OpenVpn搭建
1.前提条件
在阿里云购买三台服务器,其中有一台服务器必须有一个公网ip
2.搭建环境
# 一、环境概述:
# 专有网络:172.16.0.0/12
# 交换机(张家口):172.30.0.0/24
# 1.openvpn-server:公网(47.92.120.196)私网(172.30.0.1)
# 2.web01.magedu.org:私网(172.30.0.100)
# 2.web02.magedu.org:私网(172.30.0.200)
# 二、连接openvpn服务器
ssh root@47.92.100.196
[root@openvpn-server ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:16:3e:04:4a:08 brd ff:ff:ff:ff:ff:ff
inet 172.30.0.1/24 brd 172.30.0.255 scope global dynamic eth0
valid_lft 315358791sec preferred_lft 315358791sec
inet6 fe80::216:3eff:fe04:4a08/64 scope link
valid_lft forever preferred_lft forever
[root@openvpn-server ~]#
[root@openvpn-server ~]# curl ifconfig.me
47.92.120.196
# 这里看到的ip却只有一个172.30.0.1,没有47.92.120.196,通过curl ifocnfig.me才能看到,这是为什么?
这里就是DNAT的作用,在下面讲解一下DNAT和SNAT的区别。
# 直接通过ssh openvpn-server这台机器进行跳转到其他两台web服务器
ssh 172.30.0.100
[root@web01 ~]# yum -y install httpd;hostname > /var/www/html/index.html;systemctl enable --now httpd
[root@web02 ~]# curl 172.30.0.200
web02.magedu.org
ssh 172.30.0.200
[root@web01 ~]# yum -y install httpd;hostname > /var/www/html/index.html;systemctl enable --now httpd
[root@web01 ~]# curl 172.30.0.100
web01.magedu.org
[root@web01 ~]#
2.1 DNAT(Destination Network Address Translation)和 SNAT(Source Network Address Translation)
当我们谈论网络地址转换(NAT)时,通常会涉及两种主要类型:SNAT(源网络地址转换)和DNAT(目标网络地址转换)。这两种类型的NAT在实际网络中有广泛的应用。让我们详细了解每一种
