)(my_func(g, x1))
C2 = my_func(f, y0)(my_func(g, y1))
C = my_func(f, x0 + y0)(my_func(g, x1 + y1))(0)
IV_KEY = sha256(str(C).encode()).digest()
IV = IV_KEY[:16]
KEY = IV_KEY[16:]
aes = AES.new(key=KEY,mode=AES.MODE_CBC,IV=IV)
with open("output.txt", "w") as f:
f.write("p = %s\n" % p)
f.write("C1 = %s\n" % C1)
f.write("C2 = %s\n" % C2)
f.write("cipher = %s\n" % aes.encrypt(pad(flag)).hex())
原题为:2022midnight sun ctf crypto-kompot
具体题目分析如下
https://blog.maple3142.net/2022/04/03/midnight-sun-ctf-qualifiers-2022-writeups/#kompot_512
套用大佬的脚本解得C0
p = 3194984946529517576623074200234946014168164205272620815161235399519719606884315059679688351630156726656139476261880683998464588759384965205345409962107767
R.<x> = PolynomialRing(GF(p))
A = (
255573898199035041758965366038981084944157531399911657546492546433145386414968079402856253975194361011751146133423751388034343796045680531444243160752444
* x
+ 2903815552142613054383579208402338539795913037192087937799264976572710846298203210386085195493581420468855607449914648116910772709084472519026435777636170
) / (
x
+ 2386683479870808801459935303369975419760291443763988239234510374382152688298962756930974138943582796452015141560932451900850718037631878185501679332085683
)
B = (
132377494416343006999975863569277589493418289854129016039518413763966765500976955235604047782115253235862592410665710097368078866567903025458054587345605
* x
+ 1747644595793214356518694901929361859865467988580968186098568614375536195838520451868446204083724173193509104728376048358592847546643445182566589580577650
) / (
x
+ 2894641605792738933156836404900021526130503288556167018479410774304302335346335534666287744353802552093529238578190020705070270037282203986873569075466267
)
def F(f: R, k: Integer) -> R:
g = x
while k > 0:
if k % 2 == 1:
g = f(g)
k = k // 2
f = f(f)
return g
f = (114 * x + 514) / (1919 * x + 810)
g = (33 * x + 44) / (5 * x + 21)
def fn2mat(f):
a = f.numerator()[1]
b = f.numerator()[0]
c = f.denominator()[1]
d = f.denominator()[0]