SNAT(源网络地址转换)
- 定义:SNAT 是用于更改数据包的源 IP 地址。常常用在出站流量中。
- 使用场景:当私有网络内的设备需要访问外部网络(例如互联网)时,通常使用 SNAT。这允许多个内部设备共享一个公共IP地址进行出站连接。
- 工作原理:例如,假设一个内部设备使用私有IP(如192.168.1.10)尝试访问互联网。路由器或防火墙将使用SNAT将源地址192.168.1.10更改为公共IP地址(例如203.0.113.10),然后将数据包转发到互联网。
- 优势:可以节省IPv4地址空间,因为多个内部设备可以共享一个公共IP进行互联网访问。
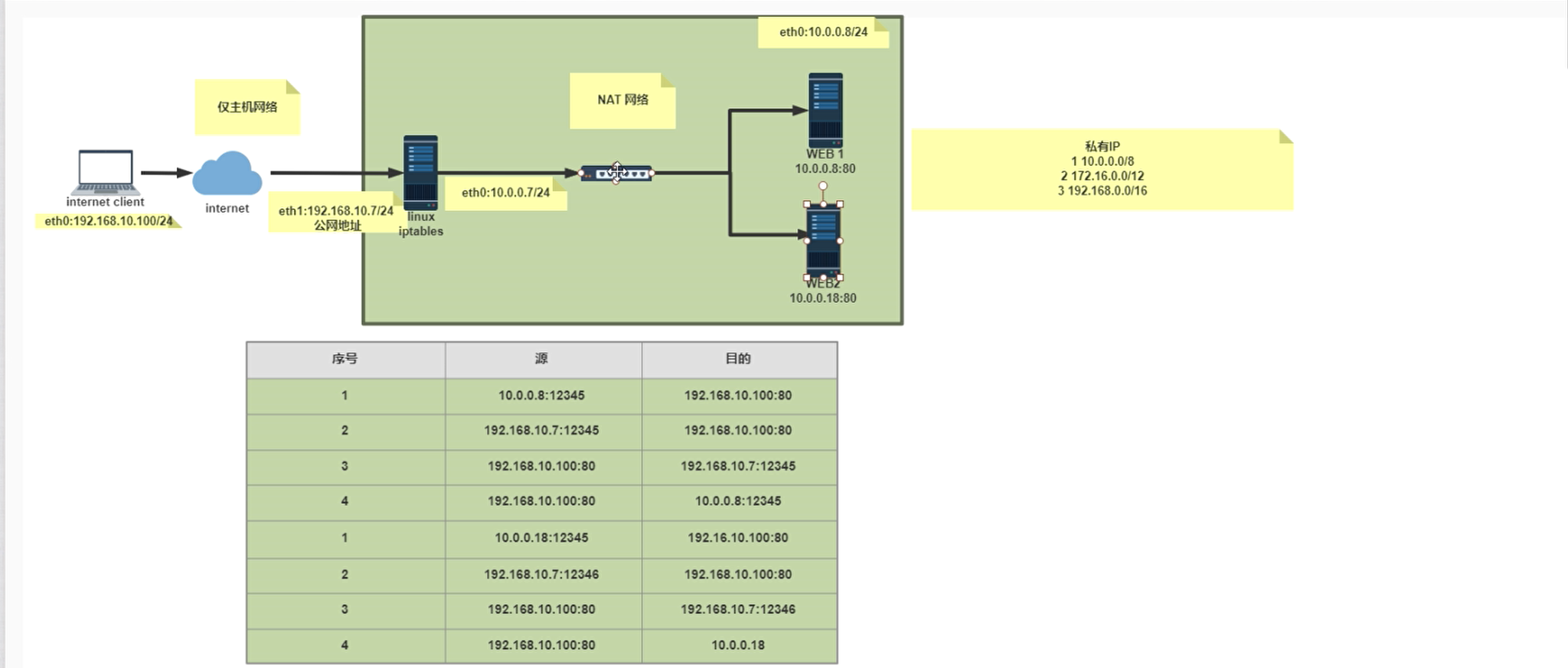
DNAT(目标网络地址转换)
- 定义:DNAT 用于更改数据包的目标 IP 地址。常常用在入站流量中。
- 使用场景:当需要将来自外部网络(例如互联网)的请求路由到私有网络内的特定设备时,通常使用 DNAT。这通常用于让外部用户访问内部服务器,例如web服务器、FTP服务器等。
- 工作原理:例如,假设有来自互联网的请求目标是一个公共IP地址(例如203.0.113.10)。路由器或防火墙会使用DNAT将目标地址更改为私有网络内的特定设备的IP地址(如192.168.1.10),然后将数据包转发到该设备。
- 优势:允许外部用户访问私有网络内的服务,同时保持其他内部设备的隔离和安全。
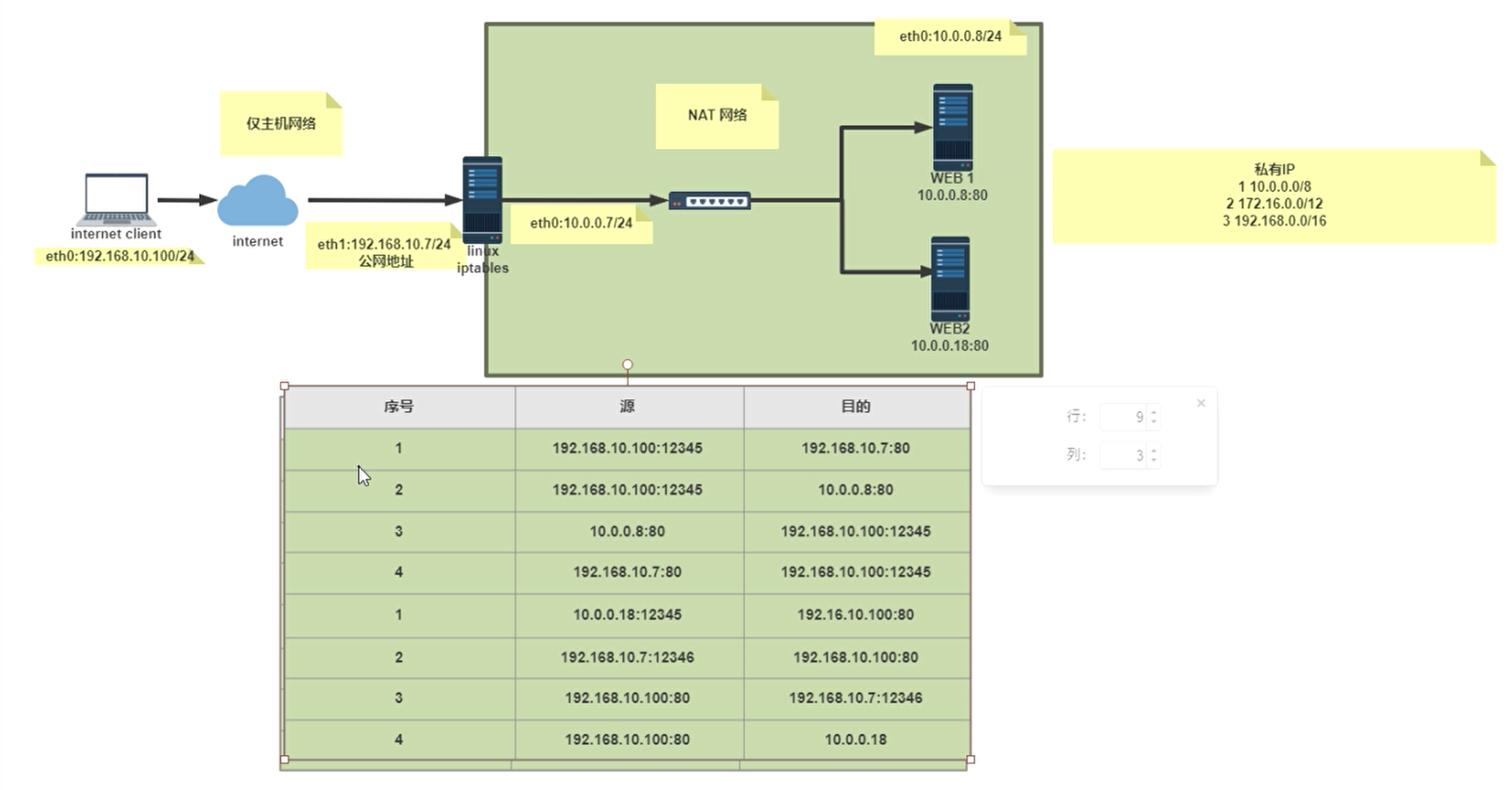
总结:
- SNAT主要关心“从哪里来”(源地址),它修改源地址。
- DNAT主要关心“要去哪里”(目标地址),它修改目标地址。
2.2 配置基于key验证
# 1.生成SSH密钥对:
[root@openvpn-server ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:xwBkc44wn2WmWiTZgRu5WLj54l7Envw/xS5Gfi6tOrI root@openvpn-server
The key's randomart image is:
+---[RSA 2048]----+
| .+*B.= |
| . *B.% |
| = +* o |
| +.oo o |
| .+ S.o |
| .+.. ..o |
| . .= o + |
| ..... * + |
| .. Eoo=oB. |
+----[SHA256]-----+
# 2.拷贝.ssh文件夹到其他两台机器上
[root@openvpn-server ~]# rsync -av .ssh 172.30.0.100:/root/
[root@openvpn-server ~]# rsync -av .ssh 172.30.0.200:/root/
# 3.使用ssh进行验证
这样就可以免密钥登录了,如果为了安全可以禁用密码登录
[root@openvpn-server ~]# vim /etc/ssh/sshd_config
# 添加下面内容
PasswordAuthentication no
2.3 安装openvpn和easy-rsa
# 查看openvpn版本
[root@openvpn-server ~]# yum list openvpn
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
Installed Packages
openvpn.x86_64 2.4.12-1.el7 @epel
[root@openvpn-server ~]#
# 安装openvpn服务器端以及证书管理工具
[root@openvpn-server ~]# yum -y install openvpn easy-rsa
3.证书管理
3.1 准备配置文件环境
# 查看安装好的openvpn的版本
[root@openvpn-server ~]# rpm -qi openvpn
Name : openvpn
Version : 2.4.12
Release : 1.el7
Architecture: x86_64
Install Date: Tue 22 Aug 2023 11:36:40 AM CST
Group : Unspecified
Size : 1286851
License : GPLv2
Signature : RSA/SHA256, Fri 18 Mar 2022 05:21:26 AM CST, Key ID 6a2faea2352c64e5
Source RPM : openvpn-2.4.12-1.el7.src.rpm
Build Date : Fri 18 Mar 2022 02:59:28 AM CST
Build Host : buildvm-x86-10.iad2.fedoraproject.org
Relocations : (not relocatable)
Packager : Fedora Project
Vendor : Fedora Project
URL : https://community.openvpn.net/
Bug URL : https://bugz.fedoraproject.org/openvpn
Summary : A full-featured SSL VPN solution
Description :
OpenVPN is a robust and highly flexible tunneling application that uses all
of the encryption, authentication, and certification features of the
OpenSSL library to securely tunnel IP networks over a single UDP or TCP
port. It can use the Marcus Franz Xaver Johannes Oberhumers LZO library
for compression.