return matrix(GF(p), [
[a, b],
[c, d]
])
# find xa=ax, yb=by, u=xy
# simplify to x_inv*a=a*x_inv, yb=by, x_inv*u=y
a = fn2mat(f)
b = fn2mat(g)
u = fn2mat(A)
v = fn2mat(B)
P.<y00,y01,y10,y11> = GF(p)[]
y = matrix([
[y00, y01],
[y10, y11]
])
x_inv = y * ~u
def add_mat_eq(polys, lhs, rhs):
for i in range(lhs.nrows()):
for j in range(lhs.ncols()):
polys.append(lhs[i, j] - rhs[i, j])
polys = []
add_mat_eq(polys, y * b, b * y)
add_mat_eq(polys, x_inv * a, a * x_inv)
# alternative way to solve this system: P.ideal(polys).groebner_basis()
M, _ = Sequence(polys).coefficient_matrix()
print(M.change_ring(Zmod(107))) # overview of matrix
print(_) # variables of each column
# no constant term so only need to find the kernel
# many solutions so any one of them will work
y00, y01, y10, y11 = M.right_kernel().basis()[0]
y = matrix(GF(p), [
[y00, y01],
[y10, y11]
])
x_inv = y * ~u
x = ~x_inv
shared = x * v * y
c0 = shared[0, 1] / shared[1, 1]
print("My kompot is ready: midnight{%d}" % c0)
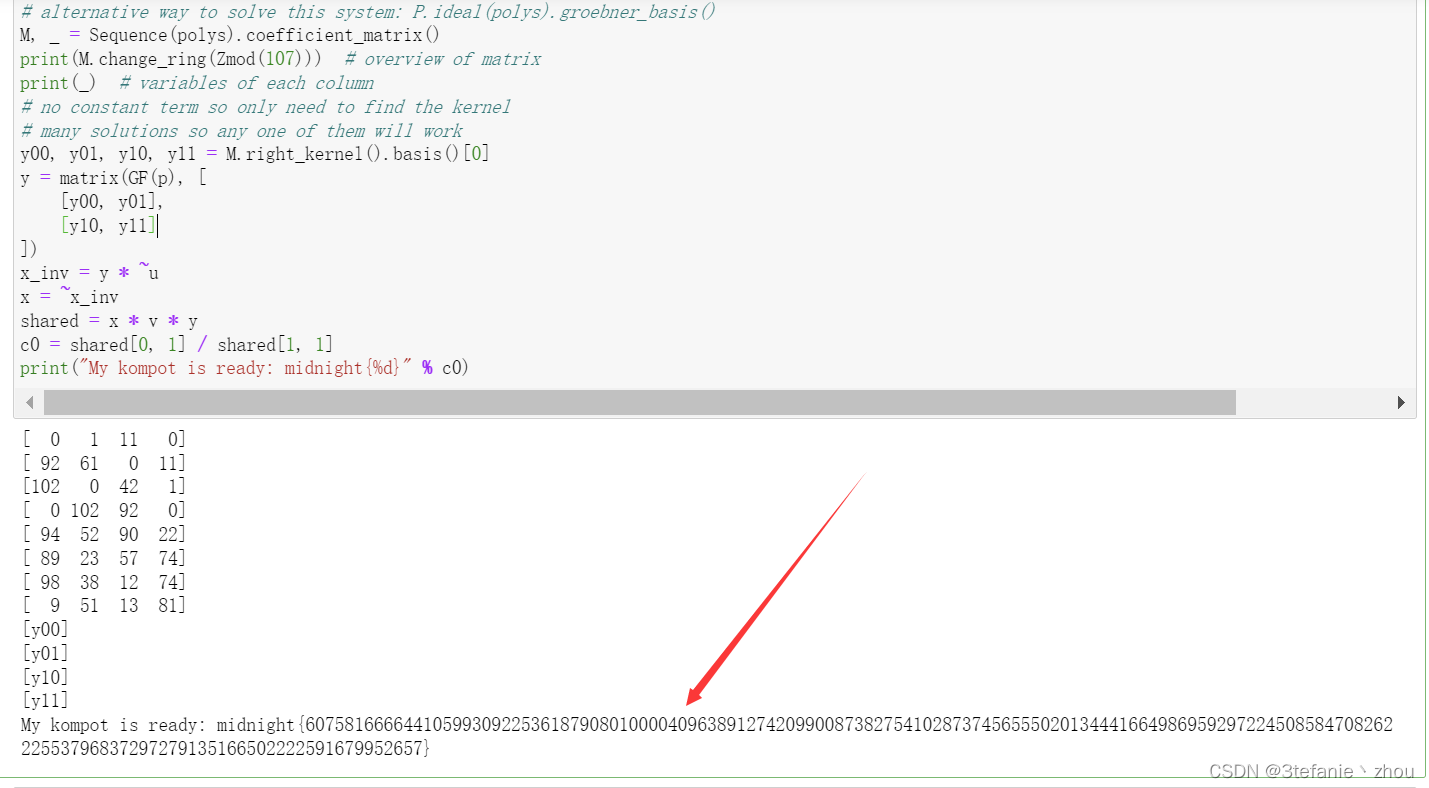
C0=60758166664410599309225361879080100004096389127420990087382754102873745655502013444166498695929722450858470826222553796837297279135166502222591679952657
然后将C0计算sha256()散列算法得到一串哈希值,然后将哈希值的前16位和后16位分别作为iv和key进行aes解密cipher即可得到flag
from Crypto.Cipher import AES
import binascii
c0 = 60758166664410599309225361879080100004096389127420990087382754102873745655502013444166498695929722450858470826222553796837297279135166502222591679952657
cipher = b'149af037d77a9412932b2c2eed330fd85b097f08fc389c8e515fed6994c9d2ee0130502048f7fe84518fba684a2b7eb3'
cipher1 = binascii.unhexlify(cipher)
IV_KEY = sha256(str(c0).encode()).digest()
IV = IV_KEY[:16]
KEY = IV_KEY[16:]
aes = AES.new(key=KEY,mode=AES.MODE_CBC,IV=IV)
print(aes.decrypt(cipher1))
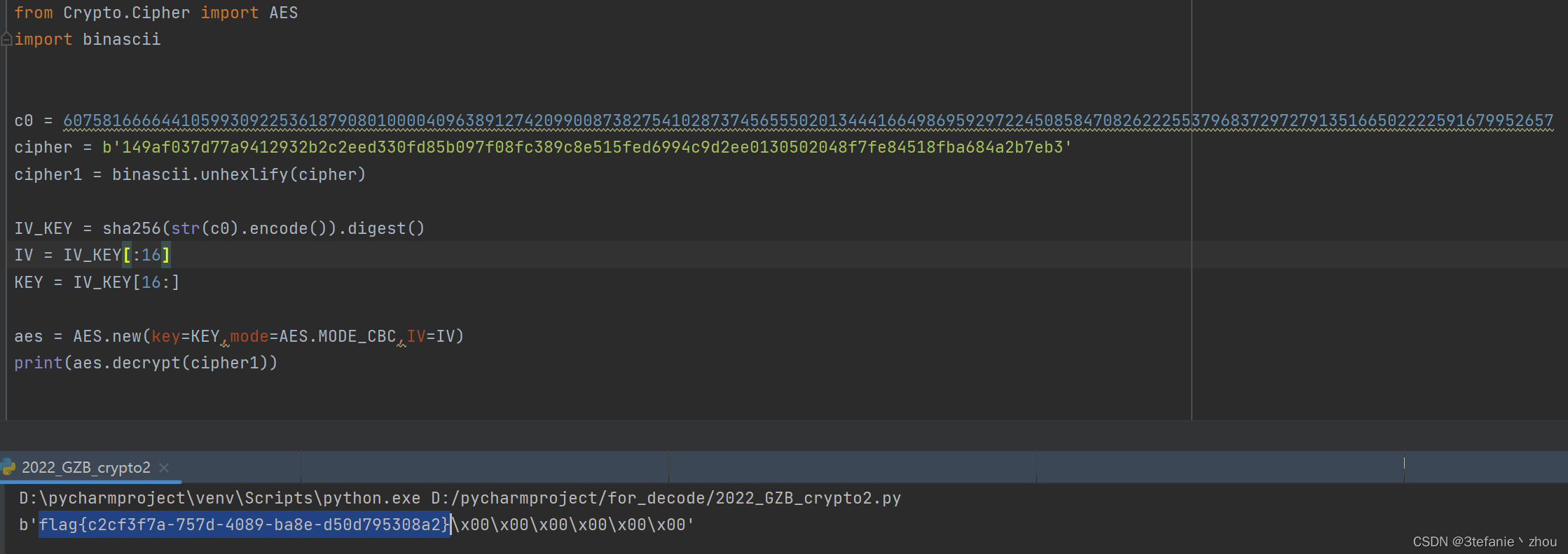
flag:
flag{c2cf3f7a-757d-4089-ba8e-d50d795308a2}
【喜欢一个女子时,岂敢不真心,岂敢不用心。】






















 1万+
1万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