[root@openvpn-server ~]#
# 查看安装openvpn的文件列表
[root@openvpn-server ~]# rpm -ql openvpn
/etc/openvpn
/etc/openvpn/client
/etc/openvpn/server
/run/openvpn-client
/run/openvpn-server
/usr/lib/systemd/system/openvpn-client@.service
/usr/lib/systemd/system/openvpn-server@.service
/usr/lib/systemd/system/openvpn@.service
/usr/lib/tmpfiles.d/openvpn.conf
/usr/lib64/openvpn
/usr/lib64/openvpn/plugins
/usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so
/usr/lib64/openvpn/plugins/openvpn-plugin-down-root.so
/usr/sbin/openvpn
/usr/share/doc/openvpn-2.4.12
/usr/share/doc/openvpn-2.4.12/AUTHORS
/usr/share/doc/openvpn-2.4.12/COPYING
/usr/share/doc/openvpn-2.4.12/COPYRIGHT.GPL
/usr/share/doc/openvpn-2.4.12/ChangeLog
/usr/share/doc/openvpn-2.4.12/Changes.rst
/usr/share/doc/openvpn-2.4.12/README
/usr/share/doc/openvpn-2.4.12/README.auth-pam
/usr/share/doc/openvpn-2.4.12/README.down-root
/usr/share/doc/openvpn-2.4.12/README.systemd
/usr/share/doc/openvpn-2.4.12/contrib
/usr/share/doc/openvpn-2.4.12/contrib/OCSP_check
/usr/share/doc/openvpn-2.4.12/contrib/OCSP_check/OCSP_check.sh
/usr/share/doc/openvpn-2.4.12/contrib/README
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/README
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/fwmarkroute.down
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/fwmarkroute.up
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf/client.down
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf/client.up
/usr/share/doc/openvpn-2.4.12/management-notes.txt
/usr/share/doc/openvpn-2.4.12/sample
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/README
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/client.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/firewall.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/home.up
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/loopback-client
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/loopback-server
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/office.up
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/openvpn-shutdown.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/openvpn-startup.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/roadwarrior-client.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/roadwarrior-server.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/static-home.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/static-office.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/tls-home.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/tls-office.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/xinetd-client-config
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/xinetd-server-config
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/auth-pam.pl
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/bridge-start
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/bridge-stop
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/ucn.pl
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/verify-cn
/usr/share/doc/openvpn-2.4.12/sample/sample-windows
/usr/share/doc/openvpn-2.4.12/sample/sample-windows/sample.ovpn
/usr/share/man/man8/openvpn.8.gz
/var/lib/openvpn
# 拷贝服务配置模板到/etc/openvpn,生成服务器配置文件
[root@openvpn-server ~]# cp /usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf /etc/openvpn/
[root@openvpn-server ~]# ll /etc/openvpn
total 20
drwxr-x--- 2 root openvpn 4096 Mar 18 2022 client
drwxr-x--- 2 root openvpn 4096 Mar 18 2022 server
-rw-r--r-- 1 root root 10784 Aug 22 13:53 server.conf
[root@openvpn-server ~]#
# 查看easy-rsa的文件列表
[root@openvpn-server ~]# rpm -ql easy-rsa
/usr/share/doc/easy-rsa-3.0.8
/usr/share/doc/easy-rsa-3.0.8/COPYING.md
/usr/share/doc/easy-rsa-3.0.8/ChangeLog
/usr/share/doc/easy-rsa-3.0.8/README.md
/usr/share/doc/easy-rsa-3.0.8/README.quickstart.md
/usr/share/doc/easy-rsa-3.0.8/vars.example
/usr/share/easy-rsa
/usr/share/easy-rsa/3
/usr/share/easy-rsa/3.0
/usr/share/easy-rsa/3.0.8
/usr/share/easy-rsa/3.0.8/easyrsa
/usr/share/easy-rsa/3.0.8/openssl-easyrsa.cnf
/usr/share/easy-rsa/3.0.8/x509-types
/usr/share/easy-rsa/3.0.8/x509-types/COMMON
/usr/share/easy-rsa/3.0.8/x509-types/ca
/usr/share/easy-rsa/3.0.8/x509-types/client
/usr/share/easy-rsa/3.0.8/x509-types/code-signing
/usr/share/easy-rsa/3.0.8/x509-types/email
/usr/share/easy-rsa/3.0.8/x509-types/kdc
/usr/share/easy-rsa/3.0.8/x509-types/server
/usr/share/easy-rsa/3.0.8/x509-types/serverClient
/usr/share/licenses/easy-rsa-3.0.8
/usr/share/licenses/easy-rsa-3.0.8/gpl-2.0.txt
[root@openvpn-server ~]#
# 准备证书签发相关文件
[root@openvpn-server ~]# cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa-server
[root@openvpn-server ~]# ll /etc/openvpn
total 24
drwxr-x--- 2 root openvpn 4096 Mar 18 2022 client
drwxr-xr-x 3 root root 4096 Aug 22 14:01 easy-rsa-server
drwxr-x--- 2 root openvpn 4096 Mar 18 2022 server
-rw-r--r-- 1 root root 10784 Aug 22 13:53 server.conf
[root@openvpn-server ~]#
# 准备签发证书相关变量的配置文件
[root@openvpn-server ~]# cp /usr/share/doc/easy-rsa-3.0.8/vars.example /etc/openvpn/easy-rsa-server/3/vars
# 建议修改给CA和OpenVPN服务器颁发的证书的有效期,可适当加长
[root@openvpn-server ~]# vim /etc/openvpn/easy-rsa-server/3/vars
#CA的证书有效期默为为10年,可以适当延长,比如:36500天
#set_var EASYRSA_CA_EXPIRE 3650
set_var EASYRSA_CA_EXPIRE 36500
#服务器证书默为为825天,可适当加长,比如:3650天
#set_var EASYRSA_CERT_EXPIRE 825
#将上面行修改为下面
set_var EASYRSA_CERT_EXPIRE 3650
3.2 准备证书相关文件
3.2.1 创建CA机构
# 进入easyrsa脚本所在的文件夹列表
[root@openvpn-server ~]# cd /etc/openvpn/easy-rsa-server/3/
[root@openvpn-server 3]# ls
easyrsa openssl-easyrsa.cnf vars x509-types
[root@openvpn-server 3]#
# 初始化 Public Key Infrastructure (PKI)生成PKI相关目录和文件
[root@openvpn-server 3]# ./easyrsa init-pki
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa-server/3/pki
[root@openvpn-server 3]#tree pki
pki
├── openssl-easyrsa.cnf
├── private
├── reqs
└── safessl-easyrsa.cnf
2 directories, 2 files
# 创建CA机构
[root@openvpn-server 3]# ./easyrsa build-ca nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating RSA private key, 2048 bit long modulus
........................................................................+++
..............................................+++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:
CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/etc/openvpn/easy-rsa-server/3/pki/ca.crt
[root@openvpn-server 3]#
# 查看文件列表
[root@openvpn-server 3]# tree pki -C
pki
├── ca.crt
├── certs_by_serial
├── index.txt
├── index.txt.attr
├── issued
├── openssl-easyrsa.cnf
├── private
│ └── ca.key
├── renewed
│ ├── certs_by_serial
│ ├── private_by_serial
│ └── reqs_by_serial
├── reqs
├── revoked
│ ├── certs_by_serial
│ ├── private_by_serial
│ └── reqs_by_serial
├── safessl-easyrsa.cnf
└── serial
12 directories, 7 files
[root@openvpn-server 3]#
# 查看生成的CA证书
[root@openvpn-server 3]# openssl x509 -in pki/ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
bc:21:18:c8:d0:e9:f9:c0
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=Easy-RSA CA
Validity
Not Before: Aug 22 06:42:24 2023 GMT
Not After : Jul 29 06:42:24 2123 GMT
Subject: CN=Easy-RSA CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:a6:d4:e2:27:20:15:40:e4:9c:a8:dc:1e:ab:1c:
46:58:0d:50:63:56:8d:a5:98:55:35:30:74:f8:0c:
e8:98:47:de:e0:1e:64:9a:d6:79:05:86:a3:ad:6f:
7f:a9:7c:e5:0e:f5:16:16:3b:73:c0:45:aa:95:d8:
30:ea:2a:26:85:7b:b1:2f:2a:6e:ba:f1:e4:d2:f4:
d6:79:7c:31:b6:aa:17:fb:04:a2:a2:8d:7b:63:13:
99:8d:38:b2:e5:14:6e:30:ed:71:b0:89:c6:05:9e:
0b:80:3c:5c:d1:f2:25:3e:9a:b6:ec:fb:e1:f6:a7:
f7:ac:13:76:44:c4:de:d0:e0:14:04:09:1c:b6:d0:
62:8e:22:73:a1:6c:4f:dc:89:e5:1b:22:92:be:b8:
35:43:d7:83:ab:fd:95:65:c3:f5:9c:18:ee:ce:d1:
0f:fc:b1:b4:70:43:5b:ac:5c:79:5a:9b:cd:02:bf:
d3:f3:0a:b3:78:c3:6c:69:e7:ac:da:d7:91:75:11:
22:c8:ae:17:d3:96:4c:d1:27:c5:b5:3e:a4:18:65:
e0:3e:69:e8:a2:9a:f4:03:7d:9f:5c:62:c0:c5:d8:
d4:e5:6f:1c:bb:a4:8c:89:f5:91:44:03:c3:15:9d:
79:8f:04:3a:79:03:30:bc:43:4e:d8:56:9d:96:86:
8a:f5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
2D:77:F9:F5:B0:DD:E2:0E:4E:51:A7:CD:7F:83:26:FC:FA:53:C4:1E
X509v3 Authority Key Identifier:
keyid:2D:77:F9:F5:B0:DD:E2:0E:4E:51:A7:CD:7F:83:26:FC:FA:53:C4:1E
DirName:/CN=Easy-RSA CA
serial:BC:21:18:C8:D0:E9:F9:C0
X509v3 Basic Constraints:
CA:TRUE
X509v3 Key Usage:
Certificate Sign, CRL Sign
Signature Algorithm: sha256WithRSAEncryption
23:00:ff:38:24:f8:e2:09:4a:cd:58:ff:ab:08:73:51:60:bb:
7f:92:67:bc:d0:31:a7:ca:95:1a:fd:a9:45:91:4f:3d:e9:58:
a9:50:53:8f:49:c4:82:c0:59:d5:a6:ab:95:07:ec:d2:85:f3:
bd:18:e8:32:8f:11:f0:c4:2d:41:0b:1d:8c:67:72:8b:c8:32:
6a:e2:81:2a:0d:9e:0f:4c:21:f0:35:0f:dd:18:b0:4f:13:d9:
12:26:f1:2e:f1:e1:0a:d0:a5:a1:18:ce:e0:2b:19:a9:07:43:
00:dd:d8:3b:42:9d:6f:53:79:b1:2a:c0:58:ca:ab:9c:e7:c3:
70:56:24:ee:da:3a:1d:77:6c:e1:f4:95:ba:72:91:ee:6b:68:
31:d1:ac:7f:85:47:23:bb:49:6b:35:29:d2:78:01:73:59:75:
20:5e:15:31:5a:dd:c4:73:18:f1:98:85:b8:34:70:ce:ba:dc:
4c:0a:d1:0d:9b:f0:ca:57:5a:ce:0a:ea:24:0d:7b:a3:eb:8d:
28:bf:07:43:e3:dc:83:ee:0a:cb:0f:49:9d:1b:26:27:0d:cb:
f9:33:85:9f:3b:b7:c4:fe:6d:3a:73:3d:69:86:72:ed:f6:1c:
d8:61:97:9f:44:81:ac:f1:bb:25:02:d5:00:aa:a8:76:d3:ae:
37:6c:11:47
[root@openvpn-server 3]#
3.2.1 为openvpn服务器颁发证书
#创建服务器证书申请文件,其中server是文件前缀
[root@openvpn-server 3]# ./easyrsa gen-req server nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
...........+++
............................................................................................+++
writing new private key to '/etc/openvpn/easy-rsa-server/3/pki/easy-rsa-1684.jLW8wL/tmp.nqY7jU'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [server]:openvpn
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa-server/3/pki/reqs/server.req
key: /etc/openvpn/easy-rsa-server/3/pki/private/server.key
[root@openvpn-server 3]#
# [root@openvpn-server 3]# tree pki/ -C
pki/ #公钥基础设施的主目录,其中包含所有的证书、密钥、和其他相关文件。
├── ca.crt #证书颁发机构(CA)的公共证书。它用于验证来自该CA签署的任何其他证书。
├── certs_by_serial #一个目录,其中包含由序列号索引的证书链接。它使得更容易地找到给定序列号的证书。
├── index.txt #一个数据库文件,其中包含CA签发的所有证书的状态信息。
├── index.txt.attr #与index.txt文件相关的属性文件。
├── issued #一个目录,其中包含CA签发的所有证书。
├── openssl-easyrsa.cnf #OpenVPN和easy-rsa的OpenSSL配置文件。
├── private #一个目录,其中包含私钥。不应与其他人分享这些密钥。
│ ├── ca.key #证书颁发机构(CA)的私钥。
│ └── server.key #OpenVPN服务器的私钥。
├── renewed #一个目录,其中包含续签的证书和密钥的相关数据。
│ ├── certs_by_serial
│ ├── private_by_serial
│ └── reqs_by_serial
├── reqs # 一个目录,其中包含证书签名请求(CSR)文件。
│ └── server.req #OpenVPN服务器的证书签名请求。
├── revoked #一个目录,其中包含被撤销的证书和密钥的相关数据。
│ ├── certs_by_serial
│ ├── private_by_serial
│ └── reqs_by_serial
├── safessl-easyrsa.cnf #另一个OpenSSL配置文件,可能是针对更安全的配置或特定的操作。
└── serial #一个文件,它包含下一个证书的序列号。
12 directories, 9 files
[root@openvpn-server 3]#
#将上面server.req的申请,颁发server类型的证书
[root@openvpn-server 3]# ./easyrsa sign-req server server
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a server certificate for 3650 days:
subject=
commonName = openvpn
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes #输入yes
Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-1886.heaNji/tmp.kGW5CF
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'openvpn'
Certificate is to be certified until Aug 19 07:13:37 2033 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt
[root@openvpn-server 3]#
# 创建 Diffie-Hellman 密钥
[root@openvpn-server 3]# ./easyrsa gen-dh
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
...............................................................................................................+......................................................................................................+.+......................................................................................................................................................................................................................................................................................................................................................................................+..........................................................................................................................................+................................................................................................++*++*
DH parameters of size 2048 created at /etc/openvpn/easy-rsa-server/3/pki/dh.pem
[root@openvpn-server 3]#
3.2.2 为客户端颁发证书
# 重新拷贝一份充当客户端环境
[root@openvpn-server openvpn]# cp -r /usr/share/easy-rsa /etc/openvpn/easy-rsa-client/
[root@openvpn-server openvpn]# cd /etc/openvpn/easy-rsa-client/3
# 生成证书申请所需目录pki和文件
[root@openvpn-server 3]# ./easyrsa init-pki
# 生成客户端用户的证书申请
[root@openvpn-server 3]# ./easyrsa gen-req xingyuyu nopass
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
...........................................................................................................+++
.....................................+++
writing new private key to '/etc/openvpn/easy-rsa-client/3/pki/easy-rsa-2122.AZW6ty/tmp.j15lap'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [xingyuyu]: #直接回车
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa-client/3/pki/reqs/xingyuyu.req #证书申请文件
key: /etc/openvpn/easy-rsa-client/3/pki/private/xingyuyu.key #私钥文件
[root@openvpn-server 3]# tree -C
.
├── easyrsa
├── openssl-easyrsa.cnf
├── pki
│ ├── openssl-easyrsa.cnf
│ ├── private
│ │ └── xingyuyu.key #私钥文件
│ ├── reqs
│ │ └── xingyuyu.req #证书申请文件
│ └── safessl-easyrsa.cnf
└── x509-types
├── ca
├── client
├── code-signing
├── COMMON
├── email
├── kdc
├── server
└── serverClient
4 directories, 14 files
[root@openvpn-server 3]#
# 回到CA的相关目录,为客户端颁发证书
[root@openvpn-server 3]#cd /etc/openvpn/easy-rsa-server/3
# 将客户端用户的申请文件导入到CA的申请目录里面,说白了就是copy文件的过程,得加上前缀邢宇宇
[root@openvpn-server 3]# ./easyrsa import-req /etc/openvpn/easy-rsa-client/3/pki/reqs/xingyuyu.req xingyuyu
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Easy-RSA error:
Unable to import: incorrect command syntax.
Run easyrsa without commands for usage and command help.
[root@openvpn-server 3]#
# 修改配置文件,刚才是为server颁发证书设置的是10年,但是现在为客户端颁发证书不能设置那么长的时间,所以需要修改
[root@openvpn-server 3]# vim vars
set_var EASYRSA_CERT_EXPIRE 180
# 签发证书
[root@openvpn-server 3]# ./easyrsa sign-req client xingyuyu
# 将CA和服务器证书相关文件复制到服务器相应的目录
[root@openvpn-server 3]# mkdir /etc/openvpn/certs
[root@openvpn-server 3]# cp /etc/openvpn/easy-rsa-server/3/pki/{ca.crt,dh.pem} /etc/openvpn/certs/
[root@openvpn-server 3]# cp /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt /etc/openvpn/certs/
[root@openvpn-server 3]# cp /etc/openvpn/easy-rsa-server/3/pki/private/server.key /etc/openvpn/certs
# 将客户端用户所需要的相关文件放到相应的目录
[root@openvpn-server 3]# mkdir /etc/openvpn/client/xingyuyu/
[root@openvpn-server 3]# find /etc/openvpn/ \( -name "xingyuyu.key" -o -name "xingyuyu.crt" -o -name ca.crt \) -exec cp {} /etc/openvpn/client/xingyuyu/ \;
# find /etc/openvpn/: find 是一个在目录结构中搜索文件的命令。/etc/openvpn/ 是要开始搜索的目录。
−name"xingyuyu.key"−o−name"xingyuyu.crt"−o−nameca.crt: 这是一个复杂的表达式,用于匹配三种文件名。
-name "xingyuyu.key": 匹配名为 "xingyuyu.key" 的文件。
-o: 逻辑 OR 操作符,表示满足任何一个条件的文件都将被选中。
-name "xingyuyu.crt": 匹配名为 "xingyuyu.crt" 的文件。
-name ca.crt: 匹配名为 "ca.crt" 的文件。
整个表达式的意思是:找到任何名称为 "xingyuyu.key"、"xingyuyu.crt" 或 "ca.crt" 的文件。
-exec cp {} /etc/openvpn/client/xingyuyu/ ;: 当 find 命令找到符合条件的文件时,它会对每个文件执行指定的操作。
-exec: 表示要对找到的文件执行一个操作。
cp {} /etc/openvpn/client/xingyuyu/: 是要执行的操作。其中 {} 是一个占位符,代表 find 命令找到的文件。所以,这个操作的意思是将找到的文件复制到 /etc/openvpn/client/xingyuyu/ 目录。
;: 表示 -exec 操作的结束。\是转义
4. 准备 OpenVPN 服务器配置文件
# 写入配置文件
[root@openvpn-server openvpn]# vim /etc/openvpn/server.conf
port 1194
proto tcp
dev tun
ca /etc/openvpn/certs/ca.crt
cert /etc/openvpn/certs/server.crt
key /etc/openvpn/certs/server.key # This file should be kept secret
dh /etc/openvpn/certs/dh.pem
server 10.8.0.0 255.255.255.0
push "route 172.30.0.0 255.255.255.0"
keepalive 10 120
cipher AES-256-CBC
compress lz4-v2
push "compress lz4-v2"
max-clients 2048
user openvpn
group openvpn
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 3
mute 20
[root@openvpn-server openvpn]#
#创建日志所在文件夹
[root@openvpn-server openvpn]# mkdir /var/log/openvpn
[root@openvpn-server openvpn]# chown openvpn.openvpn /var/log/openvpn/
# 开启网卡转发功能
[root@openvpn-server openvpn]# echo net.ipv4.ip_forward =1 >> /etc/sysctl.conf
[root@openvpn-server openvpn]# sysctl -p
# 使用openvpn,开启隧道默认的网段就是配置文件里面配置的网段,然后通过iptables配置以后将这个网段的地址指向内网地址
[root@openvpn-server openvpn]# echo "iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j MASQUERADE" >> /etc/rc.d/rc.local
[root@openvpn-server openvpn]# chmod +x /etc/rc.d/rc.local
[root@openvpn-server openvpn]# /etc/rc.d/rc.local
[root@openvpn-server openvpn]# iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * * 10.8.0.0/24 0.0.0.0/0
[root@openvpn-server openvpn]#
4.1 启动OpenVpn
# 这个文件默认Centos8没有,需要从CentOS7上拷贝
[root@openvpn-server openvpn]# vim /usr/lib/systemd/system/openvpn@.service
[root@openvpn-server openvpn]# ll /usr/sbin/openvpn
-rwxr-xr-x 1 root root 787232 Mar 18 2022 /usr/sbin/openvpn
[root@openvpn-server openvpn]#
# 启动
[root@openvpn-server openvpn]# systemctl daemon-reload
[root@openvpn-server openvpn]# systemctl enable --now openvpn@server
Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server.service to /usr/lib/systemd/system/openvpn@.service.
[root@openvpn-server openvpn]#
#查看网卡
[root@openvpn-server openvpn]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:16:3e:04:4a:08 brd ff:ff:ff:ff:ff:ff
inet 172.30.0.1/24 brd 172.30.0.255 scope global dynamic eth0
valid_lft 315348175sec preferred_lft 315348175sec
inet6 fe80::216:3eff:fe04:4a08/64 scope link
valid_lft forever preferred_lft forever
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 100
link/none
inet 10.8.0.1 peer 10.8.0.2/32 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::ea53:4d53:6150:51d6/64 scope link flags 800
valid_lft forever preferred_lft forever
[root@openvpn-server openvpn]#
#多了一个tun0的虚拟网卡,并且地址是10.8.0.1
5.准备 OpenVPN 服务器配置文件
#创建客户端的配置文件
[root@openvpn-server openvpn]# vim /etc/openvpn/client/xingyuyu/client.ovpn
client
dev tun
proto tcp
remote 39.100.98.155 1194
resolv-retry infinite
nobind
#persist-key
#persist-tun
ca ca.crt
cert xingyuyu.crt
key xingyuyu.key
remote-cert-tls server
#tls-auth ta.key 1
cipher AES-256-CBC
verb 3
compress lz4-v2
[root@openvpn-server openvpn]# tree /etc/openvpn/client/xingyuyu/
/etc/openvpn/client/xingyuyu/
├── ca.crt
├── client.ovpn
├── xingyuyu.crt
└── xingyuyu.key
0 directories, 4 files
[root@openvpn-server openvpn]#
#打包客户端用户所需的文件,这些文件需要导入到windows中的openvpn路径下才能使用
[root@openvpn-server ~]# cd /etc/openvpn/client/xingyuyu/
[root@openvpn-server ~]# tar cf /root/xingyuyu.tar ./
#将安装包解压,然后放到C:\Program Files\OpenVPN\config,就可以使用了
置文件
[root@openvpn-server openvpn]# vim /etc/openvpn/client/xingyuyu/client.ovpn
client
dev tun
proto tcp
remote 39.100.98.155 1194
resolv-retry infinite
nobind
#persist-key
#persist-tun
ca ca.crt
cert xingyuyu.crt
key xingyuyu.key
remote-cert-tls server
#tls-auth ta.key 1
cipher AES-256-CBC
verb 3
compress lz4-v2
[root@openvpn-server openvpn]# tree /etc/openvpn/client/xingyuyu/
/etc/openvpn/client/xingyuyu/
├── ca.crt
├── client.ovpn
├── xingyuyu.crt
└── xingyuyu.key
0 directories, 4 files
[root@openvpn-server openvpn]#
#打包客户端用户所需的文件,这些文件需要导入到windows中的openvpn路径下才能使用
[root@openvpn-server ~]# cd /etc/openvpn/client/xingyuyu/
[root@openvpn-server ~]# tar cf /root/xingyuyu.tar ./
#将安装包解压,然后放到C:\Program Files\OpenVPN\config,就可以使用了






















 4万+
4万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










